以仙盟之规,护代码之界
服务运维

在东方仙盟的世界观里,修仙者筑道基、炼金丹、渡天劫,每一步都需抵御心魔入侵、妖兽袭扰;而在代码的世界中,开发者写项目、搭框架、上生产,同样要防范 SQL 注入、高危函数滥用等「无形之刃」。
今天要讲的玄元安全探针,便是一款融合「仙盟防御之术」与「现代科技之法」的工具 ------ 它没有华丽的三方依赖,却能像仙盟的「巡天真人」一般,悄无声息地扫描 PHP 环境与数据库的安全隐患,为你的代码世界筑牢第一道「安全结界」。
检测代码
<?php
header("Content-Type: text/html; charset=utf-8");
$msg = []; // 检测结果信息
$phpCheck = []; // PHP 检测结果
$mysqlCheck = []; // MySQL 检测结果
$sqlsrvCheck = []; // SQL Server 检测结果
// ==================== 1. PHP 高危函数检测 ====================
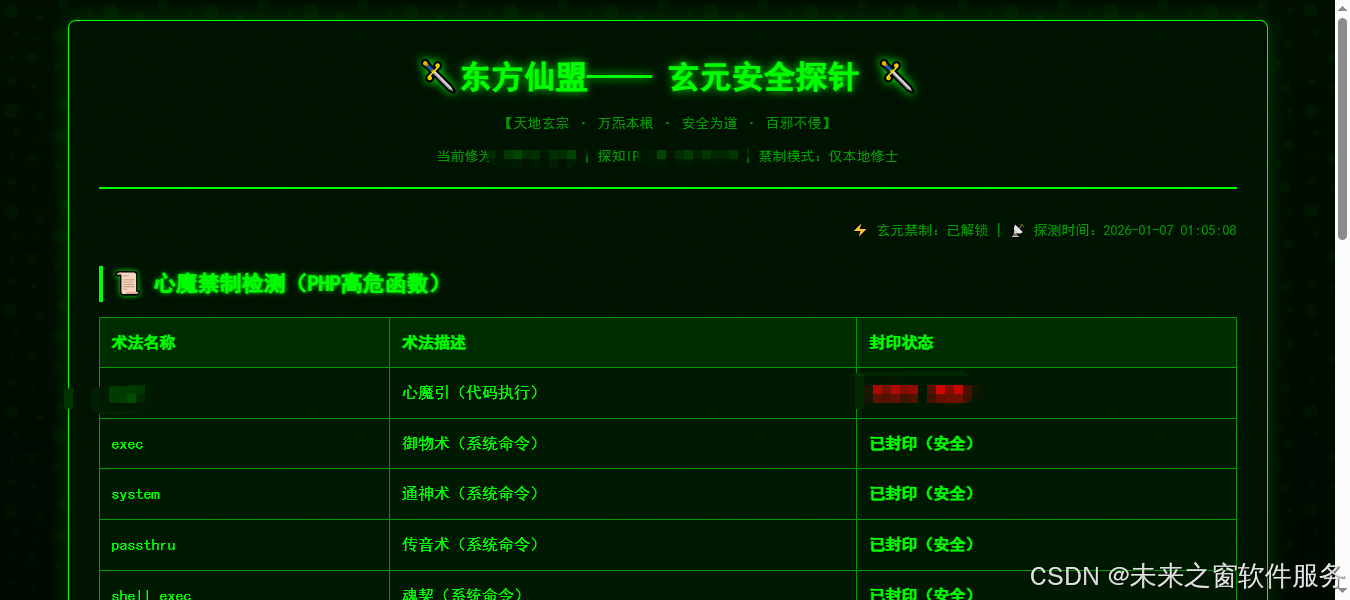
$danger_functions = [
'eval' => '代码执行',
'exec' => '系统命令执行',
'system' => '系统命令执行',
'passthru' => '系统命令执行',
'shell_exec' => '系统命令执行',
'proc_open' => '进程创建',
'popen' => '管道进程创建',
'assert' => '代码执行'
];
foreach ($danger_functions as $func => $desc) {
$disabled = in_array($func, explode(',', ini_get('disable_functions')));
$phpCheck[] = [
'func' => $func,
'desc' => $desc,
'status' => $disabled ? '已禁用(安全)' : '未禁用(高危)',
'color' => $disabled ? '#4CAF50' : '#F44336'
];
}
// ==================== 2. 接收表单提交 & 数据库检测 ====================
if ($_POST) {
$db_type = $_POST['db_type'] ?? '';
$db_host = $_POST['db_host'] ?? '127.0.0.1';
$db_port = $_POST['db_port'] ?? '';
$db_user = $_POST['db_user'] ?? '';
$db_pwd = $_POST['db_pwd'] ?? '';
// 2.1 MySQL 检测
if ($db_type == 'mysql') {
$db_port = $db_port ?: 3306;
// 检测 MySQL 扩展是否存在
if (!function_exists('mysqli_connect') && !function_exists('mysql_connect')) {
$mysqlCheck[] = ['title' => '扩展状态', 'value' => '未开启 MySQL 扩展,无法检测'];
} else {
// 连接数据库(兼容 mysqli/mysql)
$conn = function_exists('mysqli_connect')
? mysqli_connect($db_host, $db_user, $db_pwd, '', $db_port)
: mysql_connect("{$db_host}:{$db_port}", $db_user, $db_pwd);
if (!$conn) {
$mysqlCheck[] = ['title' => '连接状态', 'value' => '连接失败:' . (function_exists('mysqli_error') ? mysqli_error($conn) : mysql_error())];
} else {
// 检测 secure_file_priv 配置(无执行风险,只读查询)
$query = function_exists('mysqli_query')
? mysqli_query($conn, "SHOW VARIABLES LIKE 'secure_file_priv'")
: mysql_query("SHOW VARIABLES LIKE 'secure_file_priv'", $conn);
$row = function_exists('mysqli_fetch_assoc')
? mysqli_fetch_assoc($query)
: mysql_fetch_assoc($query);
$priv_value = $row['Value'] ?? '未知';
$priv_status = $priv_value === NULL ? '完全禁用(最安全)' : ($priv_value === '' ? '高危:允许任意路径读写' : "可控:仅允许 {$priv_value} 路径读写");
$mysqlCheck[] = ['title' => '文件读写权限(secure_file_priv)', 'value' => $priv_status];
// 检测 UDF 危险函数
$udf_query = function_exists('mysqli_query')
? mysqli_query($conn, "SELECT COUNT(*) as cnt FROM mysql.func WHERE name IN ('sys_exec','sys_eval')")
: mysql_query("SELECT COUNT(*) as cnt FROM mysql.func WHERE name IN ('sys_exec','sys_eval')", $conn);
$udf_row = function_exists('mysqli_fetch_assoc')
? mysqli_fetch_assoc($udf_query)
: mysql_fetch_assoc($udf_query);
$udf_cnt = $udf_row['cnt'] ?? 0;
$mysqlCheck[] = ['title' => '危险 UDF 函数数量', 'value' => $udf_cnt > 0 ? "发现 {$udf_cnt} 个高危 UDF,建议删除" : '无危险 UDF(安全)'];
// 关闭连接
function_exists('mysqli_close') ? mysqli_close($conn) : mysql_close($conn);
}
}
}
// 2.2 SQL Server 检测(仅检测扩展和连接,无高危查询)
if ($db_type == 'sqlsrv') {
if (!function_exists('sqlsrv_connect')) {
$sqlsrvCheck[] = ['title' => '扩展状态', 'value' => '未开启 sqlsrv 扩展,无法检测'];
} else {
$connectionInfo = ["UID" => $db_user, "PWD" => $db_pwd, "Database" => "master"];
$conn = sqlsrv_connect($db_host, $connectionInfo);
if (!$conn) {
$errors = sqlsrv_errors();
$error_msg = $errors[0]['message'] ?? '未知错误';
$sqlsrvCheck[] = ['title' => '连接状态', 'value' => "连接失败:{$error_msg}"];
} else {
$sqlsrvCheck[] = ['title' => '连接状态', 'value' => '连接成功'];
$sqlsrvCheck[] = ['title' => '扩展状态', 'value' => 'sqlsrv 扩展正常'];
sqlsrv_close($conn);
}
}
}
}
?>
<!DOCTYPE html>
<html lang="zh-CN">
<head>
<meta charset="UTF-8">
<title>未来之窗 - 安全探针工具</title>
<style>
* {margin: 0; padding: 0; box-sizing: border-box;}
body {padding: 20px; font-family: Arial, sans-serif; background: #f5f5f5;}
.container {max-width: 1000px; margin: 0 auto; background: #fff; padding: 30px; border-radius: 8px; box-shadow: 0 2px 10px rgba(0,0,0,0.1);}
h1 {text-align: center; color: #333; margin-bottom: 30px;}
h2 {color: #444; margin: 20px 0 15px; padding-bottom: 5px; border-bottom: 1px solid #eee;}
table {width: 100%; border-collapse: collapse; margin: 10px 0;}
th, td {padding: 10px; border: 1px solid #ddd; text-align: left;}
th {background: #f8f8f8;}
.form-group {margin: 15px 0;}
label {display: inline-block; width: 100px; font-weight: bold;}
input {padding: 8px; width: 250px; border: 1px solid #ddd; border-radius: 4px;}
select {padding: 8px; width: 250px; border: 1px solid #ddd; border-radius: 4px;}
button {padding: 10px 20px; background: #2196F3; color: #fff; border: none; border-radius: 4px; cursor: pointer;}
button:hover {background: #1976D2;}
.msg {padding: 10px; margin: 10px 0; border-radius: 4px;}
.success {background: #e8f5e9; color: #4CAF50;}
.danger {background: #ffebee; color: #F44336;}
.warning {background: #fff8e1; color: #FF9800;}
</style>
</head>
<body>
<div class="container">
<h1>未来之窗 - 系统安全探针</h1>
<!-- PHP 高危函数检测区 -->
<h2>一、PHP 高危函数状态检测</h2>
<table>
<tr>
<th>函数名</th>
<th>函数用途</th>
<th>状态</th>
</tr>
<?php foreach ($phpCheck as $item): ?>
<tr>
<td><?php echo $item['func']; ?></td>
<td><?php echo $item['desc']; ?></td>
<td style="color: <?php echo $item['color']; ?>"><?php echo $item['status']; ?></td>
</tr>
<?php endforeach; ?>
</table>
<!-- 数据库检测表单 -->
<h2>二、数据库安全配置检测</h2>
<form method="post">
<div class="form-group">
<label>数据库类型:</label>
<select name="db_type" required>
<option value="mysql">MySQL</option>
<option value="sqlsrv">SQL Server</option>
</select>
</div>
<div class="form-group">
<label>主机地址:</label>
<input type="text" name="db_host" value="127.0.0.1" required>
</div>
<div class="form-group">
<label>端口号:</label>
<input type="text" name="db_port" placeholder="MySQL默认3306,SQLServer默认1433">
</div>
<div class="form-group">
<label>用户名:</label>
<input type="text" name="db_user" required>
</div>
<div class="form-group">
<label>密码:</label>
<input type="password" name="db_pwd">
</div>
<div class="form-group">
<label> </label>
<button type="submit">开始检测</button>
</div>
</form>
<!-- MySQL 检测结果 -->
<?php if (!empty($mysqlCheck)): ?>
<h2>三、MySQL 检测结果</h2>
<table>
<tr>
<th>检测项</th>
<th>结果</th>
</tr>
<?php foreach ($mysqlCheck as $item): ?>
<tr>
<td><?php echo $item['title']; ?></td>
<td><?php echo $item['value']; ?></td>
</tr>
<?php endforeach; ?>
</table>
<?php endif; ?>
<!-- SQL Server 检测结果 -->
<?php if (!empty($sqlsrvCheck)): ?>
<h2>三、SQL Server 检测结果</h2>
<table>
<tr>
<th>检测项</th>
<th>结果</th>
</tr>
<?php foreach ($sqlsrvCheck as $item): ?>
<tr>
<td><?php echo $item['title']; ?></td>
<td><?php echo $item['value']; ?></td>
</tr>
<?php endforeach; ?>
</table>
<?php endif; ?>
</div>
</body>
</html>阿雪技术观
在科技发展浪潮中,我们不妨积极投身技术共享。不满足于做受益者,更要主动担当贡献者。无论是分享代码、撰写技术博客,还是参与开源项目维护改进,每一个微小举动都可能蕴含推动技术进步的巨大能量。东方仙盟是汇聚力量的天地,我们携手在此探索硅基生命,为科技进步添砖加瓦。
Hey folks, in this wild tech - driven world, why not dive headfirst into the whole tech - sharing scene? Don't just be the one reaping all the benefits; step up and be a contributor too. Whether you're tossing out your code snippets, hammering out some tech blogs, or getting your hands dirty with maintaining and sprucing up open - source projects, every little thing you do might just end up being a massive force that pushes tech forward. And guess what? The Eastern FairyAlliance is this awesome place where we all come together. We're gonna team up and explore the whole silicon - based life thing, and in the process, we'll be fueling the growth of technology