目录
1.查看日志
如下截取的是应用崩溃的关键日志:
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A Build fingerprint: 'qti/bengal_515/bengal_515:15/AQ3A.241114.001/2539:userdebug/unknown'
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A Revision: '0'
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A ABI: 'arm64'
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A Timestamp: 2025-12-08 14:20:41.230222544+0800
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A Process uptime: 47s
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A Cmdline: com.quectel.esim
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A pid: 28572, tid: 28601, name: Thread-7 >>> com.quectel.esim <<<
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A uid: 1000
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A tagged_addr_ctrl: 0000000000000001 (PR_TAGGED_ADDR_ENABLE)
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x0000000000000008
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A Cause: null pointer dereference
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A x0 b40000708e471ff0 x1 0000000000000000 x2 0000000000000008 x3 000000000000002d
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A x4 2d53756363657373 x5 0000000000000000 x6 0000000000000000 x7 0000000000000000
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A x8 0000000000000000 x9 5f6c712000737365 x10 ffffffffffffffff x11 0101010101010101
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A x12 0000000000000040 x13 ffffff0000000000 x14 ffffffffffffffff x15 0000000000000028
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A x16 0000006fecf70108 x17 0000006fecf5211c x18 0000006fe9304000 x19 0000006fe9a5a730
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A x20 0000006fe9a5a730 x21 0000006fe9a5a730 x22 0000000000006f9c x23 0000000000006f9c
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A x24 0000006fe9a5a730 x25 0000006fe9a5a730 x26 0000006fe9a5aa70 x27 00000073406b3a80
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A x28 0000006fe9962000 x29 0000006fe9a5a530
2025-12-08 14:20:41.506 28752-28752 DEBUG crash_dump64 A lr 0000006fecf52fc4 sp 0000006fe9a5a500 pc 0000006fecf52140 pst 0000000080000000
2025-12-08 14:20:41.507 28752-28752 DEBUG crash_dump64 A 7 total frames
2025-12-08 14:20:41.507 28752-28752 DEBUG crash_dump64 A backtrace:
2025-12-08 14:20:41.507 28752-28752 DEBUG crash_dump64 A #00 pc 000000000004f140 /data/app/~~Gd3Iea__Lz0MCesEj7CbrQ==/com.quectel.esim-33nIW4JKCT5WvdpUhbwnhQ==/base.apk!liblpa.so (offset 0x3000) (ql_esim_verify_SMDPP_address+36) (BuildId: 6fe1cca9088309958c8cc0b6339cd2cfe2d35e4d)
2025-12-08 14:20:41.507 28752-28752 DEBUG crash_dump64 A #01 pc 000000000004ffc0 /data/app/~~Gd3Iea__Lz0MCesEj7CbrQ==/com.quectel.esim-33nIW4JKCT5WvdpUhbwnhQ==/base.apk!liblpa.so (offset 0x3000) (ql_esim_lpa_authenticate_server+708) (BuildId: 6fe1cca9088309958c8cc0b6339cd2cfe2d35e4d)
2025-12-08 14:20:41.507 28752-28752 DEBUG crash_dump64 A #02 pc 00000000000553dc /data/app/~~Gd3Iea__Lz0MCesEj7CbrQ==/com.quectel.esim-33nIW4JKCT5WvdpUhbwnhQ==/base.apk!liblpa.so (offset 0x3000) (ql_esim_lpa_profile_download_hdlr+456) (BuildId: 6fe1cca9088309958c8cc0b6339cd2cfe2d35e4d)
2025-12-08 14:20:41.507 28752-28752 DEBUG crash_dump64 A #03 pc 0000000000049f38 /data/app/~~Gd3Iea__Lz0MCesEj7CbrQ==/com.quectel.esim-33nIW4JKCT5WvdpUhbwnhQ==/base.apk!liblpa.so (offset 0x3000) (ql_ipa_main+1032) (BuildId: 6fe1cca9088309958c8cc0b6339cd2cfe2d35e4d)
2025-12-08 14:20:41.507 28752-28752 DEBUG crash_dump64 A #04 pc 0000000000009b70 /data/app/~~Gd3Iea__Lz0MCesEj7CbrQ==/com.quectel.esim-33nIW4JKCT5WvdpUhbwnhQ==/base.apk!libesim.so (offset 0xcb1000) (OSA_tskThrMain+164) (BuildId: 939b42dcd302d3c3165a0864ae9dcd6e10e44f45)
2025-12-08 14:20:41.507 28752-28752 DEBUG crash_dump64 A #05 pc 000000000006d8d0 /apex/com.android.runtime/lib64/bionic/libc.so (__pthread_start(void*)+196) (BuildId: 64eb5106bc8ae51d575bce9d5c64cec5)
2025-12-08 14:20:41.507 28752-28752 DEBUG crash_dump64 A #06 pc 000000000005fd34 /apex/com.android.runtime/lib64/bionic/libc.so (__start_thread+68) (BuildId: 64eb5106bc8ae51d575bce9d5c64cec5)
2025-12-08 14:20:41.537 853-853 tombstoned tombstoned E Tombstone written to: tombstone_21上述关键日志是在null pointer dereference,空指针了,然后具体空指针位置如下:
#00 pc 000000000004f140 /data/app/~~Gd3Iea__Lz0MCesEj7CbrQ==/com.quectel.esim-33nIW4JKCT5WvdpUhbwnhQ==/base.apk!liblpa.so (offset 0x3000) (ql_esim_verify_SMDPP_address+36) (BuildId: 6fe1cca9088309958c8cc0b6339cd2cfe2d35e4d)
二.使用addr2line工具查看具体位置
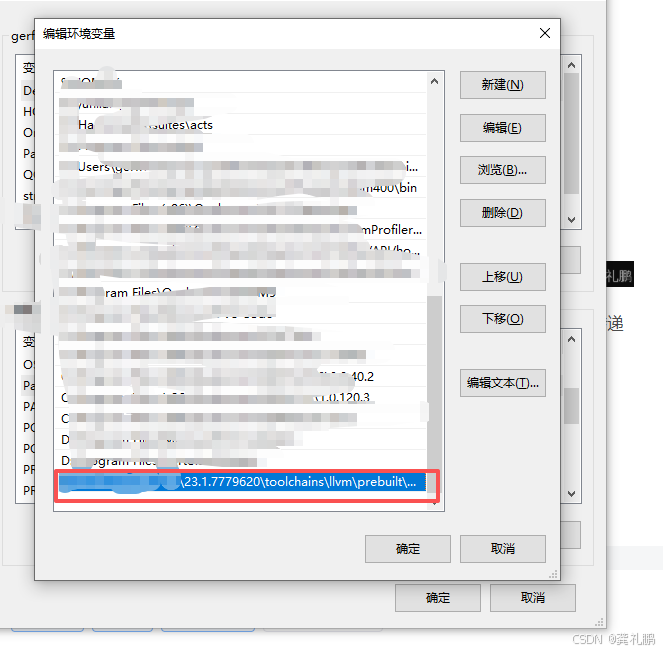
addr2line工具的位置在ndk工具里面,我这边工具位置在:xxx\23.1.7779620\toolchains\llvm\prebuilt\windows-x86_64\bin\llvm-addr2line.exe
具体用法示例:
基本用法
aarch64-linux-android-addr2line -e xxx.so 0x4f140
详细版本,显示更多信息
aarch64-linux-android-addr2line -e xxx.so -f -C -p 0x4f140
如下是具体的用法
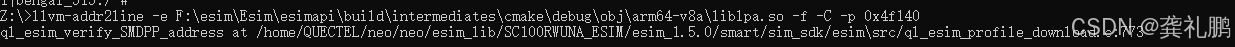
可以看出来是定位到773行空指针了,这里我们就去看为什么773行空指针了,我这里是因为传递进入的指针被回收了导致的
上述的指令如果想在任意位置使用就添加到环境变量里面即可,将xxx\23.1.7779620\toolchains\llvm\prebuilt\windows-x86_64\bin\路径添加到环境变量中