文章目录
- 总结
- [Symmetric Cryptography revisited](#Symmetric Cryptography revisited)
-
- [Symmetric Cryptography: Analogy](#Symmetric Cryptography: Analogy)
- [Symmetric Cryptography: Shortcomings](#Symmetric Cryptography: Shortcomings)
- [principles of asymmetric cryptography](#principles of asymmetric cryptography)
-
- [Idea behind Asymmetric Cryptography](#Idea behind Asymmetric Cryptography)
- [asymmetric(public key) cryptography](#asymmetric(public key) cryptography)
- [aSymmetric Cryptography: Analogy](#aSymmetric Cryptography: Analogy)
- [practical aspects of public-key cryptograpy](#practical aspects of public-key cryptograpy)
-
- [basic protocol for public-key Encryption](#basic protocol for public-key Encryption)
- [security Mechanisms of Public-Key Cryptography](#security Mechanisms of Public-Key Cryptography)
- [basic key transport protocol](#basic key transport protocol)
- [important public-key algorithm](#important public-key algorithm)
-
- [how to build public-key algorithms](#how to build public-key algorithms)
- [key lengths and security levels](#key lengths and security levels)
- [essential number theory for public-key algorithm](#essential number theory for public-key algorithm)
-
- [Euclidean algorithm](#Euclidean algorithm)
- [extended Euclidean algorithm](#extended Euclidean algorithm)
-
- [Euler's Phi Function(欧拉函数)](#Euler's Phi Function(欧拉函数))
- [Fermat's Little Theorem](#Fermat's Little Theorem)
- [欧拉定理(Euler's Theorem)](#欧拉定理(Euler's Theorem))
总结

Symmetric Cryptography revisited

Symmetric Cryptography: Analogy
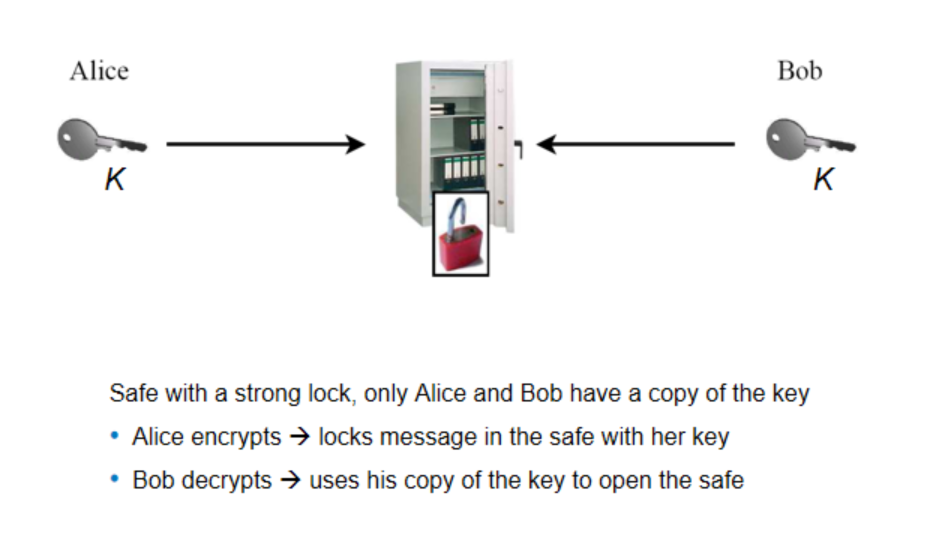
Symmetric Cryptography: Shortcomings


principles of asymmetric cryptography
Idea behind Asymmetric Cryptography

asymmetric(public key) cryptography

aSymmetric Cryptography: Analogy
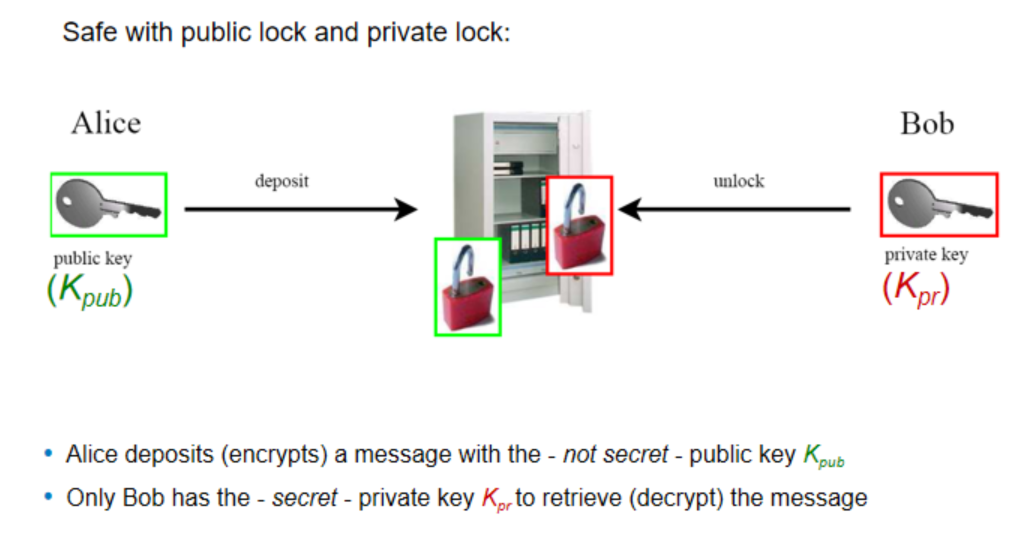
practical aspects of public-key cryptograpy
basic protocol for public-key Encryption

security Mechanisms of Public-Key Cryptography





basic key transport protocol

使用 AES 作为对称加密的混合加密协议

important public-key algorithm
how to build public-key algorithms

key lengths and security levels
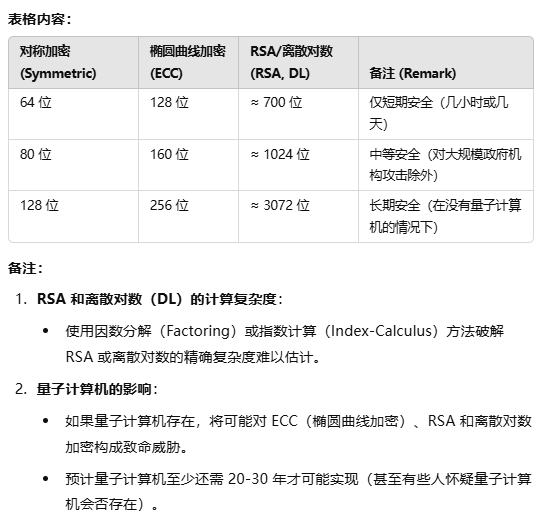
essential number theory for public-key algorithm
Euclidean algorithm


原理证明

extended Euclidean algorithm

先列出标准欧几里得算法表格,然后一步一步回代(上一步余数的等式带入当前式子)
证明





12mod67和67mod12的最后得到的式子是一样的,所以不如直接用67mod12,因为12mod67会转换成67mod12,此时67是r0,12是r1

Euler's Phi Function(欧拉函数)


欧拉函数的高效计算方法


Fermat's Little Theorem

欧拉定理(Euler's Theorem)

