1.操作步骤
用户名:admin
密码:Admin@123
新密码:Huawei@123
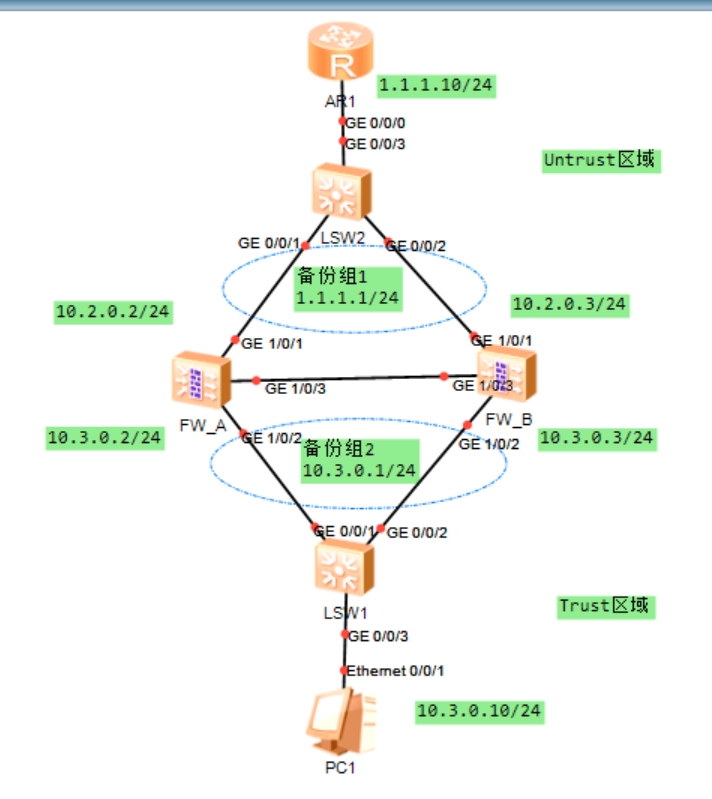
步骤1:配置防火墙网络的基本参数
(1)配置防火墙接口IP地址
防火墙A
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.2.0.2 255.255.255.0
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.2 255.255.255.0
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.10.0.1 255.255.255.252防火墙B(这里咱们可以直接修改A的配置然后粘贴到防火墙B中运行即可)
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.2.0.3 255.255.255.0
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.3 255.255.255.0
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.10.0.2 255.255.255.252(2)将接口加入安全区域
防火墙A
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/3防火墙B
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/3(3)设置默认路由
防火墙A、B
ip route-static 0.0.0.0 0 1.1.1.10步骤2:配置双击热备主备备份
(1)配置VRRP备份组(防火墙A设置为active,防火墙B设置为standby)
防火墙A
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.2.0.2 255.255.255.0
vrrp vrid 1 virtual-ip 1.1.1.1 255.255.255.0 active
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.2 255.255.255.0
vrrp vrid 2 virtual-ip 10.3.0.1 active防火墙B
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.2.0.2 255.255.255.0
vrrp vrid 1 virtual-ip 1.1.1.1 255.255.255.0 standby
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.2 255.255.255.0
vrrp vrid 2 virtual-ip 10.3.0.1 standby(2)指定心跳接口并启用双击热备功能
防火墙A
hrp inter g 1/0/3 remote 10.10.0.2
hrp enable防火墙B
hrp inter g 1/0/3 remote 10.10.0.1
hrp enable步骤3:配置安全策略(只需配置防火墙A,策略会自动备份到防火墙B中)
security-policy
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.255.0
action permit步骤4:配置NAT(只需配置防火墙A,策略会自动备份到防火墙B中)
(1)配置NAT地址池
nat address-group group01 0
mode pat
route enable
section 0 1.1.1.11 1.1.1.20(2)配置NAT策略
nat-policy
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.255.0
action source-nat address-group group01步骤5:配置路由器
(1)配置路由器R1的接口IP地址
interface GigabitEthernet0/0/0
ip address 1.1.1.10 255.255.255.0
interface LoopBack0
ip address 2.2.2.2 255.255.255.255 (2)配置默认路由
ip route-static 10.3.0.0 24 1.1.1.1步骤6:配置交换机和内网终端
(1)配置交换机VLAN
交换机1(vlan 3)
vlan batch 3
interface GigabitEthernet0/0/1
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 3交换机2(vlan 2)
vlan batch 2
interface GigabitEthernet0/0/1
port link-type access
port default vlan 2
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 2
#
interface GigabitEthernet0/0/3
port link-type access
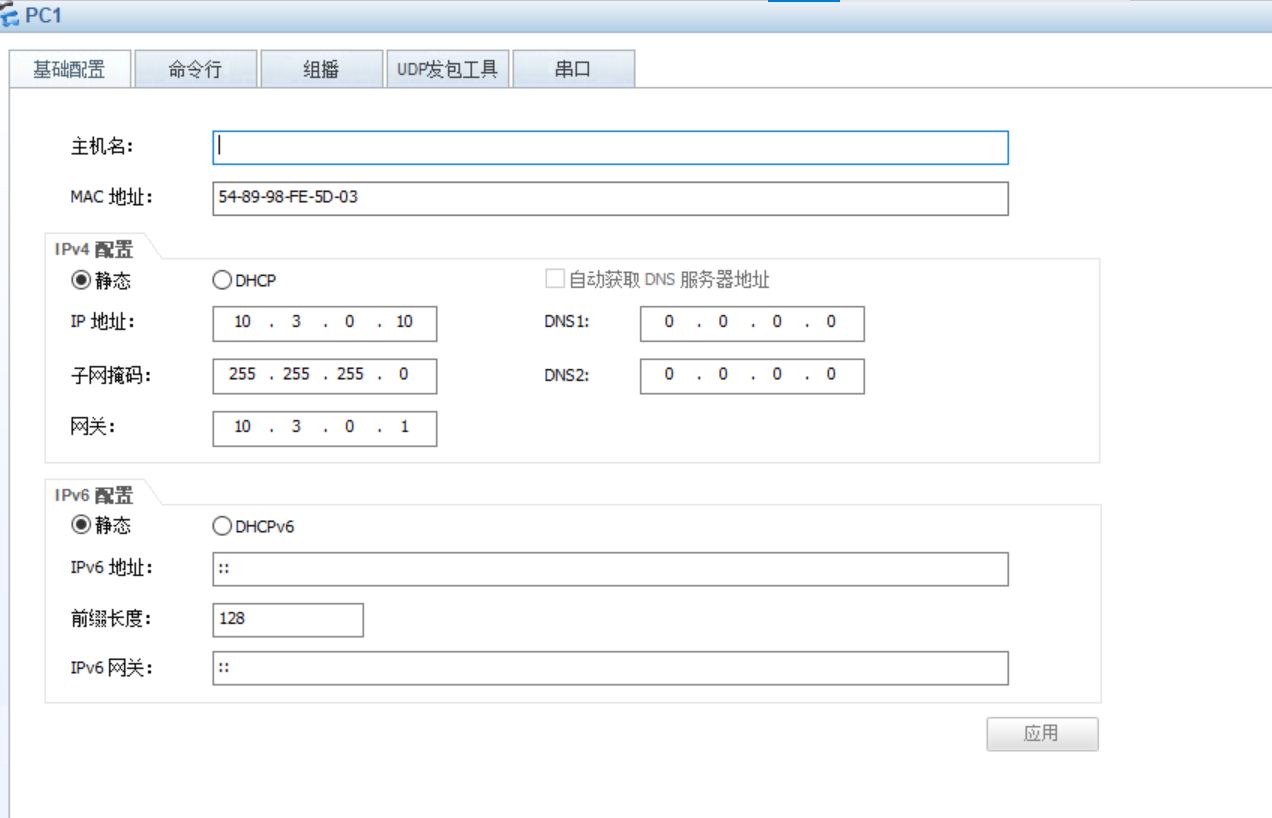
port default vlan 2(2)配置内网主机的网络参数
2.所有配置
2.1 防火墙A
2024-04-01 04:07:16.430
!Software Version V500R005C10SPC300
#
sysname USG6000V1
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
hrp enable
hrp interface GigabitEthernet1/0/3 remote 10.10.0.2
#
update schedule location-sdb weekly Sun 00:41
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 06:58
update schedule av-sdb daily 06:58
update schedule sa-sdb daily 06:58
update schedule cnc daily 06:58
update schedule file-reputation daily 06:58
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%bQO[W~6U+3a_#jH=8h/&+cZoy\]zIv|,'~avU,5gheL*cZr+@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%D<Du*bM;j-simMD!QcV3@9i/SVk5;q]os)28bZ8oAH#V9i2@@%@%
level 15
manager-user admin
password cipher @%@%ub8%>qVGN&TFNwV#37T$K`55&H_y18!\\+A)a63_,j2I`58K@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.2.0.2 255.255.255.0
vrrp vrid 1 virtual-ip 1.1.1.1 255.255.255.0 active
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.2 255.255.255.0
vrrp vrid 2 virtual-ip 10.3.0.1 active
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.10.0.1 255.255.255.252
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/3
#
ip route-static 0.0.0.0 0.0.0.0 1.1.1.10
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
nat address-group group01 0
mode pat
route enable
section 0 1.1.1.11 1.1.1.20
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.255.0
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.255.0
action source-nat address-group group01
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return2.2 防火墙B
2024-04-01 04:09:43.320
!Software Version V500R005C10SPC300
#
sysname USG6000V1
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
hrp enable
hrp interface GigabitEthernet1/0/3 remote 10.10.0.1
#
update schedule location-sdb weekly Sun 00:57
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 03:25
update schedule av-sdb daily 03:25
update schedule sa-sdb daily 03:25
update schedule cnc daily 03:25
update schedule file-reputation daily 03:25
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%mP$t!]$4])5jt|=X$O^/Xk$|S"O+&d}uF5Y%O7T,2\X>k$"X@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%W$k|O1{h6SU+H{3`'<(&_zm`eL2c4=f,'4ROt#2|w%w&zmc_@%@%
level 15
manager-user admin
password cipher @%@%9bc@-D"ccG=!J*4!c<>IKAU(Wh-e9'nBFDD~J$Q>*uO#AU+K@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.2.0.2 255.255.255.0
vrrp vrid 1 virtual-ip 1.1.1.1 255.255.255.0 standby
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.3.0.2 255.255.255.0
vrrp vrid 2 virtual-ip 10.3.0.1 standby
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.10.0.2 255.255.255.252
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/3
#
ip route-static 0.0.0.0 0.0.0.0 1.1.1.10
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return2.3 路由器AR1
[V200R003C00]
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Ethernet0/0/0
#
interface Ethernet0/0/1
#
interface Ethernet0/0/2
#
interface Ethernet0/0/3
#
interface Ethernet0/0/4
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface GigabitEthernet0/0/0
ip address 1.1.1.10 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface NULL0
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
ip route-static 10.3.0.0 255.255.255.0 1.1.1.1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return2.4 SW1
sysname Huawei
#
vlan batch 3
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 3
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
return2.5 SW2
#
sysname Huawei
#
vlan batch 2
#
cluster enable
ntdp enable
ndp enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 2
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 2
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 2
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
user-interface con 0
user-interface vty 0 4
#
return