前言
问题 :对于文件加密与否的判别,通常可以用010Editor打开压缩包,查看标记位(zip文件是从504B0102的50开始数到第9字节,RAR文件是从文件头开始数到第24个字节)。然而这种方法并不高效:一是该方法无法区分真加密与伪加密,因为无论真加密还是伪加密的标志位都不为0;二是由于加密方法的不同,标志位可能会发生改变,例如zip文件的第9字节可能改成第6字节。
方案:binwalk工具可解决上述问题,使用binwalk对压缩包进行提取,若该包为真加密则无法提取,若该包为伪加密则可绕过其加密位对包中内容进行提取
做法
1.使用binwalk对伪加密包进行提取
当前路径中存放着一个伪加密包HELLO_NoPwd.rar,使用binwalk对该包进行提取,命令行输出入下:
bash
┌──(kali㉿kali)-[~/tmp]
└─$ binwalk -Me -C /home/kali/tmp/HELLO_NoPwd HELLO_NoPwd.rar
Scan Time: 2026-02-18 21:59:48
Target File: /home/kali/tmp/HELLO_NoPwd.rar
MD5 Checksum: 2145f20ab7606fb870ff850e38a142e5
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 RAR archive data, version 4.x, first volume type: MAIN_HEAD
Scan Time: 2026-02-18 21:59:50
Target File: /home/kali/tmp/HELLO_NoPwd/_HELLO_NoPwd.rar-0.extracted/hello.py
MD5 Checksum: 6c3a562ab867246f2dffe2c31f852eec
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
Scan Time: 2026-02-18 21:59:50
Target File: /home/kali/tmp/HELLO_NoPwd/_HELLO_NoPwd.rar-0.extracted/hello.cpython-314.pyc
MD5 Checksum: 871201900704f4fb29c1711ca3e58748
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
Scan Time: 2026-02-18 21:59:50
Target File: /home/kali/tmp/HELLO_NoPwd/_HELLO_NoPwd.rar-0.extracted/__init__.cpython-314.pyc
MD5 Checksum: aed040720ec86033ab806e797ab80c9b
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
┌──(kali㉿kali)-[~/tmp]
└─$ binwalk -Me -C /home/kali/tmp/HELLO_NoPwd HELLO_NoPwd.rar
Scan Time: 2026-02-18 22:00:09
Target File: /home/kali/tmp/HELLO_NoPwd.rar
MD5 Checksum: 2145f20ab7606fb870ff850e38a142e5
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 RAR archive data, version 4.x, first volume type: MAIN_HEAD
Scan Time: 2026-02-18 22:00:10
Target File: /home/kali/tmp/HELLO_NoPwd/_HELLO_NoPwd.rar.extracted/__init__.cpython-314.pyc
MD5 Checksum: aed040720ec86033ab806e797ab80c9b
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
Scan Time: 2026-02-18 22:00:10
Target File: /home/kali/tmp/HELLO_NoPwd/_HELLO_NoPwd.rar.extracted/hello.py
MD5 Checksum: 6c3a562ab867246f2dffe2c31f852eec
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
Scan Time: 2026-02-18 22:00:10
Target File: /home/kali/tmp/HELLO_NoPwd/_HELLO_NoPwd.rar.extracted/hello.cpython-314.pyc
MD5 Checksum: 871201900704f4fb29c1711ca3e58748
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
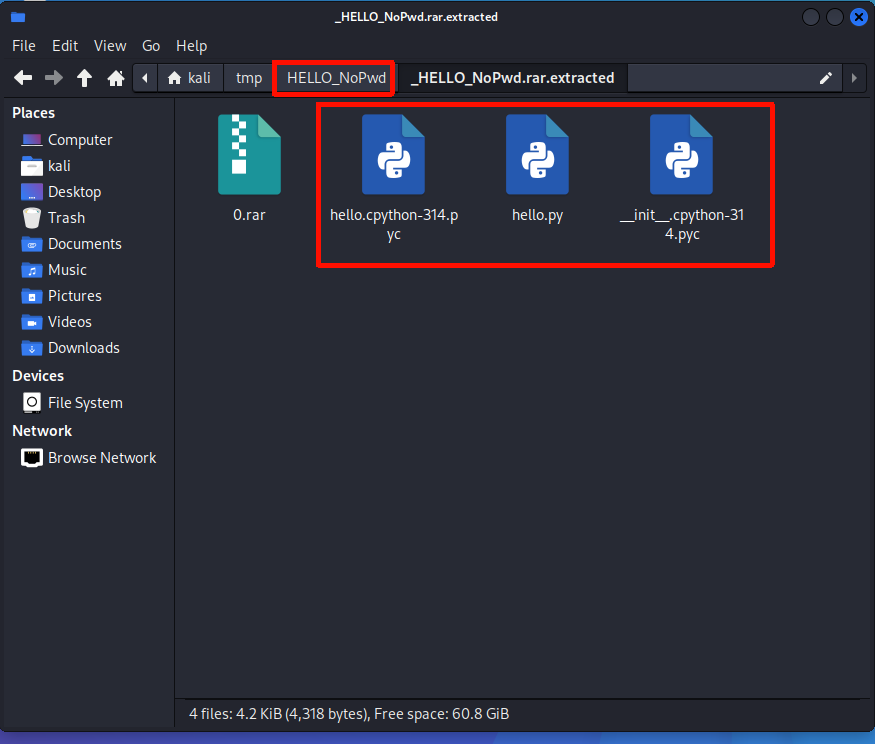
--------------------------------------------------------------------------------此外文件目录中出现了我命令里指定的文件夹HELLO_NoPwd,该文件夹中存放了提取出来的文件。
2.使用binwalk对真加密压缩包进行提取
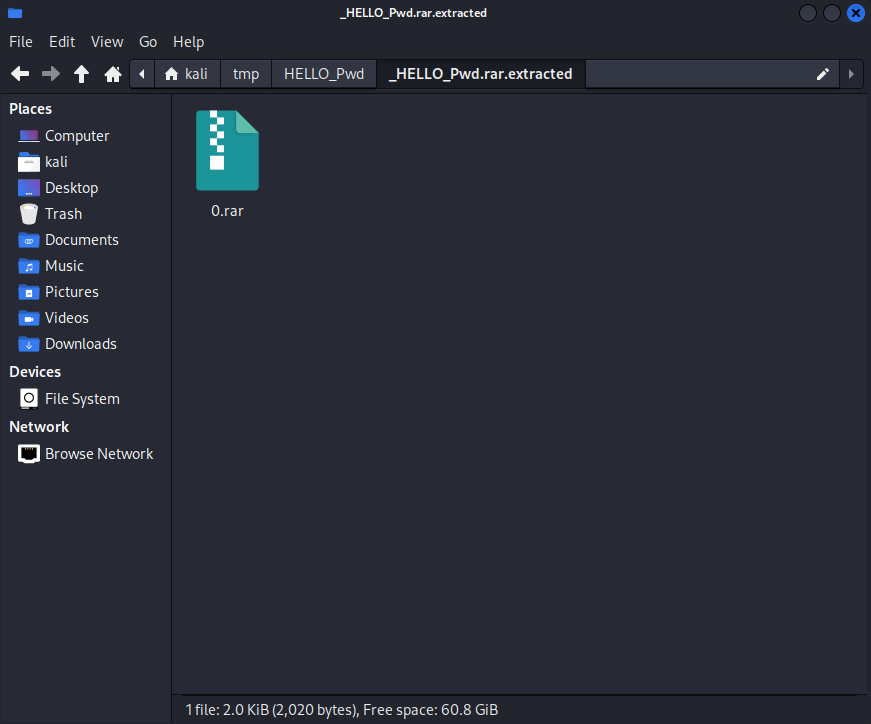
HELLO_Pwd.rar是一个真加密的压缩包,对其进行提取,命令行输出如下:
bash
┌──(kali㉿kali)-[~/tmp]
└─$ binwalk -Me -C /home/kali/tmp/HELLO_Pwd HELLO_Pwd.rar
Scan Time: 2026-02-18 22:00:58
Target File: /home/kali/tmp/HELLO_Pwd.rar
MD5 Checksum: 162cbbc655c2119ab94448b6bd012753
Signatures: 411
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 RAR archive data, version 4.x, first volume type: MAIN_HEAD文件目录中多了一个我命令中指定的HELLO_Pwd文件夹,该文件夹中的0.rar本质上是HELLO_Pwd.rar的复制,但想要查看其中内容仍需输入密码,相当于无法打开。