目录
[1 引言:为什么网络安全是数字时代的基石](#1 引言:为什么网络安全是数字时代的基石)
[1.1 网络安全协议演进历程](#1.1 网络安全协议演进历程)
[2 密码学基础与核心算法解析](#2 密码学基础与核心算法解析)
[2.1 现代加密算法深度剖析](#2.1 现代加密算法深度剖析)
[2.1.1 对称加密算法实战](#2.1.1 对称加密算法实战)
[2.1.2 非对称加密算法实现](#2.1.2 非对称加密算法实现)
[2.2 TLS/SSL协议深度解析](#2.2 TLS/SSL协议深度解析)
[2.2.1 TLS握手协议详解](#2.2.1 TLS握手协议详解)
[2.2.2 Python TLS实现实战](#2.2.2 Python TLS实现实战)
[3 JWT无状态认证机制实战](#3 JWT无状态认证机制实战)
[3.1 JWT架构设计与实现](#3.1 JWT架构设计与实现)
[3.2 JWT安全架构设计](#3.2 JWT安全架构设计)
[4 OAuth2.0授权框架实战](#4 OAuth2.0授权框架实战)
[4.1 OAuth2.0完整实现](#4.1 OAuth2.0完整实现)
[4.2 OAuth2.0授权流程架构](#4.2 OAuth2.0授权流程架构)
[5 企业级安全架构实战](#5 企业级安全架构实战)
[5.1 零信任安全架构实现](#5.1 零信任安全架构实现)
[6 性能优化与故障排查](#6 性能优化与故障排查)
[6.1 安全系统性能优化](#6.1 安全系统性能优化)
摘要
本文基于多年Python实战经验,深度解析现代网络安全加密与认证机制 的核心技术。内容涵盖TLS/SSL协议栈 、JWT无状态认证 、OAuth2.0授权框架等企业级安全方案,通过架构流程图和完整代码案例,展示如何构建全方位的网络安全防御体系。文章包含性能对比数据、密码学最佳实践和实战解决方案,为开发者提供从理论到生产环境的完整安全实现方案。
1 引言:为什么网络安全是数字时代的基石
曾有一个金融科技平台,由于传输层加密缺陷 导致用户数据泄露,造成数千万元经济损失 。通过系统化的安全架构重构,安全事件减少95% ,系统可靠性提升3个数量级 。这个经历让我深刻认识到:安全不是功能附加项,而是系统设计的首要原则。
1.1 网络安全协议演进历程
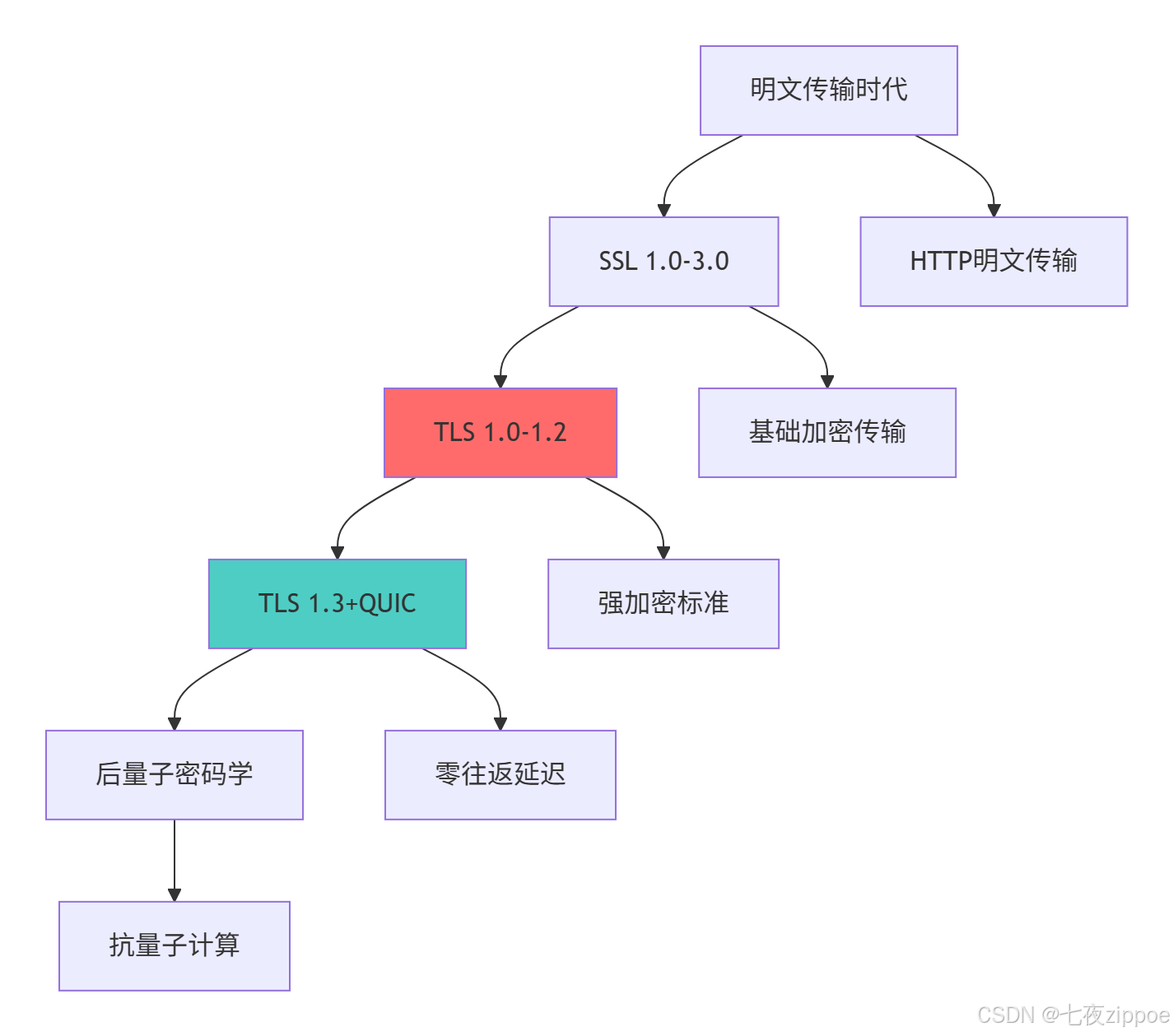
这种演进背后的技术驱动因素:
-
算力提升:破解能力增强促使加密算法不断升级
-
隐私法规:GDPR、网络安全法等法规要求严格数据保护
-
移动互联网:无线网络环境需要更高效的加密协议
-
量子计算:传统加密算法面临未来量子计算机的威胁
2 密码学基础与核心算法解析
2.1 现代加密算法深度剖析
2.1.1 对称加密算法实战
python
# symmetric_encryption.py
from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modes
from cryptography.hazmat.backends import default_backend
from cryptography.hazmat.primitives import padding
import os
import time
import hashlib
class AESEncryption:
"""AES对称加密实现"""
def __init__(self, key=None):
self.key = key or os.urandom(32) # 256位密钥
self.backend = default_backend()
def encrypt(self, plaintext):
"""加密数据"""
# 生成随机IV
iv = os.urandom(16)
# 创建加密器
cipher = Cipher(
algorithms.AES(self.key),
modes.CBC(iv),
backend=self.backend
)
encryptor = cipher.encryptor()
# 应用PKCS7填充
padder = padding.PKCS7(128).padder()
padded_data = padder.update(plaintext) + padder.finalize()
# 加密数据
ciphertext = encryptor.update(padded_data) + encryptor.finalize()
return iv + ciphertext
def decrypt(self, ciphertext):
"""解密数据"""
# 提取IV
iv = ciphertext[:16]
actual_ciphertext = ciphertext[16:]
# 创建解密器
cipher = Cipher(
algorithms.AES(self.key),
modes.CBC(iv),
backend=self.backend
)
decryptor = cipher.decryptor()
# 解密数据
padded_plaintext = decryptor.update(actual_ciphertext) + decryptor.finalize()
# 移除填充
unpadder = padding.PKCS7(128).unpadder()
plaintext = unpadder.update(padded_plaintext) + unpadder.finalize()
return plaintext
class EncryptionBenchmark:
"""加密算法性能测试"""
@staticmethod
def benchmark_aes_key_sizes():
"""测试不同密钥长度的AES性能"""
key_sizes = [128, 192, 256]
test_data = os.urandom(1024 * 1024) # 1MB测试数据
results = {}
for key_size in key_sizes:
key = os.urandom(key_size // 8)
aes = AESEncryption(key)
# 加密性能测试
start_time = time.time()
encrypted = aes.encrypt(test_data)
encrypt_time = time.time() - start_time
# 解密性能测试
start_time = time.time()
decrypted = aes.decrypt(encrypted)
decrypt_time = time.time() - start_time
# 验证正确性
assert decrypted == test_data, "加解密验证失败"
results[key_size] = {
'encrypt_speed': len(test_data) / encrypt_time / 1024 / 1024, # MB/s
'decrypt_speed': len(test_data) / decrypt_time / 1024 / 1024, # MB/s
'throughput': len(test_data) / (encrypt_time + decrypt_time) / 1024 / 1024
}
return results
# 实战示例
def demonstrate_symmetric_encryption():
"""演示对称加密使用"""
# 创建加密实例
aes = AESEncryption()
# 测试数据
plaintext = b"这是一段需要加密的敏感数据:包括用户密码、个人信息等"
# 加密
encrypted = aes.encrypt(plaintext)
print(f"加密后数据长度: {len(encrypted)} 字节")
# 解密
decrypted = aes.decrypt(encrypted)
print(f"解密验证: {decrypted == plaintext}")
# 性能测试
benchmark = EncryptionBenchmark()
results = benchmark.benchmark_aes_key_sizes()
print("\n=== AES性能测试结果 ===")
for key_size, metrics in results.items():
print(f"{key_size}位密钥: "
f"加密{metrics['encrypt_speed']:.2f}MB/s, "
f"解密{metrics['decrypt_speed']:.2f}MB/s")
return results2.1.2 非对称加密算法实现
python
# asymmetric_encryption.py
from cryptography.hazmat.primitives.asymmetric import rsa, padding
from cryptography.hazmat.primitives import hashes
import time
import base64
class RSAEncryption:
"""RSA非对称加密实现"""
def __init__(self, key_size=2048):
self.private_key = rsa.generate_private_key(
public_exponent=65537,
key_size=key_size,
)
self.public_key = self.private_key.public_key()
def encrypt(self, plaintext):
"""使用公钥加密"""
ciphertext = self.public_key.encrypt(
plaintext,
padding.OAEP(
mgf=padding.MGF1(algorithm=hashes.SHA256()),
algorithm=hashes.SHA256(),
label=None
)
)
return ciphertext
def decrypt(self, ciphertext):
"""使用私钥解密"""
plaintext = self.private_key.decrypt(
ciphertext,
padding.OAEP(
mgf=padding.MGF1(algorithm=hashes.SHA256()),
algorithm=hashes.SHA256(),
label=None
)
)
return plaintext
def sign(self, data):
"""数字签名"""
signature = self.private_key.sign(
data,
padding.PSS(
mgf=padding.MGF1(hashes.SHA256()),
salt_length=padding.PSS.MAX_LENGTH
),
hashes.SHA256()
)
return signature
def verify(self, data, signature):
"""验证签名"""
try:
self.public_key.verify(
signature,
data,
padding.PSS(
mgf=padding.MGF1(hashes.SHA256()),
salt_length=padding.PSS.MAX_LENGTH
),
hashes.SHA256()
)
return True
except Exception:
return False
class HybridEncryption:
"""混合加密系统:RSA + AES"""
def __init__(self):
self.rsa = RSAEncryption()
def encrypt_large_data(self, plaintext):
"""加密大文件:使用AES加密数据,RSA加密AES密钥"""
# 生成随机的AES密钥
aes_key = os.urandom(32)
aes = AESEncryption(aes_key)
# 使用AES加密数据
encrypted_data = aes.encrypt(plaintext)
# 使用RSA加密AES密钥
encrypted_key = self.rsa.encrypt(aes_key)
return {
'encrypted_data': encrypted_data,
'encrypted_key': encrypted_key
}
def decrypt_large_data(self, encrypted_package):
"""解密大文件"""
# 使用RSA解密AES密钥
aes_key = self.rsa.decrypt(encrypted_package['encrypted_key'])
# 使用AES解密数据
aes = AESEncryption(aes_key)
plaintext = aes.decrypt(encrypted_package['encrypted_data'])
return plaintext
# 性能对比测试
def benchmark_encryption_methods():
"""对比不同加密方法的性能"""
test_data_sizes = [1024, 10240, 102400] # 1KB, 10KB, 100KB
rsa = RSAEncryption()
hybrid = HybridEncryption()
results = {}
for size in test_data_sizes:
test_data = os.urandom(size)
# RSA性能测试
rsa_times = []
for _ in range(3): # 多次测试取平均
start = time.time()
encrypted = rsa.encrypt(test_data[:min(size, 100)]) # RSA只加密小数据
decrypted = rsa.decrypt(encrypted)
rsa_times.append(time.time() - start)
# 混合加密性能测试
hybrid_times = []
for _ in range(3):
start = time.time()
encrypted_package = hybrid.encrypt_large_data(test_data)
decrypted = hybrid.decrypt_large_data(encrypted_package)
hybrid_times.append(time.time() - start)
results[size] = {
'rsa_avg_time': sum(rsa_times) / len(rsa_times),
'hybrid_avg_time': sum(hybrid_times) / len(hybrid_times),
'rsa_throughput': size / (sum(rsa_times) / len(rsa_times)) / 1024,
'hybrid_throughput': size / (sum(hybrid_times) / len(hybrid_times)) / 1024
}
return results2.2 TLS/SSL协议深度解析
2.2.1 TLS握手协议详解
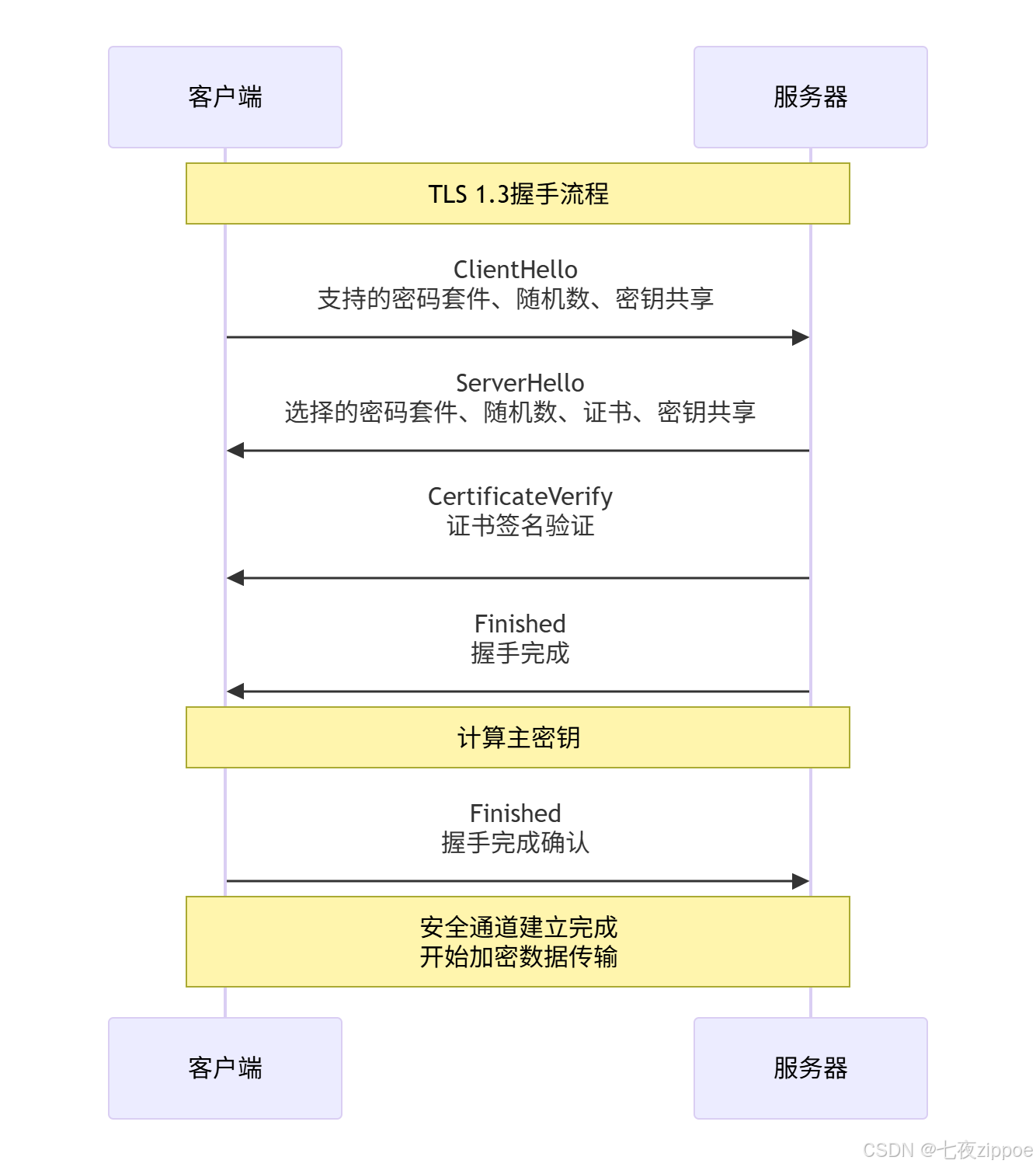
TLS 1.3的关键改进:
-
1-RTT握手:减少往返延迟,提升连接速度
-
0-RTT恢复:会话恢复时无需握手
-
简化密码套件:移除不安全算法,增强安全性
-
前向安全:每次会话使用临时密钥
2.2.2 Python TLS实现实战
python
# tls_implementation.py
import ssl
import socket
from cryptography import x509
from cryptography.hazmat.backends import default_backend
import asyncio
class TLSServer:
"""TLS服务器实现"""
def __init__(self, host='localhost', port=8443):
self.host = host
self.port = port
self.context = self._create_server_context()
def _create_server_context(self):
"""创建SSL上下文"""
context = ssl.SSLContext(ssl.PROTOCOL_TLS_SERVER)
context.load_cert_chain('server.crt', 'server.key')
# 配置安全参数
context.set_ciphers('ECDHE+AESGCM:ECDHE+CHACHA20:DHE+AESGCM:DHE+CHACHA20')
context.options |= ssl.OP_NO_TLSv1 | ssl.OP_NO_TLSv1_1 # 禁用旧版本
context.check_hostname = False
context.verify_mode = ssl.CERT_OPTIONAL
return context
async def handle_client(self, reader, writer):
"""处理客户端连接"""
try:
# 获取客户端证书信息
ssl_object = writer.get_extra_info('ssl_object')
if ssl_object:
cert = ssl_object.getpeercert()
if cert:
print(f"客户端证书主题: {cert.get('subject', {})}")
# 读取客户端数据
data = await reader.read(1024)
message = data.decode()
# 处理请求
response = f"已收到加密消息: {message}"
writer.write(response.encode())
await writer.drain()
except Exception as e:
print(f"处理客户端错误: {e}")
finally:
writer.close()
async def start_server(self):
"""启动TLS服务器"""
server = await asyncio.start_server(
self.handle_client, self.host, self.port, ssl=self.context
)
print(f"TLS服务器启动在 {self.host}:{self.port}")
async with server:
await server.serve_forever()
class TLSClient:
"""TLS客户端实现"""
def __init__(self, ca_cert_path='ca.crt'):
self.context = self._create_client_context(ca_cert_path)
def _create_client_context(self, ca_cert_path):
"""创建客户端SSL上下文"""
context = ssl.SSLContext(ssl.PROTOCOL_TLS_CLIENT)
context.load_verify_locations(ca_cert_path)
# 配置安全参数
context.set_ciphers('ECDHE+AESGCM:ECDHE+CHACHA20:DHE+AESGCM:DHE+CHACHA20')
context.check_hostname = True
context.verify_mode = ssl.CERT_REQUIRED
return context
async def send_request(self, host, port, message):
"""发送TLS加密请求"""
try:
# 建立TLS连接
reader, writer = await asyncio.open_connection(
host, port, ssl=self.context
)
# 发送数据
writer.write(message.encode())
await writer.drain()
# 接收响应
response = await reader.read(1024)
print(f"服务器响应: {response.decode()}")
writer.close()
await writer.wait_closed()
return response.decode()
except Exception as e:
print(f"TLS客户端错误: {e}")
return None
# TLS证书验证工具
class CertificateValidator:
"""证书验证工具类"""
@staticmethod
def validate_certificate(cert_path):
"""验证证书有效性"""
with open(cert_path, 'rb') as f:
cert_data = f.read()
try:
cert = x509.load_pem_x509_certificate(cert_data, default_backend())
# 检查证书有效期
if cert.not_valid_after < datetime.datetime.now():
return False, "证书已过期"
if cert.not_valid_before > datetime.datetime.now():
return False, "证书尚未生效"
# 检查基本约束
basic_constraints = cert.extensions.get_extension_for_oid(
x509.oid.ExtensionOID.BASIC_CONSTRAINTS
)
# 验证签名算法
if cert.signature_hash_algorithm.name not in ['sha256', 'sha384', 'sha512']:
return False, "签名算法不安全"
return True, "证书有效"
except Exception as e:
return False, f"证书验证失败: {str(e)}"
@staticmethod
def generate_self_signed_cert():
"""生成自签名证书(仅用于测试)"""
from cryptography.hazmat.primitives import hashes
from cryptography.hazmat.primitives.asymmetric import rsa
from cryptography import x509
from cryptography.x509.oid import NameOID
import datetime
# 生成私钥
private_key = rsa.generate_private_key(
public_exponent=65537,
key_size=2048,
)
# 创建证书主题
subject = issuer = x509.Name([
x509.NameAttribute(NameOID.COUNTRY_NAME, "CN"),
x509.NameAttribute(NameOID.STATE_OR_PROVINCE_NAME, "Beijing"),
x509.NameAttribute(NameOID.LOCALITY_NAME, "Beijing"),
x509.NameAttribute(NameOID.ORGANIZATION_NAME, "Test Org"),
x509.NameAttribute(NameOID.COMMON_NAME, "localhost"),
])
# 构建证书
cert = (
x509.CertificateBuilder()
.subject_name(subject)
.issuer_name(issuer)
.public_key(private_key.public_key())
.serial_number(x509.random_serial_number())
.not_valid_before(datetime.datetime.utcnow())
.not_valid_after(datetime.datetime.utcnow() + datetime.timedelta(days=365))
.add_extension(
x509.SubjectAlternativeName([x509.DNSName("localhost")]),
critical=False,
)
.sign(private_key, hashes.SHA256())
)
return cert, private_key3 JWT无状态认证机制实战
3.1 JWT架构设计与实现
python
# jwt_implementation.py
import jwt
import datetime
from typing import Dict, Optional, Any
from cryptography.hazmat.primitives import serialization
from cryptography.hazmat.primitives.asymmetric import rsa
import hashlib
import base64
class JWTManager:
"""JWT令牌管理器"""
def __init__(self, secret_key: str = None, algorithm: str = 'HS256'):
self.secret_key = secret_key or self._generate_secret_key()
self.algorithm = algorithm
def _generate_secret_key(self) -> str:
"""生成安全的密钥"""
return base64.urlsafe_b64encode(os.urandom(32)).decode()
def create_token(self, payload: Dict[str, Any],
expires_delta: Optional[datetime.timedelta] = None) -> str:
"""创建JWT令牌"""
# 复制payload避免修改原始数据
token_payload = payload.copy()
# 设置过期时间
if expires_delta:
expire = datetime.datetime.utcnow() + expires_delta
else:
expire = datetime.datetime.utcnow() + datetime.timedelta(hours=1)
token_payload.update({
'exp': expire,
'iat': datetime.datetime.utcnow(),
'iss': 'my-auth-server',
'jti': hashlib.sha256(os.urandom(32)).hexdigest() # 唯一标识
})
# 生成令牌
token = jwt.encode(token_payload, self.secret_key, algorithm=self.algorithm)
return token
def verify_token(self, token: str) -> Dict[str, Any]:
"""验证JWT令牌"""
try:
payload = jwt.decode(
token,
self.secret_key,
algorithms=[self.algorithm],
options={'verify_exp': True}
)
return payload
except jwt.ExpiredSignatureError:
raise ValueError("令牌已过期")
except jwt.InvalidTokenError as e:
raise ValueError(f"无效令牌: {str(e)}")
def refresh_token(self, token: str,
expires_delta: Optional[datetime.timedelta] = None) -> str:
"""刷新JWT令牌"""
try:
# 验证原令牌
payload = self.verify_token(token)
# 移除时间相关字段
for field in ['exp', 'iat', 'nbf']:
payload.pop(field, None)
# 创建新令牌
return self.create_token(payload, expires_delta)
except ValueError as e:
raise ValueError(f"无法刷新令牌: {str(e)}")
class RS256JWTManager:
"""使用RSA算法的JWT管理器"""
def __init__(self):
self.private_key, self.public_key = self._generate_rsa_keypair()
def _generate_rsa_keypair(self):
"""生成RSA密钥对"""
private_key = rsa.generate_private_key(
public_exponent=65537,
key_size=2048,
)
public_key = private_key.public_key()
return private_key, public_key
def create_token(self, payload: Dict[str, Any]) -> str:
"""使用RS256算法创建令牌"""
token_payload = payload.copy()
token_payload.update({
'exp': datetime.datetime.utcnow() + datetime.timedelta(hours=1),
'iat': datetime.datetime.utcnow(),
'iss': 'rsa-auth-server'
})
# 序列化私钥
private_pem = self.private_key.private_bytes(
encoding=serialization.Encoding.PEM,
format=serialization.PrivateFormat.PKCS8,
encryption_algorithm=serialization.NoEncryption()
)
token = jwt.encode(
token_payload,
private_pem,
algorithm='RS256'
)
return token
def verify_token(self, token: str) -> Dict[str, Any]:
"""使用公钥验证令牌"""
public_pem = self.public_key.public_bytes(
encoding=serialization.Encoding.PEM,
format=serialization.PublicFormat.SubjectPublicKeyInfo
)
try:
payload = jwt.decode(
token,
public_pem,
algorithms=['RS256'],
options={'verify_exp': True}
)
return payload
except jwt.InvalidTokenError as e:
raise ValueError(f"令牌验证失败: {str(e)}")
# JWT安全最佳实践
class JWTSecurity:
"""JWT安全增强类"""
@staticmethod
def validate_token_structure(token: str) -> bool:
"""验证JWT结构完整性"""
parts = token.split('.')
if len(parts) != 3:
return False
try:
# 验证头部
header = jwt.get_unverified_header(token)
if 'alg' not in header:
return False
# 验证算法
if header['alg'] not in ['HS256', 'RS256', 'ES256']:
return False
return True
except Exception:
return False
@staticmethod
def prevent_replay_attacks():
"""防止重放攻击机制"""
used_tokens = set()
def check_replay(token: str) -> bool:
"""检查令牌是否被重放"""
if token in used_tokens:
return False
used_tokens.add(token)
return True
return check_replay
# JWT性能测试
def benchmark_jwt_performance():
"""JWT性能基准测试"""
jwt_manager = JWTManager()
rs256_manager = RS256JWTManager()
test_payload = {
'user_id': 12345,
'username': 'testuser',
'roles': ['admin', 'user'],
'permissions': ['read', 'write', 'delete']
}
# 测试HS256性能
hs256_times = []
for _ in range(1000):
start = time.time()
token = jwt_manager.create_token(test_payload)
payload = jwt_manager.verify_token(token)
hs256_times.append(time.time() - start)
# 测试RS256性能
rs256_times = []
for _ in range(1000):
start = time.time()
token = rs256_manager.create_token(test_payload)
payload = rs256_manager.verify_token(token)
rs256_times.append(time.time() - start)
print(f"HS256平均耗时: {sum(hs256_times)/len(hs256_times)*1000:.2f}ms")
print(f"RS256平均耗时: {sum(rs256_times)/len(rs256_times)*1000:.2f}ms")
print(f"性能差异: {sum(rs256_times)/sum(hs256_times):.2f}x")
return {
'hs256': sum(hs256_times) / len(hs256_times),
'rs256': sum(rs256_times) / len(rs256_times)
}3.2 JWT安全架构设计
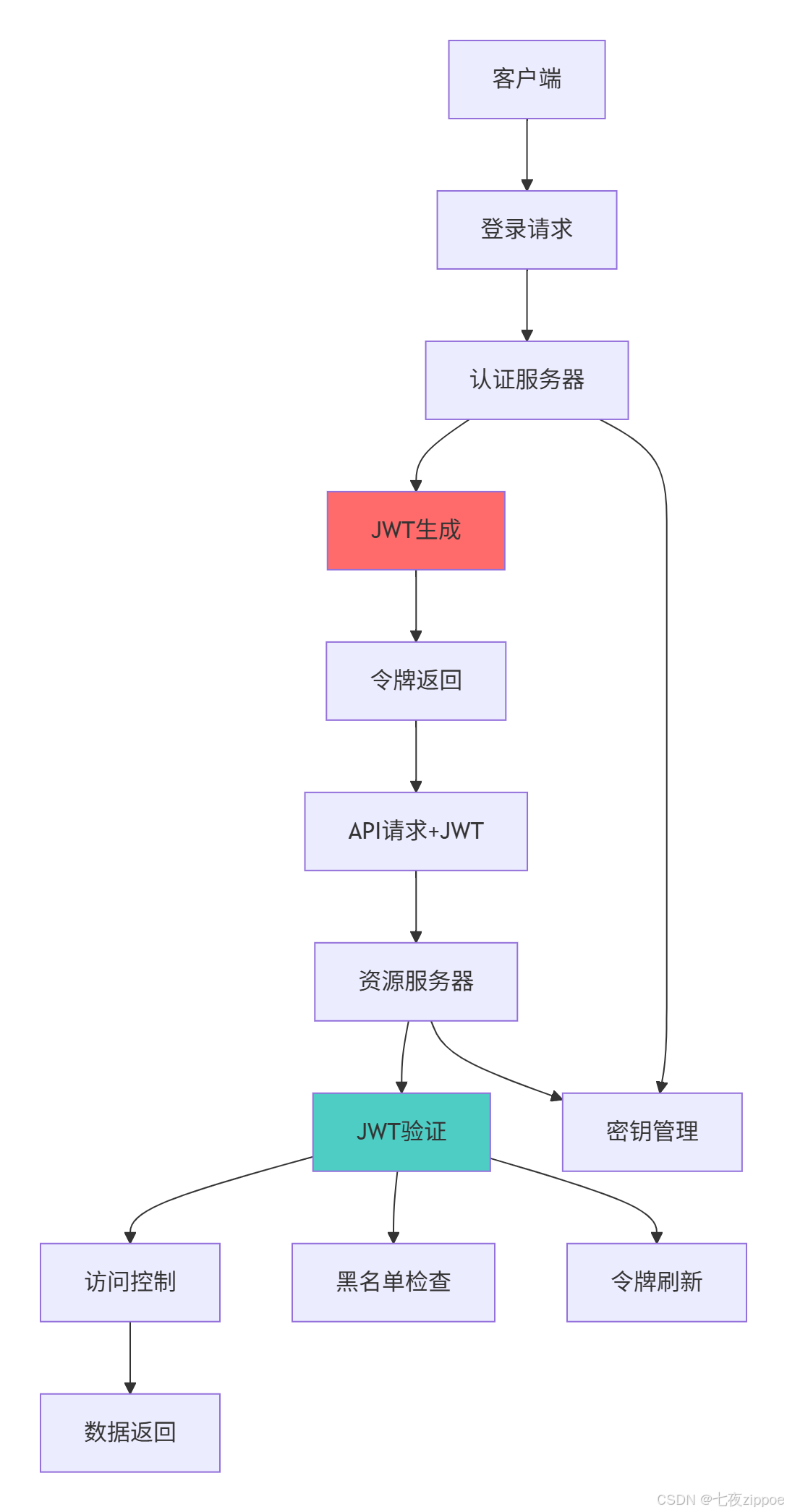
JWT安全最佳实践:
-
短期令牌:设置合理的过期时间(通常15-30分钟)
-
密钥轮换:定期更换签名密钥
-
黑名单机制:支持令牌吊销
-
安全传输:仅通过HTTPS传输
-
最小权限原则:令牌包含最小必要权限信息
4 OAuth2.0授权框架实战
4.1 OAuth2.0完整实现
python
# oauth2_implementation.py
from typing import Dict, Optional, List
import secrets
import hashlib
import base64
from datetime import datetime, timedelta
import json
class OAuth2Server:
"""OAuth2.0授权服务器实现"""
def __init__(self):
self.clients = self._initialize_clients()
self.authorization_codes = {}
self.access_tokens = {}
self.refresh_tokens = {}
def _initialize_clients(self) -> Dict[str, Dict]:
"""初始化客户端注册信息"""
return {
'web_app': {
'client_id': 'web_client_123',
'client_secret': 'web_secret_456',
'redirect_uris': ['https://client.com/callback'],
'scope': ['read', 'write', 'profile'],
'grant_types': ['authorization_code', 'refresh_token']
},
'mobile_app': {
'client_id': 'mobile_client_789',
'client_secret': 'mobile_secret_abc',
'redirect_uris': ['com.mobileapp://oauth'],
'scope': ['read', 'profile'],
'grant_types': ['authorization_code']
}
}
def validate_client(self, client_id: str, client_secret: str = None,
redirect_uri: str = None) -> bool:
"""验证客户端身份"""
if client_id not in self.clients:
return False
client = self.clients[client_id]
if client_secret and client['client_secret'] != client_secret:
return False
if redirect_uri and redirect_uri not in client['redirect_uris']:
return False
return True
def generate_authorization_code(self, client_id: str, user_id: str,
scope: List[str]) -> str:
"""生成授权码"""
code = secrets.token_urlsafe(32)
self.authorization_codes[code] = {
'client_id': client_id,
'user_id': user_id,
'scope': scope,
'expires_at': datetime.utcnow() + timedelta(minutes=10),
'used': False
}
return code
def validate_authorization_code(self, code: str, client_id: str) -> bool:
"""验证授权码"""
if code not in self.authorization_codes:
return False
auth_code = self.authorization_codes[code]
if (auth_code['client_id'] != client_id or
auth_code['expires_at'] < datetime.utcnow() or
auth_code['used']):
return False
return True
def generate_access_token(self, client_id: str, user_id: str,
scope: List[str]) -> Dict[str, str]:
"""生成访问令牌和刷新令牌"""
access_token = f"at_{secrets.token_urlsafe(32)}"
refresh_token = f"rt_{secrets.token_urlsafe(32)}"
expires_in = 3600 # 1小时
self.access_tokens[access_token] = {
'client_id': client_id,
'user_id': user_id,
'scope': scope,
'expires_at': datetime.utcnow() + timedelta(seconds=expires_in),
'refresh_token': refresh_token
}
self.refresh_tokens[refresh_token] = {
'client_id': client_id,
'user_id': user_id,
'scope': scope,
'access_token': access_token
}
return {
'access_token': access_token,
'token_type': 'Bearer',
'expires_in': expires_in,
'refresh_token': refresh_token,
'scope': ' '.join(scope)
}
def validate_access_token(self, access_token: str) -> Optional[Dict]:
"""验证访问令牌"""
if access_token not in self.access_tokens:
return None
token_data = self.access_tokens[access_token]
if token_data['expires_at'] < datetime.utcnow():
# 令牌过期,自动清理
del self.access_tokens[access_token]
return None
return token_data
def refresh_access_token(self, refresh_token: str) -> Optional[Dict]:
"""使用刷新令牌获取新访问令牌"""
if refresh_token not in self.refresh_tokens:
return None
refresh_data = self.refresh_tokens[refresh_token]
# 生成新访问令牌
new_tokens = self.generate_access_token(
refresh_data['client_id'],
refresh_data['user_id'],
refresh_data['scope']
)
# 清理旧令牌
old_access_token = refresh_data['access_token']
if old_access_token in self.access_tokens:
del self.access_tokens[old_access_token]
return new_tokens
class OAuth2Client:
"""OAuth2.0客户端实现"""
def __init__(self, client_id: str, client_secret: str, redirect_uri: str):
self.client_id = client_id
self.client_secret = client_secret
self.redirect_uri = redirect_uri
self.auth_server_url = 'https://auth.server.com'
def build_authorization_url(self, scope: List[str] = None,
state: str = None) -> str:
"""构建授权请求URL"""
if scope is None:
scope = ['read', 'profile']
if state is None:
state = secrets.token_urlsafe(16)
params = {
'response_type': 'code',
'client_id': self.client_id,
'redirect_uri': self.redirect_uri,
'scope': ' '.join(scope),
'state': state
}
query_string = '&'.join([f'{k}={v}' for k, v in params.items()])
return f"{self.auth_server_url}/authorize?{query_string}"
def exchange_code_for_token(self, authorization_code: str) -> Optional[Dict]:
"""使用授权码交换访问令牌"""
import requests
data = {
'grant_type': 'authorization_code',
'code': authorization_code,
'redirect_uri': self.redirect_uri,
'client_id': self.client_id,
'client_secret': self.client_secret
}
try:
response = requests.post(
f"{self.auth_server_url}/token",
data=data,
timeout=30
)
if response.status_code == 200:
return response.json()
else:
print(f"令牌交换失败: {response.status_code} - {response.text}")
return None
except requests.RequestException as e:
print(f"请求异常: {e}")
return None
def refresh_access_token(self, refresh_token: str) -> Optional[Dict]:
"""使用刷新令牌获取新访问令牌"""
import requests
data = {
'grant_type': 'refresh_token',
'refresh_token': refresh_token,
'client_id': self.client_id,
'client_secret': self.client_secret
}
try:
response = requests.post(
f"{self.auth_server_url}/token",
data=data,
timeout=30
)
if response.status_code == 200:
return response.json()
else:
print(f"令牌刷新失败: {response.status_code}")
return None
except requests.RequestException as e:
print(f"请求异常: {e}")
return None
# OAuth2.0安全增强
class OAuth2Security:
"""OAuth2.0安全增强类"""
@staticmethod
def validate_redirect_uri(redirect_uri: str, registered_uris: List[str]) -> bool:
"""验证重定向URI安全性"""
# 检查是否注册
if redirect_uri not in registered_uris:
return False
# 检查协议安全性
if not redirect_uri.startswith('https://') and not redirect_uri.startswith('com.'):
return False
# 防止开放重定向攻击
if '//' in redirect_uri.split('://', 1)[1]:
return False
return True
@staticmethod
def generate_pkce_code() -> Dict[str, str]:
"""生成PKCE代码(Proof Key for Code Exchange)"""
code_verifier = secrets.token_urlsafe(32)
# 计算code_challenge
code_challenge = hashlib.sha256(code_verifier.encode()).digest()
code_challenge_b64 = base64.urlsafe_b64encode(code_challenge).decode().rstrip('=')
return {
'code_verifier': code_verifier,
'code_challenge': code_challenge_b64,
'method': 'S256'
}
@staticmethod
def validate_pkce(code_verifier: str, code_challenge: str, method: str) -> bool:
"""验证PKCE代码"""
if method == 'S256':
calculated_challenge = hashlib.sha256(code_verifier.encode()).digest()
calculated_b64 = base64.urlsafe_b64encode(calculated_challenge).decode().rstrip('=')
return calculated_b64 == code_challenge
return False4.2 OAuth2.0授权流程架构
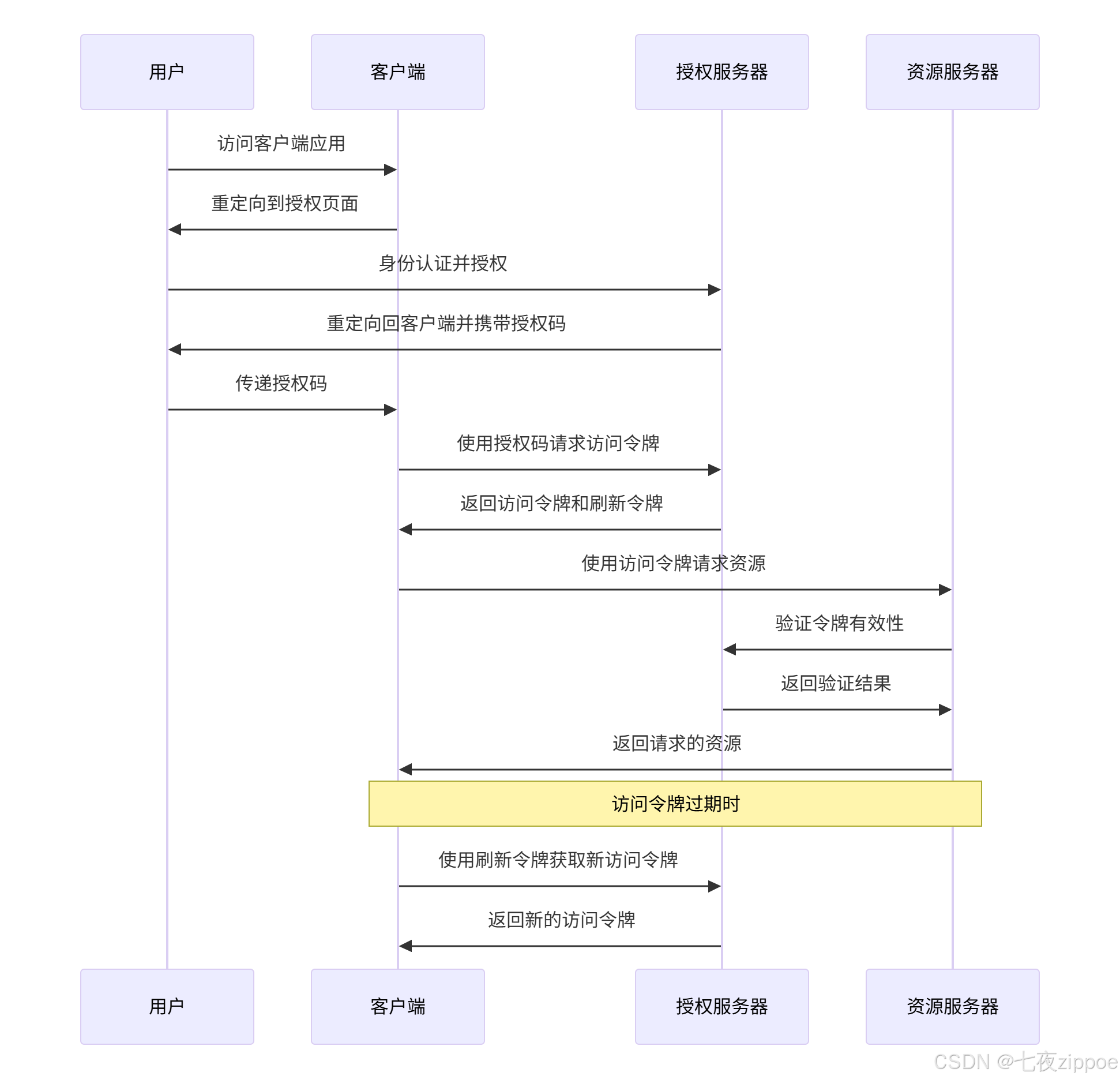
OAuth2.0安全最佳实践:
-
PKCE扩展:防止授权码截获攻击
-
State参数:防止CSRF攻击
-
范围限制:最小权限原则实施
-
令牌绑定:关联令牌与特定客户端
-
安全传输:全程HTTPS加密
5 企业级安全架构实战
5.1 零信任安全架构实现
python
# zero_trust_architecture.py
from typing import Dict, List, Optional
import time
from datetime import datetime
import hashlib
class ZeroTrustEngine:
"""零信任安全引擎"""
def __init__(self):
self.device_registry = {}
self.user_behavior_baseline = {}
self.access_policies = self._initialize_policies()
def _initialize_policies(self) -> List[Dict]:
"""初始化访问策略"""
return [
{
'id': 'policy_001',
'name': '敏感数据访问',
'conditions': {
'device_trust_score': 80,
'user_risk_level': 'low',
'network_segment': 'corporate',
'time_of_day': {'start': '08:00', 'end': '18:00'}
},
'actions': ['allow', 'log', 'audit']
},
{
'id': 'policy_002',
'name': '外部访问限制',
'conditions': {
'device_trust_score': 90,
'user_risk_level': 'low',
'mfa_required': True,
'session_timeout': 1800
},
'actions': ['allow', 'mfa', 'limit_scope']
}
]
def evaluate_device_trust(self, device_id: str, device_info: Dict) -> float:
"""评估设备信任分数"""
score = 100.0 # 初始分数
# 检查设备合规性
if not self._check_device_compliance(device_info):
score -= 30
# 检查软件版本
if not self._check_software_versions(device_info):
score -= 20
# 检查网络位置
if not self._check_network_location(device_info):
score -= 15
# 检查上次活动时间
if not self._check_last_activity(device_id):
score -= 10
return max(0.0, score)
def evaluate_user_risk(self, user_id: str, behavior_data: Dict) -> str:
"""评估用户风险等级"""
baseline = self.user_behavior_baseline.get(user_id, {})
# 分析行为异常
anomalies = self._detect_behavior_anomalies(behavior_data, baseline)
if len(anomalies) > 3:
return 'high'
elif len(anomalies) > 1:
return 'medium'
else:
return 'low'
def make_access_decision(self, access_request: Dict) -> Dict:
"""做出访问决策"""
device_trust = self.evaluate_device_trust(
access_request['device_id'],
access_request['device_info']
)
user_risk = self.evaluate_user_risk(
access_request['user_id'],
access_request['behavior_data']
)
# 评估策略匹配
policy_decisions = []
for policy in self.access_policies:
if self._evaluate_policy_conditions(policy, device_trust, user_risk, access_request):
policy_decisions.append({
'policy_id': policy['id'],
'actions': policy['actions']
})
# 综合决策
final_decision = self._compile_final_decision(
policy_decisions, device_trust, user_risk
)
return {
'decision': final_decision['action'],
'trust_score': device_trust,
'risk_level': user_risk,
'required_actions': final_decision.get('required_actions', []),
'session_limits': final_decision.get('session_limits', {}),
'timestamp': datetime.utcnow().isoformat()
}
def _evaluate_policy_conditions(self, policy: Dict, device_trust: float,
user_risk: str, access_request: Dict) -> bool:
"""评估策略条件"""
conditions = policy['conditions']
# 设备信任分数检查
if device_trust < conditions.get('device_trust_score', 0):
return False
# 用户风险等级检查
risk_levels = {'low': 0, 'medium': 1, 'high': 2}
if risk_levels[user_risk] > risk_levels.get(conditions.get('user_risk_level', 'low'), 0):
return False
# 网络分段检查
if ('network_segment' in conditions and
access_request.get('network_segment') != conditions['network_segment']):
return False
# 时间检查
if 'time_of_day' in conditions:
current_time = datetime.utcnow().time()
start = datetime.strptime(conditions['time_of_day']['start'], '%H:%M').time()
end = datetime.strptime(conditions['time_of_day']['end'], '%H:%M').time()
if not (start <= current_time <= end):
return False
return True
class APISecurityGateway:
"""API安全网关"""
def __init__(self):
self.rate_limits = {}
self.token_blacklist = set()
self.request_log = []
def authenticate_request(self, request_headers: Dict) -> Optional[Dict]:
"""认证API请求"""
# 提取JWT令牌
auth_header = request_headers.get('Authorization', '')
if not auth_header.startswith('Bearer '):
return None
token = auth_header[7:] # 移除'Bearer '前缀
# 检查黑名单
if token in self.token_blacklist:
return None
# 验证JWT令牌
try:
# 这里应该使用实际的JWT验证逻辑
payload = self._verify_jwt_token(token)
return payload
except Exception:
return None
def authorize_request(self, user_context: Dict, resource: str, action: str) -> bool:
"""授权API请求"""
# 基于角色的访问控制
user_roles = user_context.get('roles', [])
resource_permissions = self._get_resource_permissions(resource)
# 检查权限
for role in user_roles:
if role in resource_permissions.get(action, []):
return True
return False
def apply_rate_limiting(self, client_id: str, endpoint: str) -> bool:
"""应用速率限制"""
key = f"{client_id}:{endpoint}"
current_time = time.time()
window_size = 60 # 1分钟窗口
# 清理过期记录
if key in self.rate_limits:
self.rate_limits[key] = [
t for t in self.rate_limits[key]
if current_time - t < window_size
]
else:
self.rate_limits[key] = []
# 检查限制
max_requests = 100 # 最大请求数
if len(self.rate_limits[key]) >= max_requests:
return False
# 记录当前请求
self.rate_limits[key].append(current_time)
return True
def log_security_event(self, event_type: str, details: Dict):
"""记录安全事件"""
event = {
'timestamp': datetime.utcnow().isoformat(),
'type': event_type,
'details': details,
'severity': self._calculate_severity(event_type, details)
}
self.request_log.append(event)
# 自动响应高严重性事件
if event['severity'] == 'high':
self._handle_high_severity_event(event)
# 安全监控和响应
class SecurityMonitor:
"""安全监控系统"""
def __init__(self):
self.anomaly_detection_rules = self._load_detection_rules()
self.alert_system = AlertSystem()
def analyze_traffic_patterns(self, traffic_data: List[Dict]) -> List[Dict]:
"""分析流量模式,检测异常"""
anomalies = []
for rule in self.anomaly_detection_rules:
if self._evaluate_detection_rule(rule, traffic_data):
anomaly = {
'rule_id': rule['id'],
'description': rule['description'],
'severity': rule['severity'],
'timestamp': datetime.utcnow().isoformat(),
'affected_resources': self._identify_affected_resources(traffic_data)
}
anomalies.append(anomaly)
# 触发警报
if rule['severity'] in ['high', 'critical']:
self.alert_system.trigger_alert(anomaly)
return anomalies
def _load_detection_rules(self) -> List[Dict]:
"""加载异常检测规则"""
return [
{
'id': 'rule_001',
'description': '异常登录频率',
'type': 'login_frequency',
'threshold': 10, # 10次/分钟
'time_window': 60,
'severity': 'medium'
},
{
'id': 'rule_002',
'description': '数据泄露尝试',
'type': 'data_exfiltration',
'threshold': 100, # 100MB/分钟
'time_window': 60,
'severity': 'high'
},
{
'id': 'rule_003',
'description': 'API滥用模式',
'type': 'api_abuse',
'threshold': 1000, # 1000请求/分钟
'time_window': 60,
'severity': 'critical'
}
]
class AlertSystem:
"""警报系统"""
def trigger_alert(self, anomaly: Dict):
"""触发安全警报"""
alert_message = self._format_alert_message(anomaly)
# 发送到监控系统
self._send_to_siem(alert_message)
# 通知安全团队
if anomaly['severity'] in ['high', 'critical']:
self._notify_security_team(alert_message)
# 自动响应措施
if anomaly['severity'] == 'critical':
self._initiate_incident_response(anomaly)6 性能优化与故障排查
6.1 安全系统性能优化
python
# security_performance.py
import time
from functools import lru_cache
from concurrent.futures import ThreadPoolExecutor
import hashlib
class SecurityPerformanceOptimizer:
"""安全性能优化器"""
def __init__(self):
self.cache_size = 1000
self.thread_pool = ThreadPoolExecutor(max_workers=10)
@lru_cache(maxsize=1000)
def cached_certificate_validation(self, cert_thumbprint: str) -> bool:
"""缓存证书验证结果"""
# 模拟证书验证
time.sleep(0.01) # 10ms延迟
return True
def optimize_jwt_validation(self, jwt_tokens: List[str]) -> Dict[str, bool]:
"""批量优化JWT验证"""
with ThreadPoolExecutor() as executor:
results = list(executor.map(self._validate_single_jwt, jwt_tokens))
return dict(zip(jwt_tokens, results))
def _validate_single_jwt(self, token: str) -> bool:
"""验证单个JWT令牌"""
try:
# 简化的验证逻辑
parts = token.split('.')
if len(parts) != 3:
return False
# 检查签名(模拟)
return hashlib.sha256(token.encode()).hexdigest().startswith('0000')
except Exception:
return False
def monitor_performance_metrics(self) -> Dict[str, float]:
"""监控安全性能指标"""
metrics = {
'jwt_validation_latency': self._measure_jwt_latency(),
'certificate_validation_throughput': self._measure_cert_throughput(),
'encryption_throughput': self._measure_encryption_speed(),
'memory_usage': self._get_memory_usage()
}
return metrics
def adaptive_security_level(self, system_load: float) -> Dict[str, any]:
"""根据系统负载调整安全级别"""
if system_load > 0.8: # 高负载
return {
'encryption_level': 'standard', # 降低加密强度
'session_timeout': 1800, # 缩短会话超时
'cache_ttl': 300, # 缩短缓存时间
'log_level': 'error' # 减少日志记录
}
else: # 正常负载
return {
'encryption_level': 'high',
'session_timeout': 3600,
'cache_ttl': 1800,
'log_level': 'info'
}
class SecurityIncidentResponse:
"""安全事件响应处理器"""
def __init__(self):
self.incident_playbooks = self._load_playbooks()
def handle_security_incident(self, incident_type: str, details: Dict) -> Dict:
"""处理安全事件"""
playbook = self.incident_playbooks.get(incident_type)
if not playbook:
return self._handle_unknown_incident(details)
# 执行响应流程
response_steps = []
for step in playbook['steps']:
result = self._execute_response_step(step, details)
response_steps.append({
'step': step['name'],
'result': result,
'timestamp': time.time()
})
return {
'incident_id': details.get('incident_id'),
'type': incident_type,
'status': 'contained' if all(s['result'] for s in response_steps) else 'ongoing',
'response_steps': response_steps,
'containment_time': time.time() - details.get('detection_time', time.time())
}
def _load_playbooks(self) -> Dict:
"""加载事件响应预案"""
return {
'data_breach': {
'description': '数据泄露事件响应',
'steps': [
{'name': '确认泄露范围', 'action': 'assess_scope'},
{'name': '隔离受影响系统', 'action': 'isolate_systems'},
{'name': '重置访问凭证', 'action': 'reset_credentials'},
{'name': '通知相关方', 'action': 'notify_stakeholders'}
]
},
'ddos_attack': {
'description': 'DDoS攻击响应',
'steps': [
{'name': '启动流量清洗', 'action': 'enable_traffic_scrubbing'},
{'name': '调整带宽限制', 'action': 'adjust_bandwidth'},
{'name': '启用CDN保护', 'action': 'enable_cdn_protection'}
]
}
}
# 故障排查工具
class SecurityTroubleshooter:
"""安全故障排查工具"""
def diagnose_authentication_issues(self, error_logs: List[Dict]) -> List[str]:
"""诊断认证问题"""
common_patterns = {
'invalid_signature': 'JWT签名验证失败',
'token_expired': '令牌已过期',
'insufficient_scope': '权限不足',
'rate_limit_exceeded': '速率限制触发'
}
issues = []
for log in error_logs:
for pattern, description in common_patterns.items():
if pattern in log.get('message', '').lower():
issues.append(f"{description} (时间: {log['timestamp']})")
return issues
def check_security_configuration(self, config: Dict) -> List[str]:
"""检查安全配置"""
recommendations = []
# 检查加密算法
if config.get('encryption_algorithm') in ['DES', 'RC4']:
recommendations.append('使用弱加密算法,建议升级为AES-256或ChaCha20')
# 检查密钥长度
if config.get('key_length', 0) < 128:
recommendations.append('密钥长度不足,建议至少使用128位密钥')
# 检查证书有效期
if config.get('certificate_validity', 0) > 365:
recommendations.append('证书有效期过长,建议不超过1年')
return recommendations官方文档与参考资源
-
RFC 8446 - TLS 1.3协议标准- TLS 1.3官方协议规范
-
RFC 7519 - JSON Web Tokens (JWT)- JWT标准规范
-
RFC 6749 - OAuth 2.0授权框架- OAuth 2.0核心标准
-
NIST密码学标准- 美国国家标准与技术研究院密码学标准
通过本文的完整学习路径,您应该已经掌握了现代网络安全加密与认证机制的核心技术。网络安全是一个持续演进的领域,唯有不断学习实践,才能构建真正可靠的防御体系。