防火墙GRE实验
一、防火墙GRE介绍
GRE:通用路由封装协议。它是一种隧道协议,本身不提供加密,而是像一个"管道"或"包装纸",将原始的数据包(如IP、IPX、AppleTalk等)封装在另一个IP数据包中进行传输。
防火墙GRE:指的是将GRE隧道的起点和终点设置在防火墙设备上。由防火墙来负责建立、维护GRE隧道,并通常结合防火墙的安全策略(如IPsec加密、访问控制列表ACL)来实现一个完整的、安全的站点到站点连接解决方案。
简单理解:防火墙充当了GRE隧道的"端点",并使用自身的安全功能来保护和管控流过隧道的流量。
二、实验拓扑图
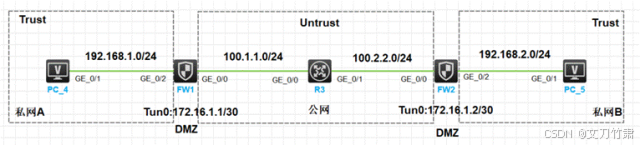
注:如无特殊说明,以下操作均采用HCL5.10.3版本且采用F1090进行实验
三、实验环境规划
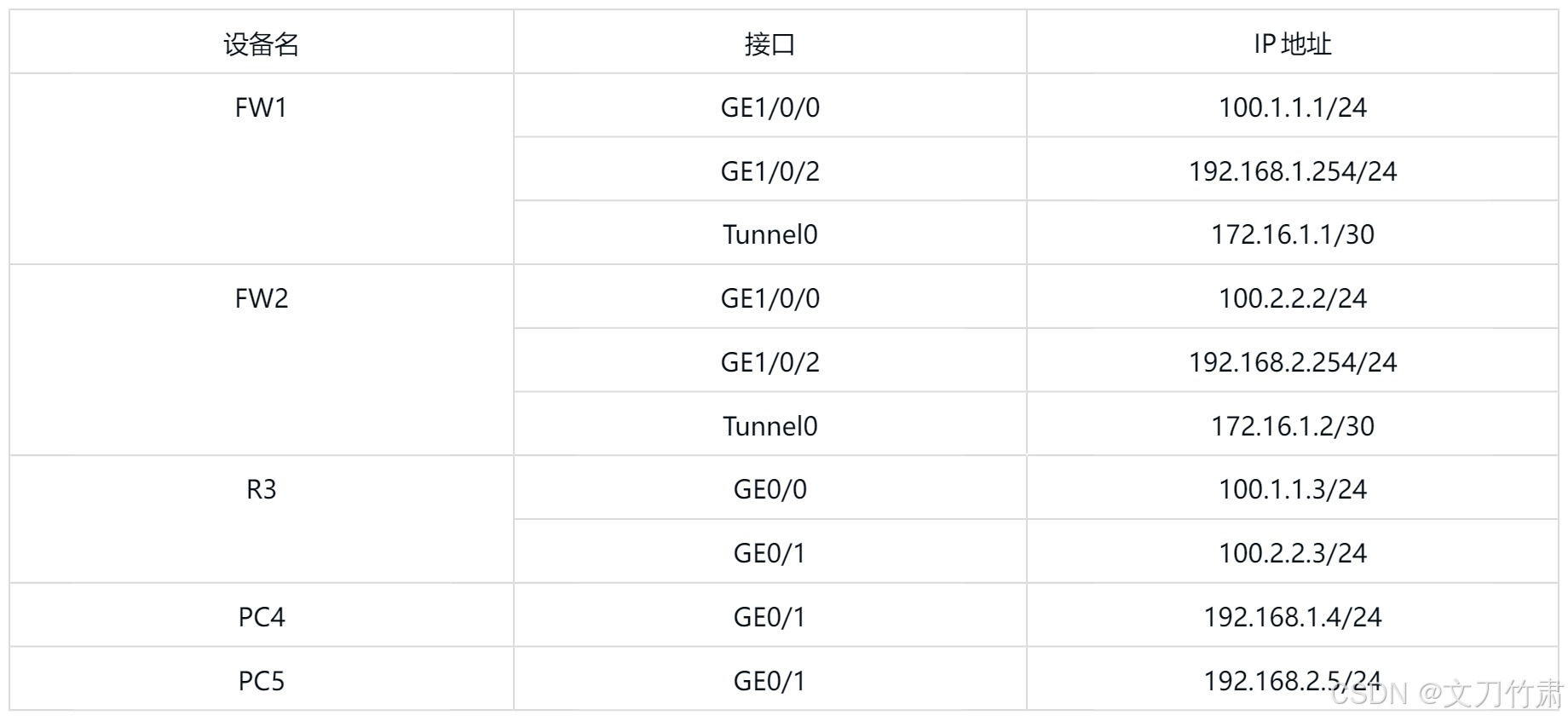
四、实验需求
1、按照图示配置IP地址和划分安全域
2、公网通过默认路由打通
3、配置GRE,要求FW1与FW2建立GRE隧道
4、配置OSPF,要求通过GRE隧道建立OSPF邻居传递双方私网路由使其互通
五、实验步骤
第一步:配置IP地址 略
第二步:划分安全域
bash
FW1:
[FW1]security-zone name Trust
[FW1-security-zone-Trust]import interface GigabitEthernet 1/0/2
[FW1-security-zone-Trust]quit
[FW1]security-zone name Untrust
[FW1-security-zone-Untrust]import interface GigabitEthernet 1/0/0
[FW1-security-zone-Untrust]quit
bash
FW2:
[FW2]security-zone name Trust
[FW2-security-zone-Trust]import interface GigabitEthernet 1/0/2
[FW2-security-zone-Trust]quit
[FW2]security-zone name Untrust
[FW2-security-zone-Untrust]import interface GigabitEthernet 1/0/0
[FW2-security-zone-Untrust]quit第三步:在防火墙上配置静态路由使其公网连通
bash
FW1:
[FW1]ip route-static 0.0.0.0 0 100.1.1.3
bash
FW2:
[FW2]ip route-static 0.0.0.0 0 100.2.2.3第四步:配置GRE隧道
步骤1:创建隧道接口,设置封装模式为GRE,指定封装的源目地址为双方公网地址
bash
FW1:
[FW1]interface tunnel 0 mode gre //进入Tunnel0接口视图,封装模式为GRE,如果没有则创建
[FW1-Tunnel0]ip address 172.16.1.1 30 //设置Tunnel0接口IP地址为172.16.1.1,掩码为30位
[FW1-Tunnel0]source 100.1.1.1 //指定GRE封装的源IP地址为100.1.1.1
[FW1-Tunnel0]destination 100.2.2.2 //指定GRE封装的目的IP地址为100.2.2.2
bash
FW2:
[FW2]interface tunnel 0 mode gre
[FW2-Tunnel0]ip address 172.16.1.2 30
[FW2-Tunnel0]source 100.2.2.2
[FW2-Tunnel0]destination 100.1.1.1步骤2:Tunnel接口加入至安全域
bash
FW1:
[FW1]security-zone name dmz
[FW1-security-zone-DMZ]import interface tunnel 0
bash
FW2:
[FW2]security-zone name dmz
[FW2-security-zone-DMZ]import interface tunnel 0第五步:配置OSPF,通过Tunnel接口建立邻居关系,传递双方私网路由
bash
FW1:
[FW1]ospf 1 router-id 1.1.1.1
[FW1-ospf-1]area 0
[FW1-ospf-1-area-0.0.0.0]network 172.16.1.0 0.0.0.3
[FW1-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
bash
FW2:
[FW2]ospf 1 router-id 2.2.2.2
[FW2-ospf-1]area 0
[FW2-ospf-1-area-0.0.0.0]network 172.16.1.0 0.0.0.3
[FW2-ospf-1-area-0.0.0.0]network 192.168.2.0 0.0.0.255第六步:配置安全策略
bash
FW1:
[FW1]security-policy ip
[FW1-security-policy-ip] rule 0 name ospf-peer
//放行OSPF的流量
[FW1-security-policy-ip-0-ospf-peer]action pass
[FW1-security-policy-ip-0-ospf-peer]source-zone local
[FW1-security-policy-ip-0-ospf-peer]source-zone dmz
[FW1-security-policy-ip-0-ospf-peer]destination-zone dmz
[FW1-security-policy-ip-0-ospf-peer]destination-zone local
[FW1-security-policy-ip-0-ospf-peer]service ospf
[FW1-security-policy-ip-0-ospf-peer]rule 1 name grevpn //放行OSPF和业务的GRE流量
[FW1-security-policy-ip-1-grevpn]action pass
[FW1-security-policy-ip-1-grevpn]source-zone local
[FW1-security-policy-ip-1-grevpn]source-zone untrust
[FW1-security-policy-ip-1-grevpn]destination-zone untrust
[FW1-security-policy-ip-1-grevpn]destination-zone local
[FW1-security-policy-ip-1-grevpn]service gre
[FW1-security-policy-ip-1-grevpn]rule 2 name ping //放行业务Ping流量
[FW1-security-policy-ip-2-ping]action pass
[FW1-security-policy-ip-2-ping]source-zone trust
[FW1-security-policy-ip-2-ping]source-zone dmz
[FW1-security-policy-ip-2-ping]destination-zone dmz
[FW1-security-policy-ip-2-ping]destination-zone trust
[FW1-security-policy-ip-2-ping]source-ip-subnet 192.168.1.0 255.255.255.0
[FW1-security-policy-ip-2-ping]source-ip-subnet 192.168.2.0 255.255.255.0
[FW1-security-policy-ip-2-ping]destination-ip-subnet 192.168.1.0 255.255.255.0
[FW1-security-policy-ip-2-ping]destination-ip-subnet 192.168.2.0 255.255.255.0
[FW1-security-policy-ip-2-ping]service ping
bash
FW2:
[FW2]security-policy ip
[FW2-security-policy-ip]rule 0 name ospf-peer
[FW2-security-policy-ip-0-ospf-peer]action pass
[FW2-security-policy-ip-0-ospf-peer]source-zone local
[FW2-security-policy-ip-0-ospf-peer]source-zone dmz
[FW2-security-policy-ip-0-ospf-peer]destination-zone dmz
[FW2-security-policy-ip-0-ospf-peer]destination-zone local
[FW2-security-policy-ip-0-ospf-peer]service ospf
[FW2-security-policy-ip-0-ospf-peer]rule 1 name grevpn
[FW2-security-policy-ip-1-grevpn]action pass
[FW2-security-policy-ip-1-grevpn]source-zone local
[FW2-security-policy-ip-1-grevpn]source-zone untrust
[FW2-security-policy-ip-1-grevpn]destination-zone untrust
[FW2-security-policy-ip-1-grevpn]destination-zone local
[FW2-security-policy-ip-1-grevpn]service gre
[FW2-security-policy-ip-1-grevpn]rule 2 name ping
[FW2-security-policy-ip-2-ping]action pass
[FW2-security-policy-ip-2-ping]source-zone dmz
[FW2-security-policy-ip-2-ping]source-zone trust
[FW2-security-policy-ip-2-ping]destination-zone trust
[FW2-security-policy-ip-2-ping]destination-zone dmz
[FW2-security-policy-ip-2-ping]source-ip-subnet 192.168.1.0 255.255.255.0
[FW2-security-policy-ip-2-ping]source-ip-subnet 192.168.2.0 255.255.255.0
[FW2-security-policy-ip-2-ping]destination-ip-subnet 192.168.1.0 255.255.255.0
[FW2-security-policy-ip-2-ping]destination-ip-subnet 192.168.2.0 255.255.255.0
[FW2-security-policy-ip-2-ping]service ping 第七步:查看效果
步骤1:查看OSPF邻居
bash
FW1:
[FW1]display ospf peer
OSPF Process 1 with Router ID 1.1.1.1
Neighbor Brief Information
Area: 0.0.0.0
Router ID AddressPri Dead-Time state Interface
2.2.2.2 172.16.1.21 37 Full/ - Tun0
FW2:
[FW2]display ospf peer
OSPF Process 1 with Router ID 2.2.2.2
Neighbor Brief Information
Area: 0.0.0.0
Router ID Address Pri Dead-TimeState Interface
1.1.1.1 172.16.1.1 1 34 Full/ - Tun0步骤2:测试双方私网PC是否能够连通
bash
PC4 Ping PC5:
<H3C>ping 192.168.2.5
Ping 192.168.2.5 (192.168.2.5): 56 data bytes, press CTRL_C to break
56 bytes from 192.168.2.5: icmp_seq=0 ttl=253 time=2.721 ms
56 bytes from 192.168.2.5: icmp_seq=1 ttl=253 time=2.864 ms
56 bytes from 192.168.2.5: icmp_seq=2 ttl=253 time=2.427 ms
56 bytes from 192.168.2.5: icmp_seq=3 ttl=253 time=2.533 ms
56 bytes from 192.168.2.5: icmp_seq=4 ttl=253 time=2.995 ms