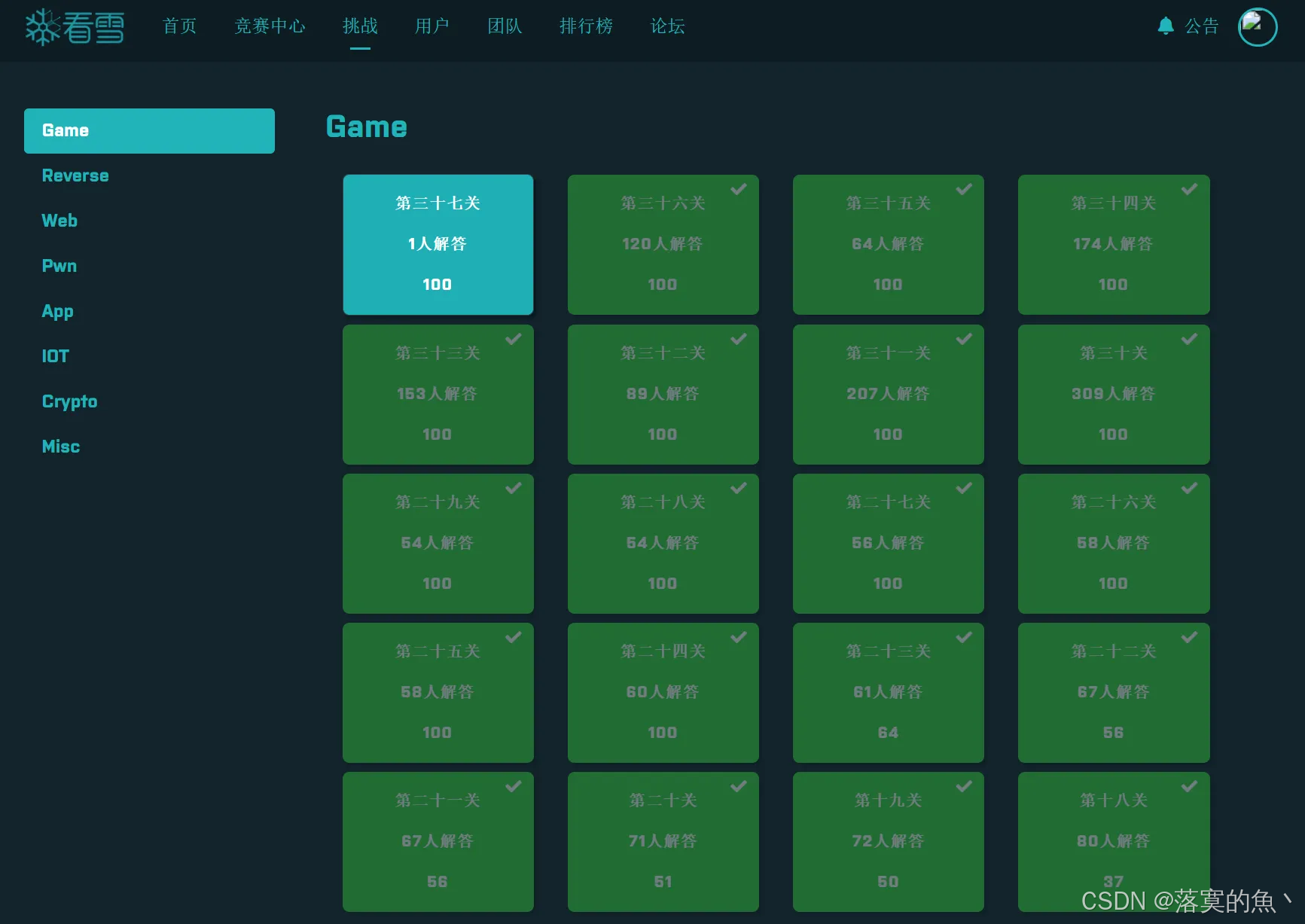
看雪CTF-GAME闯关秘籍Writeup:
鱼影安全:
闯关游戏:
第一关:
此游戏是一系列题目组合而成,您必须解决这个难题才能进入下一题或"关卡"。这些谜题的难度会随着您达到的更高级别而增加,题目内容包括技术、数学、音乐、科学、语言等。
每题分数起始分数是100,随着答题人数增加,分数会动态降低,最低为1分。
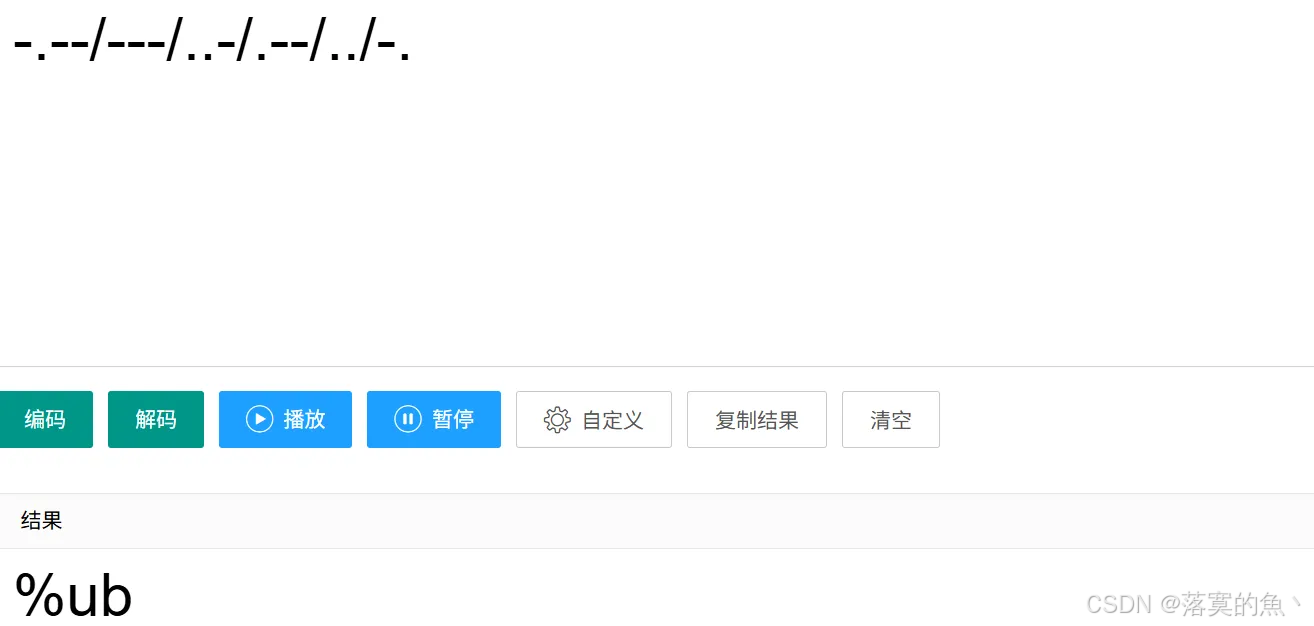
第一题:-.--/---/...-/.--/.../-.
注意:提交完正确的Flag后,请F5刷新一下页面,下一关题目就会出现。
在线解密:https://www.bejson.com/enc/morse/
第二关:
请个外援,找对象帮我修了一下 PS,牛逼扫出来了

flag{62d0cbb2c69133b52f386701726f29c1}
第三关:错误的MD5:
ZmxhZ3tiOTc2OGEzN2I0N2JlYjJkODhlMmRib2U3NmEzOWJiM30=
知识点:md5包含[0-9];[a-f]字符 o 不符合所以替换 0
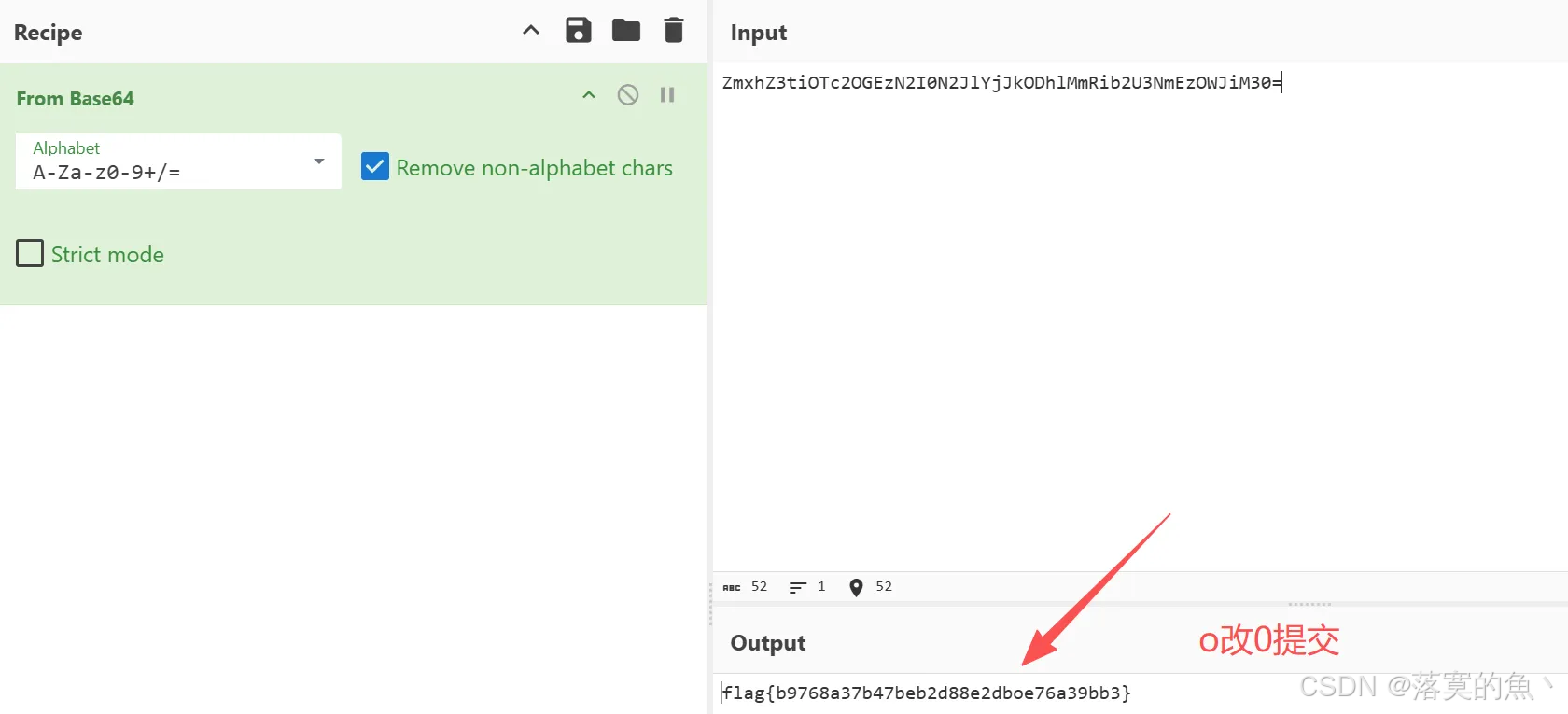
flag{b9768a37b47beb2d88e2db0e76a39bb3}
第四关 :
○● ●○ ●○ ●● ●● ●○ ●○
●○ ○○ ○○ ○● ○○ ○○ ○●
○○ ●○ ○○ ●○ ●● ●● ○○
在线解密:https://www.lddgo.net/common/braille
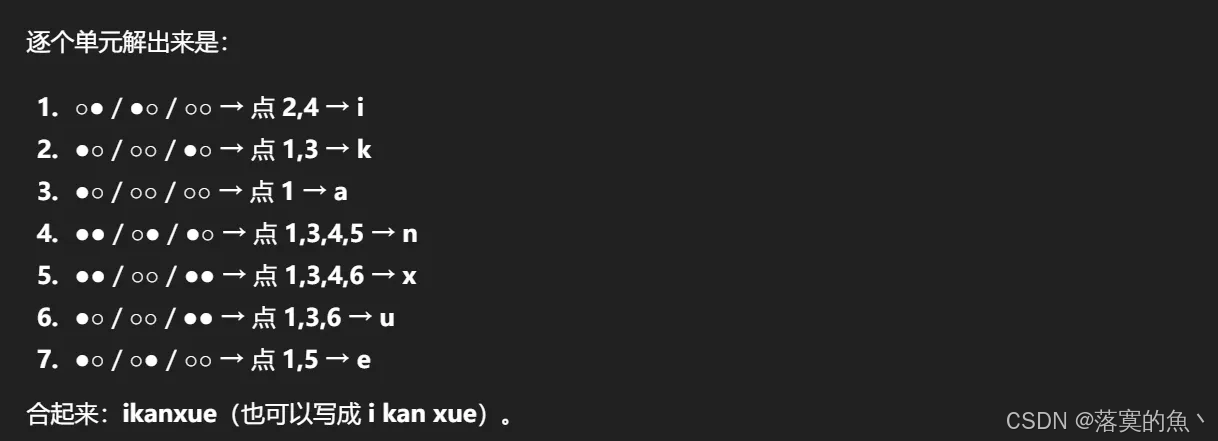
ikanxue
第五关:
看雪的历史,请下载附件闯关
在线 0 宽隐写:https://330k.github.io/misc_tools/unicode_steganography.html
ps:新手可能需要 kali 中 vim 查看 老手一看就看出来了

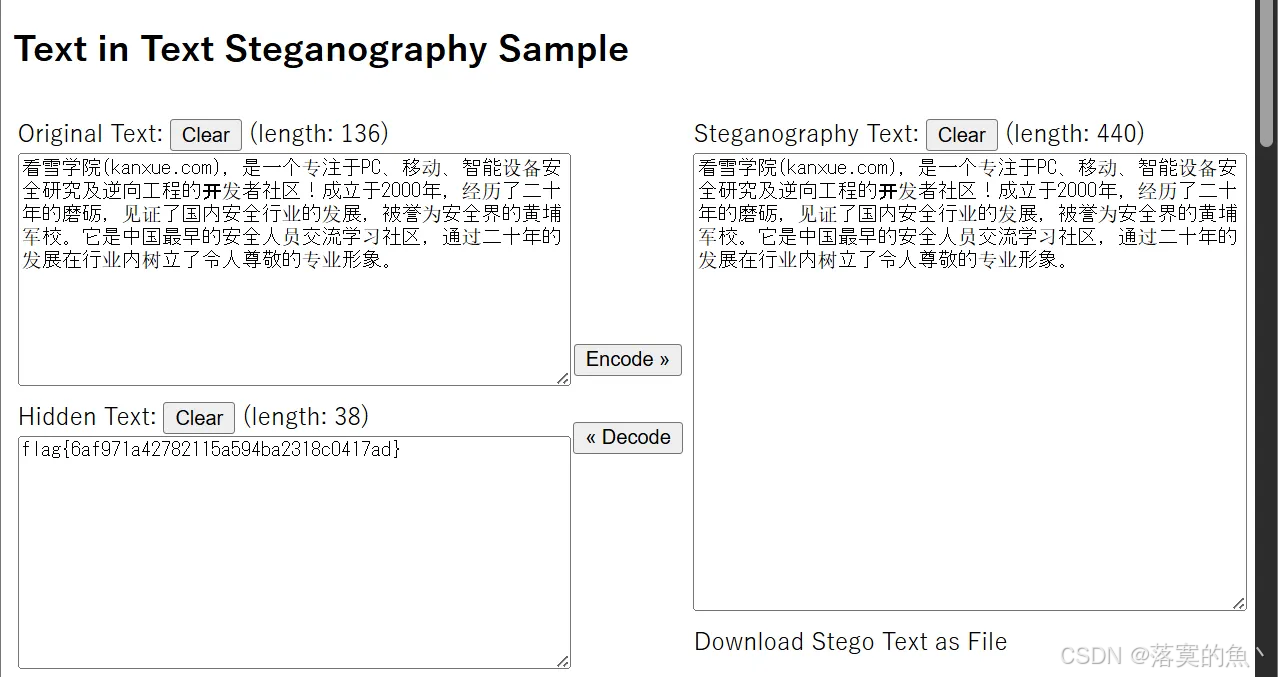

flag{6af971a42782115a594ba2318c0417ad}
第六关:
凯撒留下了什么?
0110100101101111011001000110101001111011001101110011000100110001001101010110100100110010001101100011000101100101011010010110011100110111011010010011010000110010011001000011010101100110011001110011011100110100001100010011001001100110011010000011100000110110011001000110010101100100001101110110100001111101
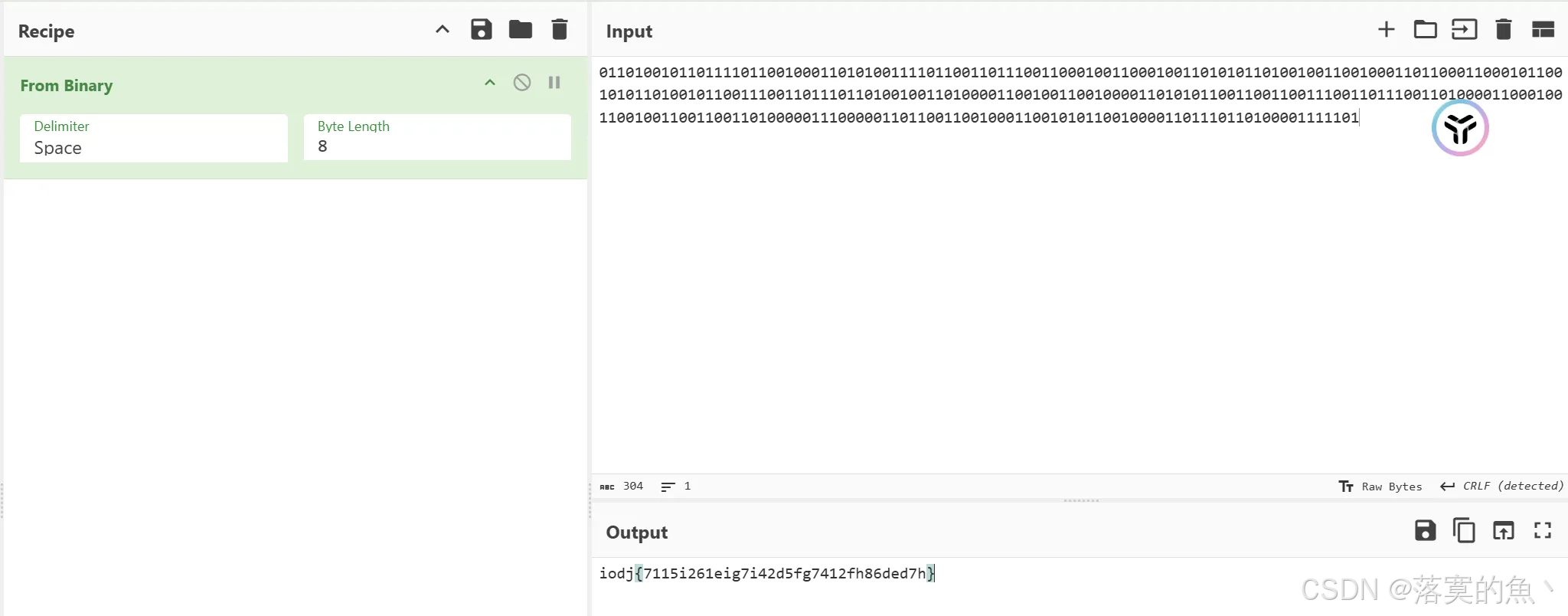
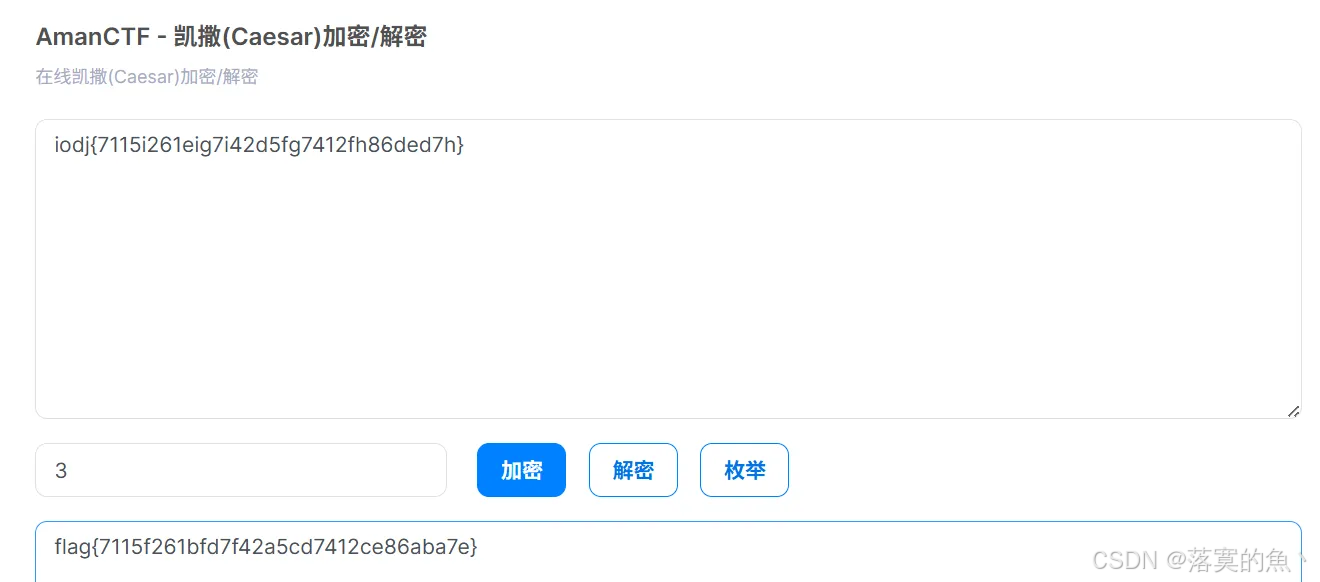
flag{7115f261bfd7f42a5cd7412ce86aba7e}
第七关:
描述:110米要跨几个栏?
在线解密:https://ctf.bugku.com/tool/railfence
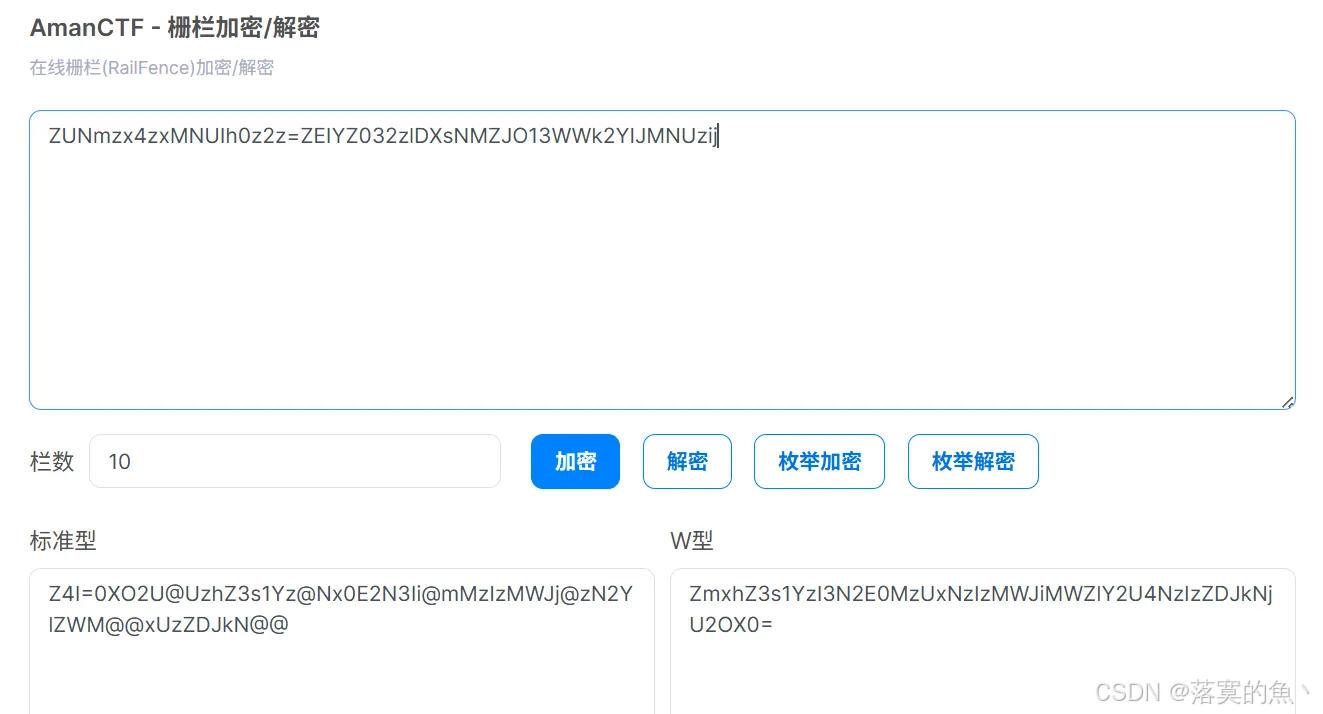
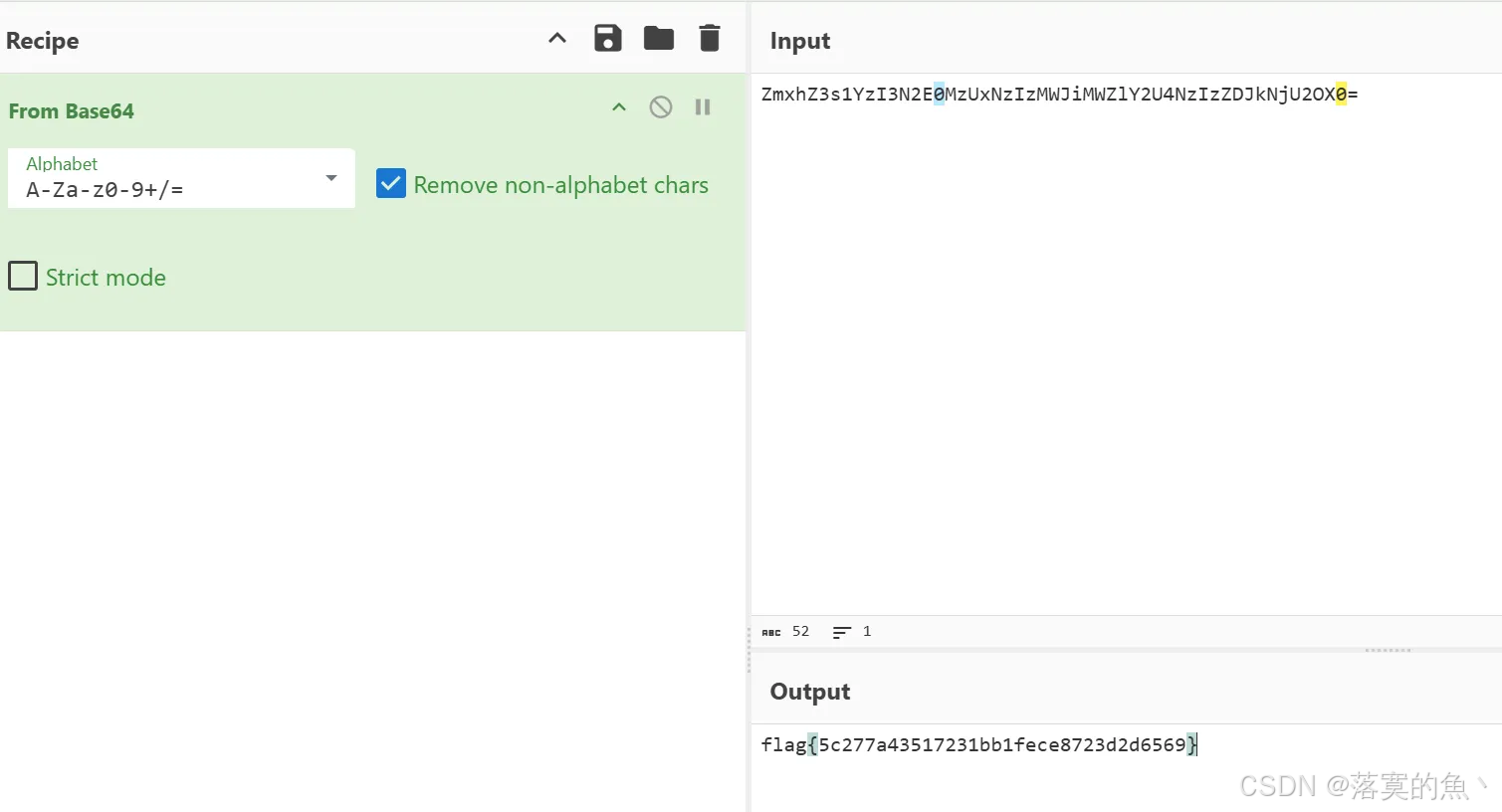
flag{5c277a43517231bb1fece8723d2d6569}
第八关:
WinXor,分析出flag
在IDA的顶部菜单中选择View -> Open Subviews -> Graph
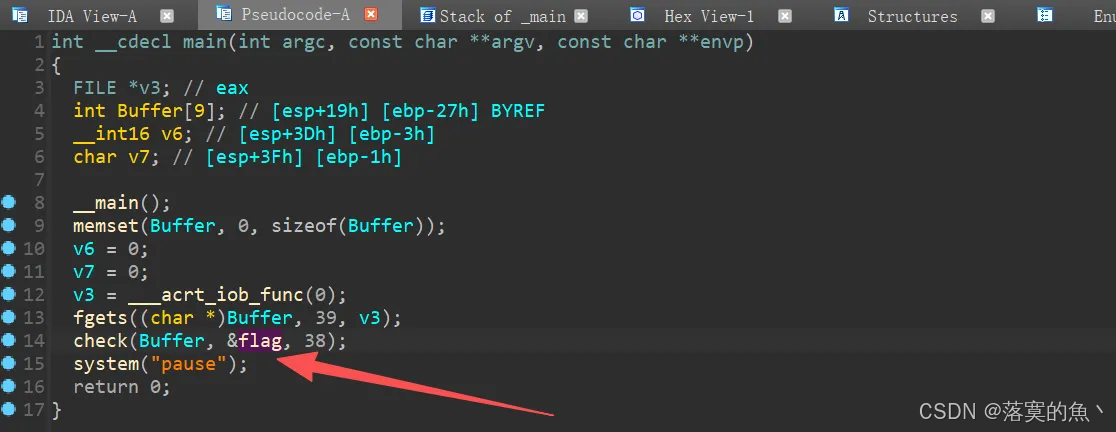
查看伪代码,flag每个值和0x31异或 写个脚本
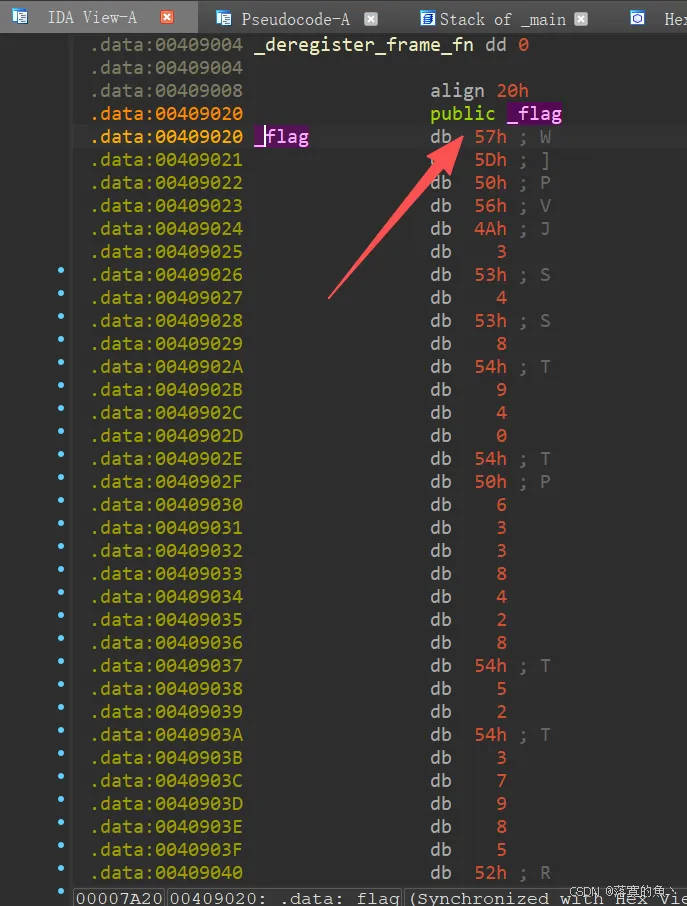
python
flag = [
0x57, 0x5D, 0x50, 0x56, 0x4A, 0x03, 0x53, 0x04, 0x53, 0x08,
0x54, 0x09, 0x04, 0x00, 0x54, 0x50, 0x06, 0x03, 0x03, 0x08,
0x04, 0x02, 0x08, 0x54, 0x05, 0x02, 0x54, 0x03, 0x07, 0x09,
0x08, 0x05, 0x52, 0x05, 0x03, 0x00, 0x01, 0x4C
]
key = 0x31
out = bytes([b ^ key for b in flag])
print(out.decode("latin-1")) # 原样打印(不报错)
print("hex:", out.hex())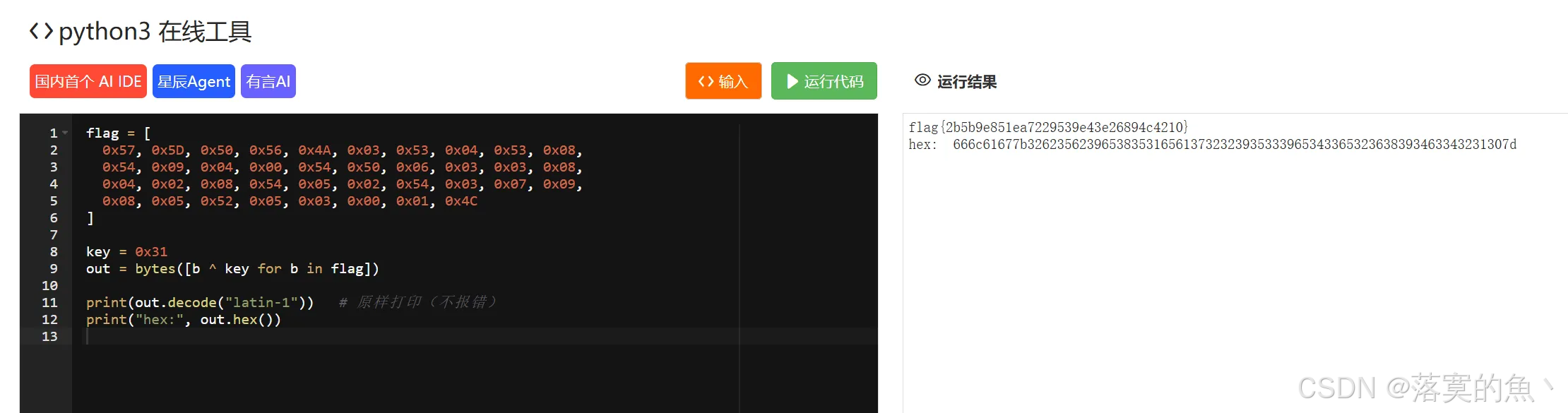
flag{2b5b9e851ea7229539e43e26894c4210}
第九关:
请看附件,一位土著告诉了你应该去哪里寻找你想要的当地特产 "振金"

YOUGOTIT
第十关:
提示:中午时分,云的影子比其它时刻小了许多。提交格式:flag{}.
很明显云影密码,原理就不说了很简单
821010841088421108841022104084210884021084210841
python
`python
821→8+2+1=11→K
1→1→A
841→13→M
884211→24→X
8841→21→U
221→5→E
4→4→D
8421→15→O
884→20→T
21→3→C
8421→15→O
841→13→M
M改N
#kanxuedotcom 注意格式
flag{kanxuedotcom}第十一关-伪加密:
还需要密码??
奇数改偶数,随波直接修复
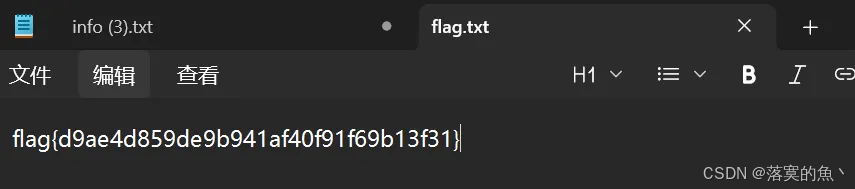
flag{d9ae4d859de9b941af40f91f69b13f31}
第十二关:
经典RSA!
已知N、e、c或已知p、q、e、c求m
python
p = 1074058774204108249701494602945344702257295575959111855899071
q = 88986629334781577655493187325102894512564116681307655782184342573939069819137
e = 9540011292252897217
c = 41548063605430288432470295597098485988788870848095534515875709414720207762389334011819123356492264118935214420228741427986850823373300101
n = p * q
phi = (p - 1) * (q - 1)
d = pow(e, -1, phi) # Python 3.8+ 支持
m = pow(c, d, n)
pt = m.to_bytes((m.bit_length() + 7) // 8, "big")
print(pt.decode())
## flag{81794a6521b73422e9d5c12ea5b8ccc3}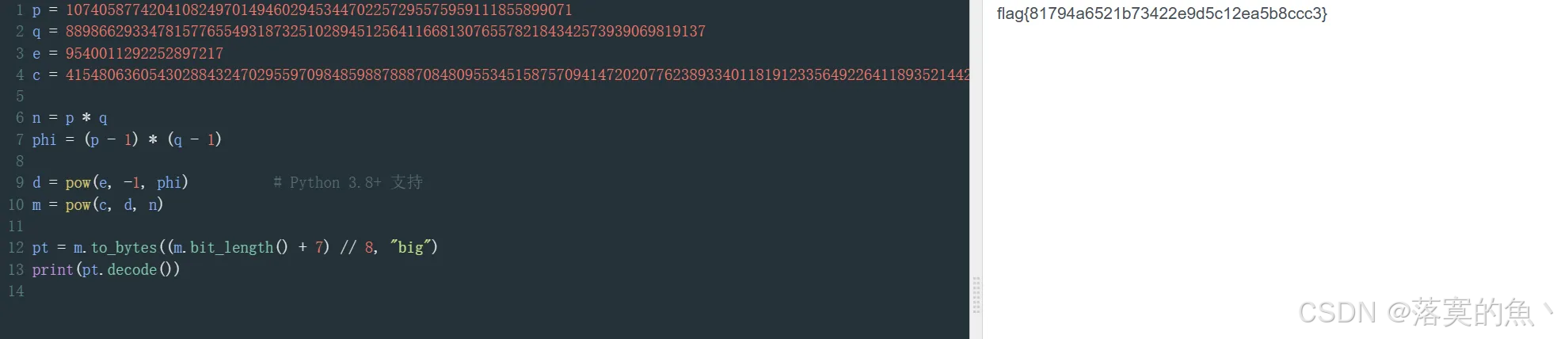
第十三关:
flag{aa6d377b2906ae97a2107e1ece8f1d04}
第十四关:
这个程序会告诉你flag
这是一个.net 的 exe 使用 dnSpy 打开分析源码,发现是异或 直接用 KEY=99 去 XOR 数组 A
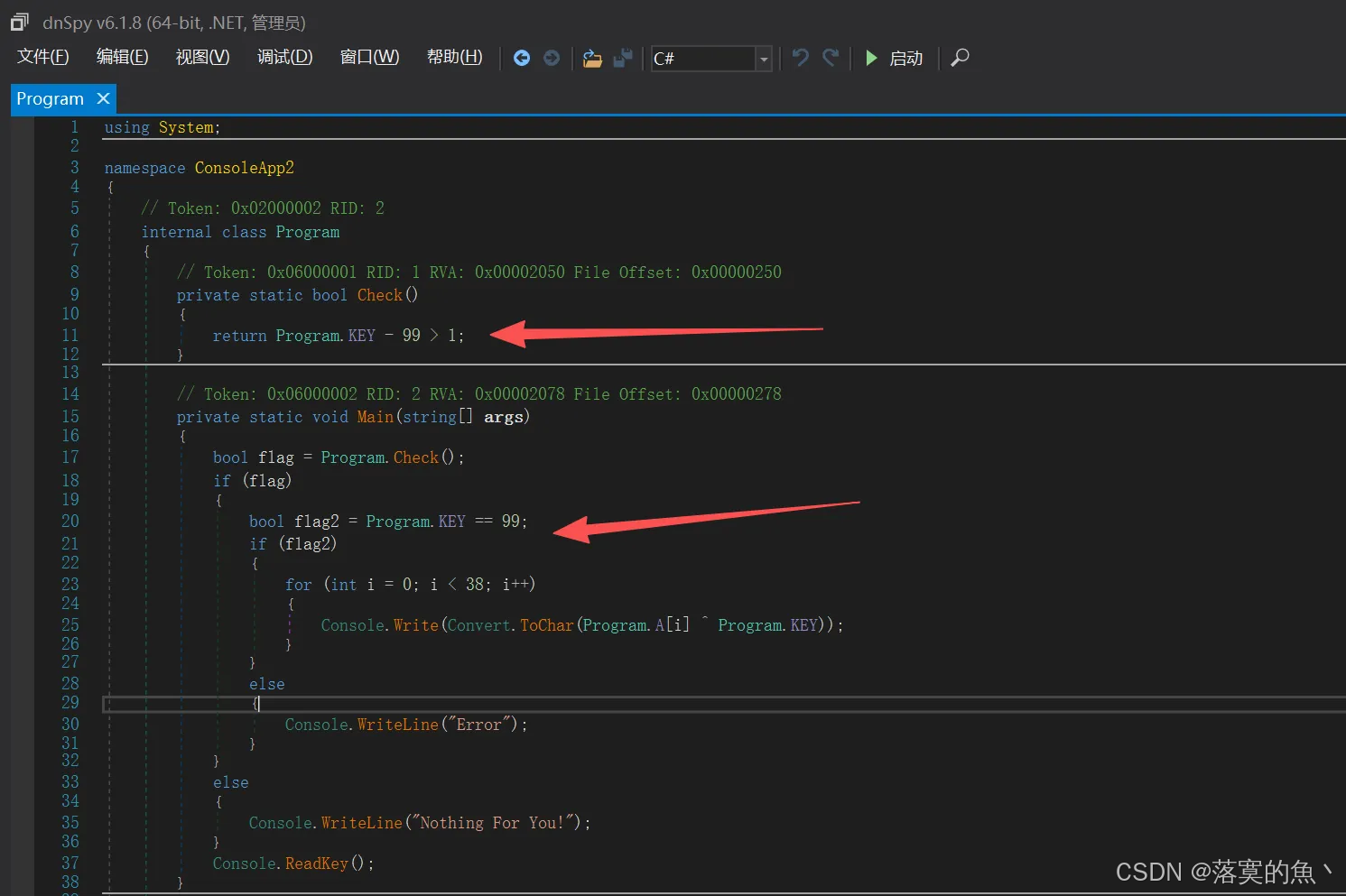
bash
A = [5,15,2,4,24,91,6,90,0,91,86,0,83,83,90,1,1,5,0,2,0,5,2,0,81,86,86,84,2,86,5,7,2,81,2,81,87,30]
KEY = 99 # 0x63
print(''.join(chr(x ^ KEY) for x in A))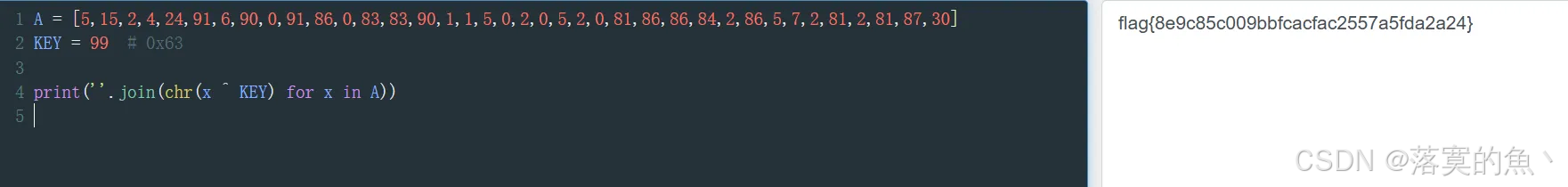
flag{8e9c85c009bbfcacfac2557a5fda2a24}
第十五关:
幸福的小羊,快乐的狼

flag{495a89667bd8820befba2e38ca93cef7}
第十六关:
Access数据库安全吗?
不安全直接小工具就可以看到密码 当然这里找了好几个都不行
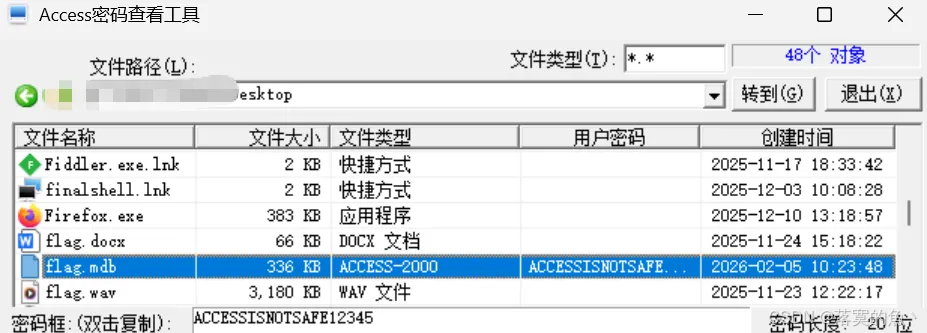
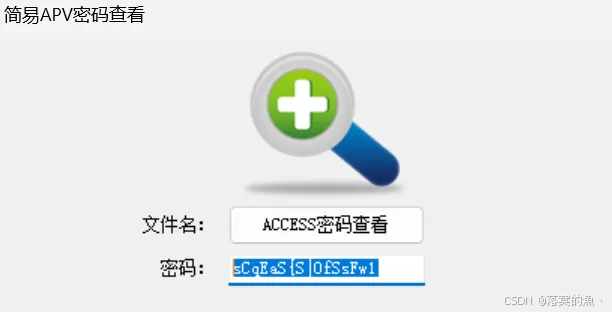
在线网站:https://www.mdbopener.com/
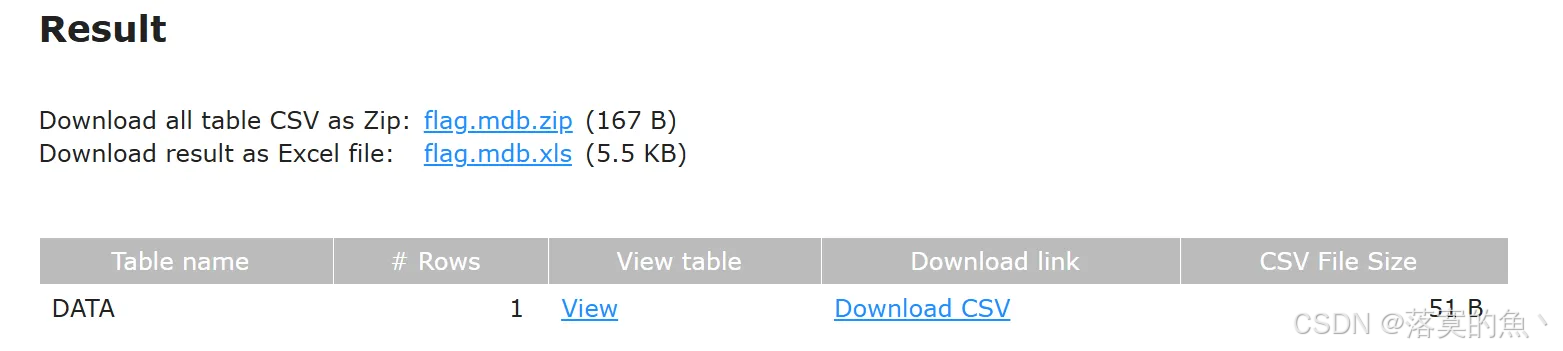
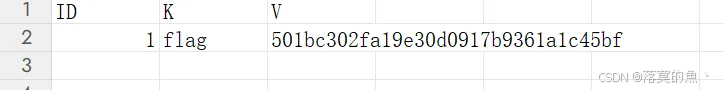
flag{c24dfa5bb27682d52bad1a77a32f6178}
第十七关:
我记得在2022年写了一个秘密文件,并添加了密码。 但是时间久了,我也忘了密码是什么。 只记得密码格式是flag{32位小写md5(hashcat_DATE)}

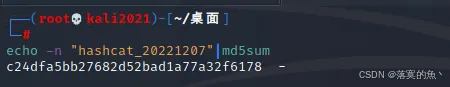
flag{c24dfa5bb27682d52bad1a77a32f6178}
第十八关:
简单的RSA,RSA解密,小e攻击
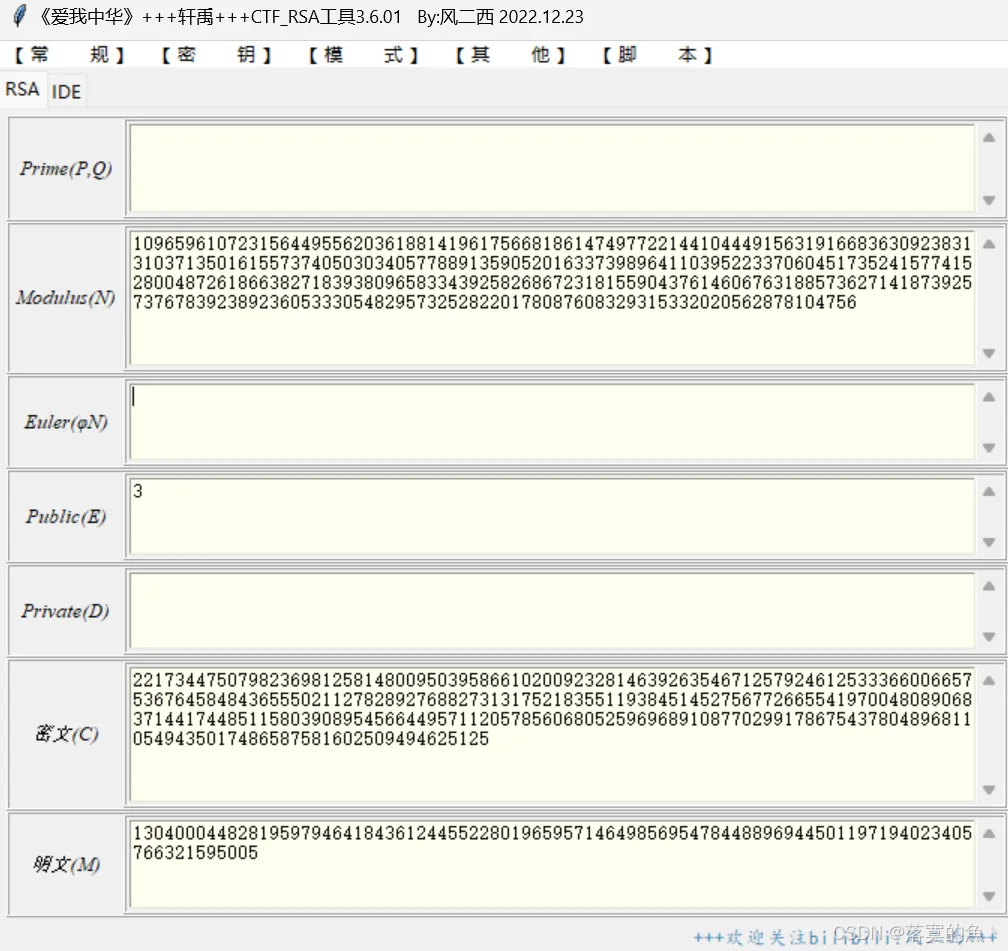
python
from Crypto.Util.number import long_to_bytes
m = 13040004482819597946418436124455228019659571464985695478448896944501197194023405766321595005
print(long_to_bytes(m))
flag{156a17333e77a3c504018cae5ada8c3b}
第十九关:
蒙娜丽莎背后的秘密
steghide info Mona.jpg steghide extract -sf Mona.jpg
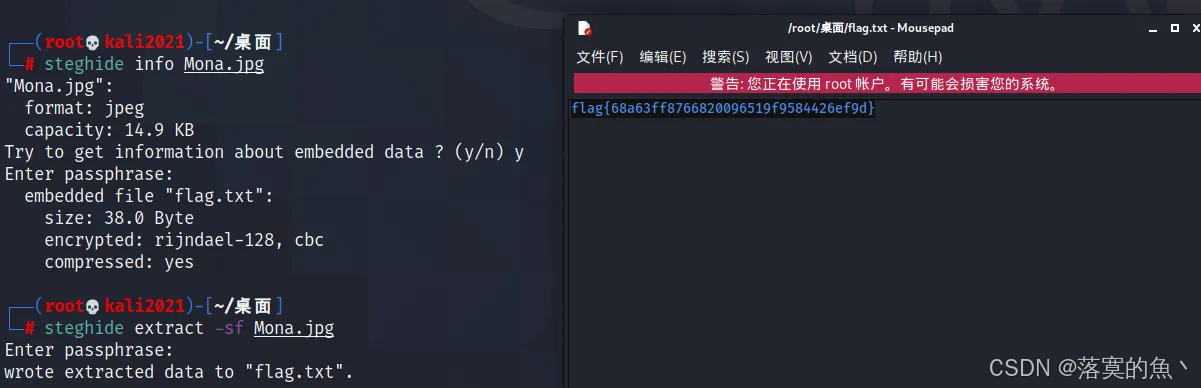
第二十关:
密码kxyyds,拿走不谢 ai 帮忙写个脚本就行:循环
python
import os, shutil, subprocess, glob
ZIP0 = "1000.zip"
PWD = "kxyyds"
WORK = "out"
SEVEN_Z = "7z" # Windows 可改成 r"C:\Program Files\7-Zip\7z.exe"
def run(cmd):
r = subprocess.run(cmd, stdout=subprocess.PIPE, stderr=subprocess.STDOUT, text=True)
return r.returncode, r.stdout
def find_next_zip(folder):
zips = []
for root, _, files in os.walk(folder):
for f in files:
if f.lower().endswith(".zip"):
zips.append(os.path.join(root, f))
return zips[0] if zips else None
def find_last_files(folder):
out = []
for root, _, files in os.walk(folder):
for f in files:
if not f.lower().endswith(".zip"):
out.append(os.path.join(root, f))
return out
def main():
shutil.rmtree(WORK, ignore_errors=True)
os.makedirs(WORK, exist_ok=True)
cur = os.path.abspath(ZIP0)
for depth in range(1, 5000): # 够用,防死循环
lvl = os.path.join(WORK, f"lvl_{depth:04d}")
os.makedirs(lvl, exist_ok=True)
# -y 自动覆盖;-p 指定密码;-o 指定输出目录
code, out = run([SEVEN_Z, "x", f"-p{PWD}", "-y", f"-o{lvl}", cur])
if code != 0:
print(f"[!] 解压失败 at level {depth}")
print(out)
return
nxt = find_next_zip(lvl)
if not nxt:
# 没有下一层 zip,说明到头了
files = find_last_files(lvl)
print(f"[+] 解到第 {depth} 层,最终文件:")
for p in files:
print(" -", p)
# 尝试直接打印文本内容(flag 常在 txt)
try:
data = open(p, "rb").read()
if len(data) <= 4096:
try:
print("[*] 内容:", data.decode(errors="ignore"))
except:
pass
except:
pass
return
cur = nxt
if __name__ == "__main__":
main()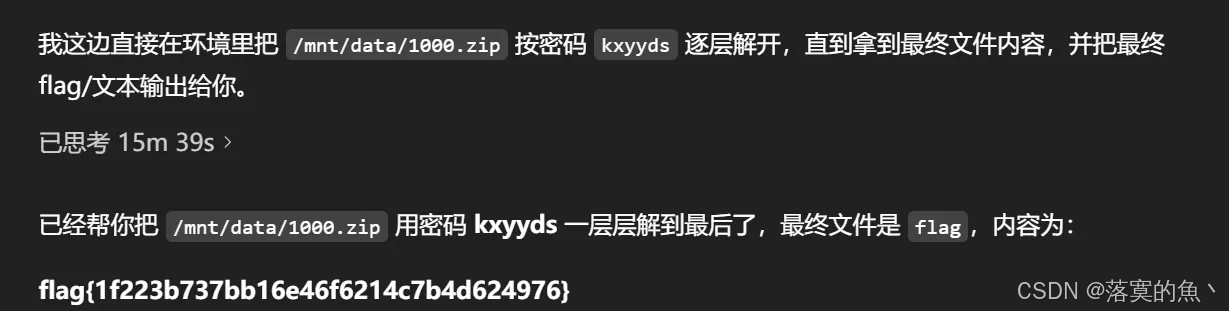
flag{1f223b737bb16e46f6214c7b4d624976}
第二十一关:
冰蝎流量解密
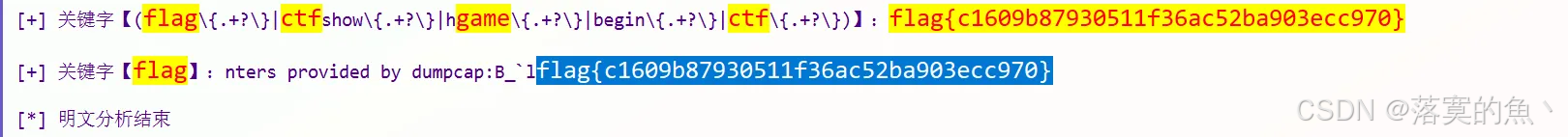
flag{c1609b87930511f36ac52ba903ecc970}
第二十二关:
多组信息 广播攻击
python
import math
from functools import reduce
e = 5
n1 = 89949876042409177323867813101117882442829410281842700894839421399069938235984672862652293711555149553911139368450418479695539026665377830420387043967934888420057079580384253446568058071795275438465859196915844311036117789185387905197534622591336675791570668600620181255395895498162948242922900968316004198713
n2 = 158070222314237392626974185091017812165079298904679085174521087973603366580430336558736309325348814673436518958534237019970593225438577445591128507171962689942666410413582117610455842920265722477107683035714729632157865401151155447832833704399012220230811610338263397941711465571368032968479517122688063228627
n3 = 125833496094734817243695739744230139753928423197094445357568225052210672076185273433284131219115166807589056837913856955225863308421027595706891518436767780997258388225847627344487525437489514108836442278605337394452980254710317777459176113478303804336257756874290812042048776397822097246306839022451765889523
c1 = 64762728744912277080725043589783603499336289903613879425542010904437303230864394867049931048301663521835907241628054764074618224274438266113678460263104551913515445611512529127927334634469590012330179879752372826052734575095603588516920928707755666937711484660415540329627440281701783814310326940135459458953
c2 = 81892486587542819638249334759512765967512221904430979434999963327372984400245787170855142342082064007218779449589865653788471102132950970574258098630324976601769573515707970686432744637736530361615660776051603206725763518018744106225576921753326376358274626814763794775824458464959673155703028669516536625027
c3 = 5951813988492004672630517384029848886357535922982582111119873076542468016342540731610619531566257550328179319875745469184900825726772278961616888632749897654771951747839709740819475124162149308143933786841856056437565919447824192953499881108366313280112296270910883925700704390324625008961208684382617602325
def egcd(a, b):
if b == 0:
return a, 1, 0
g, x, y = egcd(b, a % b)
return g, y, x - (a // b) * y
def invmod(a, m):
g, x, _ = egcd(a, m)
if g != 1:
raise ValueError("no inverse")
return x % m
def crt(cs, ns):
N = reduce(lambda x, y: x * y, ns, 1)
x = 0
for ci, ni in zip(cs, ns):
Mi = N // ni
x = (x + ci * Mi * invmod(Mi % ni, ni)) % N
return x
def iroot(k, n):
lo, hi = 0, 1
while hi ** n <= k:
hi *= 2
lo = hi // 2
while lo + 1 < hi:
mid = (lo + hi) // 2
if mid ** n <= k:
lo = mid
else:
hi = mid
return lo
C = crt([c1, c2, c3], [n1, n2, n3]) # C = m^5
m = iroot(C, e)
pt = m.to_bytes((m.bit_length() + 7) // 8, "big")
print(pt.decode())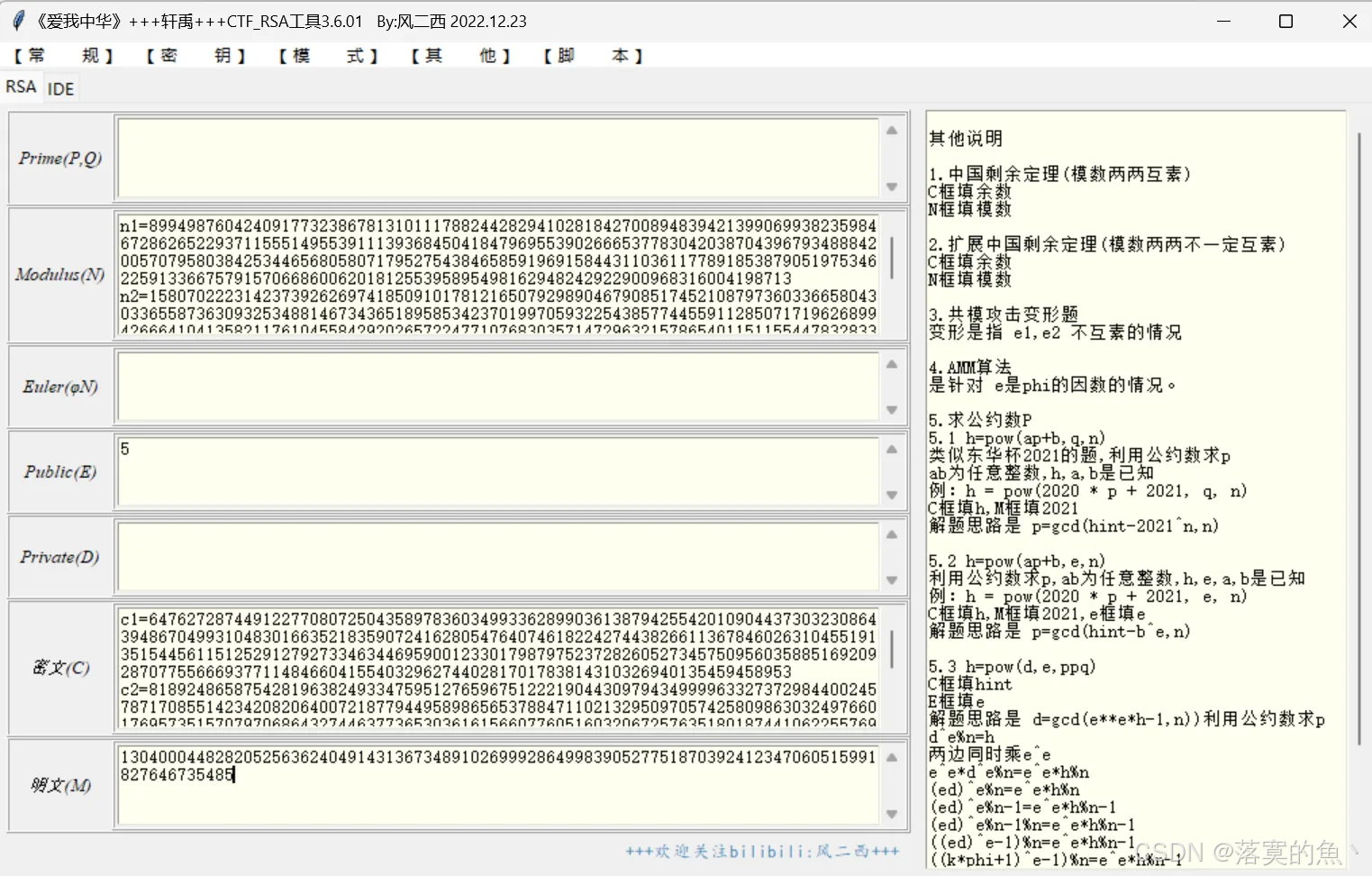
python
n = 13040004482820525636240491431367348910269992864998390527751870392412347060515991827646735485
print(n.to_bytes((n.bit_length()+7)//8, "big").decode())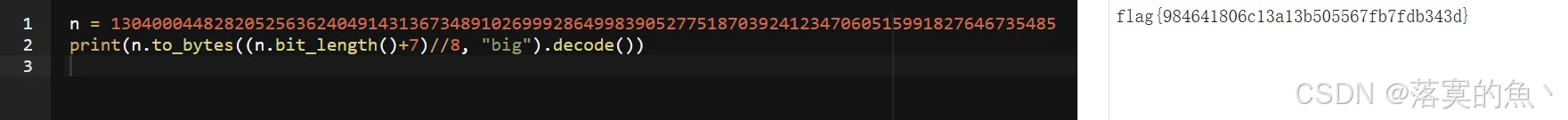
flag{984641806c13a13b505567fb7fdb343d}
第二十三关:
GLIBC-2.34,调试需要高版本Linux系统,不调试也可做
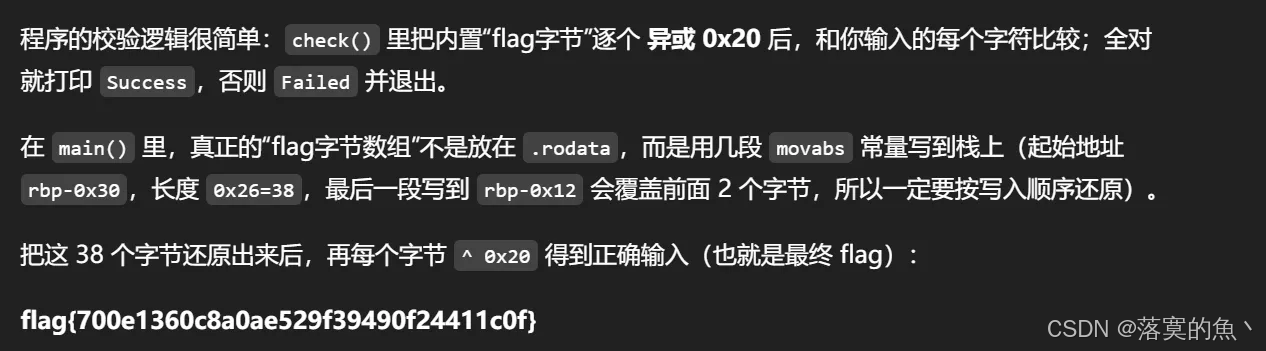
flag{700e1360c8a0ae529f39490f24411c0f}
第二十四关:
提示信息: Ctrl+U
题目路径:题目链接/Game/1-05692bfa06986eab/challenge1.php
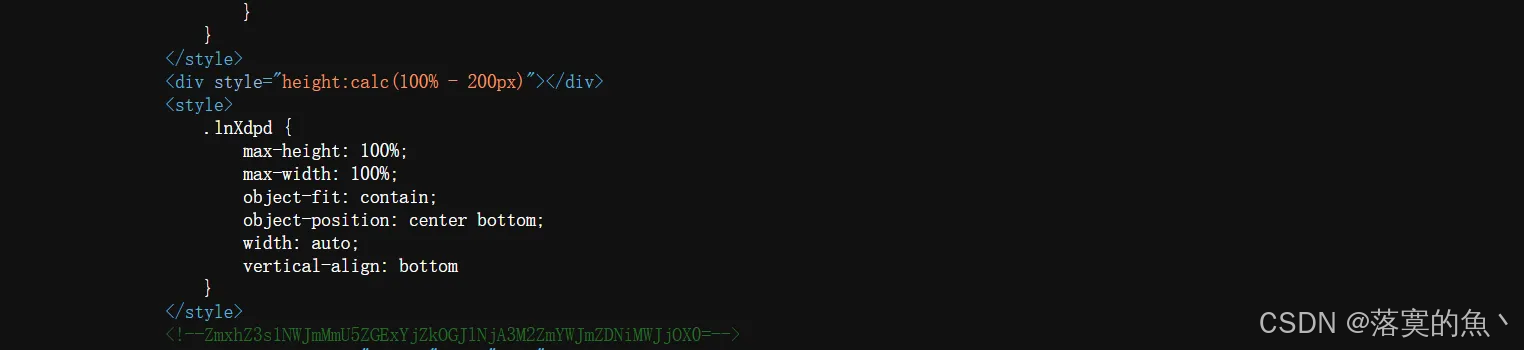
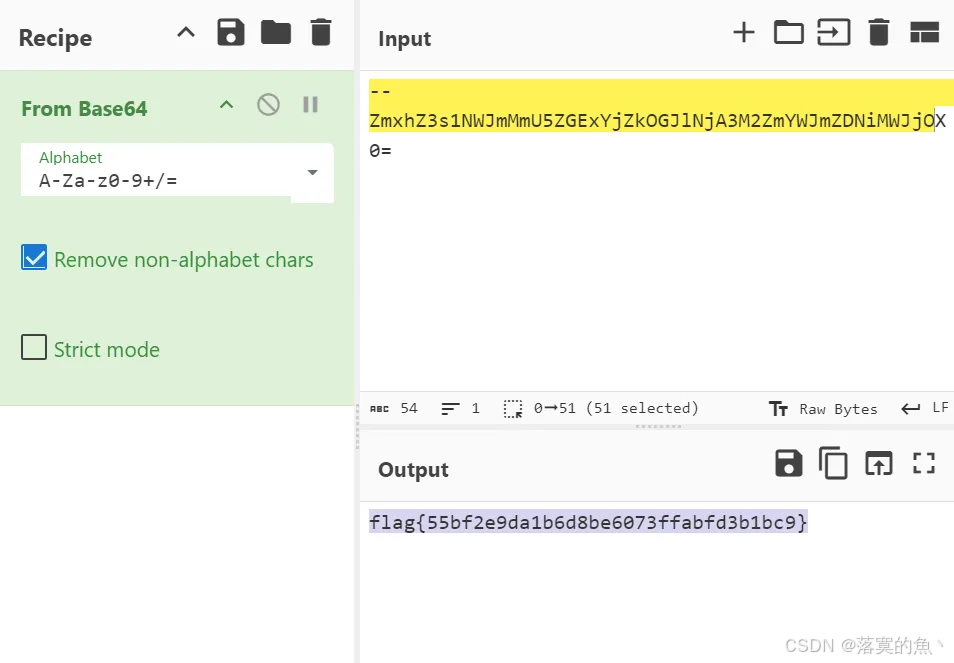
flag{55bf2e9da1b6d8be6073ffabfd3b1bc9}
第二十五关:
提示信息:GET
题目路径:题目链接/Game/2-b016162b04e6749d/challenge2.php
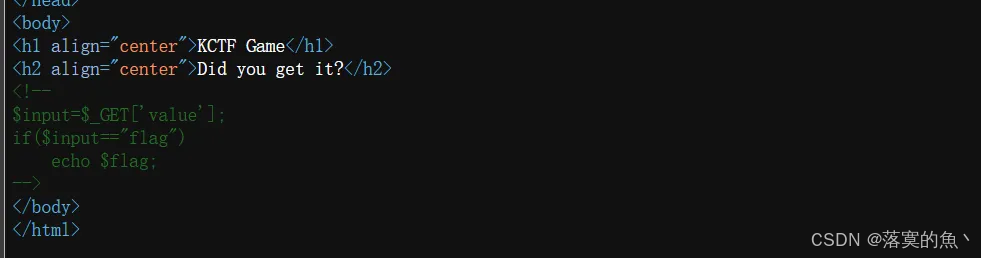
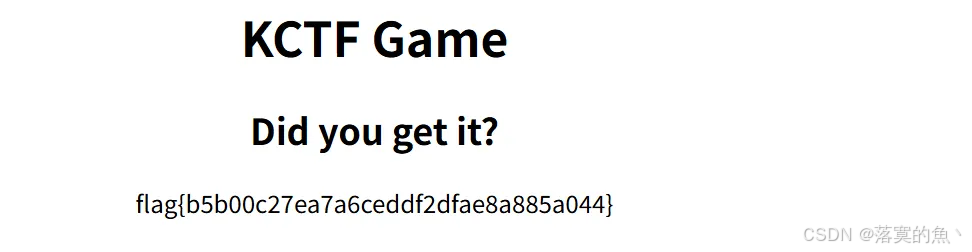
?value=flag
flag{b5b00c27ea7a6ceddf2dfae8a885a044}
第二十六关:
提示信息:POST
题目路径:题目链接/Game/3-d30a4b81c0398567/challenge3.php
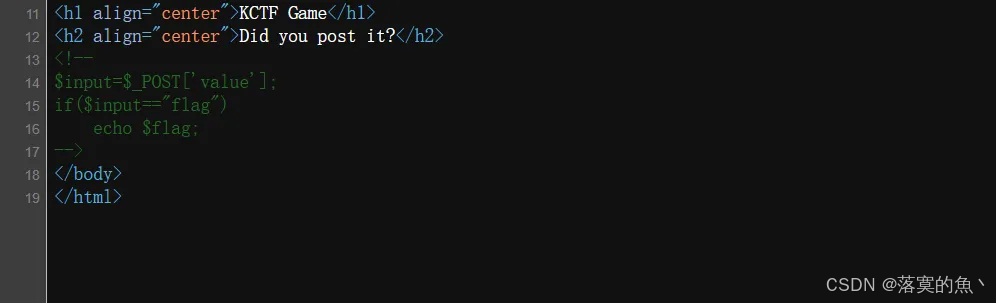
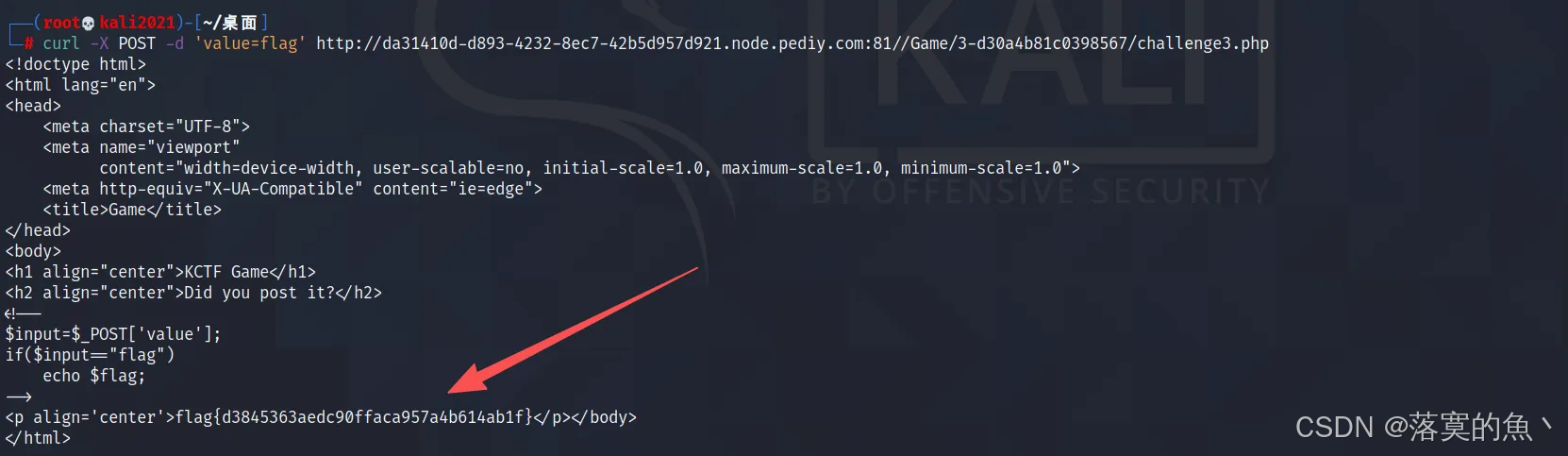
flag{d3845363aedc90ffaca957a4b614ab1f}
第二十七关:
提示信息:Compare
题目路径:题目链接/Game/8-84f7fd029d72f436/challenge8.php
bash
$value=$_GET["value"];
if(!is_numeric($value)&&$value==65535) {
echo $flag;
} else {
echo $value;
}
bash
curl http://77efda23-83b5-4e50-bd50-37b6a564621d.node.pediy.com:81//Game/8-84f7fd029d72f436/challenge8.php?value=65535d
flag{502a3bec075c3493248b89eccf154d96}
第二十八关:
提示信息:F5隐写
题目路径:题目链接/Game/10-af5f3bde91a7ebcf/challenge10.php
F5 隐写:git clone https://gitcode.com/gh_mirrors/f5/F5-steganography.git
java Extract picture.jpg -p ikanxue
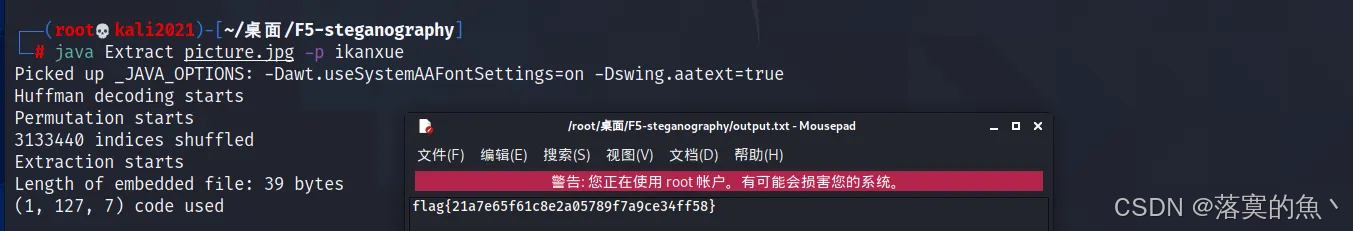
flag{21a7e65f61c8e2a05789f7a9ce34ff58}
第二十九关:
同上:一样的题目
第三十关:
难度:简单,动不了?
题目路径:题目链接/Game/4-2db6aef1f225f344/challenge4.php
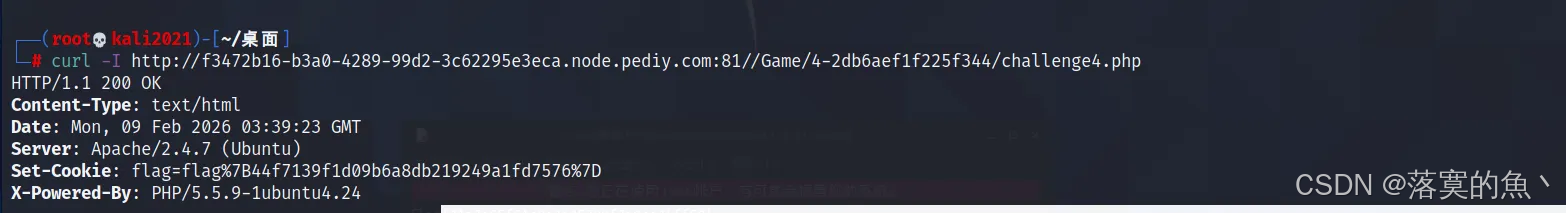
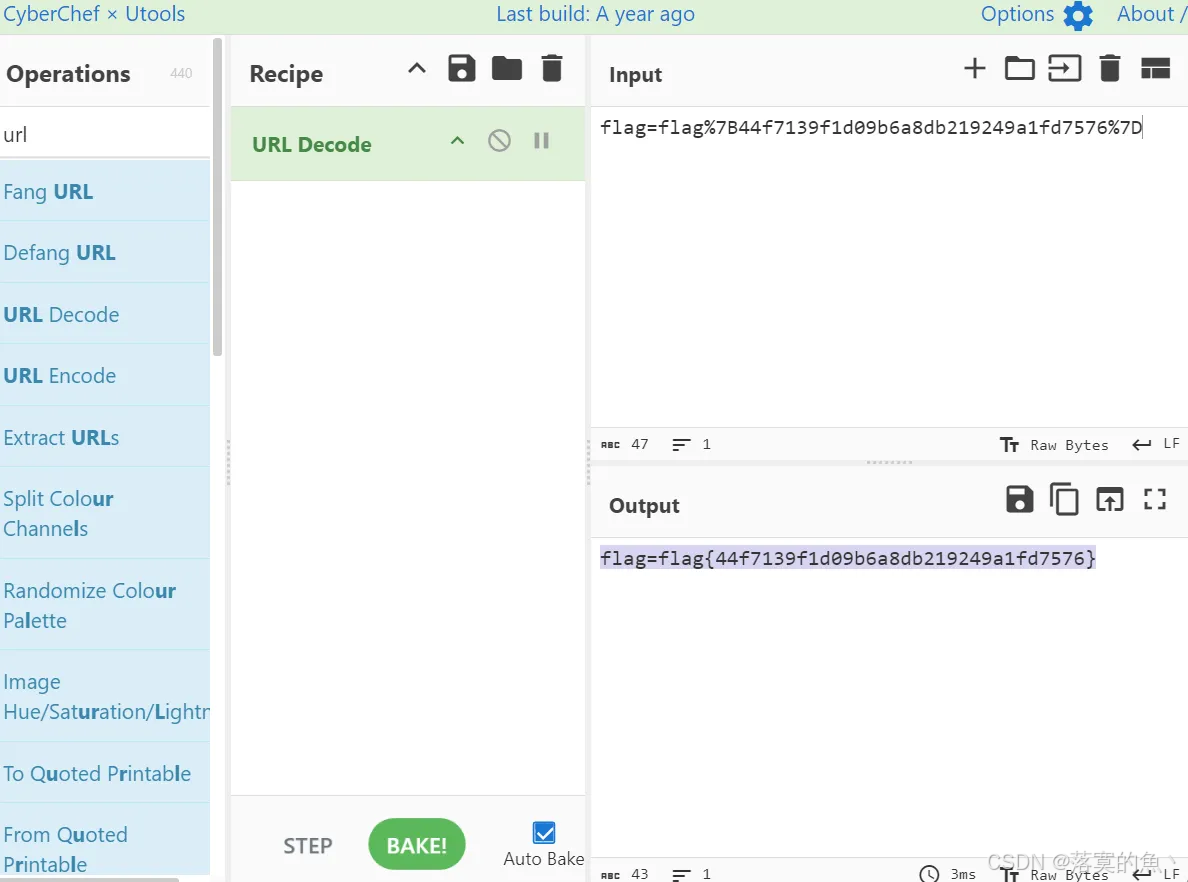
flag{44f7139f1d09b6a8db219249a1fd7576}
第三十一关:
难度:简单 类型:XFF
题目路径:题目链接/Game/6-432f430c11fd0943/challenge6.php
bash
curl -H "X-Forwarded-For:127.0.0.1" http://03ab9ce1-032a-483a-ae9f-92dab4dac4fc.node.pediy.com:81/Game/6-432f430c11fd0943/challenge6.php
flag{39a51b616c703d06f8a72c55605e3e6e}
第三十二关:
开局一个登录
难度:简单 类型:弱口令
题目路径: 题目链接/Game/7-5e93cab8e97cb97b/challenge7.php
爆破:admin,1234321 弱口令
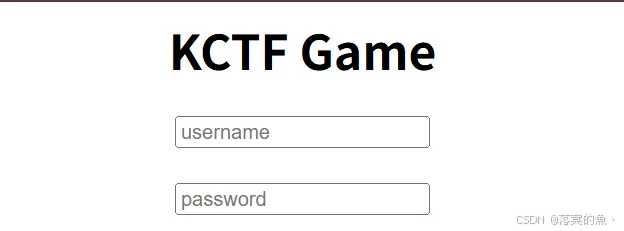
flag{858efb48f324024a85222a22f4bd7eca}
第三十三关:
给我一块饼干
难度:简单
类型:伪造
题目路径:题目链接/Game/11-580e84c1bb47bcd5/challenge11.php
时间戳base64编码 替换大一点即可。
MTg3MzAzNjgwMA%3D%3D
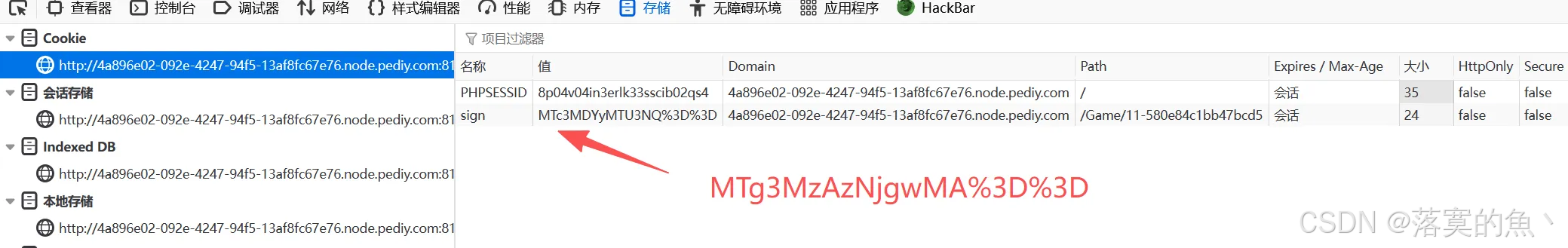
flag{c23085f7e776f581f147fc0c0ced2857}
第三十四关:
前端登录
难度:简单
类型:js逆向
题目路径:题目链接/Game/14-1957669e4ccd840a/challenge14.php
F12 查看源码,XSS 弹窗,代码审计发现是异或写个脚本
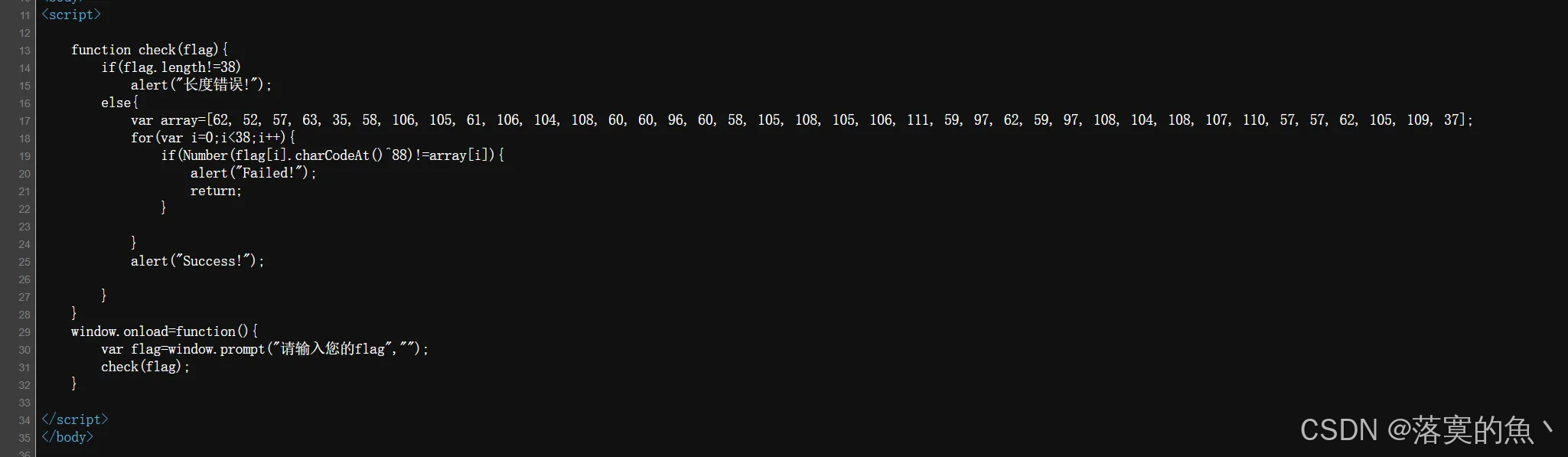
bash
a = [62, 52, 57, 63, 35, 58, 106, 105, 61, 106, 104, 108, 60, 60, 96, 60, 58, 105, 108, 105, 106, 111, 59, 97, 62, 59, 97, 108, 104, 108, 107, 110, 57, 57, 62, 105, 109, 37]
for c in a:
print(chr(c ^ 88),end='')
#flag{b21e204dd8db14127c9fc940436aaf15}第三十五关:
什么东西泄露了
难度:简单
类型:信息泄露
题目路径:题目链接/Game/15-a38d366e871ecd29/challenge15.php
F12 查看源码 代码审计
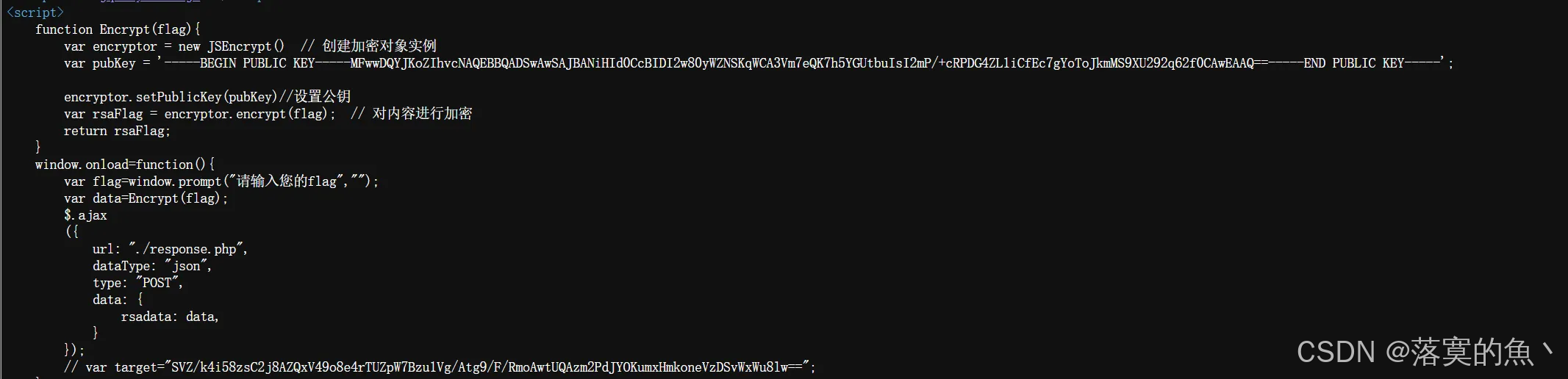
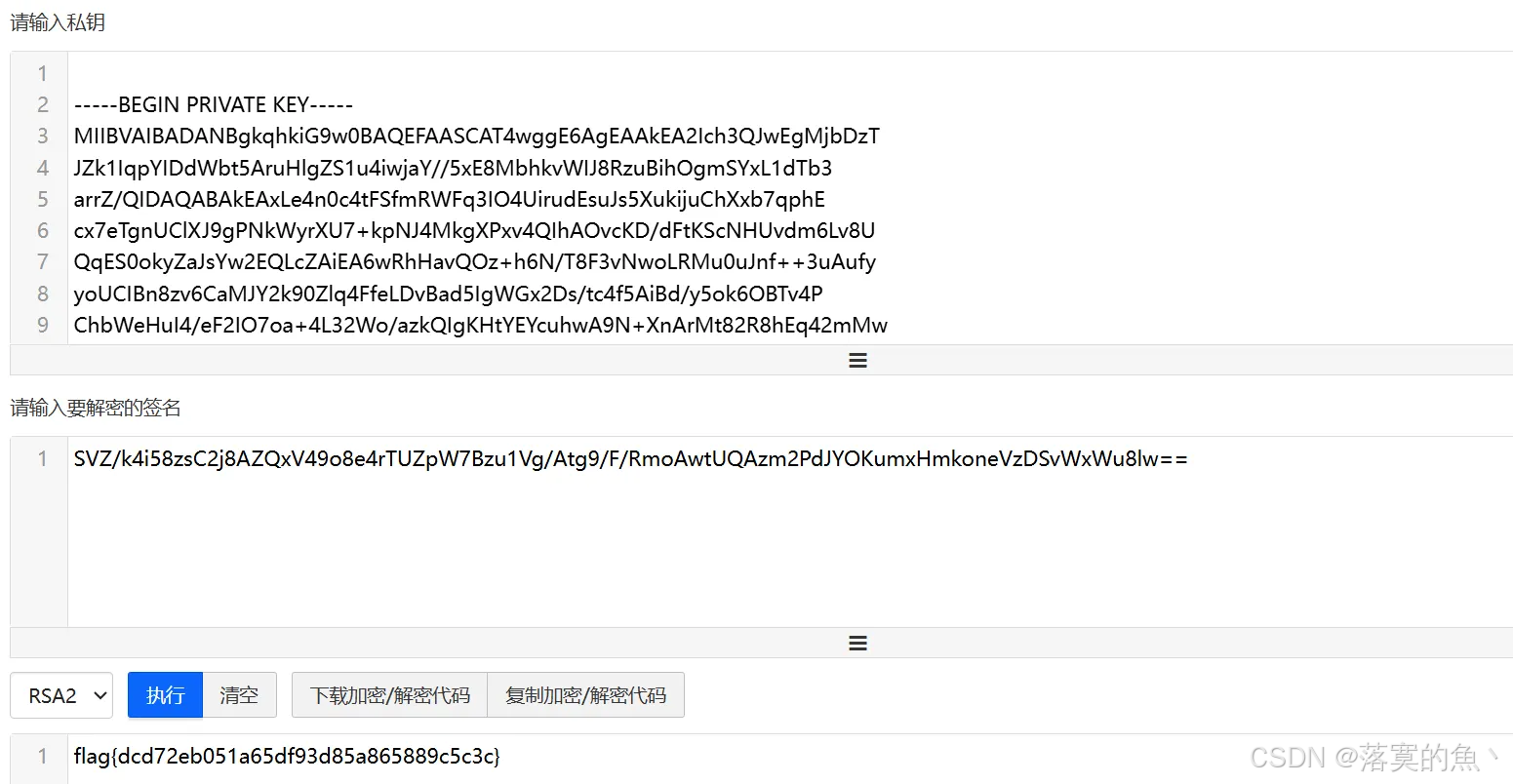
bash
-----BEGIN PRIVATE KEY-----
MIIBVAIBADANBgkqhkiG9w0BAQEFAASCAT4wggE6AgEAAkEA2Ich3QJwEgMjbDzT
JZk1IqpYIDdWbt5AruHlgZS1u4iwjaY//5xE8MbhkvWIJ8RzuBihOgmSYxL1dTb3
arrZ/QIDAQABAkEAxLe4n0c4tFSfmRWFq3IO4UirudEsuJs5XukijuChXxb7qphE
cx7eTgnUClXJ9gPNkWyrXU7+kpNJ4MkgXPxv4QIhAOvcKD/dFtKScNHUvdm6Lv8U
QqES0okyZaJsYw2EQLcZAiEA6wRhHavQOz+h6N/T8F3vNwoLRMu0uJnf++3uAufy
yoUCIBn8zv6CaMJY2k90Zlq4FfeLDvBad5IgWGx2Ds/tc4f5AiBd/y5ok6OBTv4P
ChbWeHuI4/eF2IO7oa+4L32Wo/azkQIgKHtYEYcuhwA9N+XnArMt82R8hEq42mMw
boo6o2VLV48=
-----END PRIVATE KEY-----
SVZ/k4i58zsC2j8AZQxV49o8e4rTUZpW7Bzu1Vg/Atg9/F/RmoAwtUQAzm2PdJYOKumxHmkoneVzDSvWxWu8lw==线解密:/https://www.bejson.com/enc/rsa/
第三十六关:
看不懂
难度:简单
类型:js逆向
题目路径:
题目链接/Game/16-785ef28ce2bcde47/challenge16.php
F12 看到 js 源码
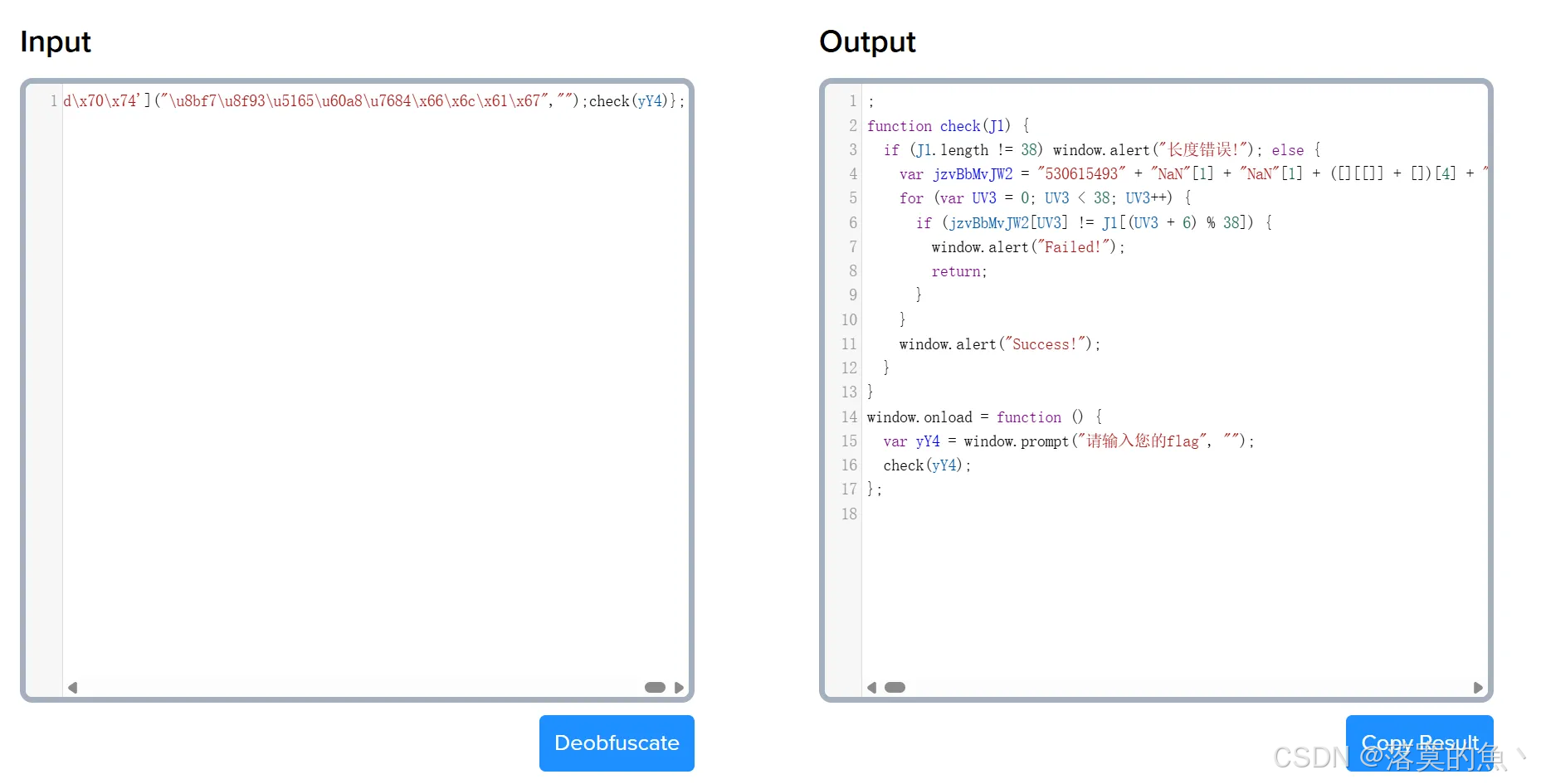
bash
;
function check(J1) {
if (J1.length != 38) window.alert("长度错误!"); else {
var jzvBbMvJW2 = "530615493" + "NaN"[1] + "NaN"[1] + ([][[]] + [])[4] + "8" + "NaN"[1] + "9" + "NaN"[1] + "3" + "0" + "9" + "8" + ([][[]] + [])[2] + "2" + ([][[]] + [])[4] + "1" + ([][[]] + [])[2] + "[object Object]"[2] + ([][[]] + [])[3] + "9" + "6" + "5" + "4" + []["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + ([][[]] + [])[0] + ([][[]] + [])[1] + ([][[]] + [])[3] + "false"[3] + "[object Object]"[5] + "NaN"[1] + ([] + []["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + "false"[2] + "[object Object]"[1] + "[object Object]"[5] + "NaN"[1] + "true"[0] + ([][[]] + [])[5] + "[object Object]"[1] + ([][[]] + [])[1])(5))[3] + ([][[]] + [])[3])(9)([]["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + ([][[]] + [])[3] + "false"[3] + "[object Object]"[5] + "NaN"[1] + ([] + []["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + "false"[2] + "[object Object]"[1] + "[object Object]"[5] + "NaN"[1] + "true"[0] + ([][[]] + [])[5] + "[object Object]"[1] + ([][[]] + [])[1])(5))[3] + ([][[]] + [])[3])(1)("[object Object]"[0])[0] + "7" + ([][[]] + [])[2]) + ([][[]] + [])[4] + "false"[2] + "NaN"[1] + []["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + ([][[]] + [])[0] + ([][[]] + [])[1] + ([][[]] + [])[3] + "false"[3] + "[object Object]"[5] + "NaN"[1] + ([] + []["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + "false"[2] + "[object Object]"[1] + "[object Object]"[5] + "NaN"[1] + "true"[0] + ([][[]] + [])[5] + "[object Object]"[1] + ([][[]] + [])[1])(5))[3] + ([][[]] + [])[3])(9)([]["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + ([][[]] + [])[3] + "false"[3] + "[object Object]"[5] + "NaN"[1] + ([] + []["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + "false"[2] + "[object Object]"[1] + "[object Object]"[5] + "NaN"[1] + "true"[0] + ([][[]] + [])[5] + "[object Object]"[1] + ([][[]] + [])[1])(5))[3] + ([][[]] + [])[3])(1)("[object Object]"[0])[0] + "6" + "7") + []["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + ([][[]] + [])[0] + ([][[]] + [])[1] + ([][[]] + [])[3] + "false"[3] + "[object Object]"[5] + "NaN"[1] + ([] + []["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + "false"[2] + "[object Object]"[1] + "[object Object]"[5] + "NaN"[1] + "true"[0] + ([][[]] + [])[5] + "[object Object]"[1] + ([][[]] + [])[1])(5))[3] + ([][[]] + [])[3])(9)([]["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + ([][[]] + [])[3] + "false"[3] + "[object Object]"[5] + "NaN"[1] + ([] + []["false"[3] + "[object Object]"[1] + "true"[1] + "true"[0]]["[object Object]"[5] + "[object Object]"[1] + ([][[]] + [])[1] + "false"[3] + "true"[0] + "true"[1] + ([][[]] + [])[0] + "[object Object]"[5] + "true"[0] + "[object Object]"[1] + "true"[1]]("true"[1] + ([][[]] + [])[3] + "true"[0] + ([][[]] + [])[0] + "true"[1] + ([][[]] + [])[1] + "[object Object]"[7] + "false"[2] + "[object Object]"[1] + "[object Object]"[5] + "NaN"[1] + "true"[0] + ([][[]] + [])[5] + "[object Object]"[1] + ([][[]] + [])[1])(5))[3] + ([][[]] + [])[3])(1)("[object Object]"[0])[0] + "7" + "[object Object]"[2]) + "9";
for (var UV3 = 0; UV3 < 38; UV3++) {
if (jzvBbMvJW2[UV3] != J1[(UV3 + 6) % 38]) {
window.alert("Failed!");
return;
}
}
window.alert("Success!");
}
}
window.onload = function () {
var yY4 = window.prompt("请输入您的flag", "");
check(yY4);
};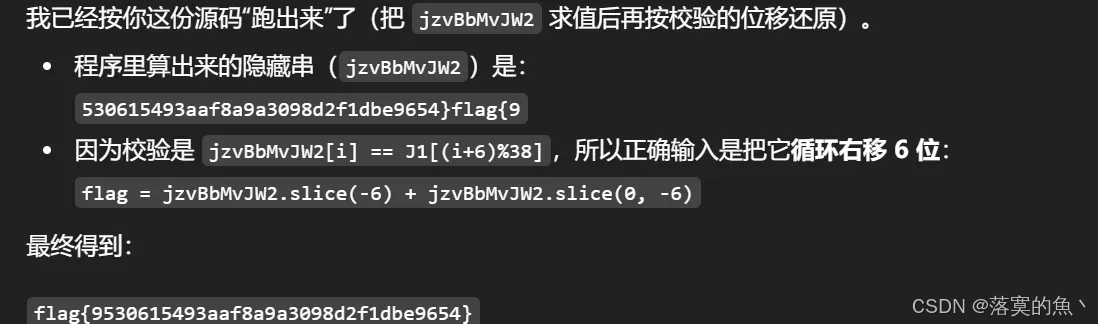
flag{9530615493aaf8a9a3098d2f1dbe9654}
第三十七关:
看雪留言板
难度:简单
类型:xss
题目路径:
题目链接/Game/17-64e45dfbe292348c/challenge17.php
到这里就结束吧,目前就一个人解出!