21 reverseMe


复制图片,在线ocr识别,https://ocr.wdku.net/,都不费眼睛。
22 misc_pic_again
┌──(holyeyes㉿kali2023)-[~/Misc/tool-misc/zsteg]
└─$ zsteg misc_pic_again.png
imagedata ... text: "$$KaTeX parse error: Undefined control sequence: \0 at position 60: ...t metric data (\̲0̲34,\225\370lC\2...\314\004_4\321\345G\231Dn\005\230\230\335\331\305_\317\217\262)\311\311\265\360\262-\336X\204\300\251\2612\023<\247m7\313\237\213\253\336\357\305S\277;\2356\014<\362\244\312\266\227\016\264\304\0200\235\200Y\316\357r;\321)
b1,rgb,lsb,xy ... file: Zip archive data, at least v2.0 to extract, compression method=deflate
b2,g,lsb,xy ... text: "A@qs{cZ;"
b2,rgb,msb,xy ... file: OpenPGP Public Key
b3,r,lsb,xy ... file: gfxboot compiled html help file
b3,rgb,lsb,xy ... text: "Kd"Yl*\6"
b4,r,lsb,xy ... file: Targa image data (0) 256 x 1 x 16 - 1-bit alpha "\021\020\020\021\001\020"
b4,g,lsb,xy ... text: "DDTDDD""DE"0ED"3vgtEgfffDC2 "
b4,g,msb,xy ... text: """*"""DD""
b4,b,lsb,xy ... text: "vUDDD"# "
b4,bgr,msb,xy ... file: OpenPGP Secret Key
┌──(holyeyes㉿kali2023)-[~/Misc/tool-misc/zsteg]
└─$ zsteg -e b1,rgb,lsb,xy misc_pic_again.png > misc_pic_again.zip
┌──(holyeyes㉿kali2023)-[~/Misc/tool-misc/zsteg]
└─$

hctf{scxdc3tok3yb0ard4g41n~~~}
23 hong
┌──(holyeyes㉿kali2023)-[~/Misc/timu/zulu]
└─$ foremost hong.mp3
Processing: hong.mp3
|*|output目录下打开相关文件

BCTF{cute&fat_cats_does_not_like_drinking}
Test-flag-please-ignore


flag{hello_world}
25 János-the-Ripper

flag{ev3n::y0u::bru7us?!}
26 Erik-Baleog-and-Olaf
经过对比,发现这个文件是一张PNG格式的图片,所以我们将他的后缀改为PNG即可


python
from PIL import Image
exp = Image.open("22kurzm.png") # 从010中最后一行网站下载的图片
cipher = Image.open("stego100.png") # 题目给的图片
new = Image.new("RGBA", size=exp.size)
for i in range(640):
for j in range(480):
y_p = exp.getpixel((i, j))
c_p = cipher.getpixel((i, j))
if y_p == c_p:
pass
else:
new.putpixel((i,j), (255,255,255))
new.save("result.png")
flag{#justdiffit}
27 can_has_stdio?
https://sange.fi/esoteric/brainfuck/impl/interp/i.html


flag{esolangs_for_fun_and_profit}
28 m1


ZmxhZ3tsNURHcUYxcFB6T2IyTFU5MTlMTWFCWVM1QjFHMDFGRH0=
flag{l5DGqF1pPzOb2LU919LMaBYS5B1G01FD}
29 碎纸机11
┌──(holyeyes㉿kali2023)-[~/.../timu/zulu/碎纸机11/images]
└─$ python suzhiji.py
┌──(holyeyes㉿kali2023)-[~/.../timu/zulu/碎纸机11/images]
└─$
python
import glob
import PIL.Image as Image
import os
import pandas as pd
def list_file():
fileList = []
#for fileName in glob.glob("*.png",key=os.path.getmtime):
# fileList.append(fileName)
fileList=sorted(glob.glob("*.png"),key=os.path.getmtime)
return (fileList)
def image_compose():
to_image = Image.new('RGB', (IMAGE_COLUMN * IMAGE_SIZE, IMAGE_ROW * IMAGE_SIZE)) # 创建一个新图
# 循环遍历,把每张图片按顺序粘贴到对应位置上
for y in range(1, IMAGE_ROW + 1):
for x in range(1, IMAGE_COLUMN + 1):
from_image = Image.open(IMAGES_PATH + image_names[IMAGE_COLUMN * (y - 1) + x - 1]).resize(
(IMAGE_SIZE, IMAGE_SIZE), Image.ANTIALIAS)
to_image.paste(from_image, ((x - 1) * IMAGE_SIZE, (y - 1) * IMAGE_SIZE))
return to_image.save(IMAGE_SAVE_PATH) # 保存新图
def combin(imgs):
img0=Image.open(imgs[0])
width = img0.width #图片的宽
height = img0.height
size=(width*len(imgs),height)#图片的高
saveimg= Image.new("RGB",size)
#saveimg.save('test.png')
savepix=saveimg.load()
for i in range(len(imgs)):
img=Image.open(imgs[i])
imgSize = img.size
width = img.width #图片的宽
height = img.height #图片的高
#print(w, h, f)
img=img.convert("RGB")
for x in range(width):
for y in range(height):
data=(img.getpixel((x,y)))
#print(data)
saveimg.putpixel(((x+i*width),y),data)
saveimg.show()
saveimg.save('test.png')
def savepix():
with open ('2.txt')as f :
im=f.read()
imgs=im.split()
img0=Image.open(imgs[0])
imgSize = img0.size
data0={}
width = img0.width #图片的宽
height = img0.height
print(width ,height)
for i in range(len(imgs)):
img=Image.open(imgs[i])
#img=img.convert("RGB")
print(imgs[i])
data0[imgs[i]]=[]
for x in range(1):
for y in range(height):
data=img.getpixel((x,y))
try:
data=data-data0[imgs[0]][y]
except:
pass
data0[imgs[i]].append(data)
data0[imgs[i]+"2"]=[]
for x in range(img.width-1,img.width):
for y in range(height):
data=img.getpixel((x,y))
data0[imgs[i]+"2"].append(data)
s=pd.DataFrame(data0)
s.to_csv(f"save2.csv",encoding="utf_8_sig")
if __name__=="__main__":
imgs=list_file()
combin(imgs)放到图片的目录里面运行

flag{You Can Repair A Picture From Splices Baesd On Entropy}
30 Training-Stegano-1
steganoI


31 pure_color

──(holyeyes㉿kali2023)-[~/Misc/tool-misc]
└─$ java -jar Stegsolve.jar
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true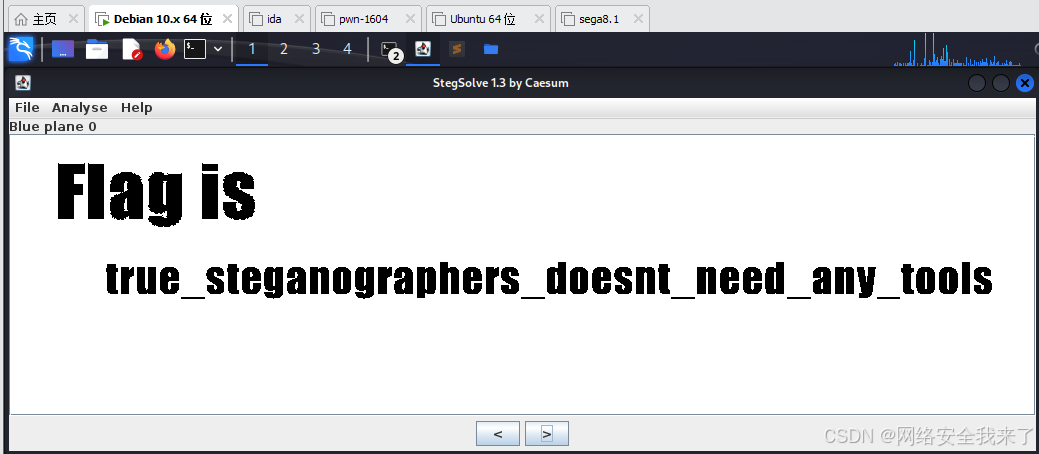
flag{true_steganographers_doesnt_need_any_tools}