此文的目的:
构建企业级应用从开发、部署、运行的一个缩影,整个流程虽然相对简陋,但是麻雀虽小五脏俱全,打通了服务编写、镜像构建、部署。为了小伙伴们大致了解DevOps和K8s集群部署有一个初步认识。
整体思路是:
1:编写一个及其简单的SpringBoot项目
2:基于Dockerfile构建镜像和Containerd
3:发布到k8s集群下属本地containerd容器池
4:编写k8s对象、kubectl apply一键运行。
前提条件:
1:已安装k8s集群服务
2:已经安装Docker
一:构建SpringBoot项目
1:基础环境
JDK:21
SpringBoot:3.5.10
2:添加SpringBoot Model
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>3.5.10</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.dashu</groupId>
<artifactId>k8s-controller</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>k8s-controller</name>
<description>k8s-controller</description>
<url/>
<licenses>
<license/>
</licenses>
<developers>
<developer/>
</developers>
<scm>
<connection/>
<developerConnection/>
<tag/>
<url/>
</scm>
<properties>
<java.version>21</java.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>3:编写简单代码
package com.dashu.controller;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RestController;
@RestController
public class TestController {
@GetMapping("/test")
public String TestMapping(){
return "hello k8s";
}
}3:打成可运行jar包
k8s-controller-0.0.1-SNAPSHOT.jar
二:构建Docker镜像
1:编写Dockerfile
FROM openjdk:21
ENV APP_PATH=/home/dashu/apps
WORKDIR $APP_PATH
## 添加jar包
ADD k8s-controller-0.0.1-SNAPSHOT.jar $APP_PATH/apps.jar
EXPOSE 8080
ENTRYPOINT ["java","-jar"]
CMD ["apps.jar"]2:jar包上传到Dockerfile同级目录
[root@localhost app]# ls
Dockerfile k8s-controller-0.0.1-SNAPSHOT.jar
[root@localhost app]#3:打包成Docker镜像
docker build -t myapp:v1 .4:保存成压缩包
docker save myapp:v1 -o /root/dockerfile/tar/myapp:v1.tar三:发布到k8s中运行
1:到k8s的woker节点上Docker镜像
我们上传的虽然是docker镜像,当前k8s当中运行的是containerd,这是可以兼容的。问题不大。
ctr -n k8s.io images import /root/pod/dockerapp/myapp_v1.tar2:查看Nodes节点上的containerd
第二个就是,就是我们本地上传的containerd
[root@k8s-node2 ~]# crictl --runtime-endpoint unix:///run/containerd/containerd.sock images
IMAGE TAG IMAGE ID SIZE
docker.io/dyrnq/metrics-server v0.6.2 25561daa66605 28.1MB
docker.io/library/myapp v1 f7598114965bc 552MB
docker.io/library/nginx 1.19 f0b8a9a541369 53.7MB
docker.io/library/nginx 1.21 0e901e68141fd 56.7MB
docker.io/library/nginx 1.23 a7be6198544f0 57MB
docker.io/library/redis 5.0.1 c188f257942c5 35.2MB
docker.io/mysql/mysql-server 8.0 1d9c2219ff692 166MB
docker.io/rancher/mirrored-flannelcni-flannel-cni-plugin v1.1.0 fcecffc7ad4af 3.82MB
docker.io/rancher/mirrored-flannelcni-flannel v0.20.2 b5c6c9203f83e 20.9MB
registry.aliyuncs.com/google_containers/coredns v1.9.3 5185b96f0becf 14.8MB
registry.aliyuncs.com/google_containers/kube-proxy v1.26.15 6c84132270a33 25.4MB
registry.aliyuncs.com/google_containers/kube-webhook-certgen v20231226-1a7112e06 eb825d2bb76b9 23.1MB
registry.aliyuncs.com/google_containers/nginx-ingress-controller v1.9.6 2bdab7410148a 105MB
registry.aliyuncs.com/google_containers/pause 3.2 80d28bedfe5de 299kB
[root@k8s-node2 ~]#3:创建k8s的指定的namespace
kubectl create ns springboot
4:下载ingress-Controller并进行部署
apiVersion: v1
kind: Namespace
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
name: ingress-nginx
---
apiVersion: v1
automountServiceAccountToken: true
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- namespaces
verbs:
- get
- apiGroups:
- ""
resources:
- configmaps
- pods
- secrets
- endpoints
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- coordination.k8s.io
resourceNames:
- ingress-nginx-leader
resources:
- leases
verbs:
- get
- update
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- create
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- discovery.k8s.io
resources:
- endpointslices
verbs:
- list
- watch
- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission
namespace: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- secrets
verbs:
- get
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
- namespaces
verbs:
- list
- watch
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- discovery.k8s.io
resources:
- endpointslices
verbs:
- list
- watch
- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission
rules:
- apiGroups:
- admissionregistration.k8s.io
resources:
- validatingwebhookconfigurations
verbs:
- get
- update
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
apiVersion: v1
data:
allow-snippet-annotations: "false"
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-controller
namespace: ingress-nginx
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
ipFamilies:
- IPv4
ipFamilyPolicy: SingleStack
ports:
- appProtocol: http
name: http
port: 80
protocol: TCP
targetPort: http
- appProtocol: https
name: https
port: 443
protocol: TCP
targetPort: https
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: NodePort
---
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-controller-admission
namespace: ingress-nginx
spec:
ports:
- appProtocol: https
name: https-webhook
port: 443
targetPort: webhook
selector:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
type: ClusterIP
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
minReadySeconds: 0
revisionHistoryLimit: 10
selector:
matchLabels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
strategy:
rollingUpdate:
maxUnavailable: 1
type: RollingUpdate
template:
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
spec:
containers:
- args:
- /nginx-ingress-controller
- --election-id=ingress-nginx-leader
- --controller-class=k8s.io/ingress-nginx
- --ingress-class=nginx
- --configmap=$(POD_NAMESPACE)/ingress-nginx-controller
- --validating-webhook=:8443
- --validating-webhook-certificate=/usr/local/certificates/cert
- --validating-webhook-key=/usr/local/certificates/key
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: LD_PRELOAD
value: /usr/local/lib/libmimalloc.so
image: registry.aliyuncs.com/google_containers/nginx-ingress-controller:v1.9.6
imagePullPolicy: IfNotPresent
lifecycle:
preStop:
exec:
command:
- /wait-shutdown
livenessProbe:
failureThreshold: 5
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
name: controller
ports:
- containerPort: 80
name: http
protocol: TCP
- containerPort: 443
name: https
protocol: TCP
- containerPort: 8443
name: webhook
protocol: TCP
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
resources:
requests:
cpu: 100m
memory: 90Mi
securityContext:
allowPrivilegeEscalation: false
capabilities:
add:
- NET_BIND_SERVICE
drop:
- ALL
readOnlyRootFilesystem: false
runAsNonRoot: true
runAsUser: 101
seccompProfile:
type: RuntimeDefault
volumeMounts:
- mountPath: /usr/local/certificates/
name: webhook-cert
readOnly: true
dnsPolicy: ClusterFirst
nodeSelector:
kubernetes.io/os: linux
serviceAccountName: ingress-nginx
terminationGracePeriodSeconds: 300
volumes:
- name: webhook-cert
secret:
secretName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission-create
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission-create
spec:
containers:
- args:
- create
- --host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.$(POD_NAMESPACE).svc
- --namespace=$(POD_NAMESPACE)
- --secret-name=ingress-nginx-admission
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.aliyuncs.com/google_containers/kube-webhook-certgen:v20231226-1a7112e06
imagePullPolicy: IfNotPresent
name: create
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 65532
seccompProfile:
type: RuntimeDefault
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
serviceAccountName: ingress-nginx-admission
---
apiVersion: batch/v1
kind: Job
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission-patch
namespace: ingress-nginx
spec:
template:
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission-patch
spec:
containers:
- args:
- patch
- --webhook-name=ingress-nginx-admission
- --namespace=$(POD_NAMESPACE)
- --patch-mutating=false
- --secret-name=ingress-nginx-admission
- --patch-failure-policy=Fail
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: registry.aliyuncs.com/google_containers/kube-webhook-certgen:v20231226-1a7112e06
imagePullPolicy: IfNotPresent
name: patch
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 65532
seccompProfile:
type: RuntimeDefault
nodeSelector:
kubernetes.io/os: linux
restartPolicy: OnFailure
serviceAccountName: ingress-nginx-admission
---
apiVersion: networking.k8s.io/v1
kind: IngressClass
metadata:
labels:
app.kubernetes.io/component: controller
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: nginx
spec:
controller: k8s.io/ingress-nginx
---
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
labels:
app.kubernetes.io/component: admission-webhook
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
app.kubernetes.io/version: 1.9.6
name: ingress-nginx-admission
webhooks:
- admissionReviewVersions:
- v1
clientConfig:
service:
name: ingress-nginx-controller-admission
namespace: ingress-nginx
path: /networking/v1/ingresses
failurePolicy: Fail
matchPolicy: Equivalent
name: validate.nginx.ingress.kubernetes.io
rules:
- apiGroups:
- networking.k8s.io
apiVersions:
- v1
operations:
- CREATE
- UPDATE
resources:
- ingresses
sideEffects: Nonekubectl apply -f ingress-nginx-deploy.yaml
5:编写k8s对象,我们给他启动起来。
apiVersion: apps/v1
kind: Deployment
metadata:
name: springboot
namespace: springboot
labels:
app: springboot
spec:
replicas: 1
selector:
matchLabels:
app: springboot
template:
metadata:
name: springboot
labels:
app: springboot
spec:
containers:
- name: springboot
image: myapp:v1
command: ["java"] # 可执行命令
args: ["-jar", "/home/dashu/apps/apps.jar"] # 命令参数(分开写)
imagePullPolicy: Never
restartPolicy: Always
---
apiVersion: v1
kind: Service
metadata:
name: springboot
# 关键修改:补充 namespace,和 Ingress/Deployment 保持一致
namespace: springboot
spec:
selector:
app: springboot
ports:
- name: springboot
port: 8080
targetPort: 8080
type: ClusterIP
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-springboot-ingress
namespace: springboot
spec:
# 新版 K8s(1.19+)推荐用 ingressClassName 替代注解
ingressClassName: nginx
rules:
# 最简规则:匹配域名(可先用 IP 测试,或改为 localhost)
- host: yonyouyou.com # 替换为你要访问的域名/IP
http:
paths:
- path: /
pathType: Prefix # 前缀匹配(所有路径都路由到后端)
backend:
service:
name: springboot
port:
number: 80806:查看最外端流量入口
[root@k8s-node1 pod]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
nginx-springboot-ingress nginx yonyouyou.com 192.168.67.129 80 31h
[root@k8s-node1 pod]# kubectl get pods
NAME READY STATUS RESTARTS AGE
springboot-b4f4d649d-hqjf8 1/1 Running 1 (10m ago) 31h
[root@k8s-node1 pod]# kubectl get service
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
springboot ClusterIP 10.100.96.205 <none> 8080/TCP 31h
[root@k8s-node1 pod]# kubectl get pods -A
NAMESPACE NAME READY STATUS RESTARTS AGE
ems nginx-59dd548446-2mzl8 1/1 Running 1 (10m ago) 32h
ingress-nginx ingress-nginx-admission-create-lpm7z 0/1 Completed 0 30h
ingress-nginx ingress-nginx-admission-patch-49mfg 0/1 Completed 0 30h
ingress-nginx ingress-nginx-controller-c954cf69-spssp 1/1 Running 1 (10m ago) 30h
kube-flannel kube-flannel-ds-dwhgb 1/1 Running 19 (10m ago) 134d
kube-flannel kube-flannel-ds-gghxh 1/1 Running 6 (10m ago) 3d4h
kube-flannel kube-flannel-ds-r2r5w 1/1 Running 19 (10m ago) 134d
kube-flannel kube-flannel-ds-z95lb 1/1 Running 18 (10m ago) 134d
kube-system coredns-5bbd96d687-5q7vt 1/1 Running 19 (10m ago) 134d
kube-system coredns-5bbd96d687-fj78w 1/1 Running 19 (10m ago) 134d
kube-system etcd-k8s-node1 1/1 Running 19 (10m ago) 134d
kube-system kube-apiserver-k8s-node1 1/1 Running 19 (10m ago) 134d
kube-system kube-controller-manager-k8s-node1 1/1 Running 20 (10m ago) 134d
kube-system kube-proxy-cgn9t 1/1 Running 18 (10m ago) 134d
kube-system kube-proxy-jxkfh 1/1 Running 19 (10m ago) 134d
kube-system kube-proxy-qdp9p 1/1 Running 19 (10m ago) 134d
kube-system kube-proxy-vhhhs 1/1 Running 6 (10m ago) 3d4h
kube-system kube-scheduler-k8s-node1 1/1 Running 20 (10m ago) 134d
kube-system metrics-server-65cf7984d5-cz7hr 1/1 Running 2 (9m59s ago) 32h
springboot springboot-b4f4d649d-hqjf8 1/1 Running 1 (10m ago) 31h
[root@k8s-node1 pod]# kubectl get service -A
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 134d
ems springboot ClusterIP 10.107.255.163 <none> 8080/TCP 32h
ingress-nginx ingress-nginx-controller NodePort 10.99.221.247 <none> 80:31452/TCP,443:32503/TCP 30h
ingress-nginx ingress-nginx-controller-admission ClusterIP 10.107.148.119 <none> 443/TCP 30h
kube-system kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 134d
kube-system metrics-server ClusterIP 10.105.9.69 <none> 443/TCP 4d6h
springboot springboot ClusterIP 10.100.96.205 <none> 8080/TCP 31h
[root@k8s-node1 pod]# kubectl get service -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx-controller NodePort 10.99.221.247 <none> 80:31452/TCP,443:32503/TCP 30h
ingress-nginx-controller-admission ClusterIP 10.107.148.119 <none> 443/TCP 30h
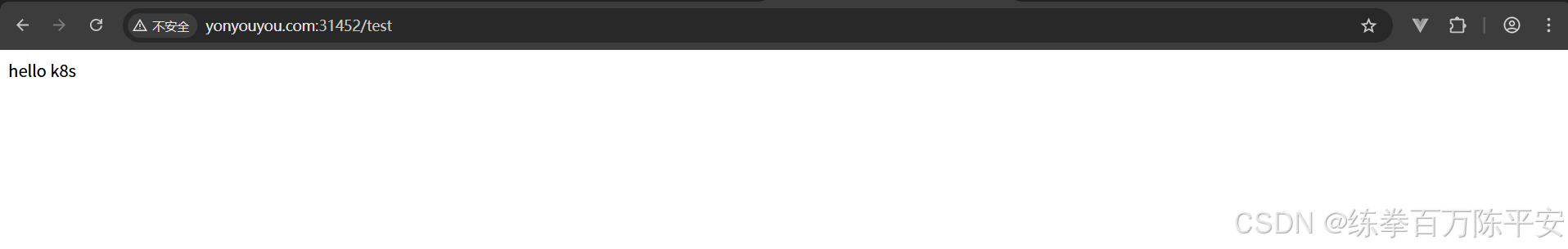
[root@k8s-node1 pod]#此时,我们得到结论,我们可以基于192.168.67.129:31452访问到流量到Pod中的服务。但是header中必须有yonyouyou.com这个域名。这个时候只需要本地host配置下即可。
192.168.67.129 yonyouyou.com然后浏览器上输入具体内容:yonyouyou.com/31452/test即可:
结果如下: