No Silver Bullet
23-24
In "No Silver Bullet," Frederick P. Brooks discusses the concept of essential difficulties in software engineering, highlighting complexity, conformity, changeability, and invisibility as key challenges.
-
Briefly explain each of these essential difficulties. (8 marks) 🆗
-
Evaluate the significance of these essential difficulties and their relevance to contemporary software engineering practices, methodologies, and technologies. (10 marks)🆗
22-23
In the article, No Silver Bullet: Essence and Accidents of Software Engineering written by Frederick P. Brooks, the author claimed that one of the very promising attacks on the essence difficulties in the software process is the requirements refinement and rapid prototyping. Explain why requirements refinement and rapid prototyping are claimed to be promising attacks. 🆗
20-21
Tom is a software engineer. He has 20 years of software development experience for the banking domain. Over the 20 years, his has success rate of up to 75% on his software development projects which is considered a very good result in the domain. His company treats him as a highly valuable asset. Is he a promising attack on the conceptual essences according to the article, No Silver Bullet, written by Frederick P. Brooks? Explain your answer in detail.
No , Tom is not a promising attack on the essential difficulties.
According to No Silver Bullet , promising attacks must tackle the core challenges of software: complexity, conformity, changeability, and invisibility.
Tom is a successful engineer, but he works within the existing system. He improves practice, not the nature of software itself. Brooks is looking for breakthroughs like AI or automation, not individual excellence.
Lec 1 exercise
n Software complexity leads to many difficulties, what are they? 🆗
n In your opinion, why is software perceived as the most conformable element? 🆗
n Define essential difficulties and accidental difficulties in the context of software engineering. Provide two examples of each type of difficulty. 🆗
n Discuss how contemporary practices like Agile and AI-enhanced tools are used to tackle essential difficulties identified by Fredrick Brooks. 🆗
Object-oriented Concepts
cohesion and coupling
23-24
In the context of software engineering, cohesion and coupling are two fundamental principles that govern the design and organization of classes, modules, and subsystems.
-
Define the terms "cohesion" and "coupling" within the context of software engineering.(6 marks)
-
Explain why these concepts are significant when designing and developing software. (4 marks)
22-23
Cohesion and coupling are common concepts in designing modular software systems.
-
Explain the concepts of cohesion and coupling. (6 marks)
-
The User class shown in Figure 1 below is considered a class with low cohesion, explain.(4 marks)

W2
Modify the following code to improve its cohesion

sol
(to make sure each class has a single, well-defined responsibility)
split the responsibilities into two separate classes:
-
SpeakerService -- handles speaker-related logic
-
ProductService -- handles product-related logic
java
// Handles all speaker-related actions
public class SpeakerService {
public Speaker saveSpeaker(Speaker speaker) {
// implementation
}
public boolean removeSpeaker(int speakerId) {
// implementation
}
public Speaker findById(int speakerId) {
// implementation
}
public void updateSpeakerPhoto(int speakerId, String photoUrl) {
// implementation
}
}
// Handles all product-related actions
public class ProductService {
public Product saveProduct(Product product) {
// implementation
}
public void deleteProducts(List<Integer> productsId) {
// implementation
}
public boolean deleteProduct(int productId) {
// implementation
}
}- Modify the following code to lower its coupling

Before Payroll is tightly coupled to ParttimeStaff.
Now Payroll doesn't care whether it's a part-time staff, intern, or freelancer --- as long as it implements Staff.
java
// Interface to abstract staff type
public interface Staff {
double getWorkedHours();
}
// Concrete class
public class ParttimeStaff implements Staff {
public double getWorkedHours() {
// ...
}
}
// Decoupled Payroll class
public class Payroll {
private Staff staff;
public Payroll(Staff s) {
this.staff = s;
}
public double calculatePay() {
return staff.getWorkedHours() * /* rate */;
}
}
把car拆出来这样就可以用别的交通工具
java
// Interface
public interface Vehicle {
void move();
}
// Concrete class
public class Car implements Vehicle {
public void move() {
System.out.println("Car is moving");
}
}
// Decoupled Traveler
class Traveler {
private Vehicle vehicle;
public Traveler(Vehicle v) {
this.vehicle = v;
}
public void startJourney() {
vehicle.move();
}
}Solid
TTL7
Discuss the Single Responsibility Principle (SRP) and provide an example of how it can be applied in a software design.
The Single Responsibility Principle (SRP) states that a class should have only one reason to change. This means that a class should have only one responsibility, i.e., only one potential source of change. For example, a class that handles user authentication should not also be responsible for sending email notifications. These responsibilities should be separated into distinct classes to adhere to SRP.
TTL8
How does the Open/Closed Principle (OCP) contribute to software maintainability and extensibility? Provide a real-world example to illustrate this principle.
The Open/Closed Principle (OCP) states that software entities should be open for extension but closed for modification. By adhering to OCP, developers can create software components that can be extended without modifying their source code, which contributes to better maintainability and extensibility.
For example, usingabstract classes orinterfaces to define general behavior that can be extended by concrete implementations without modifying the existing code showcases OCP in action.
-
Explain the concept of the Open/Closed principle in Object-Oriented design. (4 marks) 🆗
-
What is the main objective of the Open/Closed principle?(4 marks) 🆗
-
What could be the problem if we achieve the Open/Closed principle using inheritance?(4 marks) 🆗
Wk2 ex
You are provided with the following class design for a simple notification system. The class below does not adhere to the SOLID principles, particularly the Single Responsibility Principle (SRP) and the Open/Closed Principle (OCP).

Redesign the class structure to ensure that each class has only one reason to change, adhering to the Single Responsibility Principle.
Modify your design to comply with the Open/Closed Principle, allowing the system to support new notification methods without modifying existing code.
✅ 1. Define a Notification Interface
java
public interface Notification {
void send(String recipient, String message);
}✅ 2. Implement Each Notification Type Separately
java
public class EmailNotification implements Notification {
@Override
public void send(String recipient, String message) {
// Code to send email
System.out.println("Sending Email to " + recipient + ": " + message);
}
}
public class SMSNotification implements Notification {
@Override
public void send(String recipient, String message) {
// Code to send SMS
System.out.println("Sending SMS to " + recipient + ": " + message);
}
}
public class PushNotification implements Notification {
@Override
public void send(String recipient, String message) {
// Code to send Push Notification
System.out.println("Sending Push Notification to " + recipient + ": " + message);
}
}✅3. Logger Class with Single Responsibility
java
public class NotificationLogger {
public void log(String type, String message) {
// Log logic here
System.out.println("Logging " + type + ": " + message);
}
}✅ 4. NotificationService Using Composition (Extensible)
java
public class NotificationService {
private final Notification notification;
private final NotificationLogger logger;
public NotificationService(Notification notification, NotificationLogger logger) {
this.notification = notification;
this.logger = logger;
}
public void sendNotification(String recipient, String message, String type) {
notification.send(recipient, message);
logger.log(type, message);
}
}P50

Order 类通过组合 IMessageService 接口来发送消息。
Email 和 Facebook 类分别实现 IMessageService。
实现了解耦:添加新的消息发送方式(如微信)无需修改 Order 类。
✅ 核心接口与实现类(第2张图)
java
interface IMessageService {
public void Send(String text);
}
class Email implements IMessageService {
public void Send(String text) {
System.out.println(text + "\nSending product via Email...");
}
}
class Facebook implements IMessageService {
public void Send(String text) {
System.out.println(text + "\nSending product via Facebook...");
}
}✅ Order 类与客户端调用(第3张图)
java
class Order {
private IMessageService ms;
private Customer c;
public Order(Customer c) {
this.c = c;
if (c.IsPreferEmail()) {
ms = new Email();
} else {
ms = new Facebook();
}
}
public void SendMessage() {
ms.Send("Dear " + c.GetName() + ", thank you ...");
}
}-
Order组合了IMessageService接口,使其职责仅限于"下订单并通知用户",具体的发送逻辑交由Email或Facebook实现。 -
若将来增加
WeChat只需添加新类实现IMessageService,无需改动Order,符合 OCP。
主函数调用
java
class OrderServiceComposition {
public static void main(String args[]) {
Order o = new Order(new Customer("David", false)); // false → prefer Facebook
o.SendMessage();
}
}TTL10
Explain the Interface Segregation Principle (ISP) and discuss its role in software design.
The Interface Segregation Principle (ISP) states that a client should not be forced to implement an interface that it doesn't use. By creating specific interfaces for specific client requirements, ISPs promote modularity and reusability by allowing for smaller, more focused interfaces that cater to the specific needs of each client class.
TTL11
Describe how the Dependency Inversion Principle (DIP) helps to decouple software modules and enhance flexibility in a software architecture.
The Dependency Inversion Principle (DIP) emphasizes that high-level modules should not depend on low-level modules, but both should depend on abstractions. DIP helps to decouple software modules and enhance flexibility by relying on abstractions rather than concrete implementations. For example, depending on an abstract database interface rather than a specific database implementation allows for different database implementations to be used without modifying the high-level module.
TTL12
Whatis the problem with the following interface? Improve it.
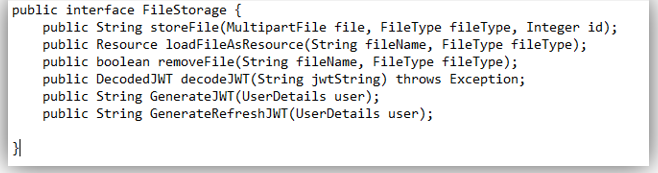
ISP: violates Clients should not be forced to depend on interfaces they do not use
java
public interface FileStorageService {
String storeFile(MultipartFile file, FileType fileType, Integer id);
Resource loadFileAsResource(String fileName, FileType fileType);
boolean removeFile(String fileName, FileType fileType);
}
public interface JwtService {
DecodedJWT decodeJWT(String jwtString) throws Exception;
String generateJWT(UserDetails user);
String generateRefreshJWT(UserDetails user);
}composition
In Object Oriented programming, we could use composition instead of inheritance in some situations. What are the THREE advantages of using composition over inheritance? (6 marks)
Design patterns
Lecture4 ex 4
You are tasked with designing a flexible sorting system for a data analysis application. The application needs to sort lists of data in various ways, such as bynumerical value , alphabetical order , or custom-defined criteria. The sorting method should be easily interchangeable during the run-time without modifying the existing code structure.
Task:
• Describe the Strategy design pattern and explain how it can be applied to solve the problem of interchangeable sorting methods.
Description of Strategy Pattern:
• The Strategy pattern defines a family of algorithms, encapsulates each one, and makes them interchangeable. This pattern allows the algorithm to vary independently from the clients that use it.
Advantages of Using the Strategy Pattern:
• Flexibility : It allows the client to choose and change the sorting algorithm at runtime without altering the client code.
• Maintainability : New sorting strategies can be added easily without modifying existing classes, adhering to the Open/Closed Principle.
• **Reusability:**Different sorting strategies are encapsulated in their own classes, making them reusable across different context.
• Draw a class diagram to represent your design for the system. Include at least three different sorting strategies: numerical, alphabetical, and a custom strategy of your choice.

Briefly explain the advantages of using the Strategy pattern in this context.
The State pattern is a behavioral pattern - it's used to manage algorithms, relationships and responsibilities between objects.
The definition of State provided in the original Gang of Four book on Design Patterns states: Allows an object to alter its behavior when its internal state changes. The object will appear to change its class.
Tutorial4 ex 2
A vending machine has various states like "NoSelection ", "HasSelection ", "InsertedMoney ", and "Dispensed ". The operations (events) a vending machine can perform are selectItem() , insertMoney() , dispenseItem() , cancel() , and refundMoney().
The behavior of these operations changes depending upon the current state of the machine. For instance, you can't dispense an item when there is "NoSelection" , or you can't make a selection when the machine is already in the "Dispensed" state. Which is the best design pattern for the vending machine problem? Justify your answer. (6 marks) Draw a class diagram for the design of the system.
Answer: State design pattern is suitable for the problem.
Justification: The vending machine has multiple states. Using State pattern, we can localize state-related operation into state classes making the code simpler and easy to maintain. The operations will transit the vending machine's states, by using State pattern, the state transition can be more explicit and easy to understand.

Tutorial4 ex 3
Question 3: An e-commerce platform usually provides multiple delivery strategies for customers such as Express Delivery, Standard Delivery, Drone Delivery, In-Store Pickup and more. Each delivery type has its own set of rules and calculations for cost, delivery date, etc.
- Express Delivery: This could involve a higher cost , but the item will be delivered the same day or the next day.
- Standard Delivery: This typically has a lower cost , but the item might take several days to be delivered.
- Drone Delivery: This involves a high cost, but offers speedy delivery.
- In-Store Pickup: The customer will come to the store to pick up the item, so no delivery charge is applied.
Include all the delivery strategies into one delivery class can clutter the code and lead to challenges for code maintenance. Which design pattern is the best candidate to solve the problem? Justify your answer. (6 marks) Draw a class diagram for the design of the system.
Answer: Strategy design pattern is the best candidate for the problem.
Justification: Each delivery strategy can be encapsulated as a separate class making it more reusable, maintainable, and testable. The delivery strategy is replaceable during runtime making if more flexible,

23-24
Design patterns are widely used in the field of software engineering to solve commonly occurring problems in software design. Understanding these patterns will equip you with the knowledge to design robust and scalable systems.
- Define the following concepts in the context of software design. (6 marks)
• Creational Design Patterns
• Structural Design Patterns
• Behavioral Design Patterns
-
The strategy design pattern is a behavioral pattern that allows the strategy (or algorithm) to be selected at runtime. Explain in detail the key components of the Strategy design pattern, using a real-world example to illustrate your explanation. (5 marks)
-
Draw a UML diagram for the Strategy patterns. (6 marks)
20-21
A parcel delivery company requires navigation software that generates delivery routes depending on various conditions. When delivery personnel enters the condition to the software, the software will generate an appropriate route and display the route on the map. Below is a table showing the condition and the respective algorithm to produce a suitable route.

A junior programmer started the coding process. He wrote a simple navigation program and added all the routing algorithms into the program. At first the program work fines but later when the company requests to add the more complicated condition, the program becomes more difficult to maintain. To ensure maintainability, you are requested to write the software following a suitable object-oriented design pattern.
-
Suggest a suitable design pattern. Justify your suggestion. (4 marks)
-
Write pseudo-code to illustrate the suggested design pattern for the solution. (20 marks)
Figure 2 illustrates the class diagram for asimple factory pattern of the Make Phone Call program. The corresponding code fragments are shown in Figure 3 below.


-
What is the main problem of the simple factory pattern?
-
Modify the class diagram shown in Figure 2 to provide a solution for the main problem of the simple factory pattern. (8 marks)
software reuse
22-23
List and explain THREE benefits of software reuse. (12 marks) 🆗
Compared to the Object-Oriented approach, how does the software component approach improve software reusability? (12 marks) 🆗
-
Higher-level reuse -- Components are larger, self-contained units that encapsulate complete functionality, making them easier to reuse across different systems.
-
Loose coupling and clear interfaces -- Components interact through well-defined interfaces, reducing dependencies and making integration simpler.
-
Independent and flexible deployment -- Components can be reused, updated, or replaced independently, often across different platforms and technologies.
20-21
What are the advantages of the component approach software development for software reusability over an object-oriented approach software development? 🆗
Q5
Component-Based Software Engineering (CBSE) is a branch of software engineering that emphasizes the design and construction of software systems using reusable software components.
-
Elaborate THREE main characteristics of a component in the context of CBSE. (6 marks)
-
Briefly explain the component identification sub-process in the context of development with reuse for CBSE. (6 marks)
这个不考了
20-21
A multi-national company is considering developing software to upgrade its finance department. The budget of $8 million for the software is allocated. The CFO of the company hopes that the software can be ready three months before the end of the year, which is a 30% shorter time compare to its normal development progress. He also wants the software to be able to serve the department steadily for the next 20 years because any upgrades or changes of software can be risky and costly to the department. The required software can be very complicated because the company is operating in several countries across different continents where the cultural background is diverse. Moreover, operation regulation and external policies are substantially different in between countries. The CTO of the company warned that the system has to be highly secured especially when the financial data is transmitting between the regional branches. The MIS department of the company understands that to shorten the development cycle, software reuse technique might be the solution.
Given an array of available techniques for software reuse, choosing the right technique can be challenging. Extract the key facts that influence the choice of techniques from the above statements to assist the MIS department in the process of selection. (8 marks)
wk5 lec 28*
• A software development team is tasked with creating a fitness tracking application that supports multiple user roles (athletes, coaches, health professionals), includes workout planning features, and integrates with external wearable devices (e.g., Fitbit). The client demands delivery within five months and prioritizes maintainability.
• Complete the following structured short-answer questions based on the scenario:
-
Name one software reuse technique suitable for this project.
-
State two reasons why the technique you chose in part 1) is suitable for this project.
wk5 lec P35*
You are a software engineering consultant hired by a company that develops mobile applications for different industries, such as healthcare, finance, and education. The company is considering adopting software reuse techniques to reduce development time and costs while maintaining high quality. They are particularly interested in understanding the differences between Application Frameworks and Software Product Lines (SPL).
Scenario:
The company plans to develop a new set of mobile apps for small businesses, including:
A point-of-sale (POS) app for retail stores.
An appointment scheduling app for service-based businesses.
An inventory management app for warehouses.
All apps need to run on both iOS and Android, and they must share common features like user authentication, payment processing, and data analytics.
wk5 lec p36
Define Application Frameworks and Software Product Lines (SPL), highlighting their key differences.
Recommend which technique (Application Frameworks or SPL) is more suitable for the company needs. Justify your choice with at least three specific reasons based on the scenario.
Identify two potential challenges the company might face when implementing your recommended technique.
wk5 lec p37*
For each strategy (Application Framework, SPL, and COTS), explain how it tackles at least two of the essential difficulties discussed in the essay written by Fred Brooks "No Silver Bullet", using examples to show your strategy in action.
Your task is to challenges the below given answer.
Application Frameworks:
• Complexity: Frameworks like Django reduce complexity by providing a structured blueprint---pre-built modules for carts, payments, and user accounts simplify the app's design. Instead of juggling chaotic code, you follow a clear MVC pattern.
• Changeability: They handle evolving needs well; adding a new payment gateway (e.g., Stripe) is just a matter of plugging into Django's extensible architecture via middleware or apps.
Software Product Lines (SPL):
• Complexity: SPLs tame complexity by creating a reusable core (e.g., shared checkout and inventory logic) for variants like mobile and desktop e-commerce apps, reducing redundant design work.
• Conformity: They align with real-world constraints by specializing the core---
e. g., a mobile version conforms to touch inputs, while desktop supports keyboard navigation, all from one base.
COTS*:
• Complexity: COTS like Shopify slashes complexity---you get a pre-built e-commerce solution with carts and analytics out of the box, no need to design from scratch.
• Changeability: It adapts to changes via configuration (e.g., adding a discount feature through plugins), though major shifts might hit customization limits.
23-24
Software Product Lines (SPL) is a software engineering methodology that uses platforms and reusable components to create a series of related applications.
-
Explain the concept of Software Product Lines (2 marks) 🆗
-
Discuss THREE of its advantages. (6 marks) 🆗
-
Let's think about a web development company that developed Software Product Lines for e-commerce applications.
The company has decided to create two version of products as follows:
• Product 1 includes basic e-commerce functionalities like a simple checkout system and basic inventory management.
• Product 2 includes advanced features like sophisticated inventory and supply chain management, integration with multiple payment gateways, and advanced analytics.
The company understands that its clients use different web hosting environments like Apache, NGINX, or cloud services like AWS or Azure. It wants its products to work smoothly in these different environments. So, it further specializes each product to ensure compatibility and optimize performance for each of these hosting environments.
What are the specializations the company has used when extending the product lines? Justify your answers. (6 marks)
Critical Analysis
FEMA
感觉这个界定挺玄学的,不太会考
e.g1 Game App
• Requirements FMEA:
• Function: Run the game on all phones.
• Failure Mode: "Game lags on old phones."
• RPN
• Severity: 8 (players quit)
• Occurrence: 4 (many old phones)
• Detection: 3 (easy to test)
• RPN = 8*4*3.
• Fix: Optimize graphics.
e.g2 Banking App
Design FMEA:
Function: Transferring money to another account
Failure Mode: transfer fails if server down?
RPN
Severity: 10 (money lost)
Occurrence: 2 (rare)
Detection: 5 (hard to catch)
RPN = 10*2*5.
Fix: Add offline queue.
eg3. exercise
• Task: Perform an FMEA on an Online Voting System
• Components: User authentication, vote submission, result tallying.
• Steps:
• Identify 3 failure modes.
• Assign Severity (1-10), Occurrence (1-10), Detection (1-10).
• Calculate RPN (Severity × Occurrence × Detection).

User Login System FMEA
You're a quality engineer analyzing a simple user login system for a web application. The system authenticates users via a username and password. You need to perform an FMEA to identify potential failures and prioritize risks.
- Identify two failure modes for the login system.
- For each failure mode:
- Describe the effect on the system or user.
- Suggest a possible cause.
- Assign Severity (S) (1-10: 1 = minor, 10 = catastrophic), Occurrence (O) (1-10: 1 = rare, 10 = frequent), and Detection (D) (1-10: 1 = always detected, 10 = undetectable).
- Calculate the Risk Priority Number (RPN) = S × O × D.
Answer
|--------------------------|-------------------|-----------------------|----------|------------|-----------|-----|
| Failure Mode | Effect | Cause | Severity | Occurrence | Detection | RPN |
| Incorrect password check | User cannot login | Logical error in code | 7 | 3 | 4 | 84 |
| Server timeout | Login hang | Network overload | 5 | 4 | 3 | 60 |
File Upload Feature FMEA
You're assessing a file upload feature in a cloud storage app. Users upload files via a web interface, and the system saves them to a server. Perform an FMEA to evaluate risks.
- Identify two failure modes for the file upload feature.
- For each failure mode:
- Describe the effect.
- Suggest a possible cause.
- Assign S , O , and D ratings (1-10 scale).
- Calculate the RPN.
Answer
|-----------------|-----------------------------|----------------------|----------|------------|-----------|-----|
| Failure Mode | Effect | Cause | Severity | Occurrence | Detection | RPN |
| File corruption | User loss data | Transfer interrupt | 9 | 3 | 4 | 108 |
| Upload timeout | Upload failed, user retries | Slow server response | 6 | 5 | 3 | 90 |
Real-Time Video Streaming Service FMEA**
You're a quality engineer for a real-time video streaming service (e.g., a live sports app). The critical function under analysis is "Stream video to user device", which handles encoding, transmission, and playback. The system processes 10,000 streams/hour during peak events. Perform an advanced FMEA with quantitative RPNs based on the following data:
- Historical Logs:
- 50 stream interruptions in 1,000 hours (0.05/hour/stream).
- 20 buffering delays in 1,000 hours (0.02/hour/stream).
- 10 decode errors in 1,000 hours (0.01/hour/stream).
- 5 crashes in 1,000 hours (0.005/hour/stream).
- Detection Metrics:
- Monitoring catches 90% of interruptions, 80% of delays, 70% of decode errors, 50% of crashes.
- Impact Assessment:
- Interruption: 10% user dropout (severe).
- Delay: 5% user dropout (moderate).
- Decode error: 8% user dropout (significant).
- Crash: 15% user dropout + complaints (critical).
- Identify four failure modes for "Stream video to user device."
- For each failure mode:
- Describe the effect on users/system.
- Identify a cause.
- Assign quantitative Severity (S) , Occurrence (O) , and Detection (D) ratings (1-10 scale):
- S: Based on user dropout % and impact (1 = <1%, 10 = >10%).
- O: From failure rate/hour (1 = <0.001, 10 = >0.1).
- D: From detection % (1 = >95%, 10 = <10%).
- Calculate RPN = S × O × D.
Answer
|----------------------|-------------------------------|--------------------------|----|---|---|-----|
| Failure Mode | Effect | Cause | S | O | D | RPN |
| stream interruptions | 10% user dropout | Network package loss | 10 | 5 | 2 | 100 |
| buffering delays | 5% user dropout | Insufficient bandwidth | 6 | 3 | 3 | 54 |
| decode errors | 8% user dropout | Codec error/incompatible | 8 | 2 | 4 | 64 |
| crashes | 15% user dropout + complaints | Memory overflow | 10 | 1 | 6 | 60 |
e.g
FMEA with Quantitative RPN
Task: Analyze a cloud storage API
• Failure Mode: "Upload fails under load."
• Data:
• MTTF = 1000 hours
• Downtime = $5K/hour
• Test Coverage = 90%.
• Calculate RPN, suggest mitigation.
ans:
Failure Mode: Upload fails under load.
Metrics:
• Severity: 5K/hour × hour outage = 5K impact → 8 (high but not catastrophic).
• Occurrence: MTTF = 1000 hours → Failure rate = 1/1000 = 0.001/hour → 2 (rare).
• Detection: 90% coverage → D% = 0.9 → (1 - 0.9) = 0.1 → 1 (very detectable).
• RPN: S x O x D = 8 × 2 × 1 = 16.
**Mitigation:**Add autoscaling to handle load spikes.
RCA
E-Commerce Order Processing Failure RCA
You're a reliability engineer performing an RCA for an e-commerce platform after a major outage where "Order processing fails"---customers couldn't complete purchases during a peak sale, costing $50K/hour. The system handles order validation, payment, and inventory updates. Using FTA, analyze the failure based on:
- Historical Data:
- Network disconnect: 0.02/hour (2% chance/hour).
- Server overload (caused by both):
- "High load" (0.05/hour)
- "No scaling" (0.15, 15% chance of no auto-scaling).
- Payment gateway failure: 0.03/hour (3% chance/hour).
- Database lock (caused by both):
- "Concurrency bug" (0.01/hour)
- "No lock timeout" (0.2, 20% chance of missing timeout logic).
- System Insight: Any one of these---network issue, server overload, payment failure, or DB lock---can halt order processing (top-level OR gate).
You are require to: -
- Construct the fault tree.
- Calculate the probability per hour of "Order processing fails" (round to three decimal places).
- Calculate MTTF.
Answer
顶层事件:订单处理失败
由四类问题触发(OR Gate):Network disconnect, Server overload, Payment gateway failure, Database lock
其中两个故障是由多个子原因组成的 AND Gate:
· Server Overload (AND):
- P = 0.05 × 0.15 = 0.0075/hour.
- (原因1:High load(0.05/hour)原因2:No scaling(15% 机会 = 0.15 概率))
· DB Lock (AND):
- P = 0.01 × 0.2 = 0.002/hour.
- (原因1:Concurrency bug(0.01/hour) 原因2:No lock timeout(0.2 概率))
· Network: 0.02/hour (direct).
· Payment: 0.03/hour (direct).
· Top Event (OR):
- P = 1 - (1 - 0.02) × (1 - 0.0075) × (1 - 0.03) × (1 - 0.002).
- = 1 - 0.98 × 0.9925 × 0.97 × 0.998.
- = 1 - 0.9419438 = 0.0580562 ≈ 0.058/hour (5.8% chance/hour).
MTTF = 1/0.058 = 17.24 hours
Cloud Backup System Failure RCA
You're investigating a cloud backup system failure where "Backup fails to complete", leaving customer data unprotected during a critical window. The RCA aims to trace root causes after 10% of backups failed last month (100 failures in 1,000 hours). Data includes:
- Network Issue (caused by either):
- "Packet loss" (0.04/hour)
- "Slow bandwidth" (0.03/hour).
- Storage Failure (caused by both):
- "Disk full" (0.02/hour)
- "No auto-expansion" (0.25, 25% chance of no expansion logic).
- Software Bug (caused by either):
- "Compression error" (0.015/hour)
- "File lock" (0.01/hour)
- "No retry" (0.3, 30% chance of no retry logic).
- Top-Level Logic: Any one of Network, Storage, or Software failure causes the backup to fail.
Your tasks: -
- Construct the fault tree (provided above).
- Calculate the probability per hour of "Backup fails to complete" (round to three decimal places).
- Calculate MTTF.
Answer
· Network Issue (OR):
- P = 1 - (1 - 0.04) × (1 - 0.03) = 1 - 0.96 × 0.97 = 1 - 0.9312 = 0.0688/hour.
· Storage Failure (AND):
- P = 0.02 × 0.25 = 0.005/hour.
· Software Bug:
- Lock Issue (AND): P = 0.01 × 0.3 = 0.003/hour.
- Total (OR): P = 1 - (1 - 0.015) × (1 - 0.003) = 1 - 0.985 × 0.997 = 1 - 0.982045 = 0.017955/hour.
· Top Event (OR):
- P = 1 - (1 - 0.0688) × (1 - 0.005) × (1 - 0.017955).
- = 1 - 0.9312 × 0.995 × 0.982045.
- = 1 - 0.909698 = 0.090302 ≈ 0.090/hour (9.0% chance/hour).
e.g Login Failure
Scenario: Users can't log into a banking app.
• Task:
• Build a fault tree:
• Top Event: "Login fails."
• Causes:
• "Login fails" if either "DB down" or "Auth error"
• "DB down" if either "Power outage" [0.01/hour] or "DB crash" [0.02/hour]
• "Auth error" if both "Bad credentials" [0.04/hour] and "No retry" [0.5]
• Calculate the probability.
Dynamic and Static Nature
• p(Server offline) = 0.01/hour
• p(Auth failed) = 0.02/hour
• p(Too many transactions) = 0.05/hour
• p(No lock timeout) = 0.1
• p(No validation) = 0.03
• Per Hour: "Gateway server offline" (0.01/hour), "API authentication error" (0.02/hour), "Too many transactions" (0.05/hour).
• No Time Unit: "No lock timeout set" (0.1), "No input validation" (0.03).
这个例题咋没给答案
e,g
Real-Time Chat App Disconnect
• Scenario: You're analyzing a real-time chat app where the top event is "User disconnects unexpectedly"---a critical failure that disrupts conversations. The system has multiple failure points, and the fault tree includes a top-level OR gate with both time-based and static probabilities
• The causes identify:
• Network Drop: 0.03/hour
• Server Crash: "Server overload": 0.04/hour and "No retry logic": 0.2
• Client Bug: "Bug in client code": 0.02/hour or "No client update": 0.1
• Task
• Build the fault tree
• Calculate the probability per hour of "User disconnects unexpectedly"
这个例题咋没给答案
open-source development
Tutorial
- What is the Bazaar model of software development and how does it contrast with traditional models?
The Bazaar model of software development is a decentralized model characterized by open collaboration and peer review. It contrasts with traditional models like the Cathedral model, where development is centralized and closed to outsiders, with changes released in full-fledged versions.
Key Principles of Open Source Development
- Define meritocracy in the context of open source development. 23-24
In open source development, meritocracy refers to the idea that individuals gain influence based on their contributions to the project. The more valuable contributions a person makes, the more they are recognized and respected within the community.
- Explain the role of user feedback in open source projects. 23-24
User feedback plays a crucial role in open source projects. It helps developers understand how the software is being used, what issues users are facing, and what features they would like to see in future updates.
- How does transparency factor into open source development? 23-24
Transparency in open source development means that the entire development process is open to public scrutiny. This includes the code base, issue tracking, discussions, and decision-making processes.
- Discuss the implications of licenses in open source software development.
Licenses define the legal parameters of how open-source software can be used, modified, and distributed. They protect the rights of both the developers and the users.
- Describe how principles of open source development can be implemented in a corporate setting.
In a corporate setting, open source principles can be applied to improve transparency, foster collaboration, and accelerate innovation. For instance, companies can use open source tools, contribute to open source projects, and even open source their own projects.
- Explain "Inner Source" and how it's related to open source development principles.
"Inner Source" is the practice of using open source methodologies within a single organization. It encourages collaboration across teams and departments, promotes codereuse , and improves code quality.
- Discuss the application of open source principles in the government sector.
In the government sector, open source principles can be used to improve transparency and citizen engagement. Governments can use open source software, release public data, and even invite citizens to contribute to software projects.
- What potential impact could embracing open source principles have on the future of software development?
Embracing open source principles can transform software development by promoting transparency, collaboration, and community. This can lead to higher-quality software, faster innovation, and a more inclusive and sustainable software industry.
Case Studies of Open Source Projects
- Give an example of a successful open source project and explain why it succeeded.
The Linux kernel is a successful open source project. It succeeded due to a combination of factors such as strong leadership, a dedicated community, and the ability to meet the needs of a diverse user base.
- What common challenges do open source projects face and how can they be mitigated?
Common challenges include coordinating contributions from a distributed community, ensuring the quality and security of the code, and sustaining momentum over time. These can be mitigated through things like clear governance structures, strong leadership, active community engagement, and robust quality assurance processes.
The Social and Cultural Aspects of Open Source Development
- Explain the social and cultural aspects of open source development.
The social and cultural aspects of open source development involve the community that forms around the project. This includes social norms, communication patterns, decision-making processes, conflict resolution mechanisms, and recognition systems.
- How does an open source community resolve conflicts that arise during the development process?
Open source communities typically resolve conflicts through mechanisms like public discussions, votes, or decisions by a designated authority like a project leader or a steering committee.
- What role does recognition and reputation play in open source communities?
Recognition and reputation are major motivators in open source communities. Contributors earn recognition for their contributions, and this can enhance their reputation within the community, potentially leading to career opportunities.
- How do open source platforms promote continuous learning and mentorship?
Open source platforms promote continuous learning and mentorship by allowing new contributors to learn from experienced ones. They provide opportunities to work on real-world projects, gain feedback, and improve skills.
Black-box Testing
Boundary Value Testing (BVT)
Tutorial11
Consider a software application that calculates the monthly payments of a car loan. The application accepts three inputs:
- Cost of the car: The cost should be a positive integer between 1,000 and 200,000.
- Loan period: The period of the loan in years should be a positive integer between1 and 10 years.
- Interest rate: The annual interest rate should be a positive decimal between 0.01 (1%) and 0.2 (20%).
- Create Normal Boundary Value cases to test the functionality of this application.
- Create Robust Boundary Value cases to test the functionality of this application.
- Create Worst-case Boundary Value cases to test the functionality of this application.
- Create Robust Worst-case Boundary Value cases to test the functionality of this application.
sol
Boundary values
- Cost of the car: 1000 (min), 1001 (min+), 100000(nom), 199999 (max-), and $200,000 (max).
- Loan period: 1 year (min), 2 years (min+), 5 years (nom), 9 years (max-), and 10 years (max).
- Interest rate: 0.01 (min), 0.02 (min+), 0.1 (nom), 0.19 (max-), and 0.2 (max).
p.s 在这个题目中,虽然按照常规计算,名义值是100500,但在实际应用中,选择100000作为名义值是为了简化测试过程,并且它更符合实际情况。这也是为什么答案中选择了100000而不是100500。Invalid values
- Cost of the car: Lower invalid value 999, Upper invalid value 200,001.
- Loan period: Lower invalid value 0 years, Upper invalid value 11 years.
- Interest rate: Lower invalid value 0, Upper invalid value 0.21.
| min | min+ | nom | max- | max | invalid low | invalid high | |
|---|---|---|---|---|---|---|---|
| Cost of the car | 1000 | 1001 | 100000 | 199999 | 200000 | 999 | 200001 |
| Loan period | 1 | 2 | 5 | 9 | 10 | 0 | 11 |
| Interest rate | 0.01 | 0.02 | 0.1 | 0.19 | 0.2 | 0 | 0.21 |
- Normal Boundary Value cases
Number of test cases = 4(n) + 1 = 4(3) + 1 = 13 test cases.
|------|-----------------|-------------|---------------|-----------------|
| Case | Cost of the car | Load period | Interest rate | Expected result |
| 1 | 100000 | 5 | 0.01 | |
| 2 | 100000 | 5 | 0.02 | |
| 3 | 100000 | 5 | 0.1 | |
| 4 | 100000 | 5 | 0.19 | |
| 5 | 100000 | 5 | 0.2 | |
| 6 | 100000 | 1 | 0.1 | |
| 7 | 100000 | 2 | 0.1 | |
| 8 | 100000 | 9 | 0.1 | |
| 9 | 100000 | 10 | 0.1 | |
| 10 | 1000 | 5 | 0.1 | |
| 11 | 1001 | 5 | 0.1 | |
| 12 | 199999 | 5 | 0.1 | |
| 13 | $200000 | 5 | 0.1 | |
- Robust Boundary Value cases
Number of test cases = 6(n) + 1 = 6(3) + 1 = 19 test cases.
|------|-----------------|-------------|---------------|-----------------|
| Case | Cost of the car | Load period | Interest rate | Expected result |
| 1 | 100000 | 5 | 0 | |
| 2 | 100000 | 5 | 0.01 | |
| 3 | 100000 | 5 | 0.02 | |
| 4 | 100000 | 5 | 0.1 | |
| 5 | 100000 | 5 | 0.19 | |
| 6 | 100000 | 5 | 0.2 | |
| 7 | 100000 | 5 | 0.21 | |
| 8 | 100000 | 0 | 0.1 | |
| 9 | 100000 | 1 | 0.1 | |
| 10 | 100000 | 2 | 0.1 | |
| 11 | 100000 | 9 | 0.1 | |
| 12 | 100000 | 10 | 0.1 | |
| 13 | 100000 | 11 | 0.1 | |
| 14 | 999 | 5 | 0.1 | |
| 15 | 1000 | 5 | 0.1 | |
| 16 | 1001 | 5 | 0.1 | |
| 17 | 199999 | 5 | 0.1 | |
| 18 | 200000 | 5 | 0.1 | |
| 19 | $200001 | 5 | 0.1 | |
- Worst-case Boundary Value cases
Number of test cases = Cartesian product the possible values for 3 variables = 5^3 = 125 test cases.
|------|-----------------|-------------|---------------|-----------------|
| Case | Cost of the car | Load period | Interest rate | Expected result |
| 1 | 1000 | 1 | 0.01 | |
| 2 | 1000 | 1 | 0.02 | |
| | 1000 | 1 | 0.1 | |
| | 1000 | 1 | 0.19 | |
| | 1000 | 1 | 0.2 | |
| | 1000 | 2 | 0.01 | |
| | 1000 | 2 | 0.02 | |
| | 1000 | 2 | 0.1 | |
| | 1000 | 2 | 0.19 | |
| | 1000 | 2 | 0.2 | |
| | 1000 | 5 | 0.2 | |
| | 1000 | 5 | 0.01 | |
| | 1000 | 5 | 0.02 | |
| | 1000 | 5 | 0.1 | |
| | 1000 | 5 | 0.19 | |
| | 1000 | 5 | 0.2 | |
- Robust Worst-case Boundary Value cases
Number of test cases = Cartesian product the possible values for 3 variables = 7^3 = 343 test cases.
Equivalence Class Partitioning
Lecture
Consider an example of a simple car rental system where the desired output is the rental cost.
The system calculates the cost based on the type of car, rental duration (in days), and whether the customer has a membership for a discount.
Here are the rules:
-
Economy cars cost 20 per day, SUVs 50 per day, and Luxury cars are $100 per day.
-
Members get a 10% discount on the total cost.
sol
output equivalence classes
-
Economy car/non-members: $20/day
-
Economy car / members: $20/day with a 10% discount
-
SUV / non-members: $50/day
-
SUV / members: $50/day with a 10% discount
-
Luxury car / non-members: $100/day
-
Luxury car / members: $100/day with a 10% discount
Weak Normal Equivalence Class Testing
-
Renting an Economy car for 3 days by a non-member.
-
Renting an Economy car for 2 days by a member.
-
Renting an SUV for 4 days by a non-member.
-
Renting an SUV for 7 days by a member.
-
Renting a Luxury car for 1 day by a non-member.
-
Renting a Luxury car for 5 days by a member.
Strong Normal Equivalence Class Testing
you would now choose one representative from each equivalence class and test for all possible combinations.
注意这里添加了一个天数,强等价类测试中,为了考虑所有交互组合与输出变化,还是推荐列入多个天数作为变量之一
-
Economy car rented by a non-member for 1 day.
-
Economy car rented by a non-member for 2 days.
-
Economy car rented by a member for 1 day.
-
Economy car rented by a member for 2 days.
-
SUV rented by a non-member for 1 day.
-
SUV rented by a non-member for 2 days.
-
SUV rented by a member for 1 day.
-
SUV rented by a member for 2 days.
-
Luxury car rented by a non-member for 1 day.
-
Luxury car rented by a non-member for 2 days.
-
Luxury car rented by a member for 1 day.
-
Luxury car rented by a member for 2 days.
Robust Equivalence Class Testing
involves testing with both valid and 'just outside' invalid inputs.
• In our car rental example, the valid inputs are:
-
Type of car: Economy, SUV, or Luxury.
-
Duration of rental: A positive integer for rental days.
-
Membership status: Whether the customer is a member or not.
• And the invalid inputs could be:
-
Type of car: Any type other than Economy, SUV, or Luxury (e.g., compact, pickup).
-
Duration of rental: Non-positive integers (e.g., 0 or negative numbers).
-
Membership status: Any status other than member or non-member (e.g., pending).
23-24
Consider a function f(x1, x2) where the values of x1 and x2 are defined to be:
a <= x1 <= b and c<= x2<=d
Assume the equivalence classes for x1 is {a, a+1, ..., ta}, {ta+1, ..., tb}, {tb+1, tb+2, ..., b} and the equivalence classes for x2 is {c, c+1, ..., tc}, {tc+1, tc+2, ..., td}, {td+1, td+2, ..., d}.
- In weak normal equivalence class testing, what is the minimum number of test cases? (1 mark)
3
- Using graphical representation, show the minimum test cases one could generate using weak normal equivalence class testing. (3 marks)

- Instrong normal equivalence class testing, how many test cases are generated? (1 mark)
9
-
Explain in detail why a weak normal equivalence class testing generates less test cases compare to a strong normal equivalence class testing? (6 marks)
a weak normal equivalence Cover each valid equivalence class at least once.
a strong normal equivalence Test all combinations of valid equivalence classes. -
List the equivalence classes of x1 and x2 for robustness testing. (2 marks)
Valid Equivalence Classes
X1: V1 {a, a+1, ..., ta}, V2{ta+1, ..., tb}, V3{tb+1, tb+2, ..., b}
X2: V4 {c, c+1, ..., tc}, V5{tc+1, tc+2, ..., td}, V6{td+1, td+2, ..., d}
Invalid Equivalence Classes
X1: IV1{values < a},IV2{values > b}
X2:IV3{values < c},IV4{values > d}
- Using graphical representation, show the minimum test cases you could generate using weak robust equivalence class testing. (4 marks)

- Using graphical representation, show the test cases you could generate using strong robust equivalence class testing. (3 marks)

20-21
A store in the city offers different discounts depending on the purchases made by the individual. The discount goes as follow, purchases of 0.1 up to 50.99 have no discount, purchases over 51 and up to 200.99 have a 5% discount, and purchases of 201 and up to 500.99 have 10% discounts, and purchases of $501 and above have 15% discounts. To check if the software calculates the discounts correctly according to the ranges of purchase values, what valid input partitions would you use?
output equivalence classes
0.1 up to 50.99 - no discount
question 2
Consider a function f(x1, x2) where the values of x1 and x2 are defined to be 1000 <= x1 <=10000 and 10-year <= x2 <= 50-year.
Assume the equivalence classes for x1 and x2 are: -
x1
V1 = [1000 to 5000]
V2 = [5001 to 10000]
x2
V3 = [10-year to 19-year]
V4 = [20-year to 29-year]
V5 = [30-year to 50-year]
Using graphical representation, show the minimum test cases one could generate using weak normal equivalence class testing.
| Test Case | x₁ Value (from) | x₂ Value (from) |
|---|---|---|
| TC1 | V₁ (e.g., 2000) | V₃ (e.g., 15) |
| TC2 | V₂ (e.g., 8000) | V₄ (e.g., 25) |
| TC3 | V₁ (e.g., 3000) | V₅ (e.g., 45) |
共需测试 3 个用例,每个等价类被至少覆盖一次。
Why a strong normal equivalence class testing generates more test cases compare to a weak normal equivalence class testing?
a strong normal equivalence Test all combinations of valid equivalence classes.
a weak normal equivalence Cover each valid equivalence class at least once.
List the equivalence classes of x1 and x2 for robustness testing.
Valid Equivalence Classes(已知):
x₁: V₁ = [1000 -- 5000], V₂ = [5001 -- 10000]
x₂: V₃ = [10 -- 19], V₄ = [20 -- 29], V₅ = [30 -- 50]
Invalid Equivalence Classes:
x₁:
IV₁: [<1000]
IV₂: [>10000]
x₂:
IV₃: [<10]
IV₄: [>50]
Using graphical representation, show the minimum test cases you could generate using the weak robust equivalence class testing.
| Test Case | x₁ | x₂ | 来源 |
|---|---|---|---|
| TC1 | 2000 | 15 | V₁ × V₃ |
| TC2 | 8000 | 25 | V₂ × V₄ |
| TC3 | 3000 | 45 | V₁ × V₅ |
| TC4 | 900 | 15 | IV₁ × V₃ |
| TC5 | 11000 | 25 | IV₂ × V₄ |
| TC6 | 2000 | 5 | V₁ × IV₃ |
| TC7 | 3000 | 60 | V₁ × IV₄ |
Decision Table Based Testing
Question 3
Consider an online e-commerce platform that calculates shipping costs based on three factors: the type of item being shipped (Fragile or Non-Fragile) , the chosen shipping method (Standard, Express, or Overnight) , and thetotal order price (Below 50, 50-100, Above 100).
The rules for shipping costs are as follows:
- Standard shipping costs 5 for Non-Fragile items and 10 for Fragile items.
- Express shipping costs 10 for Non-Fragile items and 15 for Fragile items.
- Overnight shipping costs 20 for Non-Fragile items and 25 for Fragile items.
- Orders below 50 incur an additional handling fee of 5, regardless of item type or shipping method.
- Orders between 50 and 100 have no additional fees.
- Orders above $100 get free shipping, regardless of item type or shipping method.
Create a decision table to represent the logic of this system and describe how you would convert this decision table into test cases for the e-commerce platform.
Answer
|-----------------|----------|---------|---------|-------------|-------------|-------------|--------|
| | Case 1 | Case 2 | Case 3 | Case 4 | Case 5 | Case 6 | Case 7 |
| Item Type | Fragile | Fragile | Fragile | Non-Fragile | Non-Fragile | Non-Fragile | - |
| Shipping Method | Standard | Exp | ON | Standard | Exp | ON | - |
| Order Price | <50 | \<50 | <50 | \<50 | <50 | \<50 | >100 |
| Shipping Fee | 10 | 15 | 25 | 5 | 10 | 20 | 0 |
| Handling Fee | 5 | 5 | 5 | 5 | 5 | 5 | 0 |
| Total | 15 | 20 | 30 | 10 | 15 | $25 | |
|-----------------|----------|---------|---------|-------------|-------------|-------------|
| | Case 8 | Case 9 | Case 10 | Case 11 | Case 12 | Case 13 |
| Item Type | Fragile | Fragile | Fragile | Non-Fragile | Non-Fragile | Non-Fragile |
| Shipping Method | Standard | Exp | ON | Standard | Exp | ON |
| Order Price | 50-100 | 50-100 | 50-100 | 50-100 | 50-100 | 50-100 |
| Shipping Fee | 10 | 15 | 25 | 5 | 10 | 20 |
| Handling Fee | 0 | 0 | 0 | 0 | 0 | 0 |
| Total | 10 | 15 | 25 | 5 | 10 | 20 |
Week11 P72
Example
Consider a function f(x1,x2) where the values of x1 and x2 are defined to be
a <= x1 <= b and c <= x2 <= d
• When both input values x1 and x2 are within their ranges (defined in the condition stubs), compute y value (described in the action stubs).
• In all other situations, output an error message
sol
这里是一般情况

however, in all other situations, output an error message

'--' indicates "don't care"
条件精细化拆分(下方更复杂表格)

White-box testing
Lecture 1

Tutorial 12

The above is a binary search function written in C language. Answer the following questions base on the code.
Question 1
Draw a control flow graph corresponding to the preceding function.

Question 2 (感觉不太可能考)
For the preceding function, derive a set of test cases that will cover branch testing.
Answer
|--------|-----------------------------------------|-----------------------------------------------|
| | Path | Test Case |
| P1 | 1-2-3-5-13 | arraysize = 3, searchkey = b, array = abc |
| P2 | 1-2-4-5-13 | arraysize = 0, searchkey = a |
| P3 | 1-2-4-5-6-7-8-12-5-13 | impossible |
| P4 | 1-2-4-5-6-7-9-10-12-5-6-7-8-12-5-13 | arraysize = 3, searchkey = a, array = abc |
| P5 | 1-2-4-5-6-7-9-11-12-5-6-7-8-12-5-13 | arraysize = 3, searchkey = c, array = abc |
Question 3 (感觉不太可能考)
Design additional test cases that will cover multiple-condition testing.
Answer
According to while (bot <= top && !found), Multiple-condition testing is as follows
(条件来自代码片段的判断:while (bot <= top && !found),表示循环继续的两个条件:bot <= top 和 !found)
|-----------------|-------------|-----------------------------------------------|
| bot <= top | ! found | Test Case |
| T | T | arraysize = 3, searchkey = a, array = abc |
| T | F | arraysize = 3, searchkey = b, array = abc |
| F | T | arraysize = 3, searchkey = d, array = abc |
| F | F | impossible |
ps. 这里注意
| 判断语句 | 是否多条件测试考虑点 | 说明 |
|---|---|---|
while(bot <= top && !found) |
是 | 多条件测试关注的复合条件 |
if(array[mid] == searchKey) |
否(单条件判断) | 只需单条件测试,关注条件真/假 |
Question 4
Determine the cyclomatic complexity of the preceding function.
Answer
V(G) = e -- n + 2p = 16 -13 + 2 = 5
edge = 16
node = 13
p = 1
Question 5 (感觉不太可能考)
Derive a set of test cases that cover McCabe's Basis Paths.
Answer
|-------------------|-------------------------------------------------------|---------------------------------------------------|
| | Path | Test Case |
| P1 | 1-2-4-5-6-7-9-10-12-5-6-7-9-11-12-5-6-7-8-12-5-13 | arraysize = 7, searchkey = e, array = abcdefg |
| P2: Flip at 2 | 1-2-3-5-6-7-9-10-12-5-6-7-9-11-12-5-6-7-8-12-5-13 | impossible |
| P3: Flip at 5 | 1-2-4-5-13 | arraysize = 0, searchkey = a |
| P4: Flip at 7 | 1-2-4-5-6-7-8-12-5-6-7-9-11-12-5-6-7-8-12-5-13 | impossible |
| P5: Flip at 9 | 1-2-4-5-6-7-9-11-12-5-6-7-9-11-12-5-6-7-8-12-5-13 | arraysize = 7, searchkey = a, array = abcdefg |