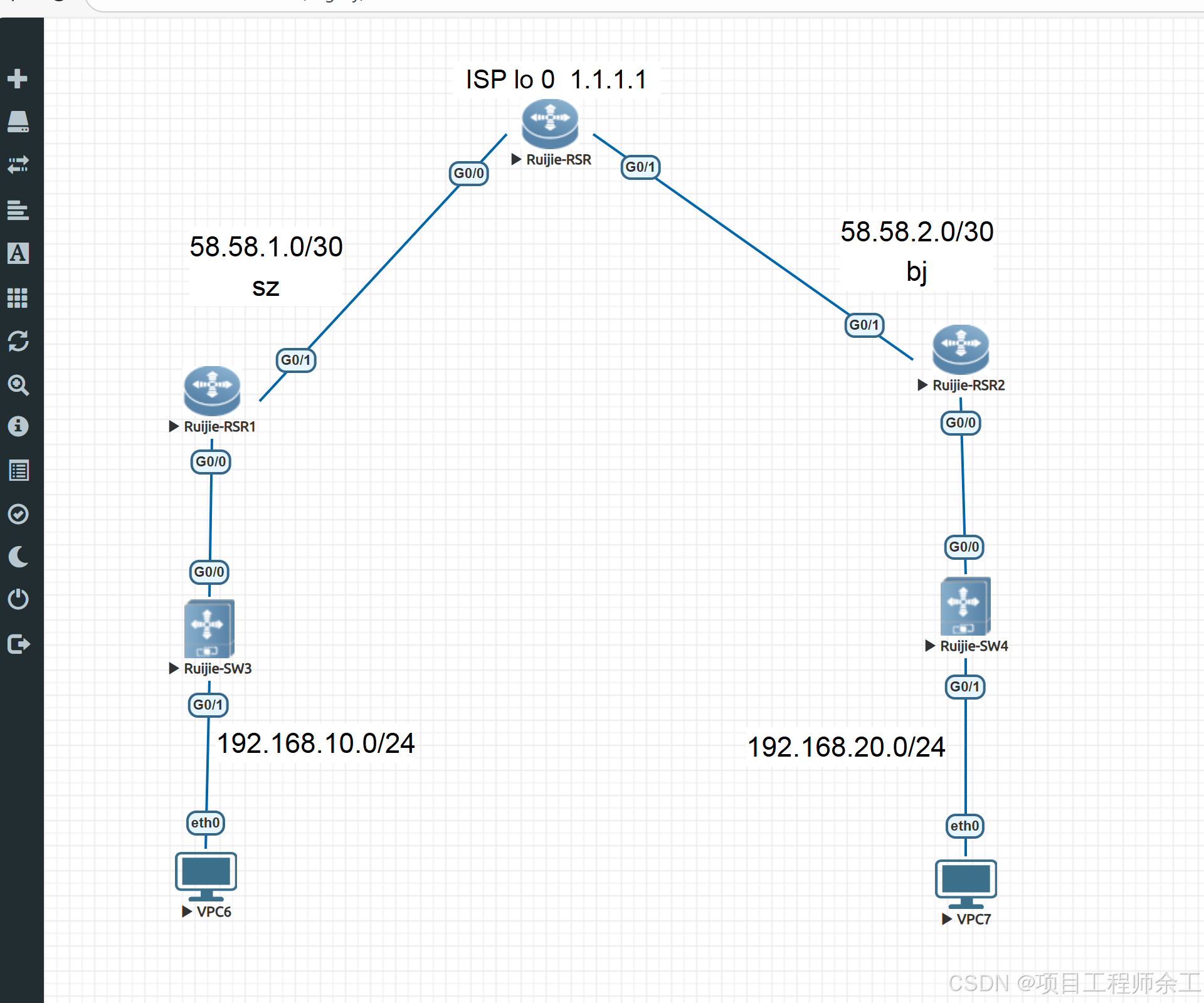
网络规划设计
1、r1和r2两个分支之间建立ipsec vpn
2、两边pc不但可以上网访问1.1.1.1还能互相通过ipsec vpn 隧道互访
3、最后扩展为换R2为ipsec模板模式配置
r1配置
sz#show running-config
Building configuration...
Current configuration: 1614 bytes
version RG-NSE-Route(V1.06)
hostname sz
!
ip access-list extended 100
5 deny ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 //把不做nat的数据给干掉
10 permit ip 192.168.10.0 0.0.0.255 any //nat上公网的数据
!
ip access-list extended 101
10 permit ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 //用于ipsec感兴趣流
!
no cwmp
!
service dhcp
!
ip dhcp pool 10 //用于pc的dhcp
network 192.168.10.0 255.255.255.0
dns-server 114.114.114.114
default-router 192.168.10.254
!
webmaster level 0 username admin password 7 073f07221c1c
!
crypto isakmp policy 1 // 里面参数两边要一样
encryption 3des
authentication pre-share
!
crypto isakmp keepalive 10 periodic //PDP探测
!
crypto isakmp key 0 admin address 58.58.2.2 //预共享密钥和对端地址
crypto ipsec transform-set admin esp-des esp-md5-hmac //加密方式
!
crypto map admin 5 ipsec-isakmp
set peer 58.58.2.2 //对端地址
set transform-set admin
match address 101
!
interface GigabitEthernet 0/0
ip address 192.168.10.254 255.255.255.0
ip nat inside
!
interface GigabitEthernet 0/1
ip address 58.58.1.2 255.255.255.252
crypto map admin //调用
ip nat outside
!
ip nat inside source list 100 interface GigabitEthernet 0/1 overload //nat上网
!
ip route 0.0.0.0 0.0.0.0 58.58.1.1
r2配置
bj#show running-config
Building configuration...
Current configuration: 1614 bytes
version RG-NSE-Route(V1.06)
hostname bj
!
ip access-list extended 100
5 deny ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255
10 permit ip 192.168.20.0 0.0.0.255 any
!
ip access-list extended 101
10 permit ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255
!
no cwmp
!
service dhcp
!
ip dhcp pool 20
network 192.168.20.0 255.255.255.0
dns-server 114.114.114.144
default-router 192.168.20.254
!
install 0 X86
!
sysmac 5000.0002.0001
!
webmaster level 0 username admin password 7 1226011f4303
!
crypto isakmp policy 1
encryption 3des
authentication pre-share
!
crypto isakmp keepalive 10 periodic
!
crypto isakmp key 7 04361c0b370d address 58.58.1.2
crypto ipsec transform-set admin esp-des esp-md5-hmac
!
crypto map admin 5 ipsec-isakmp
set peer 58.58.1.2
set transform-set admin
match address 101
!
no service password-encryption
!
redundancy
!
vpdn limit_rate 15
!
vlan 1
!
interface GigabitEthernet 0/0
ip address 192.168.20.254 255.255.255.0
ip nat inside
!
interface GigabitEthernet 0/1
ip address 58.58.2.2 255.255.255.252
crypto map admin
ip nat outside
!
ip nat inside source list 100 interface GigabitEthernet 0/1 overload
!
ip route 0.0.0.0 0.0.0.0 58.58.2.1
验证
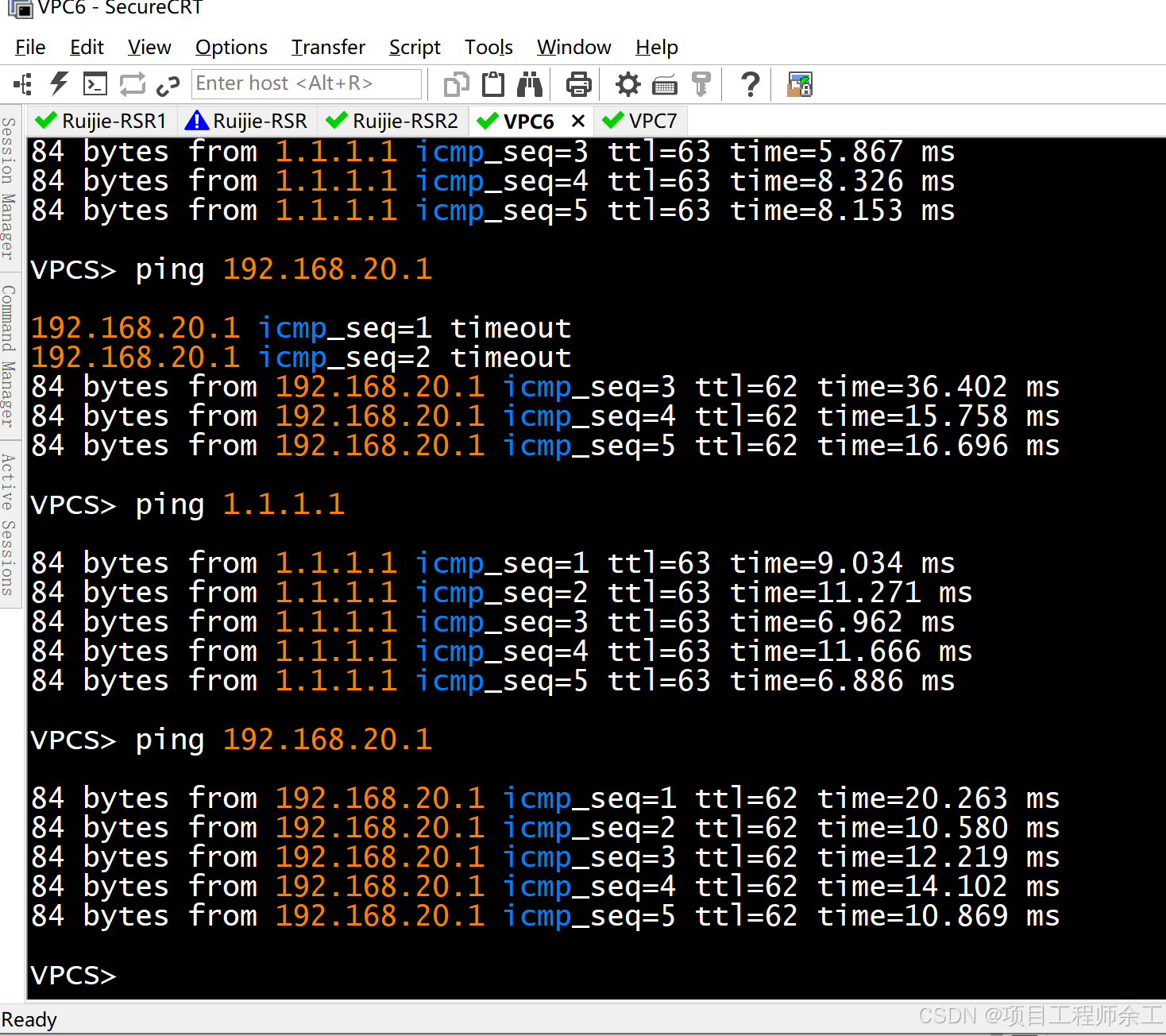
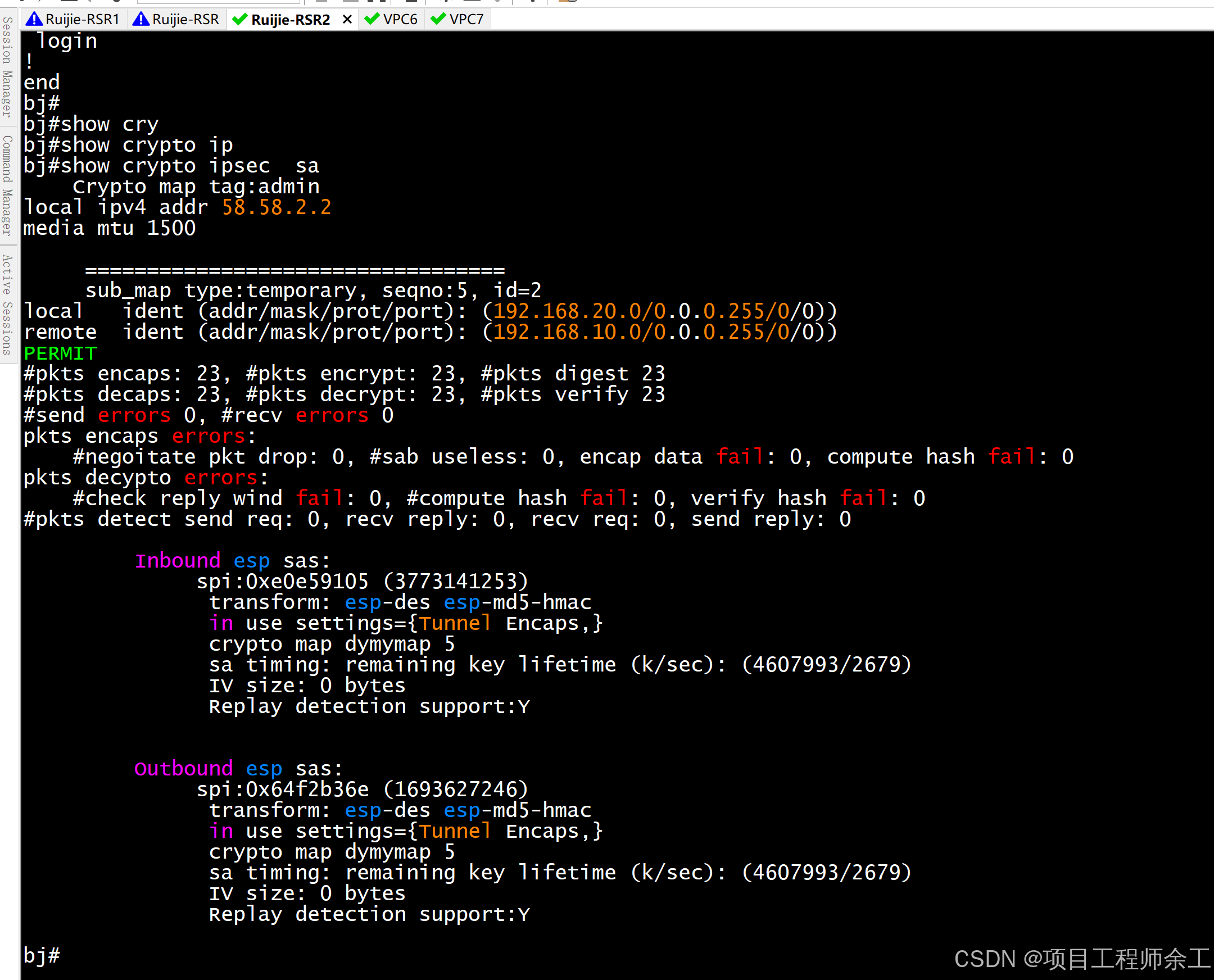
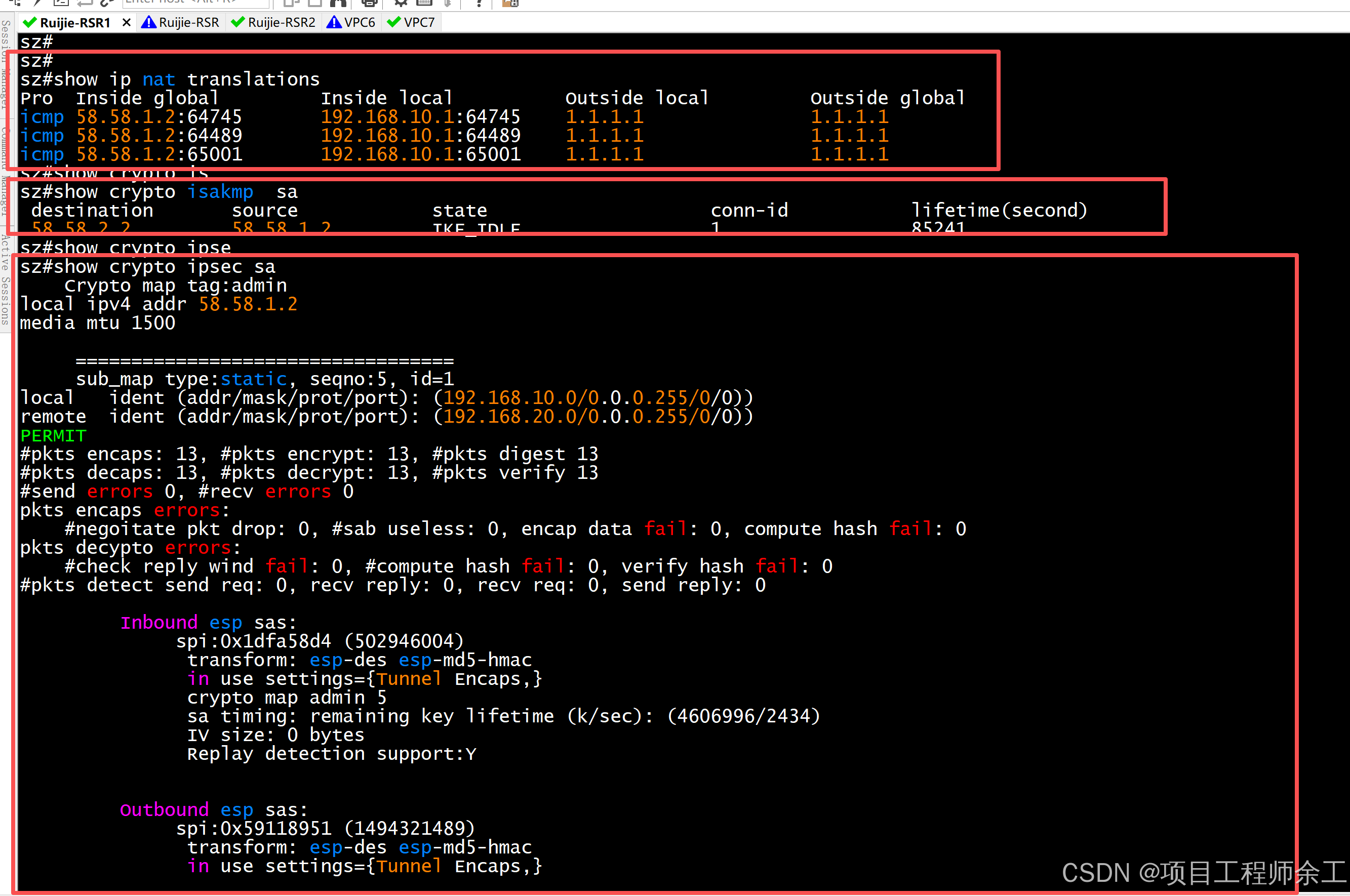
上面是nat记录同,下面是ipsec数据(注意两pc不ping一下,是看不到任何ipsec数据的,必须得先ping一下触发建立)
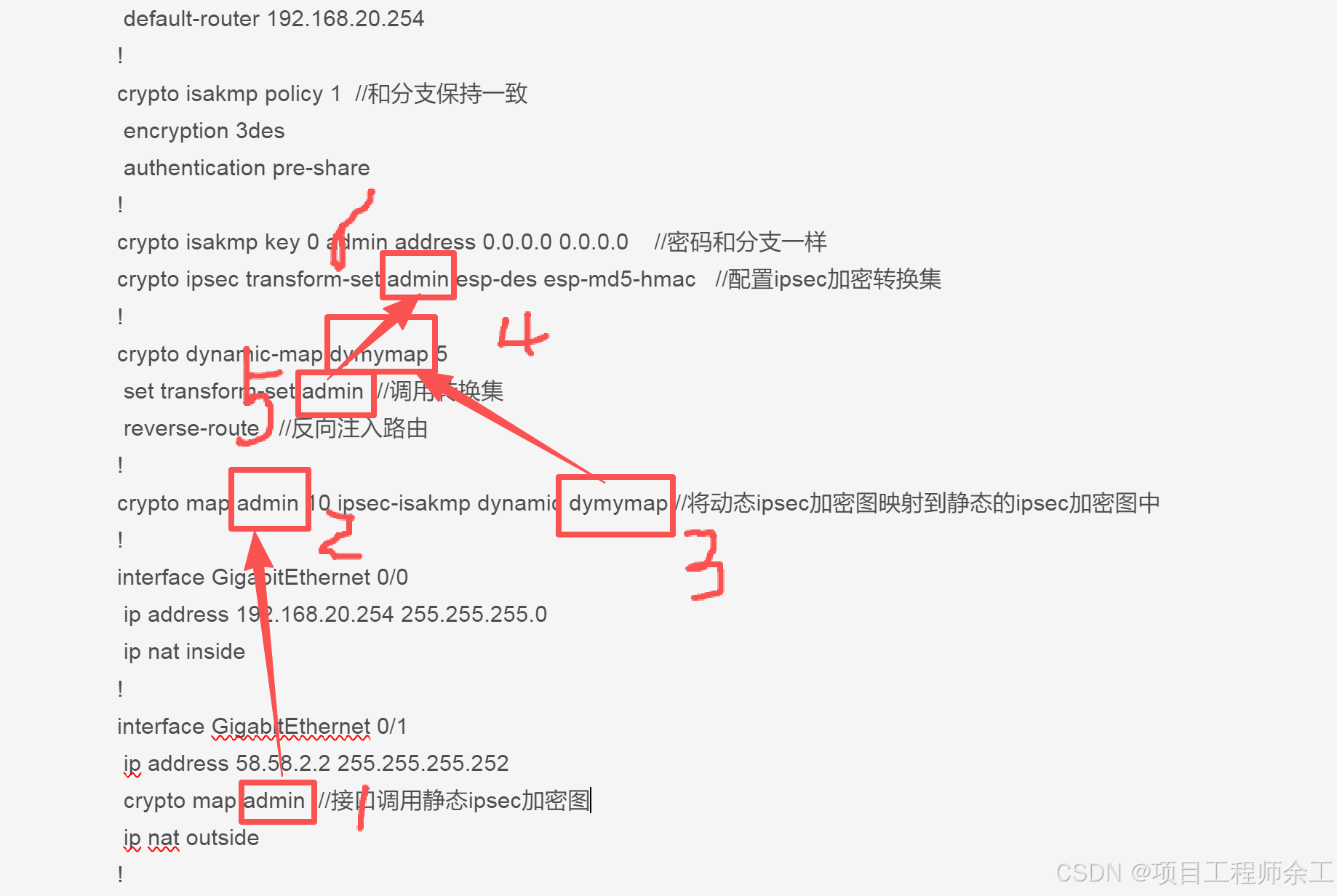
扩展测试,R2做成模板方式被动接受分支连接配置(R1配置不变),以后新增分支同R1一样就可以了
!
ip access-list extended 100
5 deny ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255
10 permit ip 192.168.20.0 0.0.0.255 any
!
原ipsec感兴趣流访问控制列表不需要了
ip access-list extended 101
10 permit ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255
!
service dhcp
!
ip dhcp pool 20
network 192.168.20.0 255.255.255.0
dns-server 114.114.114.144
default-router 192.168.20.254
!
crypto isakmp policy 1 //和分支保持一致
encryption 3des
authentication pre-share
!
crypto isakmp key 0 admin address 0.0.0.0 0.0.0.0 //密码和分支一样
crypto ipsec transform-set admin esp-des esp-md5-hmac //配置ipsec加密转换集
!
crypto dynamic-map dymymap 5
set transform-set admin //调用转换集
reverse-route //反向注入路由
!
crypto map admin 10 ipsec-isakmp dynamic dymymap //将动态ipsec加密图映射到静态的ipsec加密图中
!
interface GigabitEthernet 0/0
ip address 192.168.20.254 255.255.255.0
ip nat inside
!
interface GigabitEthernet 0/1
ip address 58.58.2.2 255.255.255.252
crypto map admin //接口调用静态ipsec加密图
ip nat outside
!
ip nat inside source list 100 interface GigabitEthernet 0/1 overload
!
ip route 0.0.0.0 0.0.0.0 58.58.2.1
这个模板配置逻辑是一环套一环
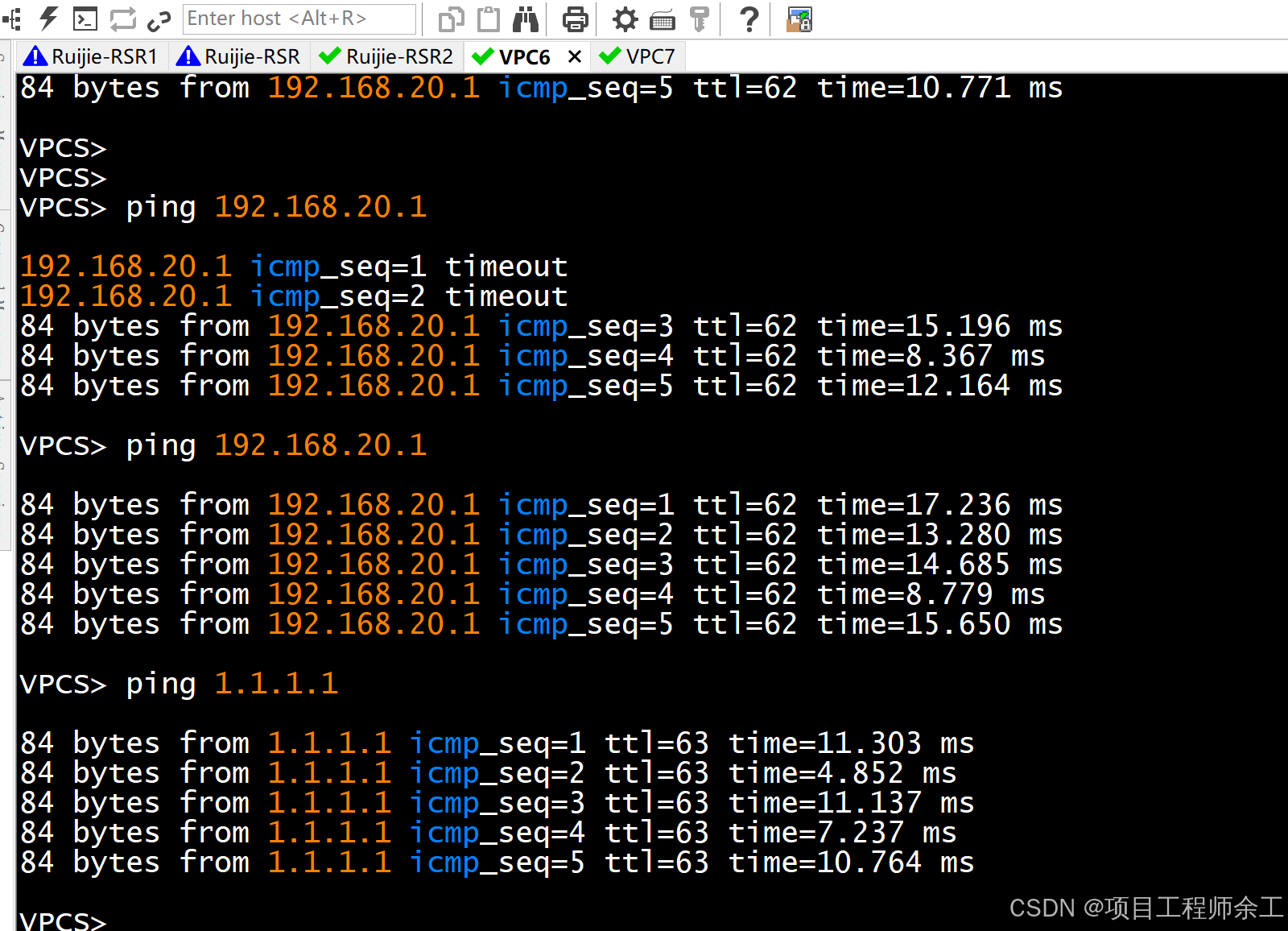
r1主动访问测试发现丢两个包就通了
之后r2模板方就可以主动访问分支了
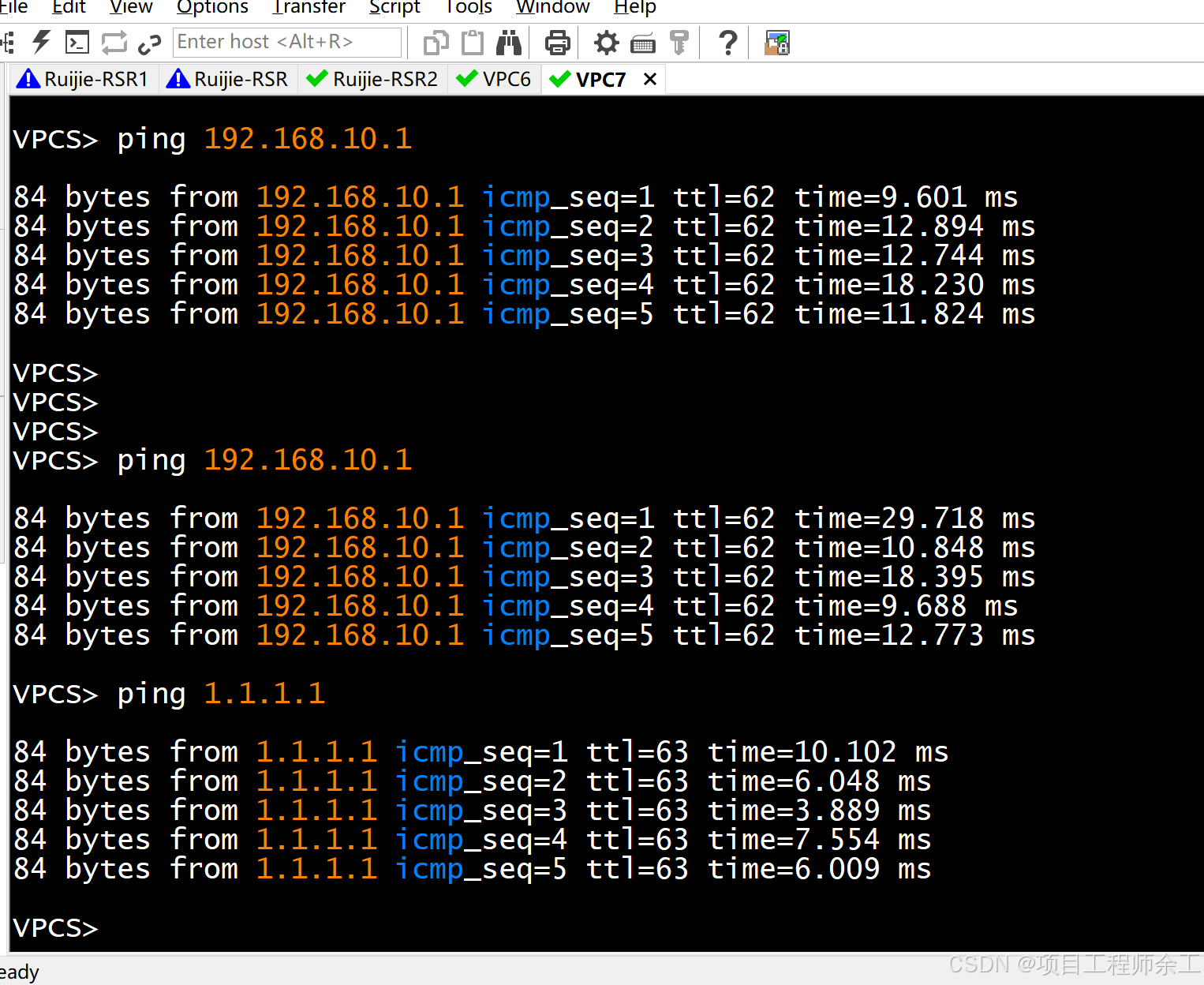
在r2模板方查看