摘要
-
Akamai安全情报与响应小组(SIRT)发现了一项未经认证的命令注入,该事件此前在2019年部分披露。缺陷出在Vivotek遗留固件中的*/cgi-bin/admin/eventtask.cgi* 参数。最初被分配为CVE-2019-19936,但具体细节从未公开,且该CVE仍处于保留状态。
-
Vivotek已确认该漏洞影响了运行旧固件的旧硬件,并表示已在最新固件中进行修补。
-
我们对Vivotek Dome相机FD8154-F2型号进行了脆弱性测试。我们买了相机,然后在测试前重置到厂商默认设置。默认登录是root,摄像头也没有设置密码。
-
截至发布时,我们尚未看到该漏洞被积极利用。
-
某些固件型号默认为根账户密码为mpeg4soc,用户账户登录密码为CVE-ID CVE-2025-12592。
介绍
Akamai安全情报响应小组(SIRT)发现、审查和分析野外活跃威胁有两种方式------被动和主动。我们对针对全球定制蜜罐网络的样本进行逆向工程,并检查和调查固件以了解潜在漏洞。
随着补丁更新的连锁效应,固件的各个角落里可能隐藏着多个零日事件。这对物联网(IoT)设备(如IP摄像头)尤其危险,因为它们以基本管理员凭证闻名------尤其是当固件被厂商退役时。
一旦厂商停止更新,这些设备就会成为网络中的永久弱点,为攻击者提供可被利用的入侵路径,从而绕过现代防御。
发现经过
在一次固件调查中,我决定寻找公开的Vivotek固件中的新零日漏洞,因为有多个版本可用。我下载的固件是针对他们的老设备,厂商已不再支持,但它们在许多现有设备型号中仍然被广泛使用。
我用的是Vivotek Dome相机型号FD8154-F2进行分析,已重置为厂商默认设置(见图1)。

图1:Vivotek Dome相机型号FD8154-F2
我专注于 /usr/share/www/cgi-bin 目录,寻找可以通过网页请求访问的二进制文件。快速用二进制grep 搜索系统找到了 几个目标,第一个是eventtask.cgi。
通过查看带有radare2和IDA的二进制,你可以在图2生成的代码中看到变量s 被传递给包含用户POST请求输入的system()。
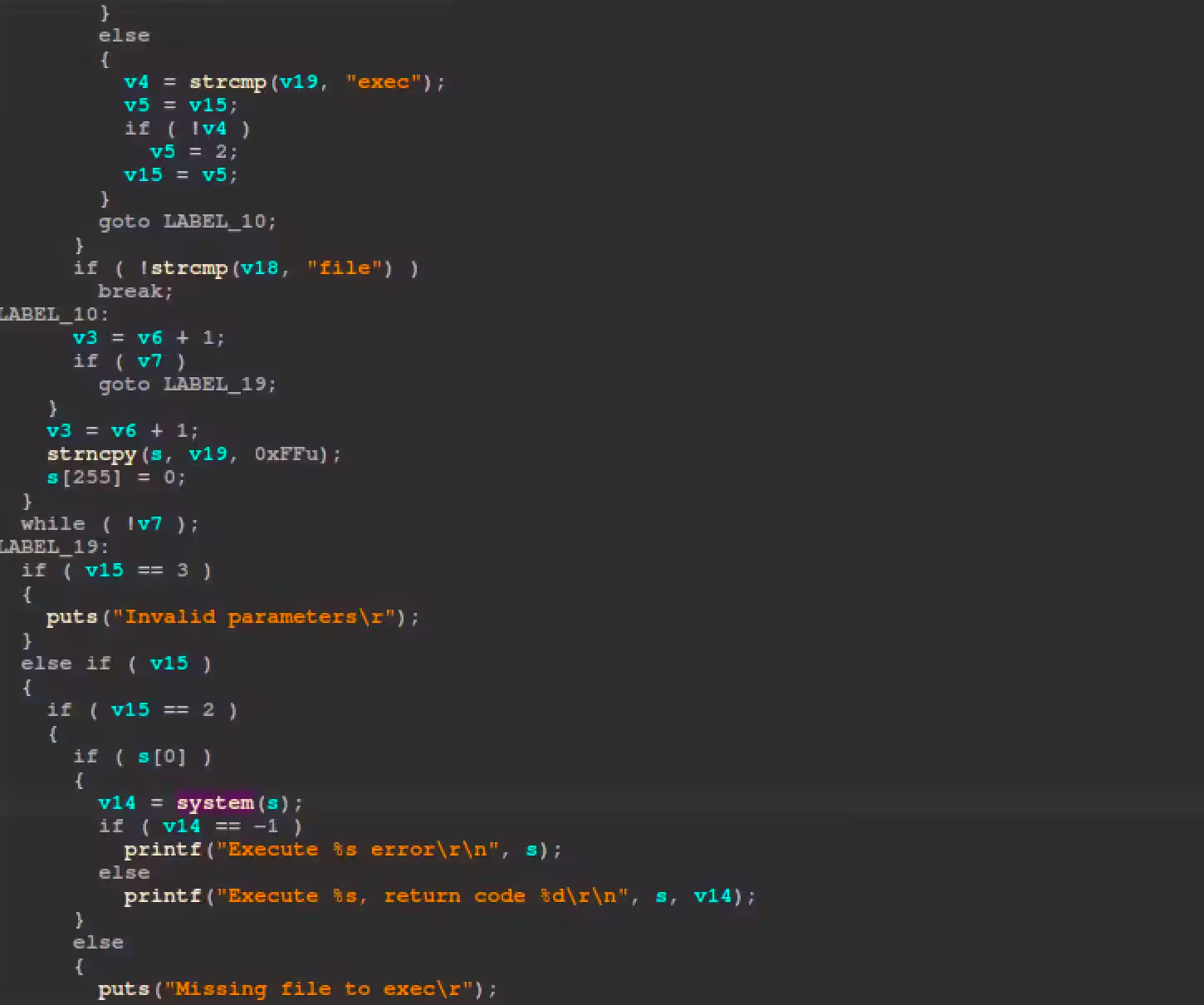
图2:生成代码显示用户输入传递给system()函数
开发过程
只需一个简单的curl命令,就能在易受攻击的设备上运行任意命令。我已遮蔽细节,因为该漏洞不会在不支持的固件中修复,但我提供了图3中执行运行时间命令的结果。
> POST /cgi-bin/admin/eventtask.cgi HTTP/1.1
> Host: 192.168.0.132
> User-Agent: curl/8.5.0
> Accept: */*
> Content-Length: 23
> Content-Type: application/x-www-form-urlencoded
>
< HTTP/1.1 200 OK
< Date: Tue, 04 Jan 2000 19:24:43 GMT
< Server: Boa/0.94.14rc21
< Accept-Ranges: bytes
< Connection: close
< 19:24:43 up 3 days, 19:20, load average: 0.98, 0.53, 0.41
< Content-type: text/plain
<
Execute uptime, return code 0脆弱性测试
默认情况下摄像头没有认证功能,所以一个简单的 curl 命令对eventtask.cgi 返回"缺少参数",很可能意味着你的设备存在漏洞
curl -v http://192.168.0.132/cgi-bin/admin/eventtask.cgi
* Trying 192.168.0.132:80...
* Connected to 192.168.0.132 (192.168.0.132) port 80
> GET /cgi-bin/admin/eventtask.cgi HTTP/1.1
> Host: 192.168.0.132
> User-Agent: curl/8.5.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Date: Mon, 03 Jan 2000 01:41:09 GMT
< Server: Boa/0.94.14rc21
< Accept-Ranges: bytes
< Connection: close
< Content-type: text/plain
<
Missing parameter此前部分披露
在网上搜索Vivotek eventtask.cgi CVE未找到任何结果,攻击日志中也未显示任何先前的利用尝试。然而,有人提醒我,Vivotek的一份.pdf文件中提到了eventtask.cgi和CVE-ID,但细节模糊,且CVE仍处于保留状态。看起来这个漏洞被发现了,但并未被记录和发布。
可能存在漏洞的设备型号
有相当数量的模型受到影响,其中许多较旧且不再由厂商支持,但在实际应用中仍然广泛使用。
由于受影响设备涵盖室内、室外、住宅、商业及其他领域,我制作了一系列表格,帮助识别各受影响型号,评估其脆弱性。
表1通过前缀标识设备类型和典型使用方式。
| Prefix | Device type | Typical use |
|---|---|---|
| FD | Fixed dome camera | Ceiling or wall-mounted domes for indoor/outdoor use |
| IB | Bullet camera | Cylindrical cameras, often with infrared and outdoor housings |
| IP | Box/compact network camera | Traditional rectangular box-style cameras |
| CC | Compact/panoramic camera | 180-degree panoramic or compact wall cameras |
| CD | Corner dome camera | Anti-ligature or corner-mounted for detention/industrial use |
| FE | Fisheye camera | 360-degree panoramic hemispheric lenses |
| IT | Transport/industrial camera | Ruggedized cameras for vehicles or transport systems |
| IZ | Zoom/PTZ camera (box style) | Motorized zoom lenses, often indoor installations |
| SD | Speed dome/PTZ camera | Fully motorized pan-tilt-zoom domes, often outdoor or high-end security |
| MA/MS | Multisensor camera | Multi-lens panoramic cameras (180-degree or 360-degree views) |
| MD | Mobile/compact dome camera | Smaller, vehicle, or ATM-type compact domes |
| PD/PZ | Pan/zoom cameras | PT or PTZ cameras for specific deployments |
| TB/VC/VS | Video server/encoder/decoder | For analog-to-IP video conversion or stream management |
| -VVTK (suffix) | Internal/OEM reference | Sometimes appended by Vivotek or partners for internal use |
Vivotek的数值系列大致展示了典型分辨率和生成(年代),如表2所示。
| Series | Typical resolution (Era) |
|---|---|
| 7xxx | Early 1 MP / VGA / D1 series (2008--2012) |
| 8xxx | 2--5 MP range, mainstream (2013--2018) |
| 9xxx | 5--12 MP, AI / Smart Stream / IR (2019--2024) |
| 81xx / 83xx / 91xx | Subseries within those generations (FD8136, FD9165, etc.) |
表2:Vivotek的分辨率和代号(年代)可用系列号表示
Vivotek 设备型号
表3显示了易受攻击的Vivotek设备型号。
| Model | Model | Model | Model |
|---|---|---|---|
| AS5336E-VVTK | BB5315-VVTK | BD5115-VVTK | BS5332-VVTK |
| CC8130-VVTK | CC8160-VVTK | CC8370-HV | CC8370-VVTK |
| CC8371-HV | CC9381-VVTK | CD8371-HNTV | CD8371-HNVF2 |
| CD8371-VVTK | FD7130-VVTK | FD7131-VVTK | FD7141-VVTK |
| FD7160-VVTK | FD8131-VVTK | FD8133-VVTK | FD8133-VVTK |
| FD8134-VVTK | FD8135-VVTK | FD8136-VVTK | FD8137-VVTK |
| FD8138-H | FD8151V-VVTK | FD8152-VVTK | FD8154-VVTK |
| FD8161-VVTK | FD8161-VVTK | FD8162-VVTK | FD8163-VVTK |
| FD8164-VVTK | FD8166A-N | FD8166AS-VVTK | FD8166A-VVTK |
| FD8166-VVTK | FD8167A-VVTK | FD8167-T | FD8167-VVTK |
| FD8168-VVTK | FD8169A_sample- | FD8169A_sample_v2- | FD8169A-VVTK |
| FD8169-VVTK | FD816BA-HT | FD816BA-VVTK | FD816B-HF2 |
| FD816B-VVTK | FD816CA-HF2 | FD816C-HF2 | FD8173-H |
| FD8177-H | FD8177-VVTK | FD8179-VVTK | FD8182-VVTK |
| FD8335-VVTK | FD8338-HV | FD8361-VVTK | FD8362E-VVTK |
| FD8363-VVTK | FD8365-HTV_v2_010600 | FD8365_v2-VVTK | FD8366-VVTK |
| FD8367A-V | FD8367A-VVTK | FD8367-TV | FD8367-V |
| FD8369A-V | FD8369A-VVTK | FD836BA-VVTK | FD836B-VVTK |
| FD836B-VVTK_vml3 | FD8372-VVTK | FD8373-EHV | FD8379-HV |
| FD8382-VVTK | FD8X69A-FD8X67A | FD8x6BA,IB836BA-VVTK | FD8X6B-IB836B_0101l |
| FD8x82,IB8382-VVTK | FD8x82-VVTK | FD9165-HT | FD9167-H |
| FD9167-HT | FD9167-VVTK | FD9171-HT | FD9171-VVTK |
| FD9181-VVTK | FD9187-H | FD9187-HT | FD9187-VVTK |
| FD9189-VVTK | FD9360-VVTK | FD9365-(E)HTV | FD9365-HTV |
| FD9365-VVTK | FD9367-VVTK | FD9368-VVTK | FD9371-HTV |
| FD9371-VVTK | FD9380-VVTK | FD9381-VVTK | FD9387-HTV |
| FD9387-HV | FD9387_sample_42331 | FD9388-HTV | FD9388-VVTK |
| FD9389-VVTK | FD9391-EHTV | FD9x67-VVTK | FE8171-VVTK |
| FE8171V-VVTK | FE8172-VVTK | FE8172-VVTK | FE8173-VVTK |
| FE8174-VVTK | FE8180-VVTK | FE8181-VVTK | FE8182-VVTK |
| FE9180-VVTK | FE9181-H | FE9181-VVTK | FE9182-VVTK |
| FE9191-VVTK | FE9381-VVTK | FE9382-VVTK | FE9391-VVTK |
| FE9582-VVTK | IB8156-VVTK | IB8168-VVTK | IB8338-H |
| IB8354-VVTK | IB8360-VVTK | IB8360-W | IB8367A-VVTK |
| IB8367-T | IB8367-VVTK | IB8369A-VVTK | IB8369-VVTK |
| IB836BA-HT | IB836BA-VVTK | IB8373-EH | IB8377-H |
| IB8377HT-VVTK | IB8379-VVTK | IB8382-F3 | IB8382-T |
| IB8382-VVTK | IB9360-VVTK | IB9365_87_LPR-W_49663_1 | IB9365-EHT |
| IB9365-EHT_0113a_sampleforiris | IB9365-HT | IB9365-LPR | IB9367-H |
| IB9367-HT | IB9367-VVTK | IB9368-VVTK | IB9371-VVTK |
| IB9380-VVTK | IB9381-VVTK | IB9387-H | IB9387-HT |
| IB9387-LPR | IB9387-LPR_fixed | IB9387-VVTK | IB9388-VVTK |
| IB9389-VVTK | IB9391-EHT | IB9391-VVTK | IP7130-VVTK |
| IP7138-VVTK | IP7142-VVTK | IP7151-VVTK | IP7152-VVTK |
| IP7153-VVTK | IP7154-VVTK | IP7160-VVTK | IP7161-VVTK |
| IP7330-VVTK | IP7361-VVTK | IP8130-VVTK | IP8131-VVTK |
| IP8131W-VVTK | IP8132-VVTK | IP813x-VVTK | IP8151-VVTK |
| IP8152-VVTK | IP8152-VVTM | IP8160_1 | IP8160-VVTK |
| IP8160-W | IP8160W-VVTK | IP8161-VVTK | IP8162-VVTK |
| IP8166-VVTK | IP8172-VVTK | IP8330-VVTK | IP8331-VVTK |
| IP8331-VVTK | IP8332-VVTK | IP8335-VVTK | IP8336-VVTK |
| IP8337-VVTK | IP8352-VVTK | IP8362-VVTK | IP8364-VVTK |
| IP8372-VVTK | IP9165-0100f_013 | IP9165-0100f_016 | IP9165-0100f_017 |
| IP9165-0100f_018 | IP9165-0100f_019 | IP9165-0100f_020 | IP9165-VVTK |
| IP9167-HT | IP9167-VVTK | IP9171-HP | IP9171-VVTK |
| IP9172-LPC | IP9181-VVTK | IP9191-VVTK | IT9360-VVTK |
| IT9368-VVTK | IT9380-VVTK | IT9388-VVTK | IT9389-VVTK |
| IZ9361-EH | IZ9361-VVTK | MA8391-VVTK | MA9321-VVTK |
| MA9322-VVTK | MD7560-COGN | MD7560-VVTK | MD8531-VVTK |
| MD8562-VVTK | MD8563-EHF2 | MD8563-EHF4 | MD8563-VVTK |
| MD8565-N | MS8391-VVTK | MS9321-VVTK | MS9390-HV |
| MS9390-VVTK | PD8136-VVTK | pt8133-VVTK | PT8133-VVTK |
| PZ7131-VVTK | PZ71X1-VVTK | PZ71X2-VVTK | PZ81XX-VVTK |
| SD81X1-VVTK | SD8332E-VVTK | SD8333-E | SD8362-VVTK |
| SD8363E-VVTK | SD8363-VVTK | SD8364E-VVTK | SD8364-VVTK |
| SD83X3-VVTK | SD83X6E-VVTK | SD83X6-VVTK | SD9161-H |
| SD9361(2)-EH(L) | SD9361-EHL | SD9361-VVTK | SD9362(4)(6)-EH |
| SD9362-EH | SD9362-EHL | SD9362-EHL_37544_010600 | SD9362-VVTK |
| SD9363(4)-EH(L) | SD9363-EHL | SD9363-VVTK | SD9364-EH |
| SD9364-EHL | SD9364_v2-VVTK | SD9364-VVTK | SD9365(6)-EH(L) |
| SD9365-EHL | SD9365-VVTK | SD9366-EHL | SD9366_v2-VVTK |
| SD9366-VVTK | SF8172-VVTK | TB9330-VVTK | VC8101-VVTK |
| VS8100-v2 | VS8100-V2 | VS8100-v2_sample_41102 | VS8100-VVTK |
| VS8101-VTPE | VS8101-VVTK | VS8102-AGVI | vs8102-VVTK |
| VS8102-VVTK | VS8401-VVTK | VS8801-VVTK | VVTK-IB938 |
表3:受影响的Vivotek设备(注:固件版本0100c至0305a4存在漏洞;这些版本已被厂商退役,不会更新)
带有默认密码的相机型号
表4标明了易受攻击的Vivotek设备型号,默认密码为mpeg4soc。
|--------------------|--------------------|--------------------|--------------------|-------------------|
| FD7131-VVTK-0100g | FD7131-VVTK-0201c | FD7131-VVTK-0300b | FD7141-VVTK-0200a | IP7131-VVTK-0200a |
| IP7133-VVTK-0201a | IP7133-VVTK-0202a | IP7133-VVTK-0203a | IP7134-VVTK-0202a | IP7135-VVTK-0100i |
| IP7135-VVTK-0101b | IP7135-VVTK-0199z | IP7135-VVTK-0400a | IP7137-VVTK-0199z | IP7137-VVTK-0200a |
| IP7137-VVTK-0202b | IP7137-VVTK-0300a | IP7137-VVTK-0302a | IP7137-VVTK-0401a | IP7138-VVTK-0201k |
| IP7142-VVTK-0300a | IP7142-VVTK-0302c | IP7151-VVTK-0200g | IP7152-VVTK-0200c | IP7153-VVTK-0200c |
| IP7153-VVTK-0300a | IP7154-VVTK-0200a | IP7330-VVTK-0101c | IP7330-VVTK-0200b | IP7330-VVTK-0300b |
| IP8131-VVTK-0100e1 | IP8131-VVTK-0100e2 | IP8131-VVTK-0100f | IP8131W-VVTK-0100e | PT7135-VVTK-0400a |
| PT7137-TCON-0101b | PT7137-VVTK-0400a | PT7137-VVTK-0400b | PT7137-VVTK-0500a | PT7137-VVTK-0500b |
| PZ7131-VVTK-0100b | PZ7131-VVTK-0200a | PZ71X1-VVTK-0201a | PZ71X1-VVTK-0201a1 | PZ71X2-VVTK-0201a |
| SD73X3-VVTK-0102a | SD73X3-VVTK-0103c | SD73X3-VVTK-0103cb | TC5330-VVTK-0200a | TC5332-TCVV-0101b |
| TC5333-TCVV-0101b | TC5633-TCVV-0200a | TC5633-VVTK-0200a | VS7100-VVTK-0101e | VS7100-VVTK-0200c |
| VS7100-VVTK-0301b3 | | | | |
表4。默认密码为mpeg4soc的设备列表
YARA规则
图5展示了利用尝试匹配的YARA规则。
rule EventTask_CGI_CVE_2019_19936_HTTP
{
meta:
author = "Akamai SIRT"
purpose = "detection of requests/logs referencing eventtask.cgi exploitation"
strings:
$endpoint = "/cgi-bin/admin/eventtask.cgi" nocase
$token = "eventtask" nocase
$method = "method=" nocase
$file = "file=" nocase
$execword = "exec" nocase
condition:
// match the endpoint/token plus at least one exec-ish indicator,
// OR match method/file plus exec/system tokens (covers truncated lines)
( ($endpoint or $token) and ( $method or $file or $execword )
or ( $method and ($file or $execword) ))
}图5:YARA规则将匹配剥削尝试
结论
随着老旧的物联网设备老化并不再被制造商支持,它们依然对安全构成重大威胁。这些设备------从摄像头和路由器到工业传感器和智能家居设备------设计时安全功能有限,且常依赖已不再维护或针对新发现漏洞进行修补的过时固件。
一旦厂商停止更新,这些设备就会成为网络中的永久弱点,为攻击者提供可被利用的入侵路径,从而绕过现代防御。遗留的物联网设备经常部署在更换成本高昂或运营中断的关键环境中,导致组织尽管存在风险,仍选择保持其在线状态。
因此,未修补的遗留物联网系统依然是持续存在的攻击面,可用于数据泄露、横向移动或被僵尸网络纳入------这使得其识别、隔离或安全退役成为现代网络安全战略中至关重要的一环。