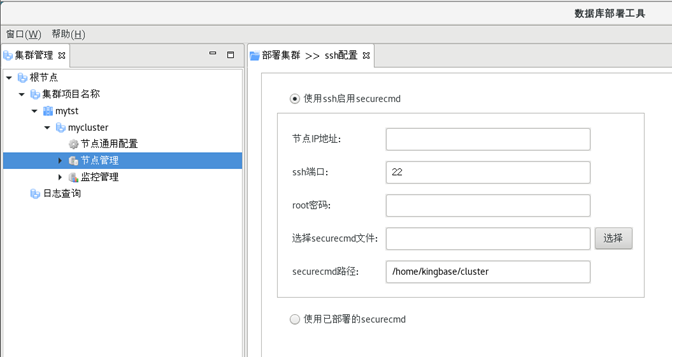
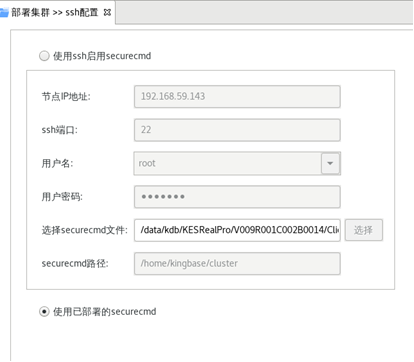
之前部署集群配置securecmdd工具使用图形化方式 配置报错,然后改用命令行方式手工配置使用。
1、在节点上部署securecmdd工具(all_nodes)
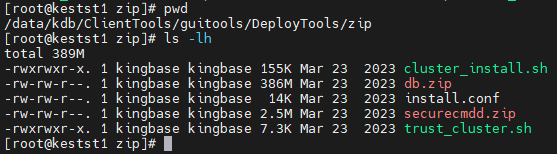
#查看数据库软件安装包:(自带securecmdd工具)
!
root@kestst1 zip\]# cp securecmdd.zip /home/kingbase/cluster/ \[root@kestst1 zip\]# cd /home/kingbase/cluster/ \[root@kestst1 cluster\]# unzip securecmdd.zip Archive: securecmdd.zip creating: securecmdd/ creating: securecmdd/lib/ inflating: securecmdd/lib/libcrypto.so.1.1 inflating: securecmdd/lib/libssl.so.1.1 creating: securecmdd/bin/ inflating: securecmdd/bin/sys_securecmd inflating: securecmdd/bin/sys_secureftp inflating: securecmdd/bin/sys_HAscmdd.sh inflating: securecmdd/bin/sys_securecmdd creating: securecmdd/share/ inflating: securecmdd/share/sys_HAscmdd.conf inflating: securecmdd/share/key_file inflating: securecmdd/share/securecmdd_config inflating: securecmdd/share/securecmdd.service inflating: securecmdd/share/securecmd_config inflating: securecmdd/share/accept_hosts \[root@kestst1 cluster\]# cd securecmdd/share/ \[root@kestst1 share\]# ls -lh total 24K -rw-------. 1 root root 381 Mar 23 2023 accept_hosts -rw-------. 1 root root 1.7K Mar 23 2023 key_file -rw-------. 1 root root 376 Mar 23 2023 securecmd_config -rw-------. 1 root root 647 Mar 23 2023 securecmdd_config -rw-r--r--. 1 root root 275 Mar 23 2023 securecmdd.service -rw-r--r--. 1 root root 310 Mar 23 2023 sys_HAscmdd.conf \[root@kestst1 share\]# 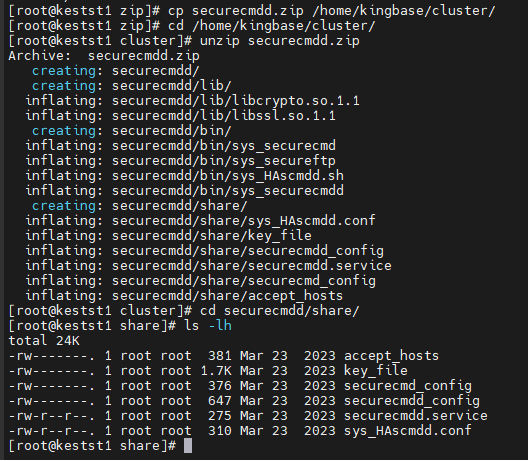 ###执行初始化 \[root@kestst1 bin\]# sh sys_HAscmdd.sh init successfully initialized the sys_securecmdd, please use "sys_HAscmdd.sh start" to start the sys_securecmdd ###查看生成的文件: \[root@kestst1 bin\]# ls -lh /etc/systemd/system/securecmdd.service -rw-r--r--. 1 root root 312 Jan 16 16:54 /etc/systemd/system/securecmdd.service ###查看内容: \[root@kestst1 bin\]# cat /etc/systemd/system/securecmdd.service \[Unit
Description=KingbaseES - sys_securecmdd daemon
After=network.target
Service
Type=simple
ExecStart=/home/kingbase/cluster/securecmdd/bin/sys_securecmdd -f /etc/.kes/securecmdd_config
ExecReload=/bin/kill -HUP $MAINPID
KillMode=process
Restart=always
RestartSec=10s
Install
WantedBy=multi-user.target
root@kestst1 bin\]# ###查看认证配置文件: 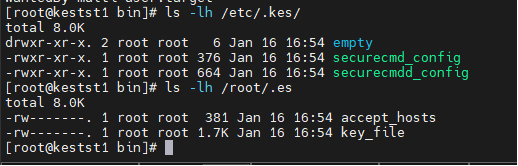 ###查看securecmdd服务配置文件: 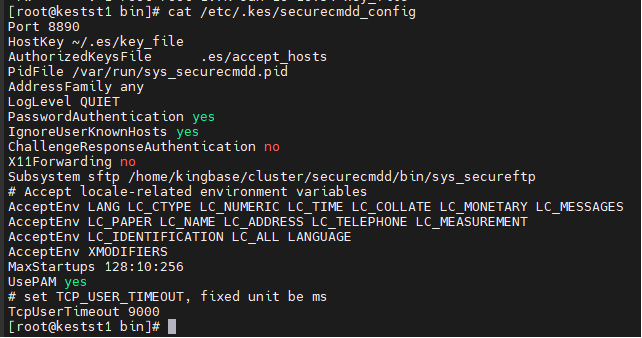 ###启动securecmdd服务 \[root@kestst1 bin\]# sh sys_HAscmdd.sh start Created symlink from /etc/systemd/system/multi-user.target.wants/securecmdd.service to /etc/systemd/system/securecmdd.service. \[root@kestst1 bin\]# ps -ef\|grep secure root 123671 1 0 16:58 ? 00:00:00 sys_securecmdd: /home/kingbase/cluster/securecmdd/bin/sys_securecmdd -f /etc/.kes/securecmdd_config \[listener\] 0 of 128-256 startups root 123837 72540 0 16:58 pts/1 00:00:00 grep --color=auto secure \[root@kestst1 bin\]# netstat -atnlp\|grep 8890 tcp 0 0 0.0.0.0:8890 0.0.0.0:\* LISTEN 123671/sys_securecm tcp6 0 0 :::8890 ::😗 LISTEN 123671/sys_securecm \[root@kestst1 bin\]# systemctl status securecmdd ● securecmdd.service - KingbaseES - sys_securecmdd daemon Loaded: loaded (/etc/systemd/system/securecmdd.service; enabled; vendor preset: disabled) Active: active (running) since Thu 2025-01-16 16:58:01 CST; 45s ago Main PID: 123671 (sys_securecmdd) CGroup: /system.slice/securecmdd.service └─123671 sys_securecmdd: /home/kingbase/cluster/securecmdd/bin/sys_securecmdd -f /etc/.kes/securecmdd_config ... Jan 16 16:58:01 kestst1.shanjia.com systemd\[1\]: Started KingbaseES - sys_securecmdd daemon. \[root@kestst1 bin\]# 之后添加节点可以使用已部署 进行后续操作