免责声明:内容仅供学习参考,请合法利用知识,禁止进行违法犯罪活动!
本次游戏没法给
内容参考于:微尘网络安全
上一个内容:14.Windows驱动-ida和Windbg动静结合调试
省流总结:
首先通过索引(eax就是索引,3环传进来的)得到一个函数列表的首地址偏移,这里的edi是0也就是ssdt里的第一个数据就是函数列表的首地址
然后函数列表的首地址存放的是函数的偏移,然后通过下图红框的代码读取获取函数偏移
然后函数首地址+函数偏移得到函数地址,就完了
上一个内容通过Windbg找到了SSDT(KeServiceDescriptorTable 和KeServiceDescriptorTableShadow )的调用过程,本次就来找它索引的解密
首先使用Windbg来到下图红框的函数,KiSystemServiceStart
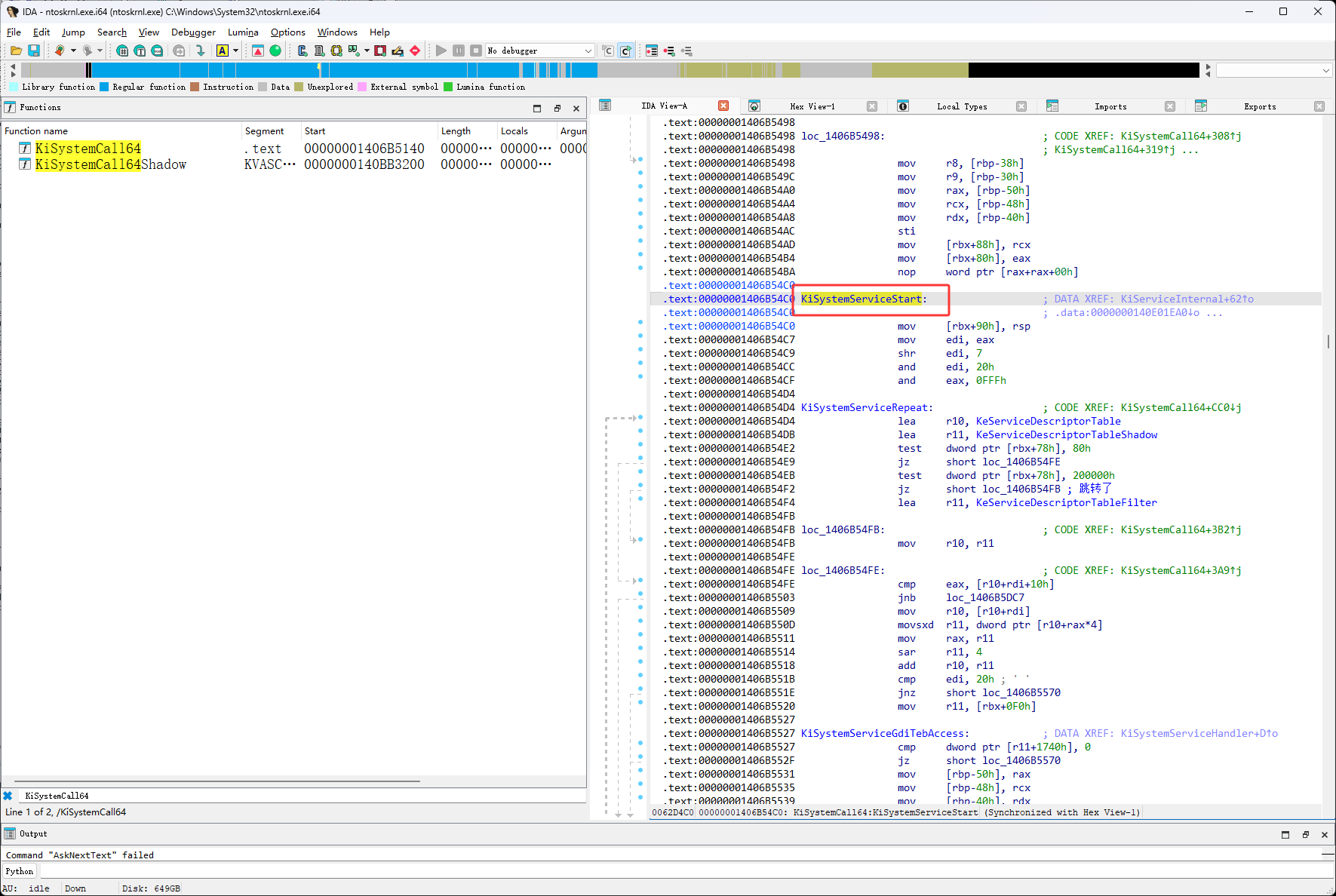
在下图红框位置输入u KiSystemServiceStart L20,然后按回车
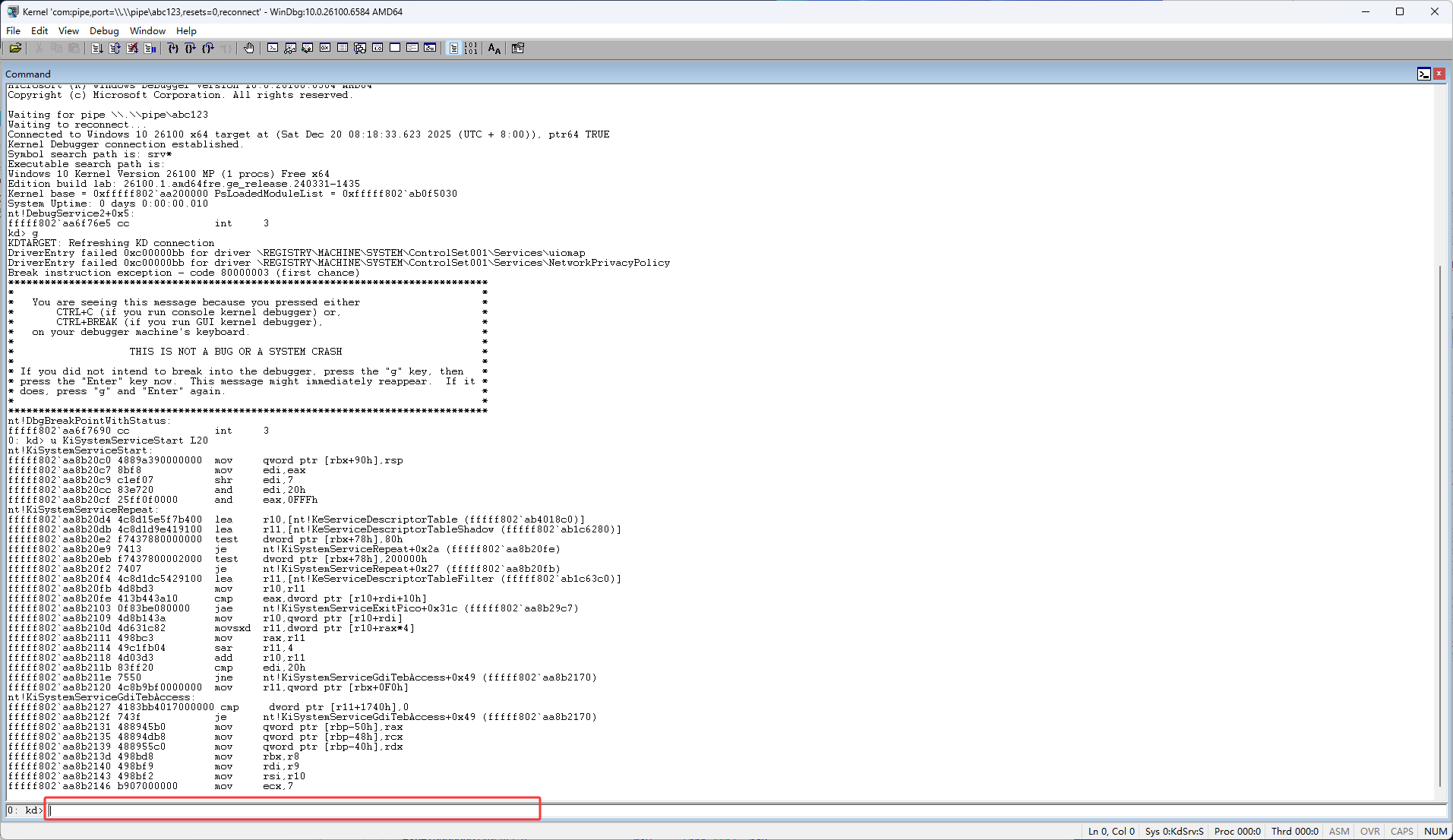
上方指令执行完后
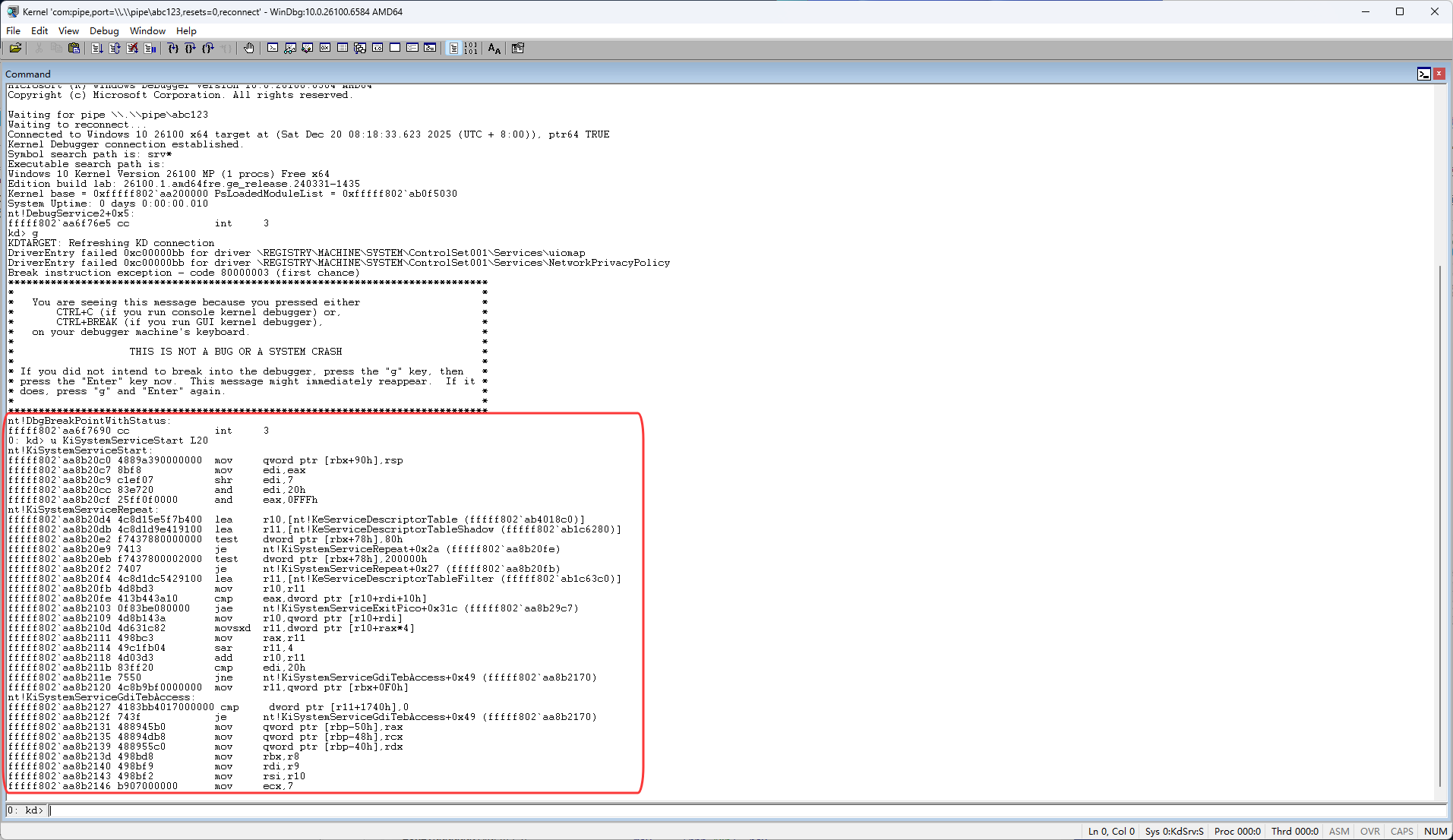
然后找到KiSystemServiceStart的地址
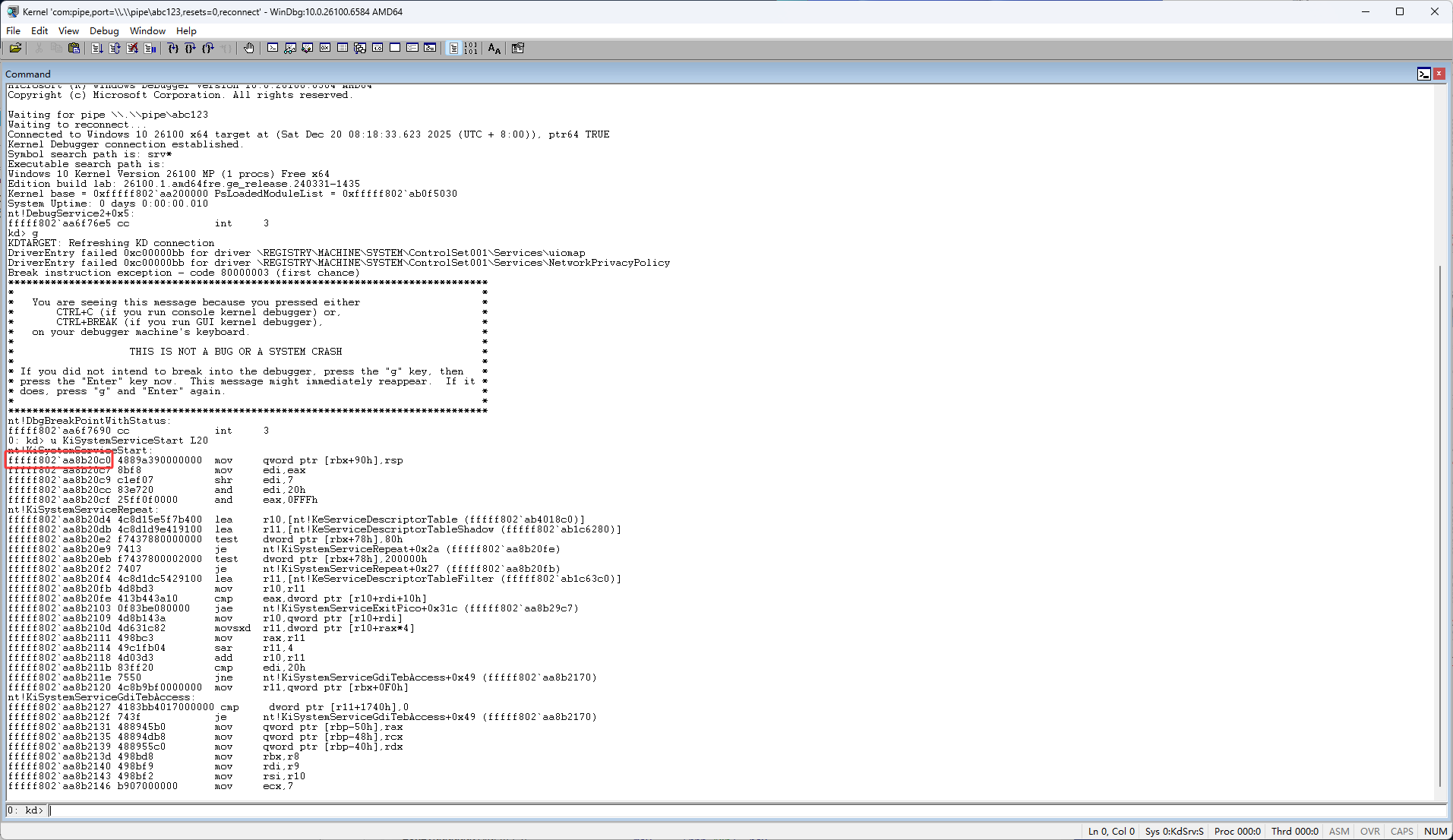
然后设置断点
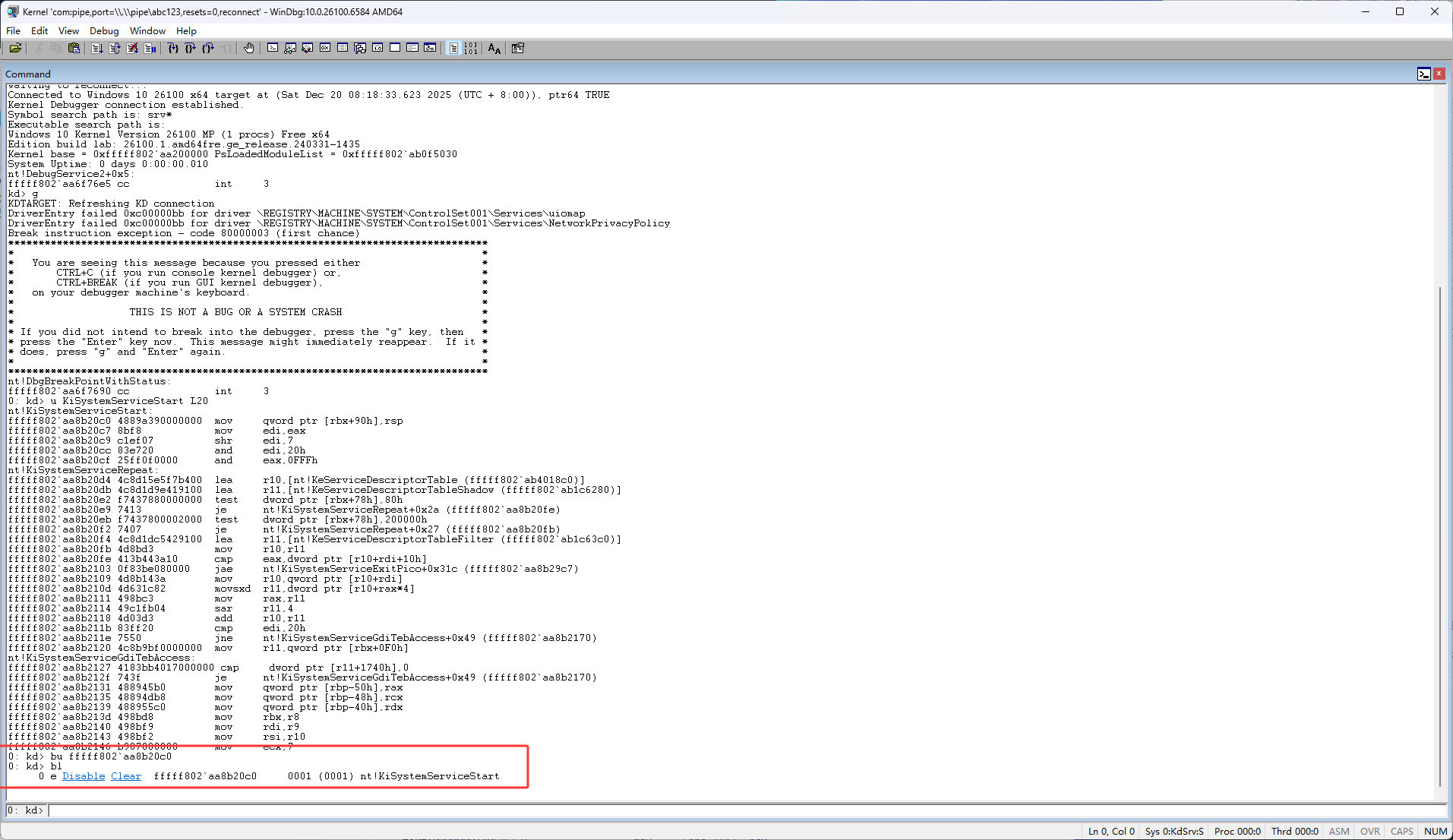
然后输入g让操作系统跑起来,然后等待断到KiSystemServiceStart函数上
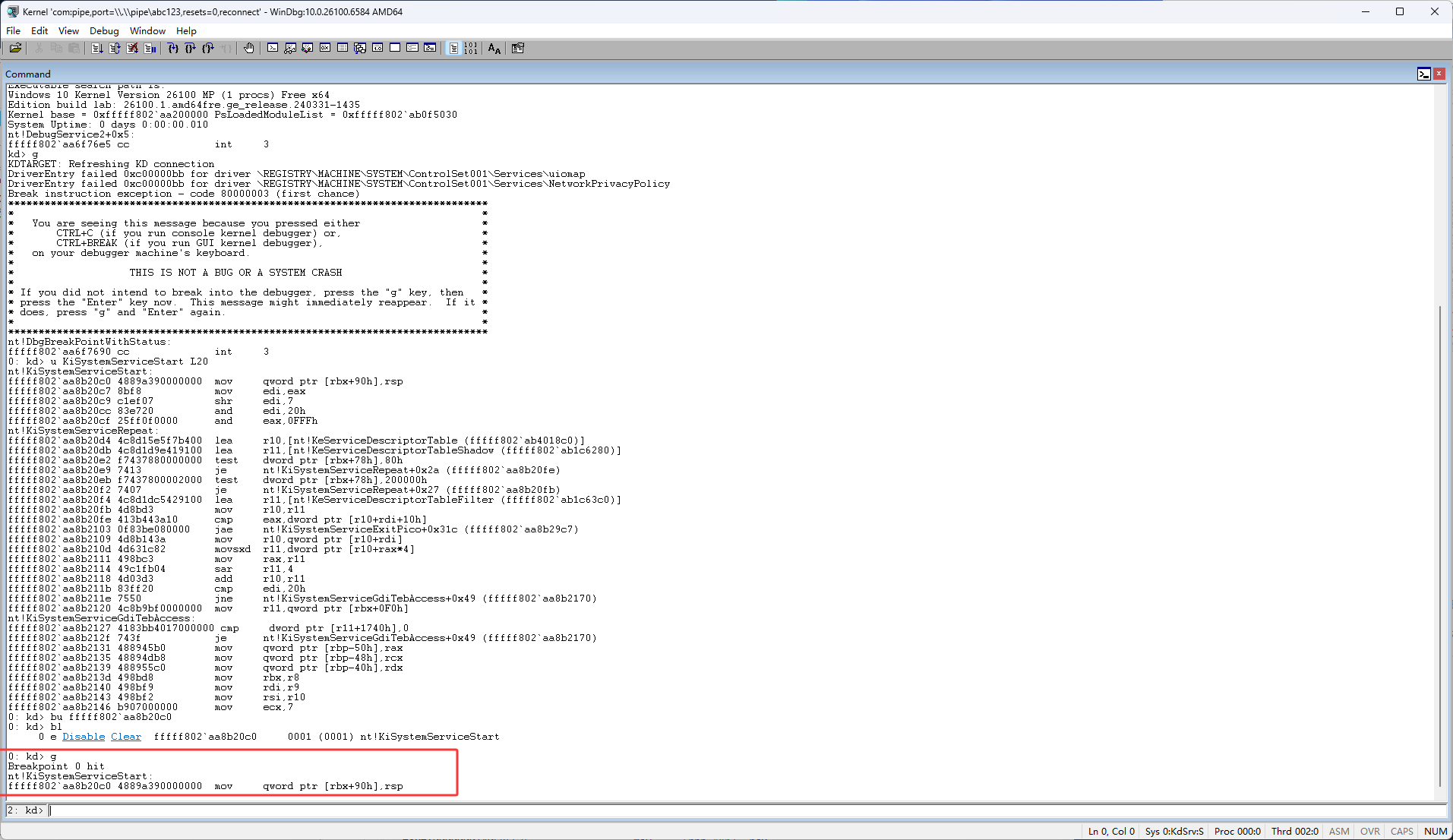
然后先介绍一下情况,下图红框的eax就是我们从3环传的索引,比如之前的ReadProcessMemory传的是3F,OpenProcess传的是0x26,这里的代码会通过eax进行一些列的操作最终得到0环中函数的地址,下面就一步一步调试代码,看看它是怎样得到的函数地址,又是怎样调用的
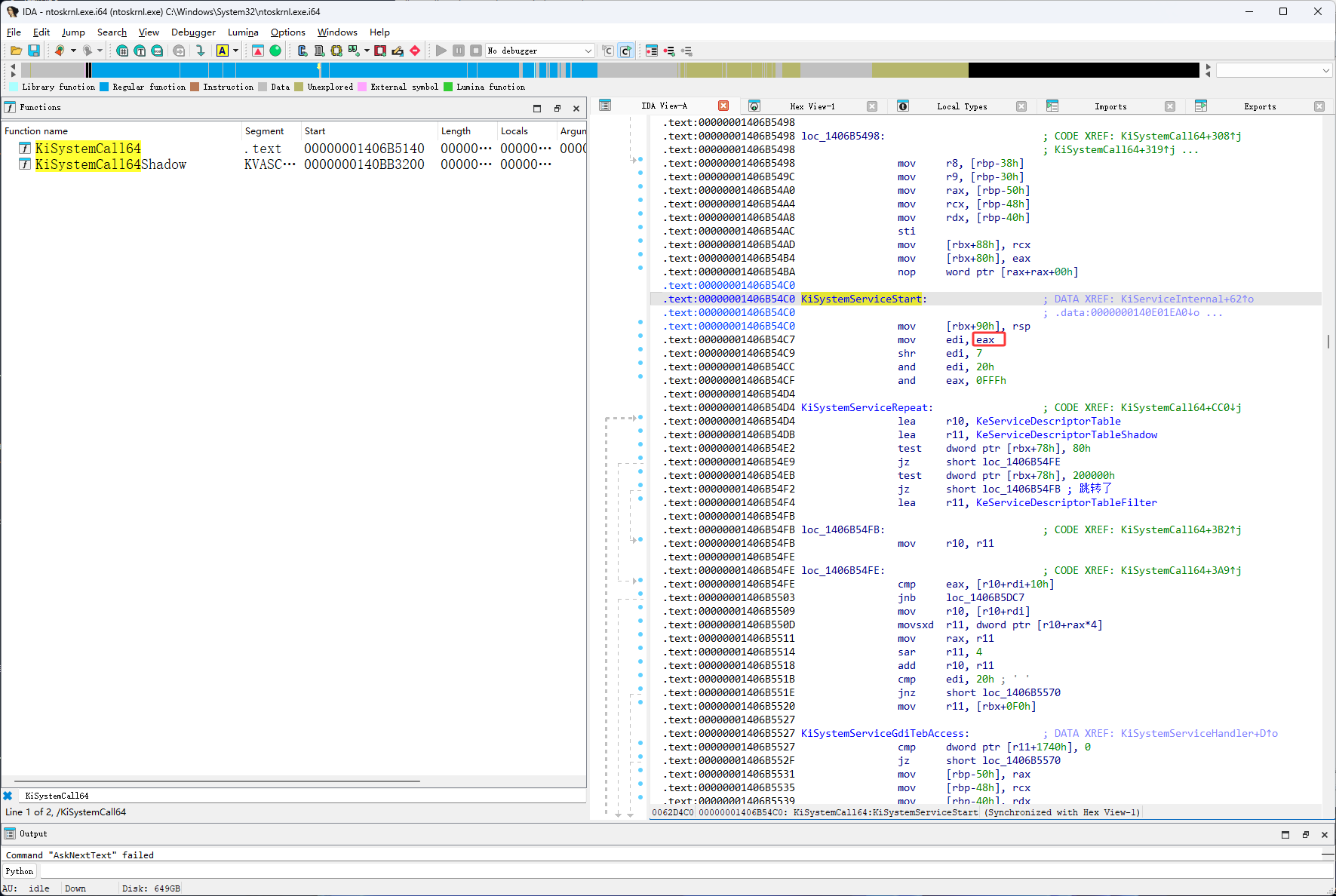
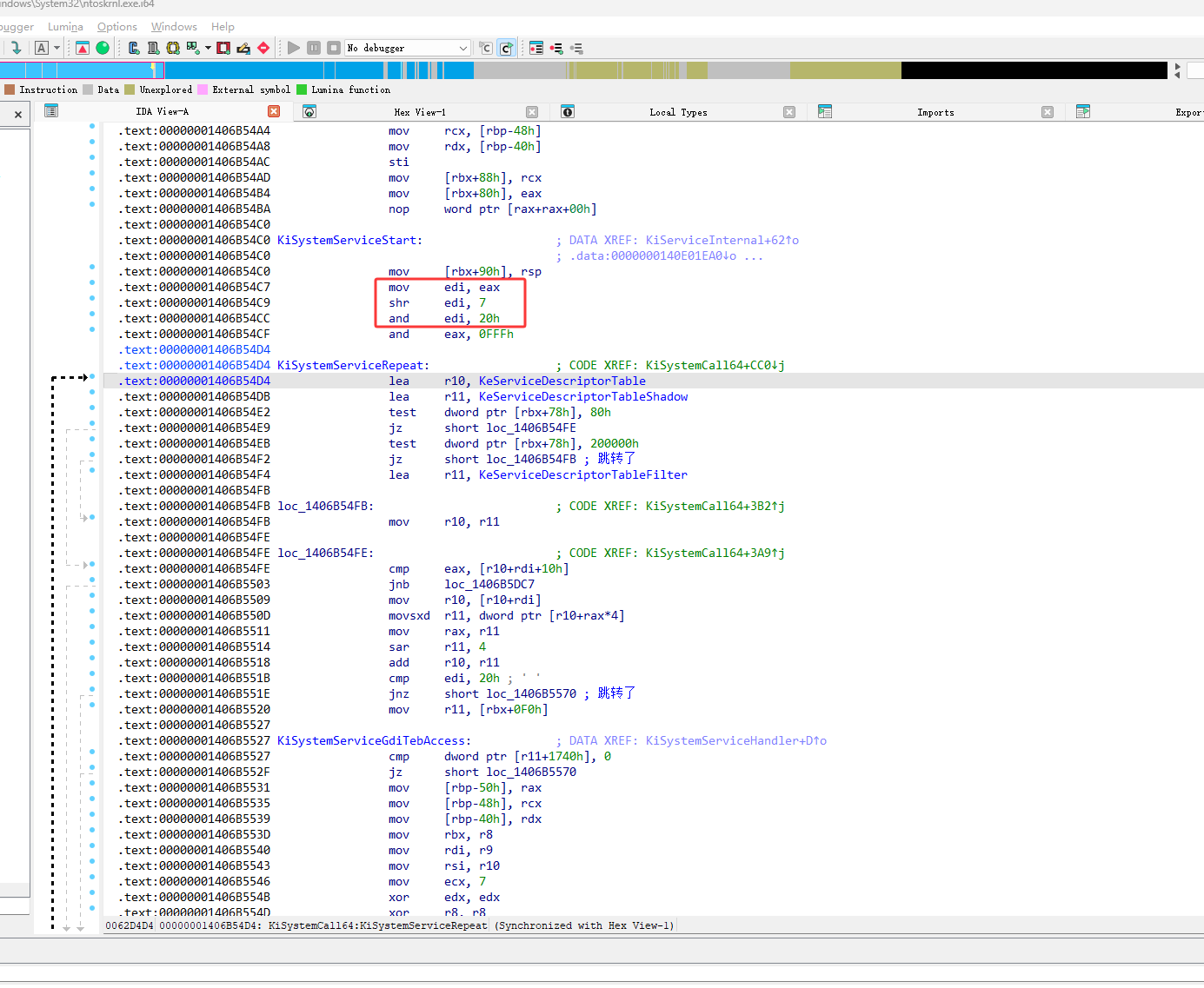
这里要把eax的值给edi,注意这时还没有执行 mov edi,eax 这个代码
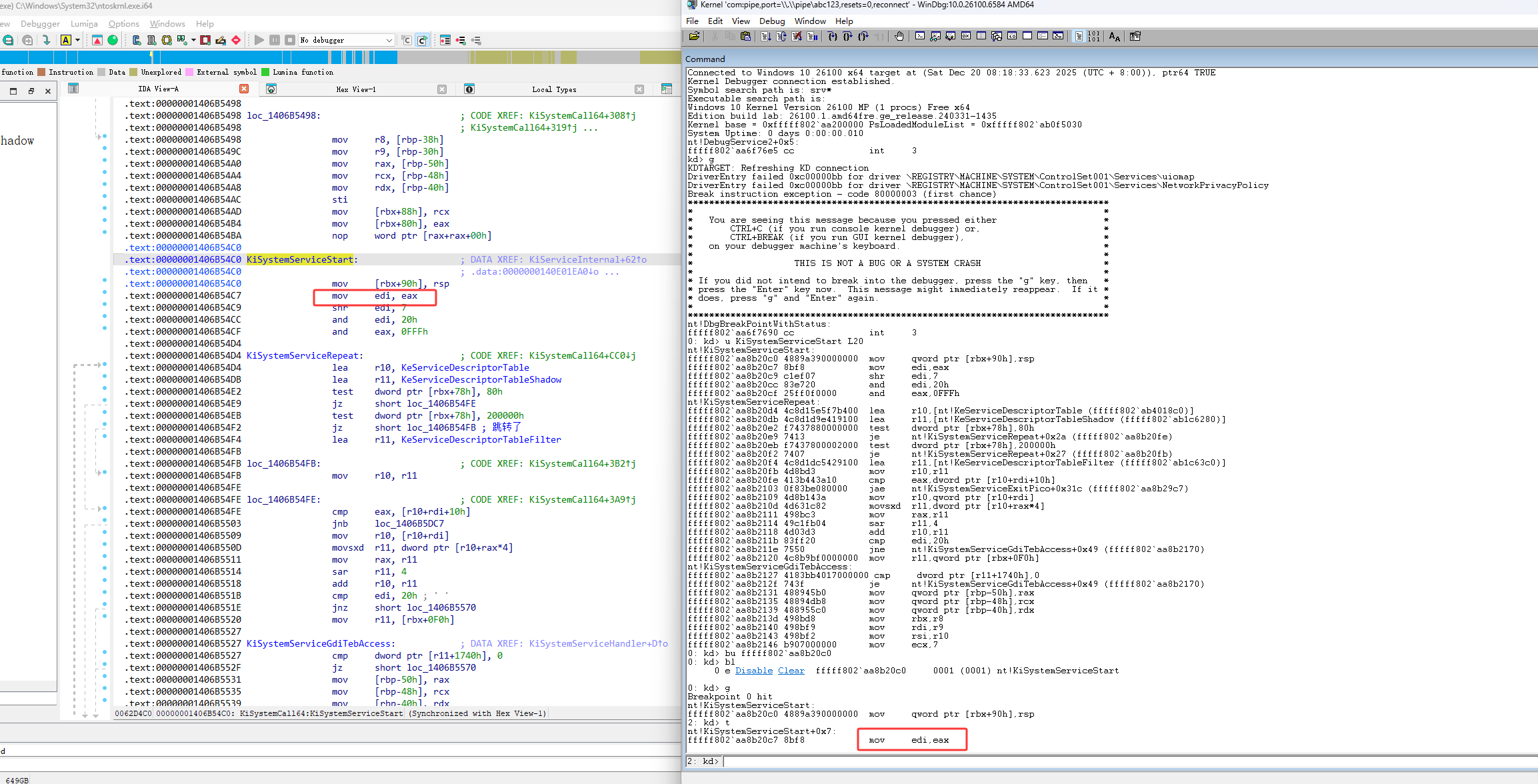
然后输入r查看寄存器,这时的eax是3e
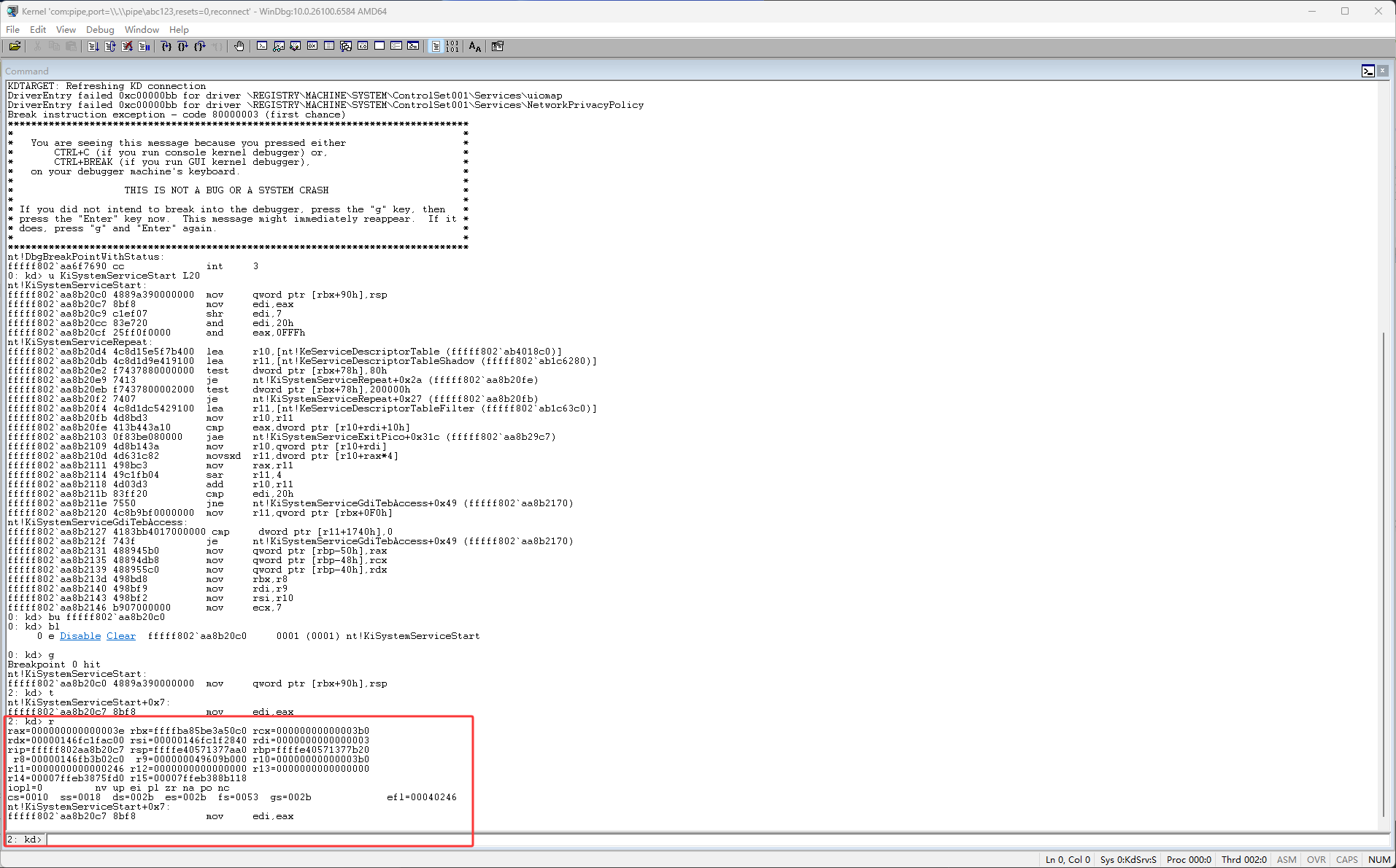
然后继续按F11,单步执行代码,执行了 mov edi,eax 这个代码 edi的值也变成了3e
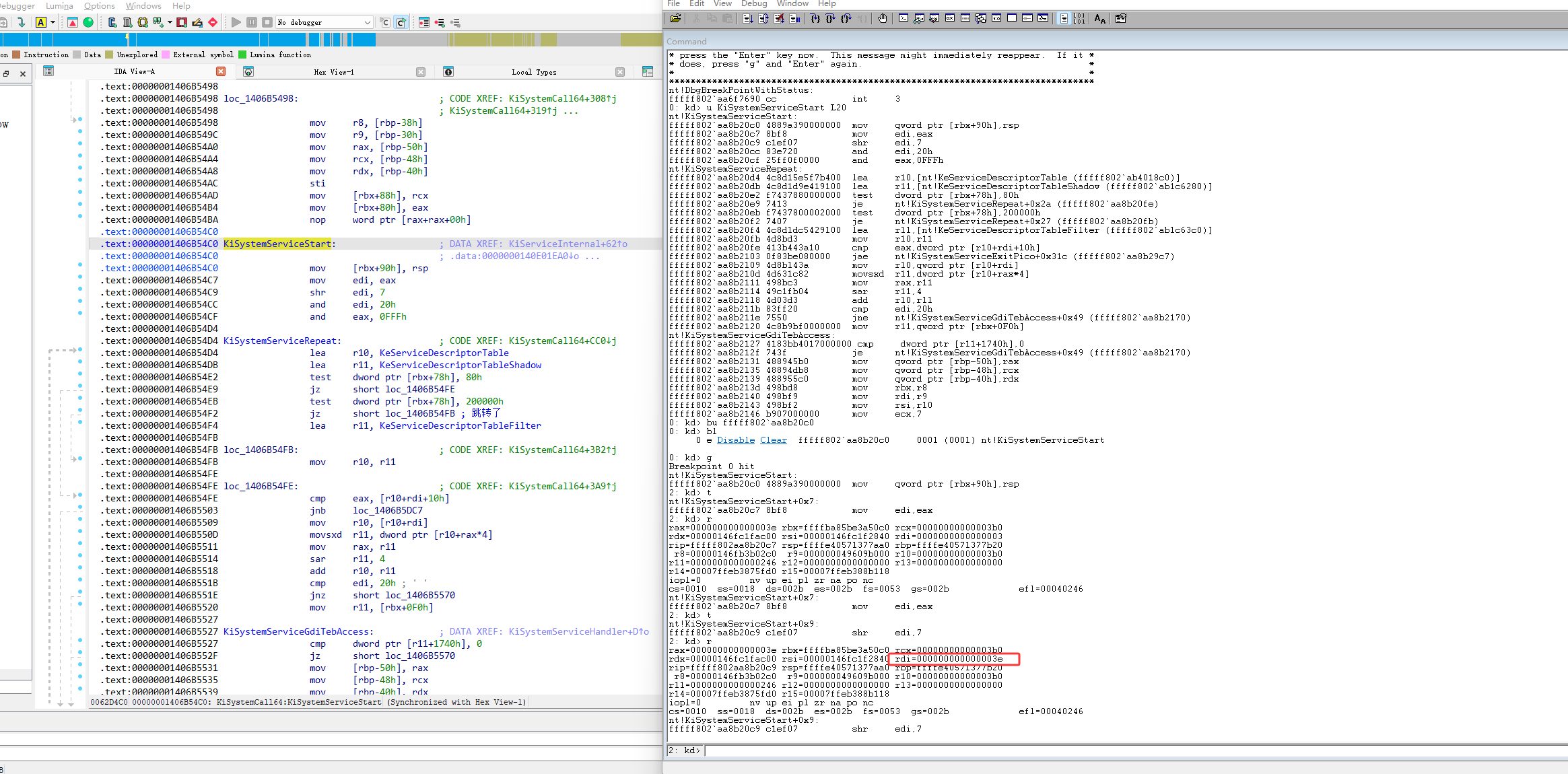
然后按F11继续单步执行,然后就执行了 shr edi,7,shr指令是右移操作,右移完edi的值就变成了0
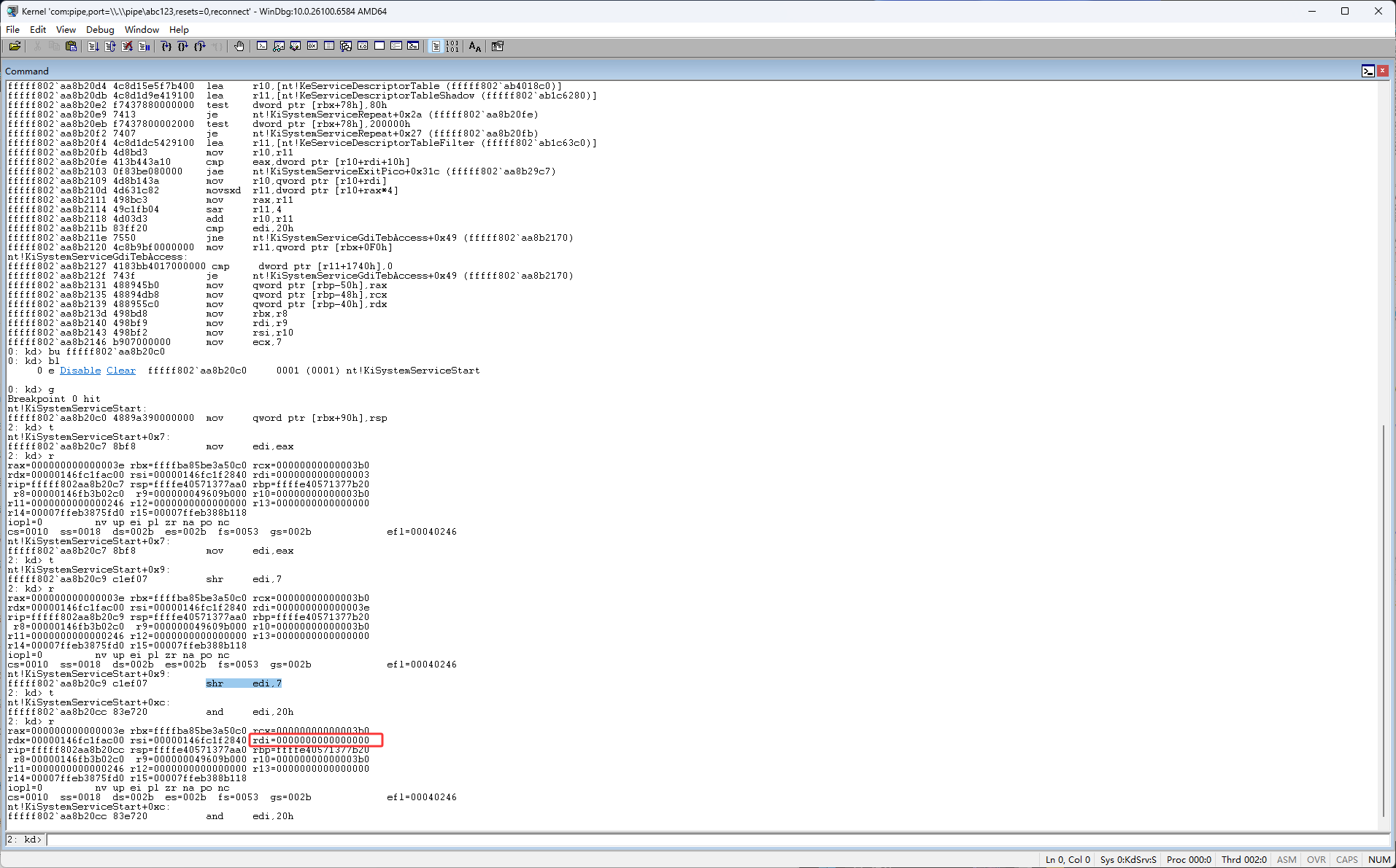
下图红框的两个代码执行完edi的还是0
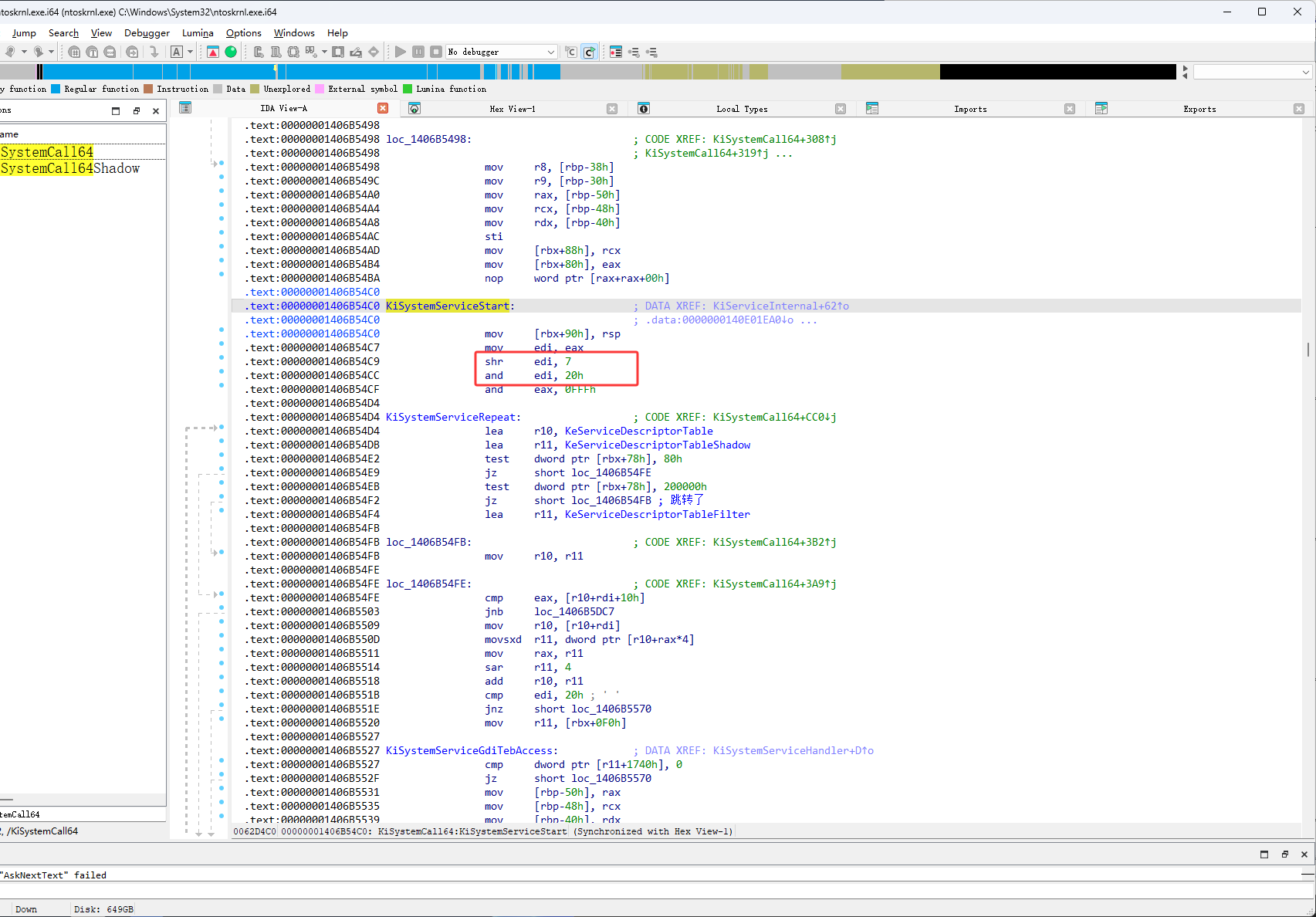
下图红框的eax的是执行完and eax,0FFFh后的值
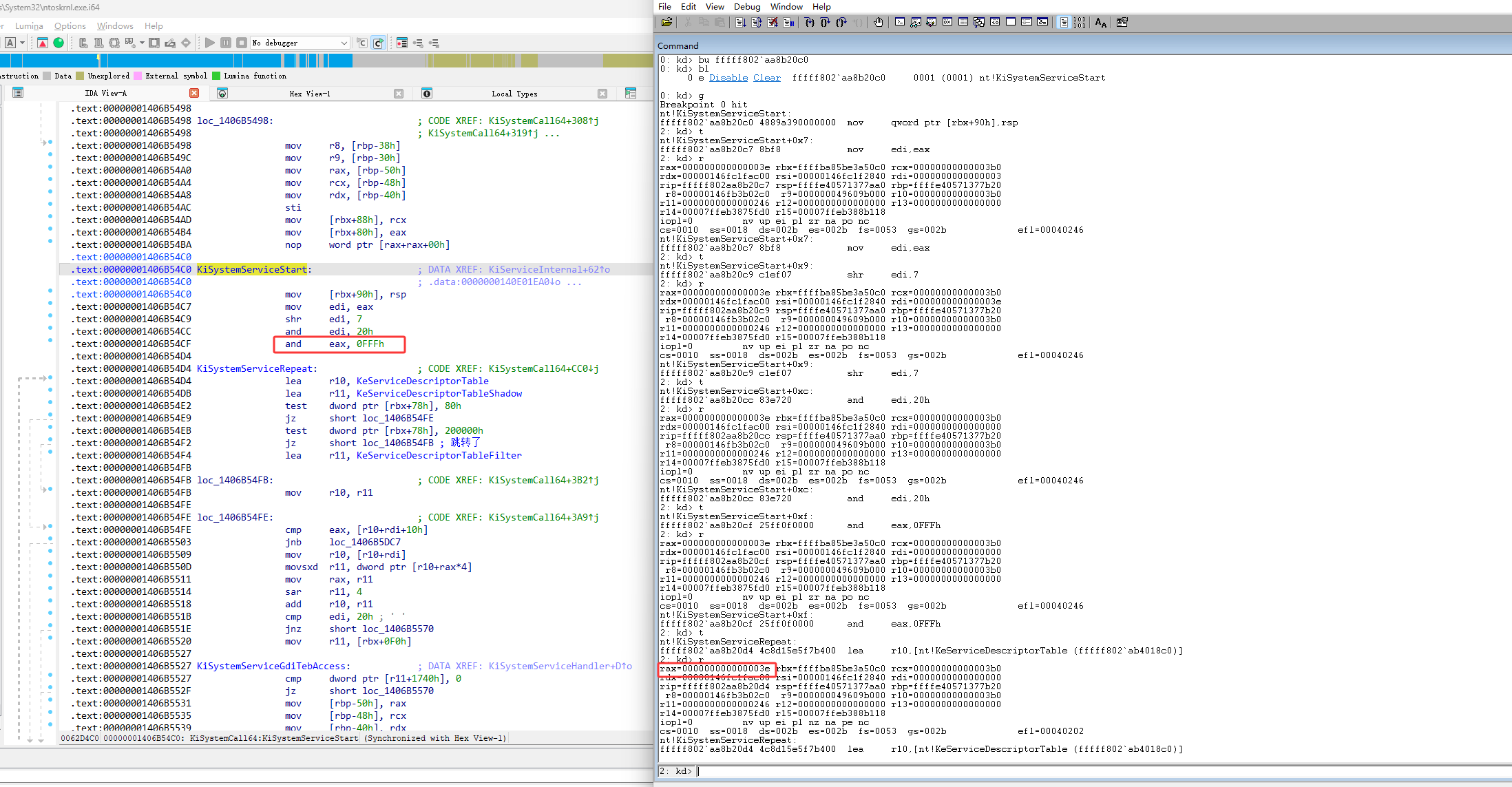
然后接下来就开始搞ssdt了,如下图dq是以8字节的方式查看内存,如下图查看 KeServiceDescriptorTable的内存,可以看到它里面都是内存地址
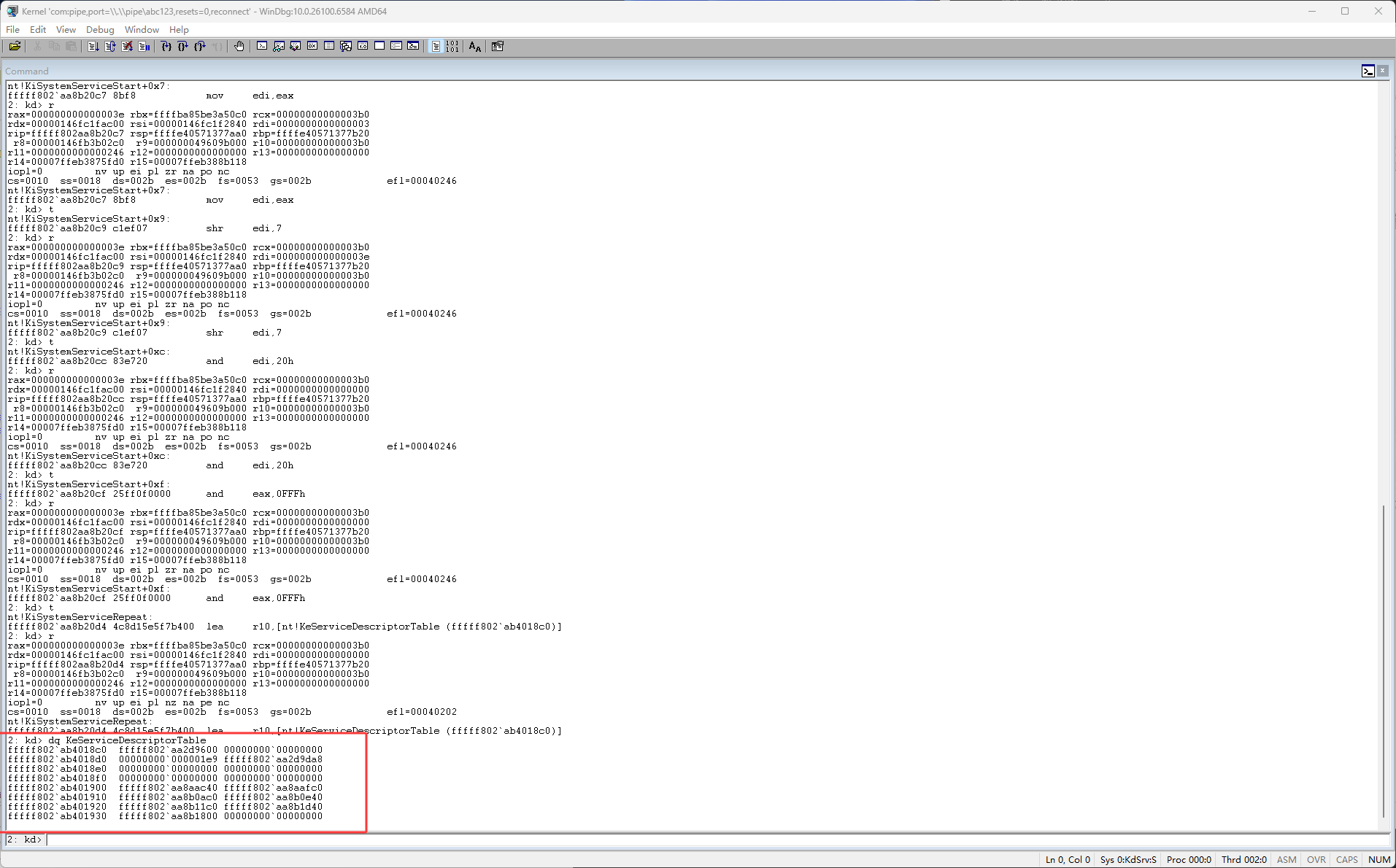
如下图它里面的内存地址并不都是函数
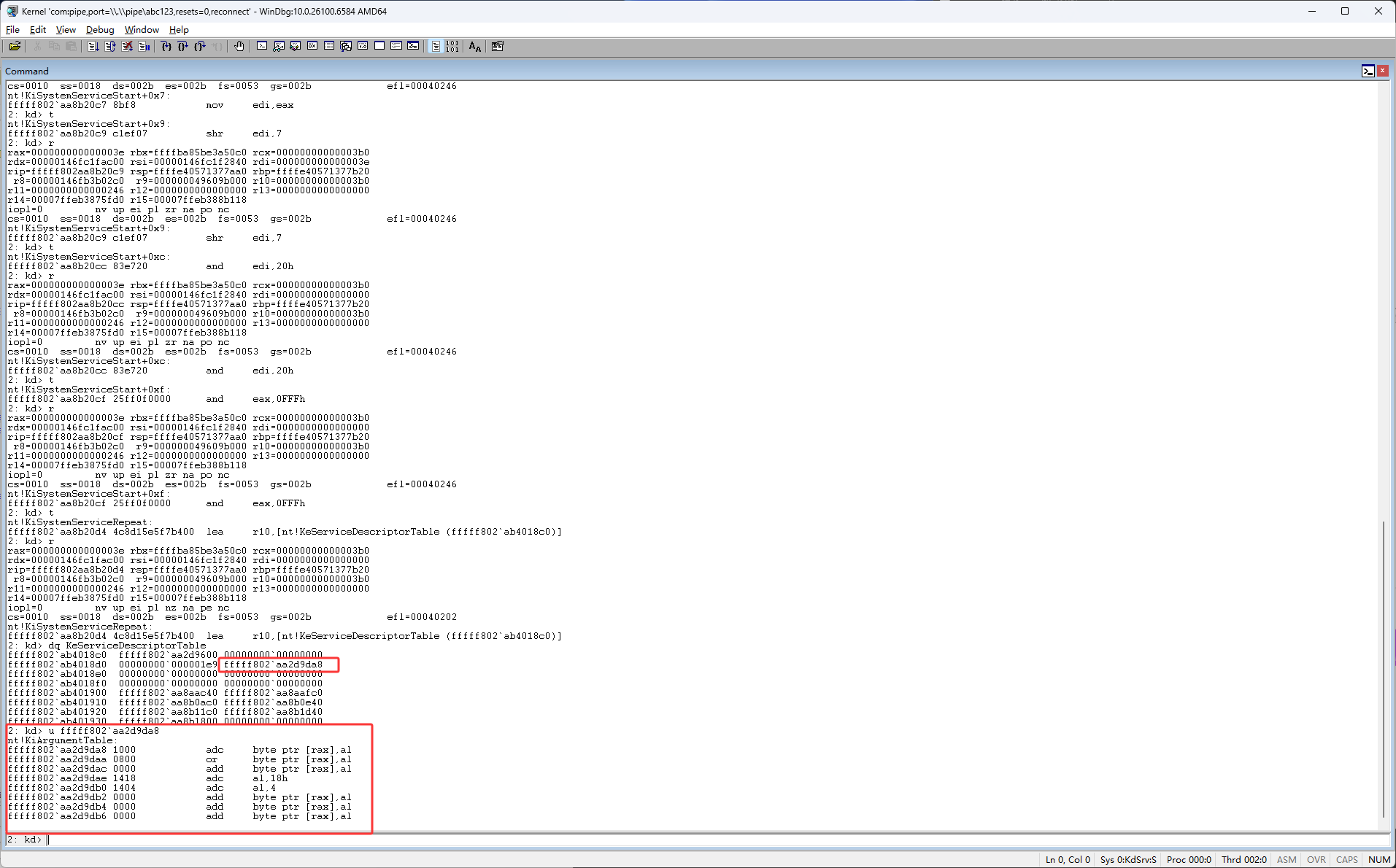
然后接下来继续按F11单步执行,如下图红框这时的r10是KeServiceDescriptorTable
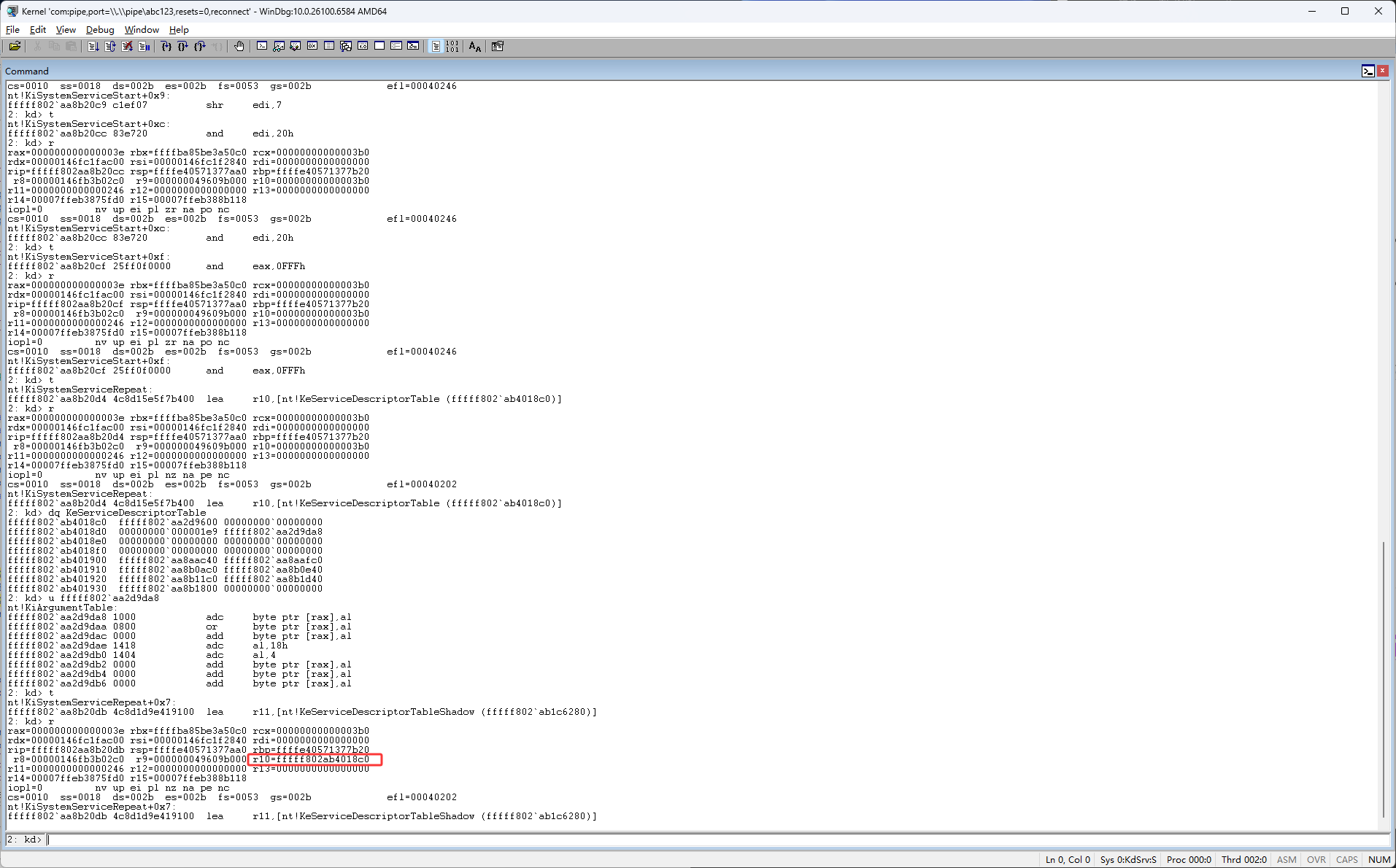
如下图红框KeServiceDescriptorTableShadow的内容,可以看到它和KeServiceDescriptorTable差不多
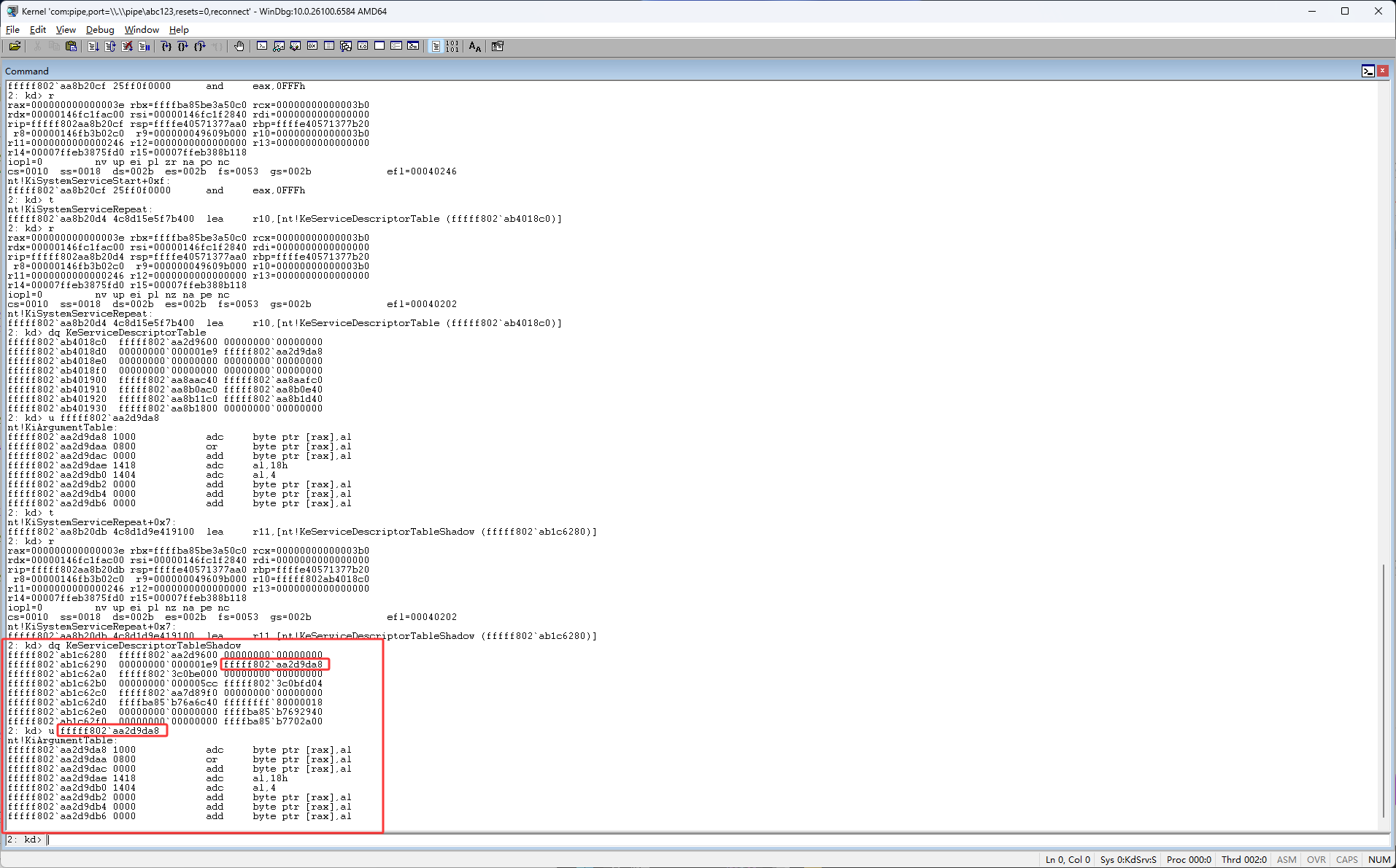
然后继续按F11单步执行,继续单步执行的话,主要是注意下图蓝框的代码跳不跳转,因为我们现在知道了r10是ssdt表,然后eax是ssdt表的索引,我们现在只需要关注r10和eax相关的代码就可以了,所以主要关注下图蓝框的代码
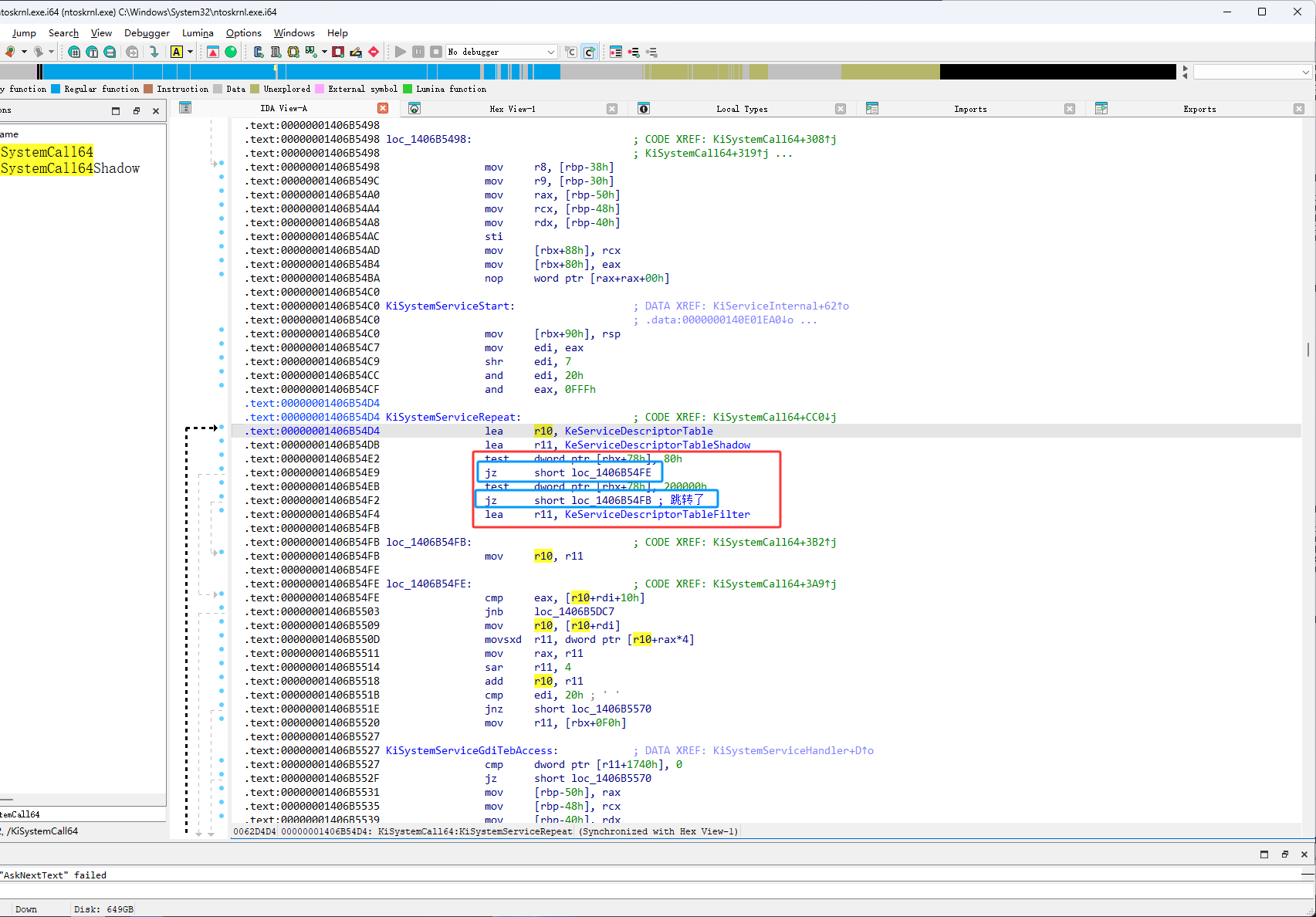
这时它在下图红框位置跳转了,但是之前它是在下图蓝框位置跳转的,下图蓝框的代码是mov r10, r11,也就是让原本是KeServiceDescriptorTable的r10变成了KeServiceDescriptorTableShadow,KeServiceDescriptorTable是早期SSDT表(WindowsPX时代)它里面主要存放了x86的函数用来让最新的系统兼容老驱动,KeServiceDescriptorTableShadow是最新的ssdt表,它里面存放了x64的系统核心函数(内核函数地址)
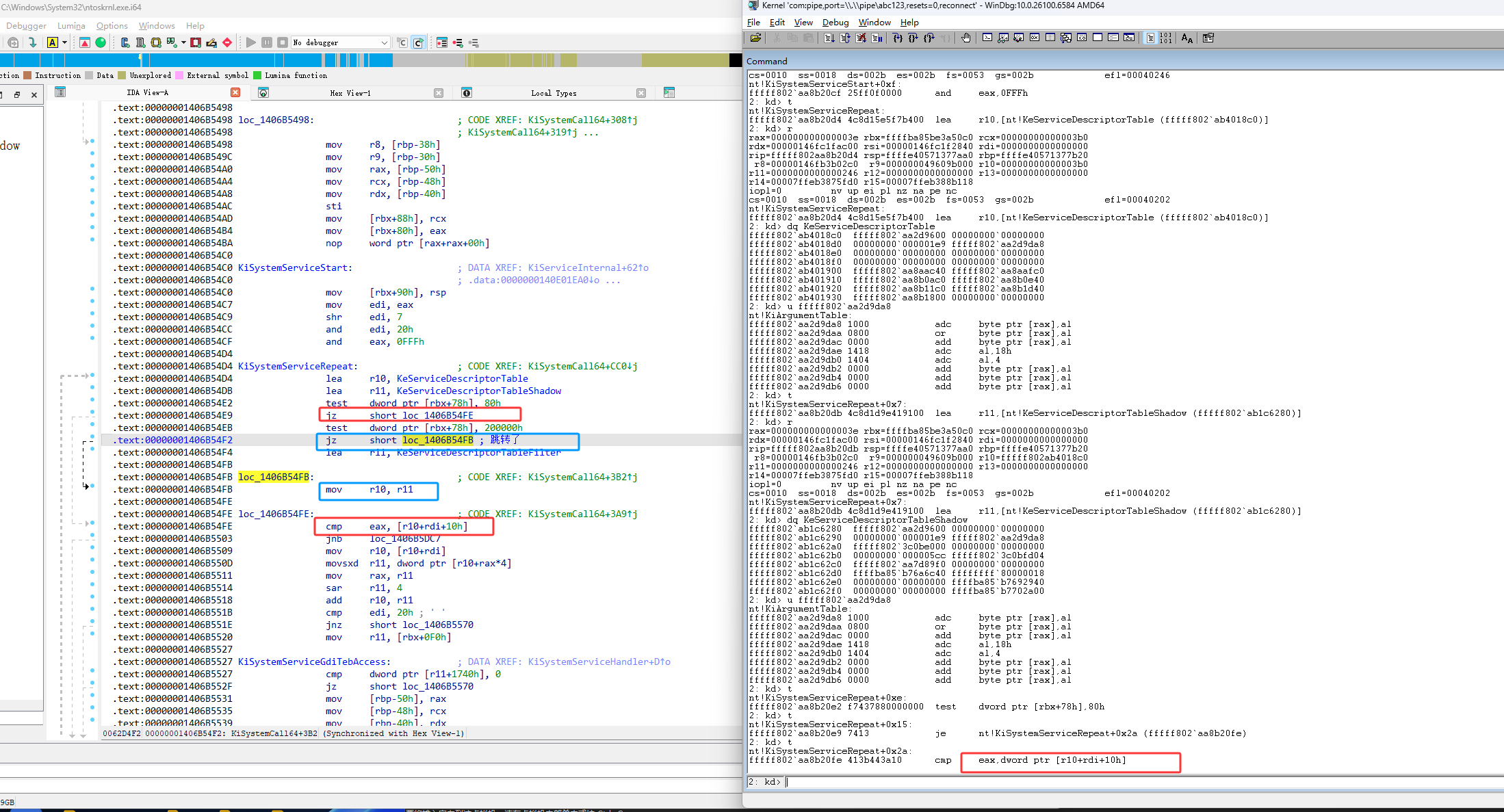
然后接下来观察,它在下图红框什么位置进行的跳转
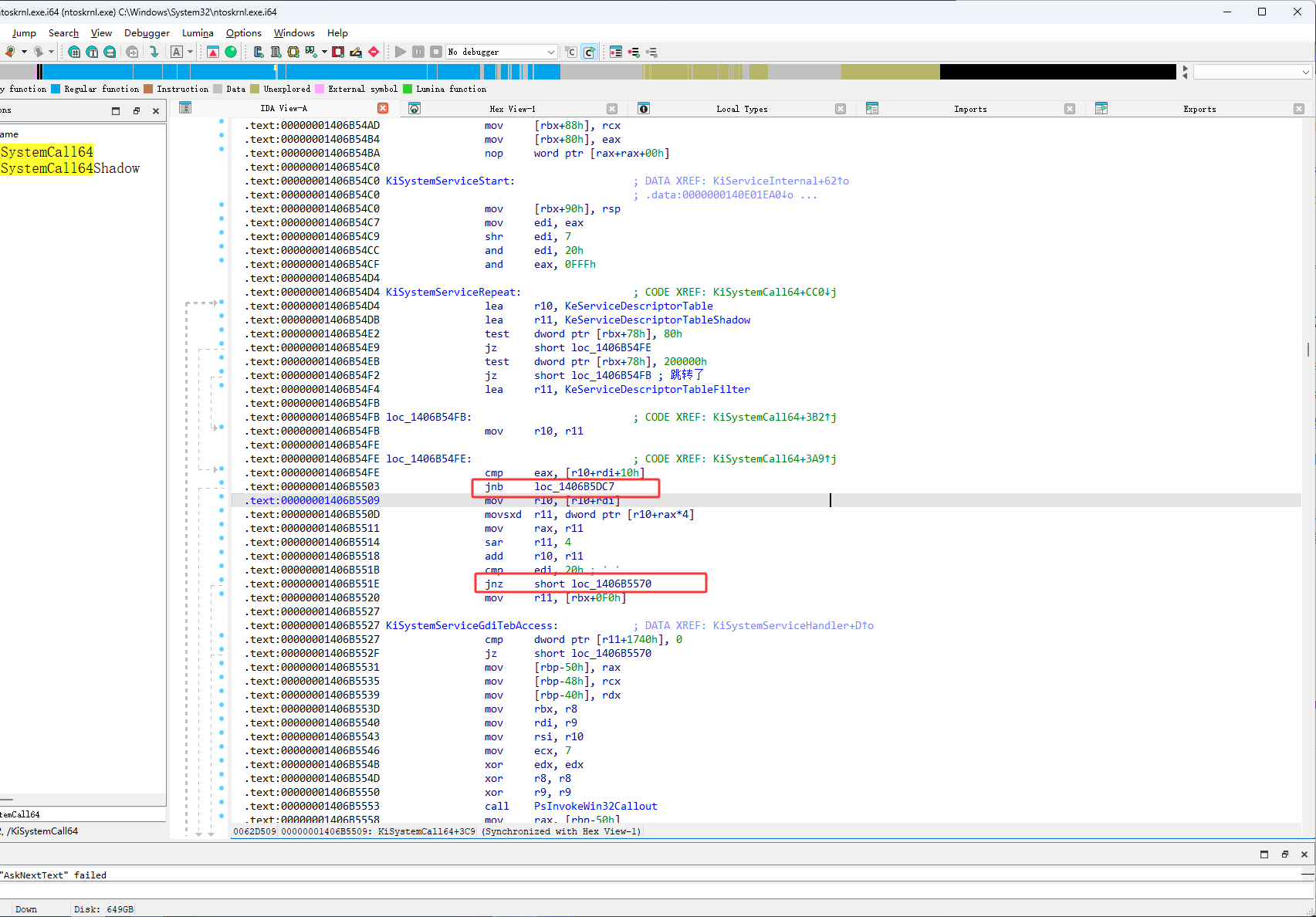
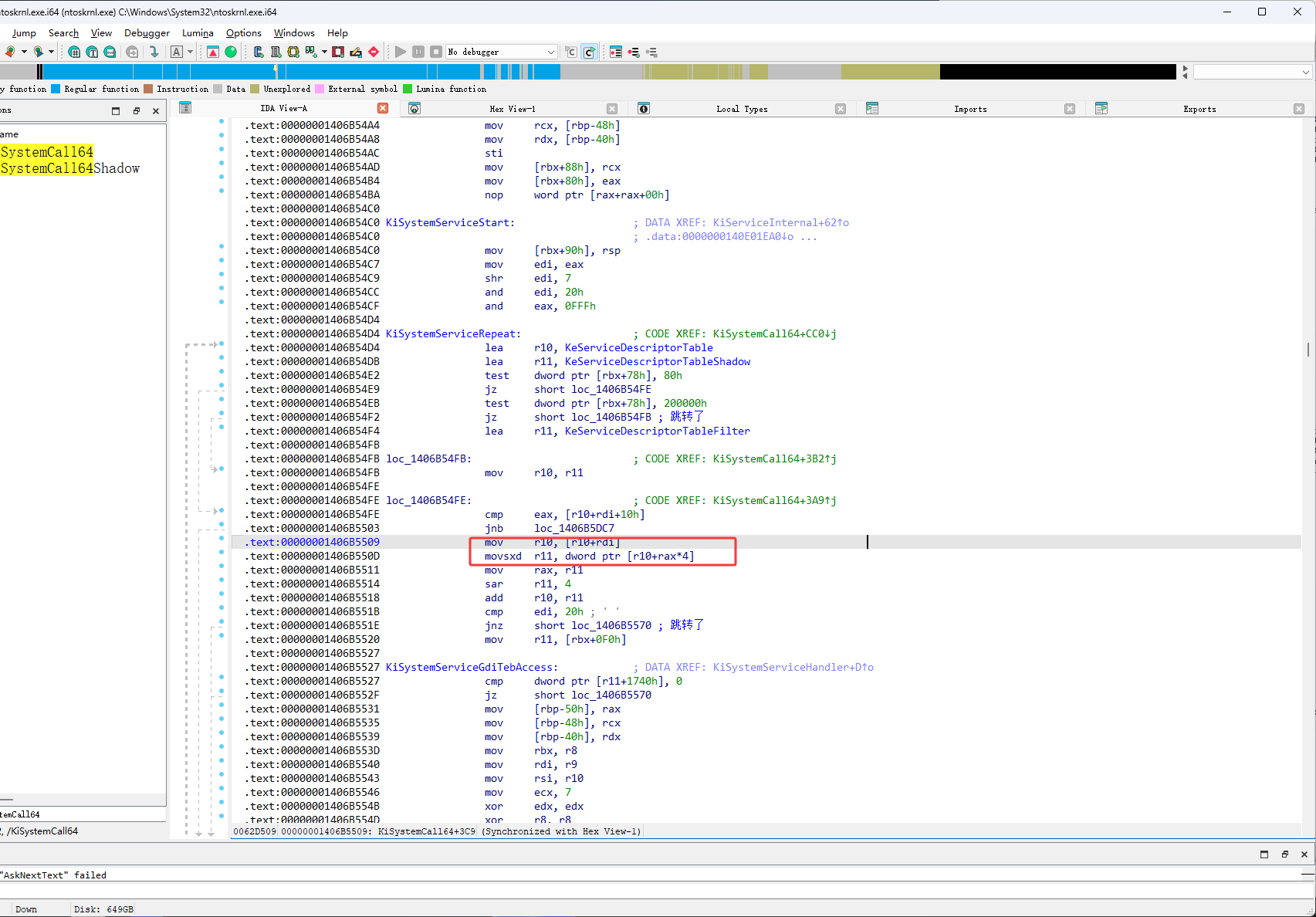
如下图按完F11后,它并没有在上图第一个红框位置进行跳转,如下图红框这里它要执行 mov r10,qword ptr [r10+rdi],r10现在是ssdt,rdi现在是0,也就是说它要从读取ssdt第一个位置的数据
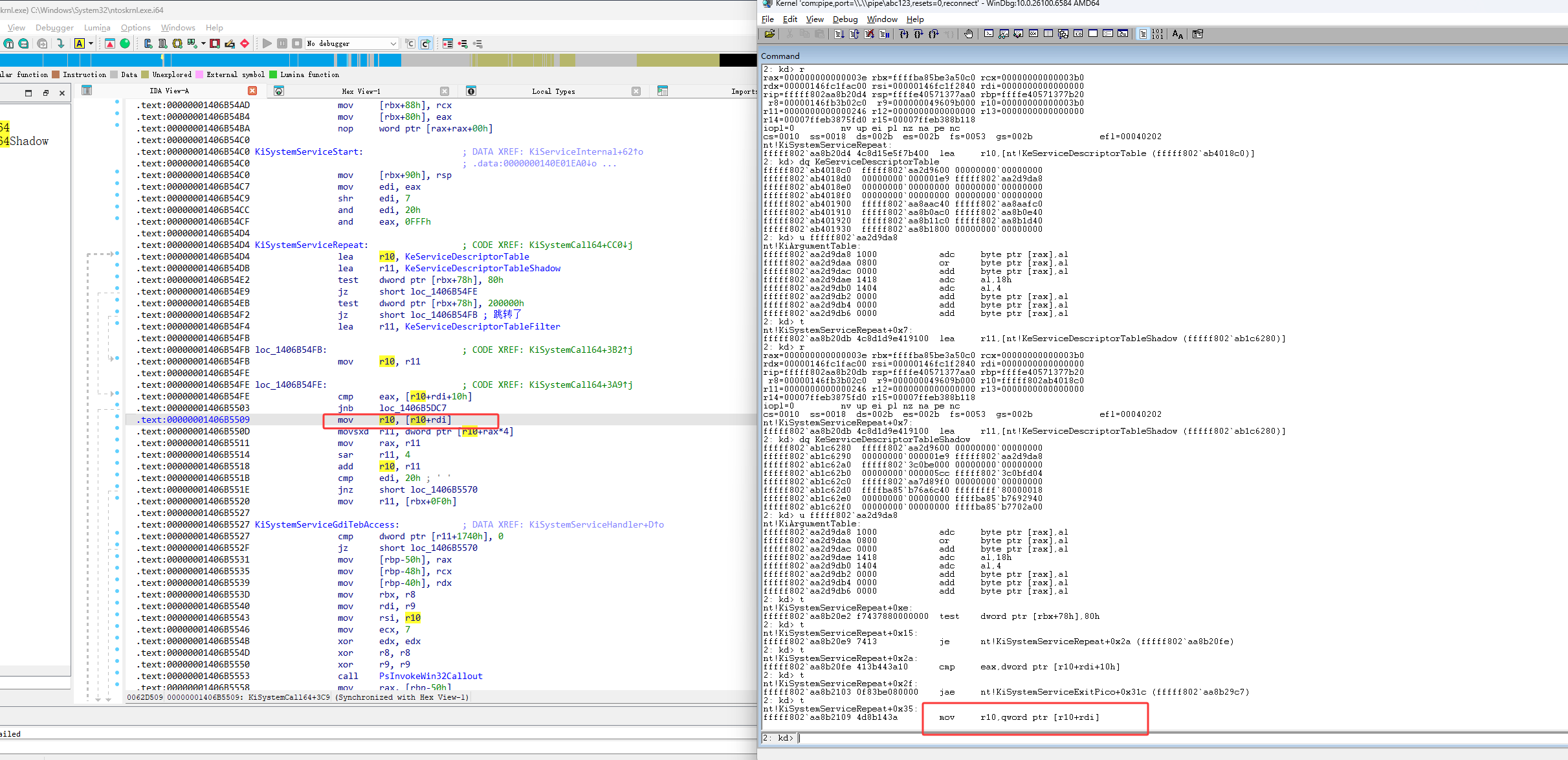
也就是要把r10赋值成下图红框的值
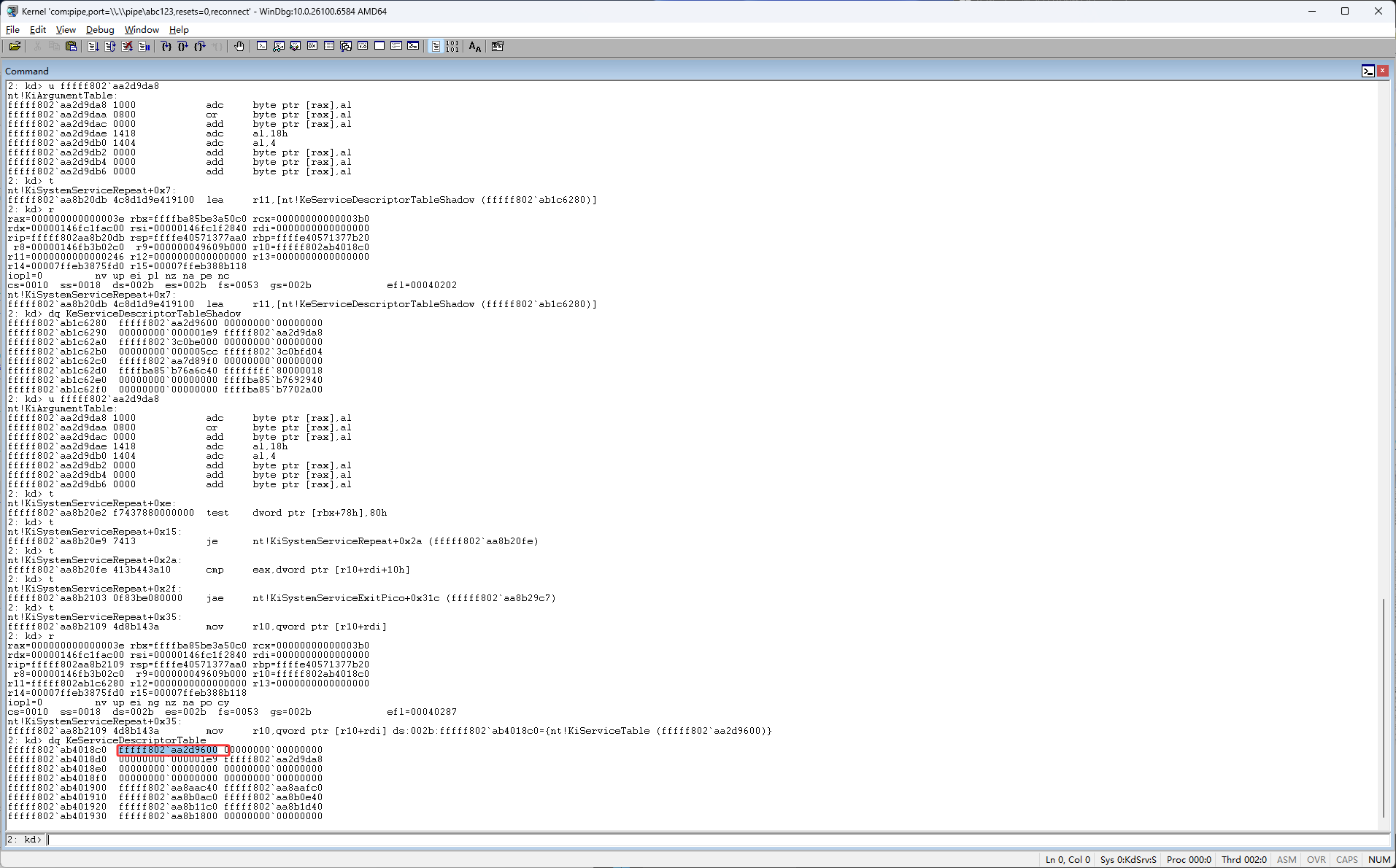
如下图按完F11,执行了 mov r10,qword ptr [r10+rdi]
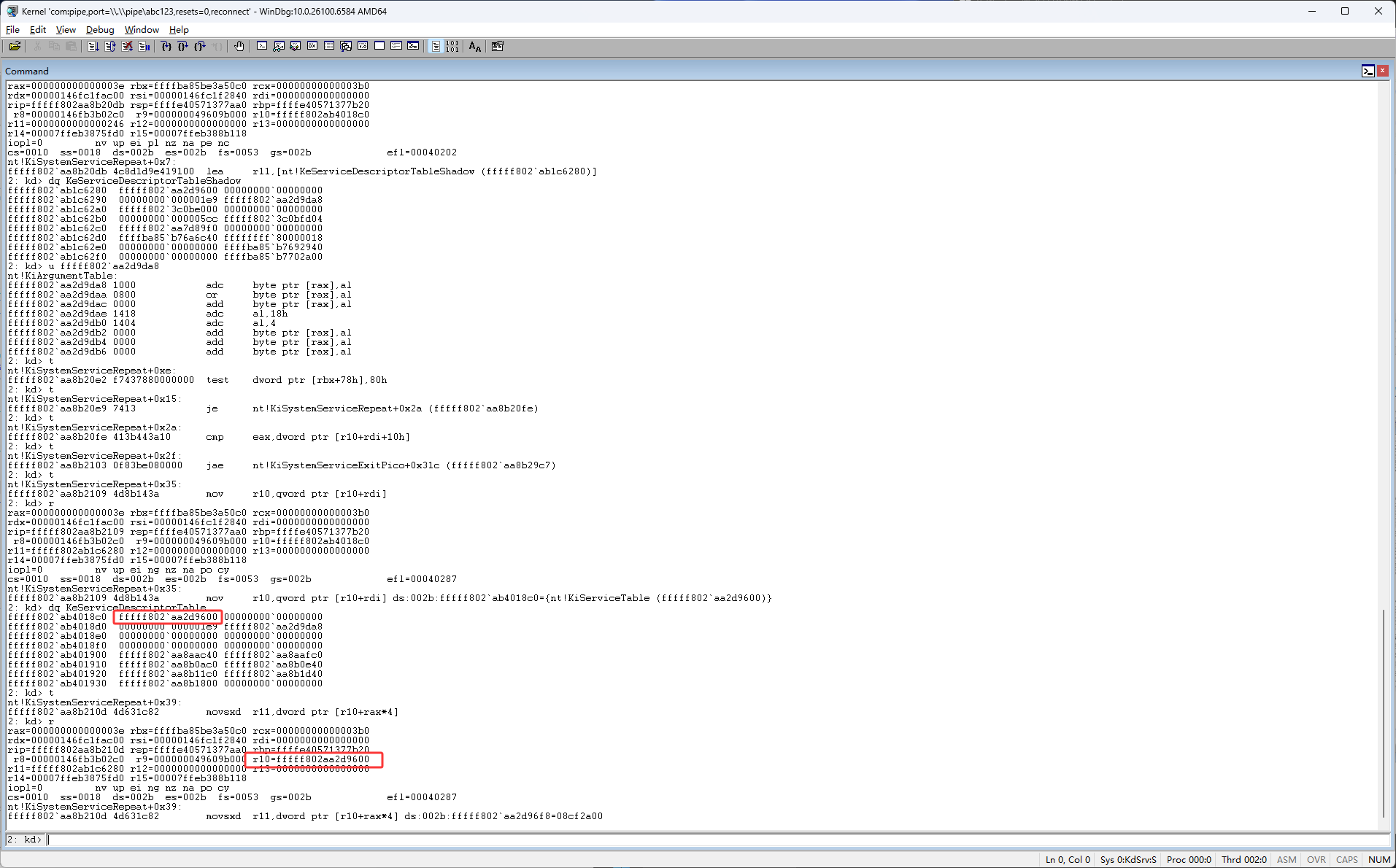
然后接下来是 movsxd r11, dword ptr [r10+rax*4],rax是索引,现在所以是3e,movsxd是把一个32位的数扩展成64位,r10现在的是ssdt第一个数据,rax是索引,这也就是说要从ssdt表中得到第一个数据,然后从第一个数据里的3e位置获取一个数据,大小是4字节,如下图就是来得到08cf2a00
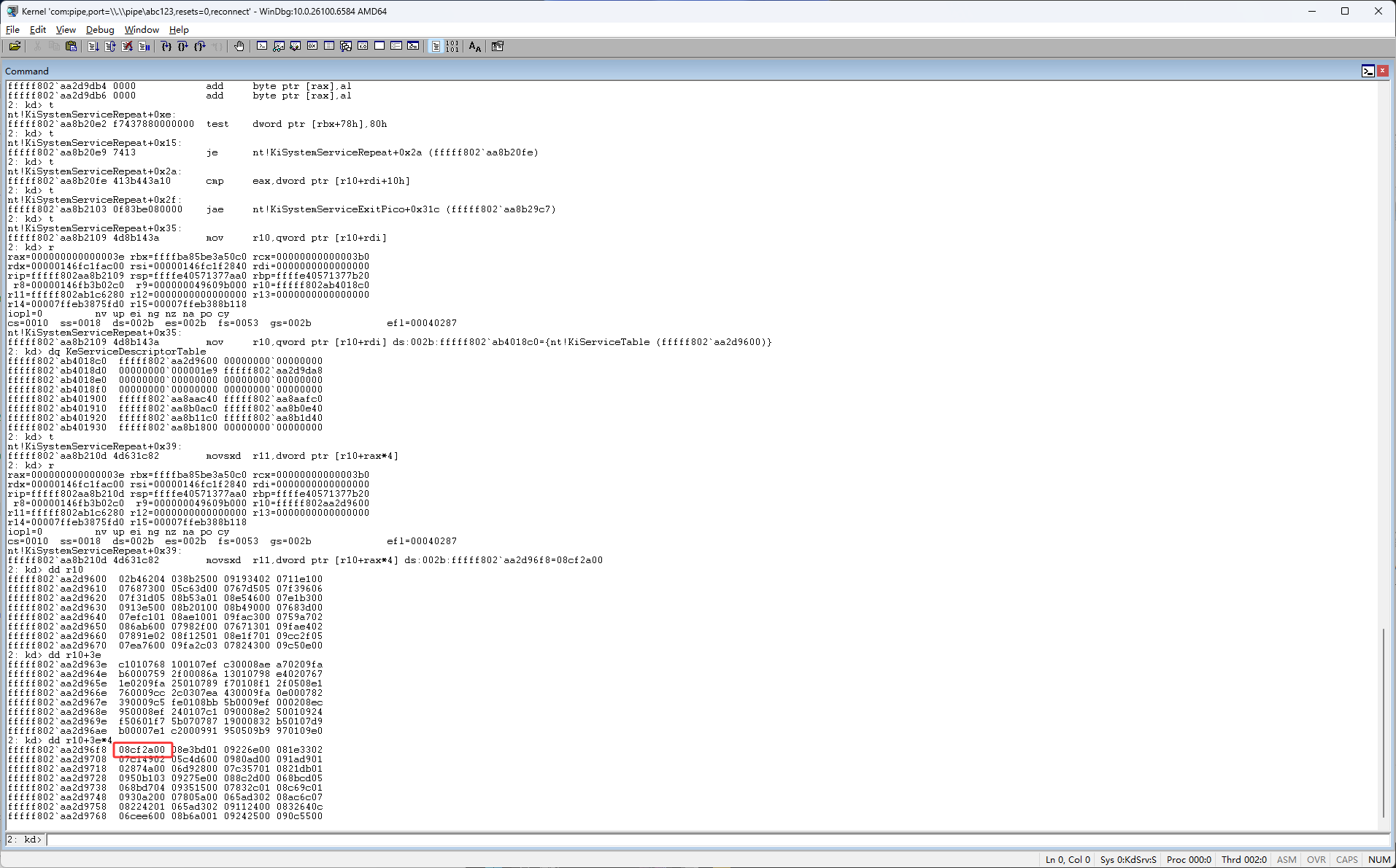
如下图按F11执行完 movsxd r11,dword ptr [r10+rax*4]后
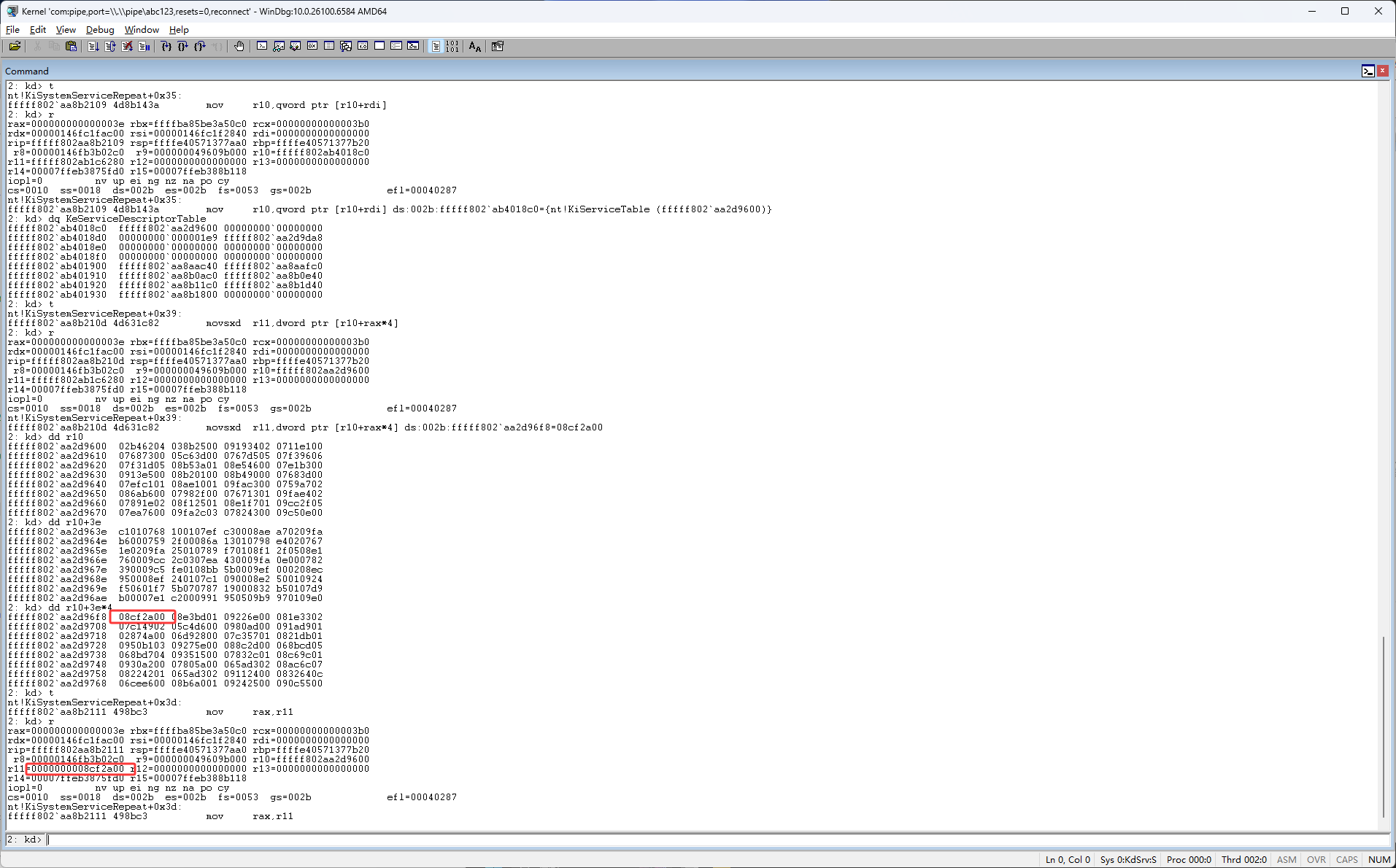
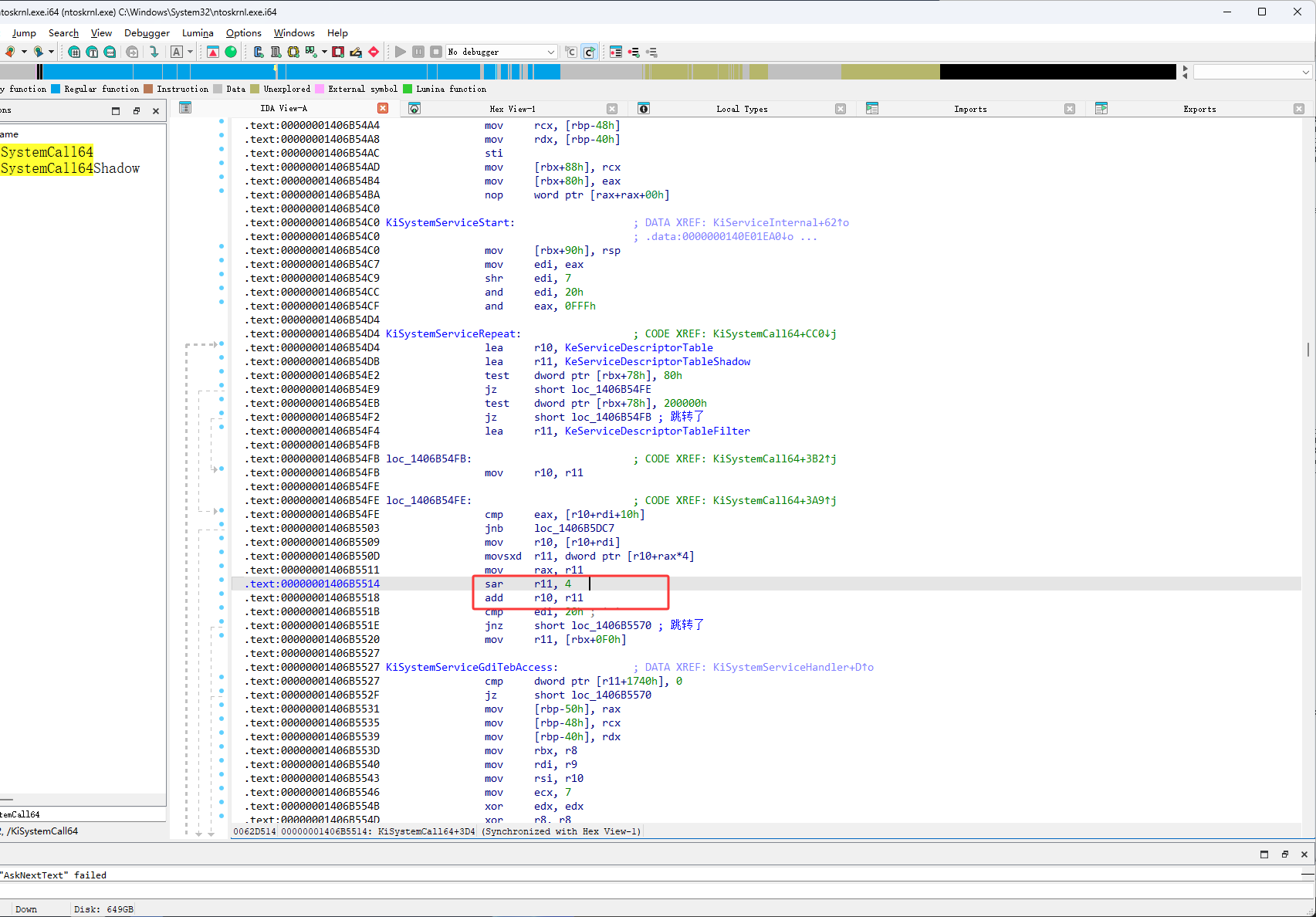
下图红框位置右移了4
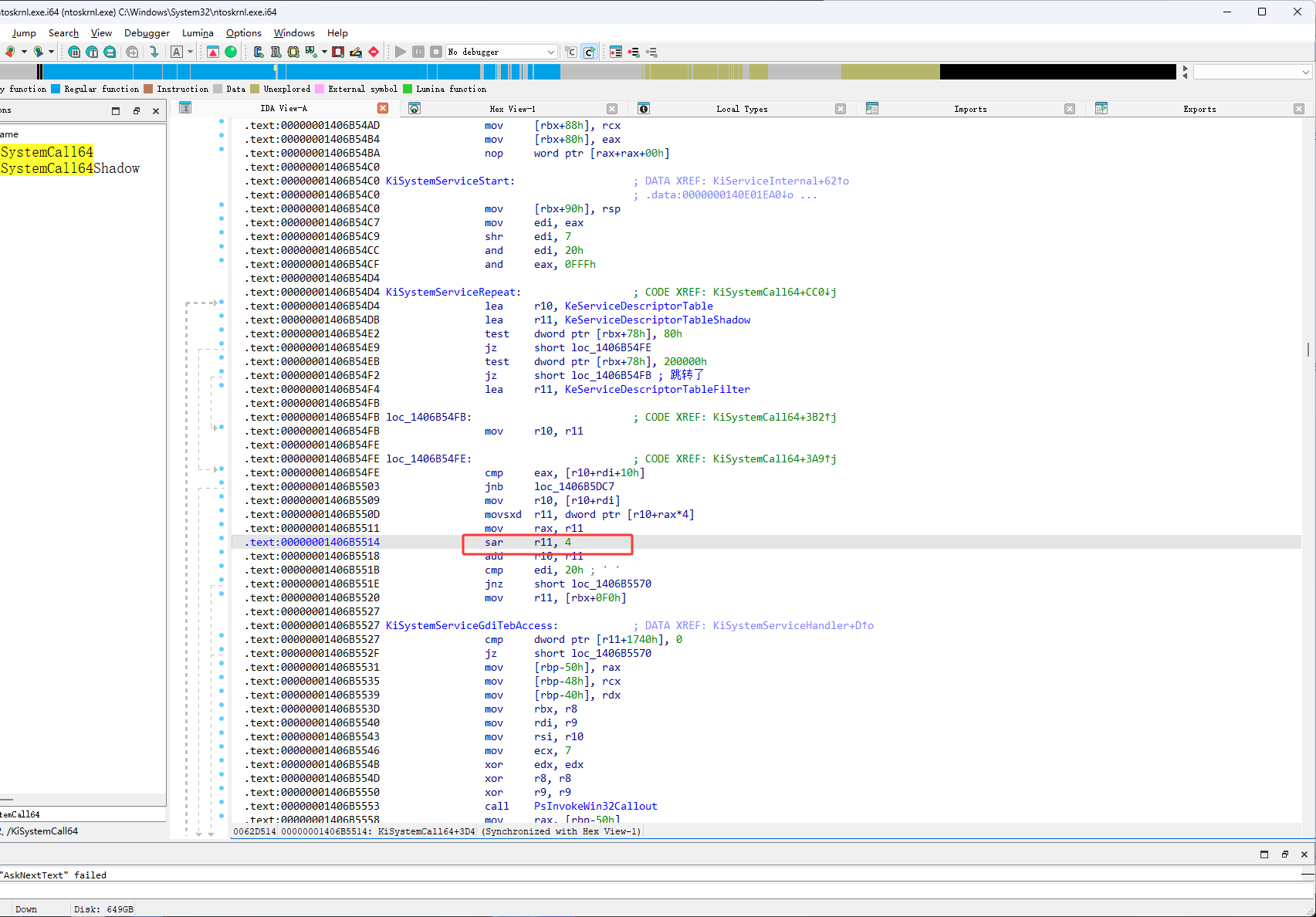
得到的结果是8CF2A0
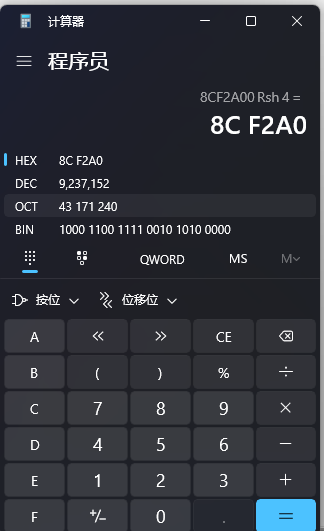
如下图红框
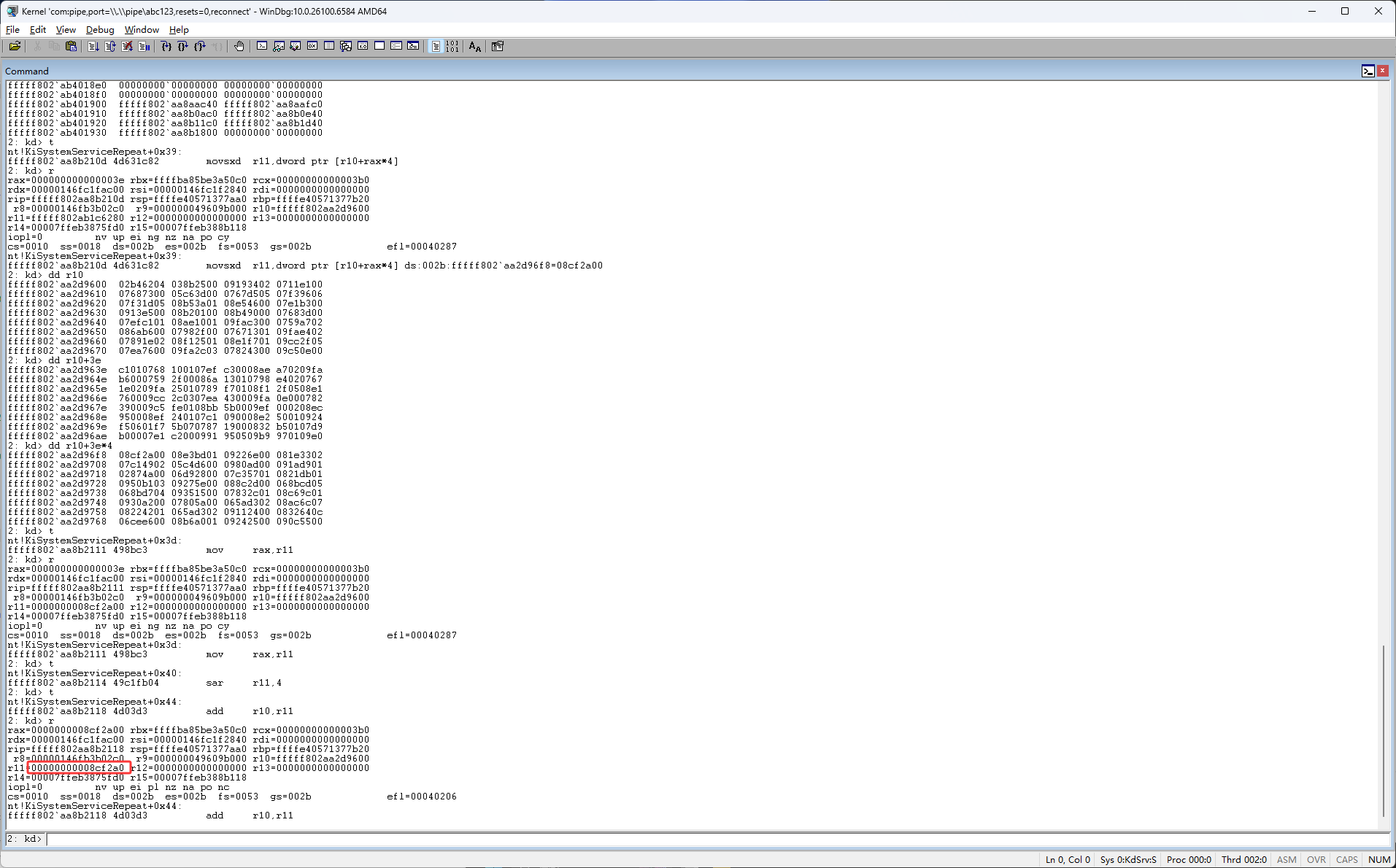
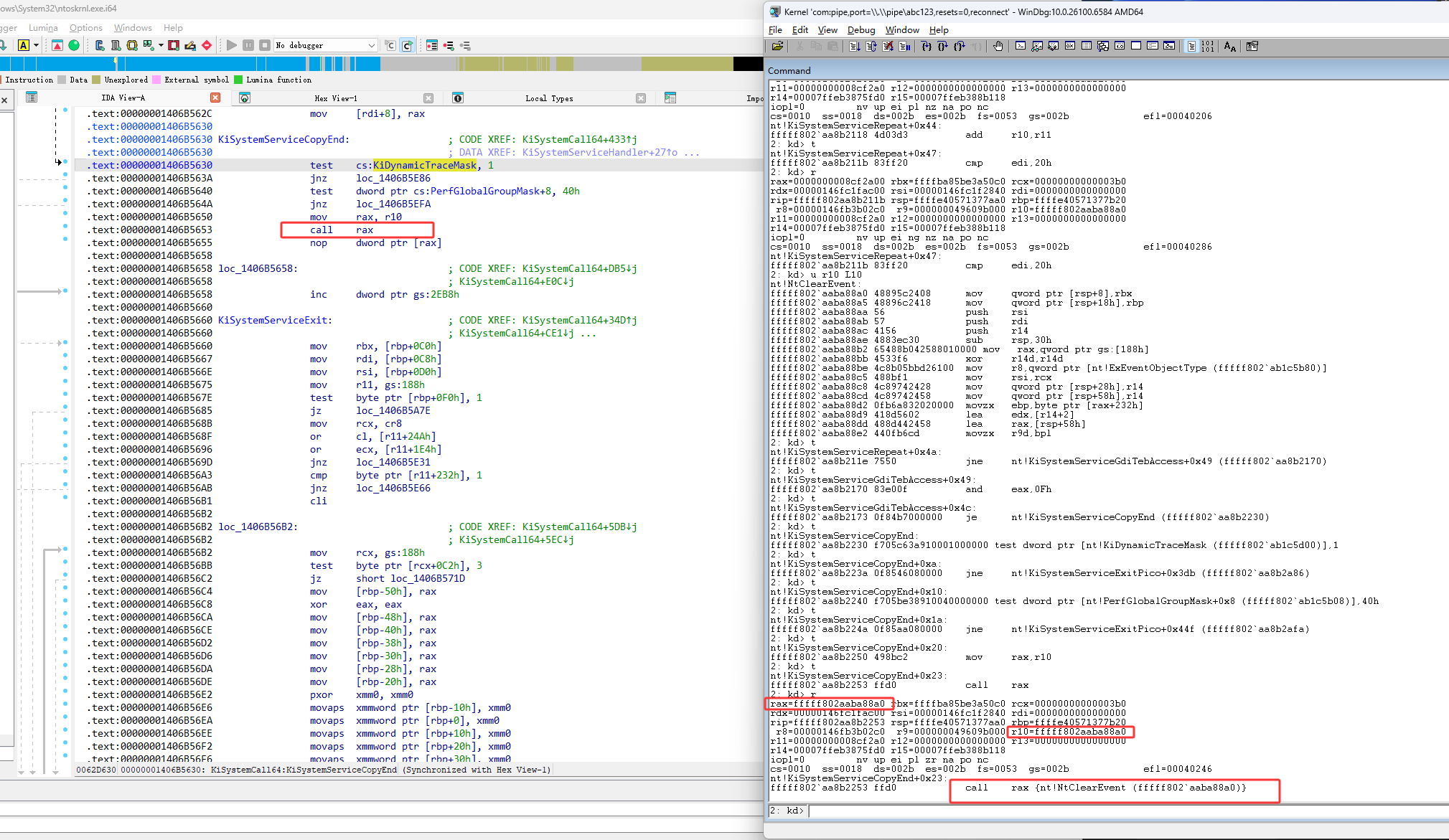
然后继续按F11,r10是ssdt,这里与r11进行了相加,这说明r11是一个偏移,r10+r11是一个内存地址
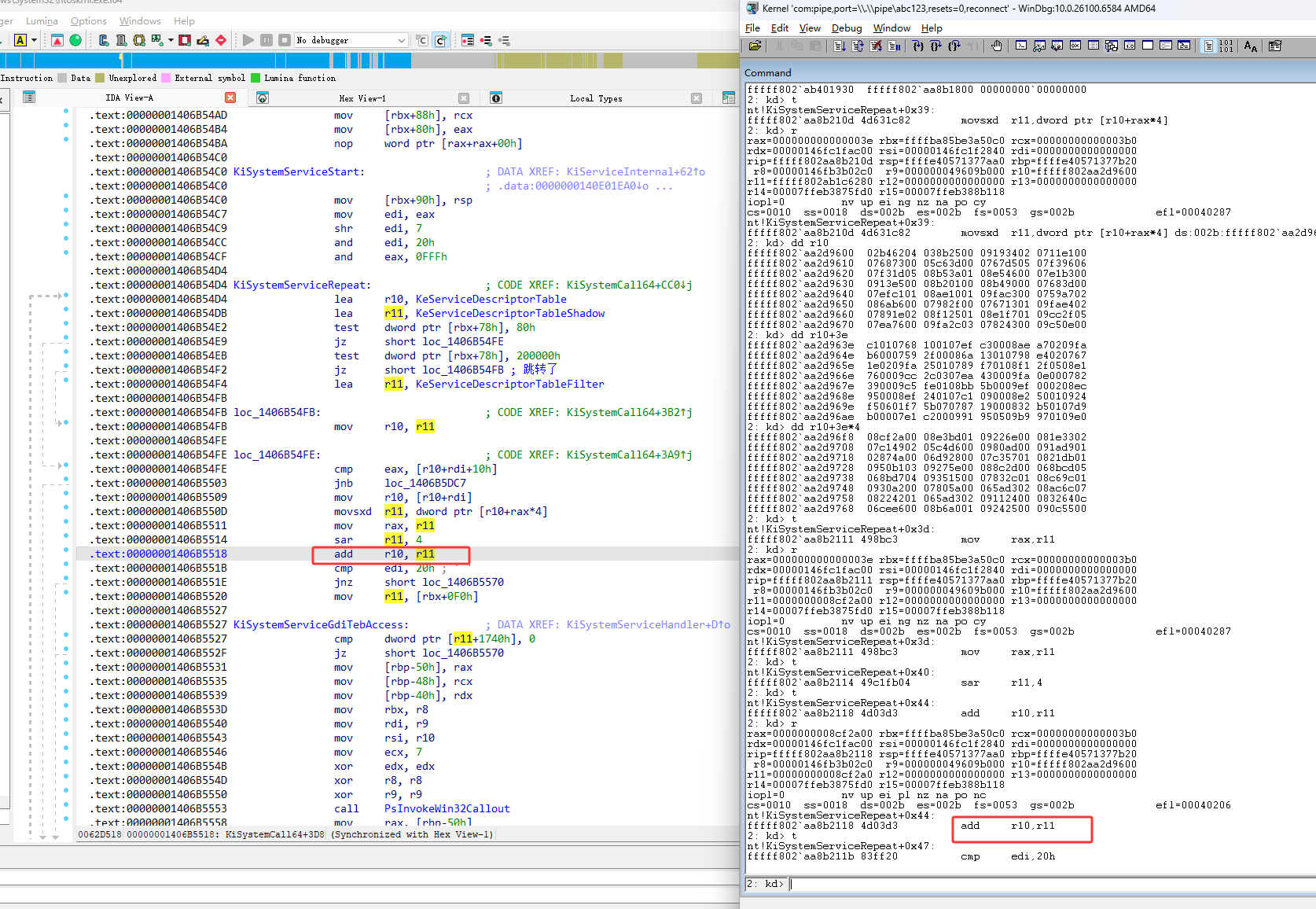
如下图红框3e是NtClearEvent函数
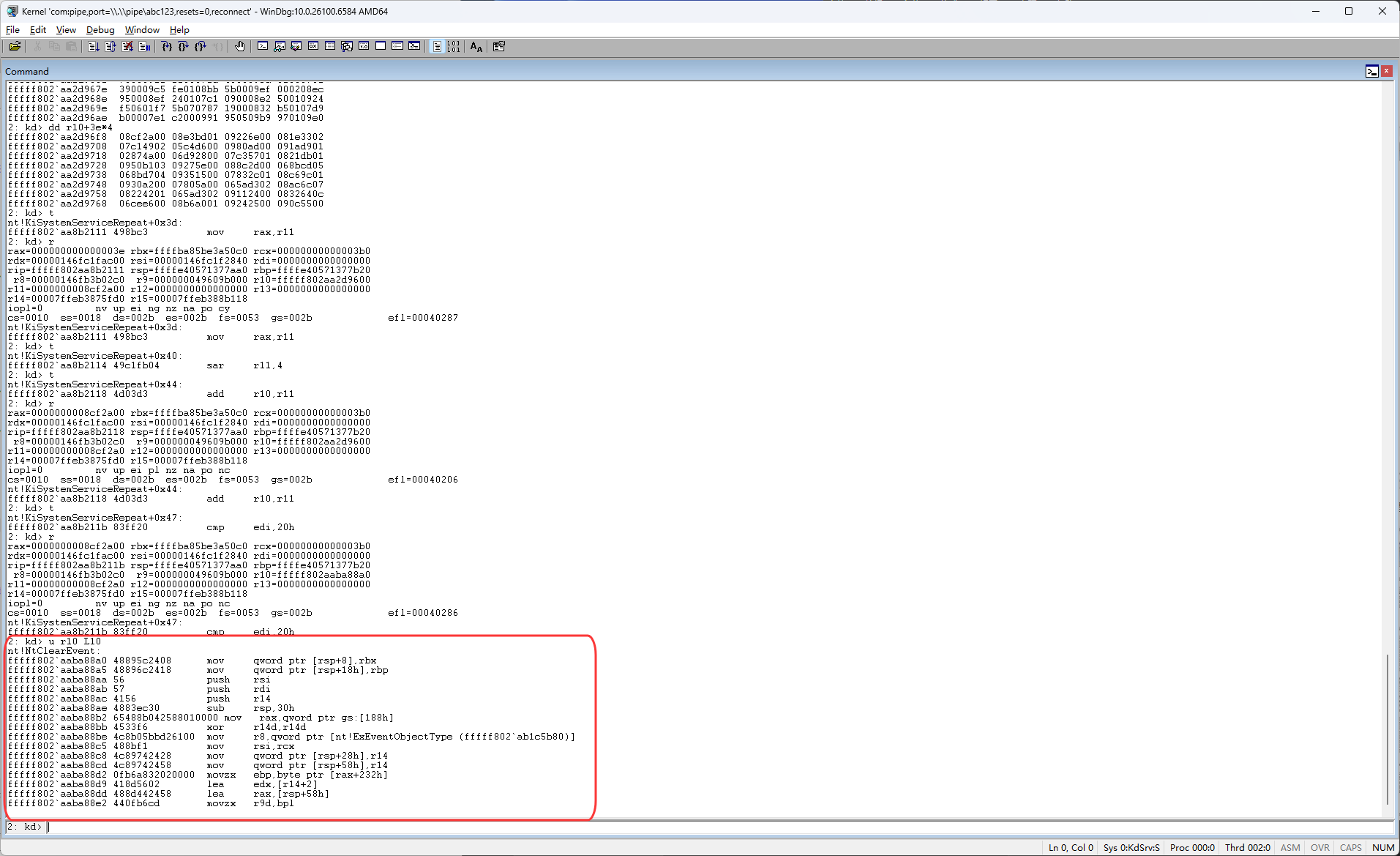
现在就把ssdt进行解密了,接下来就是一直按F11,看看是否存在call r10这样的代码,这里在下图红框位置进行了跳转
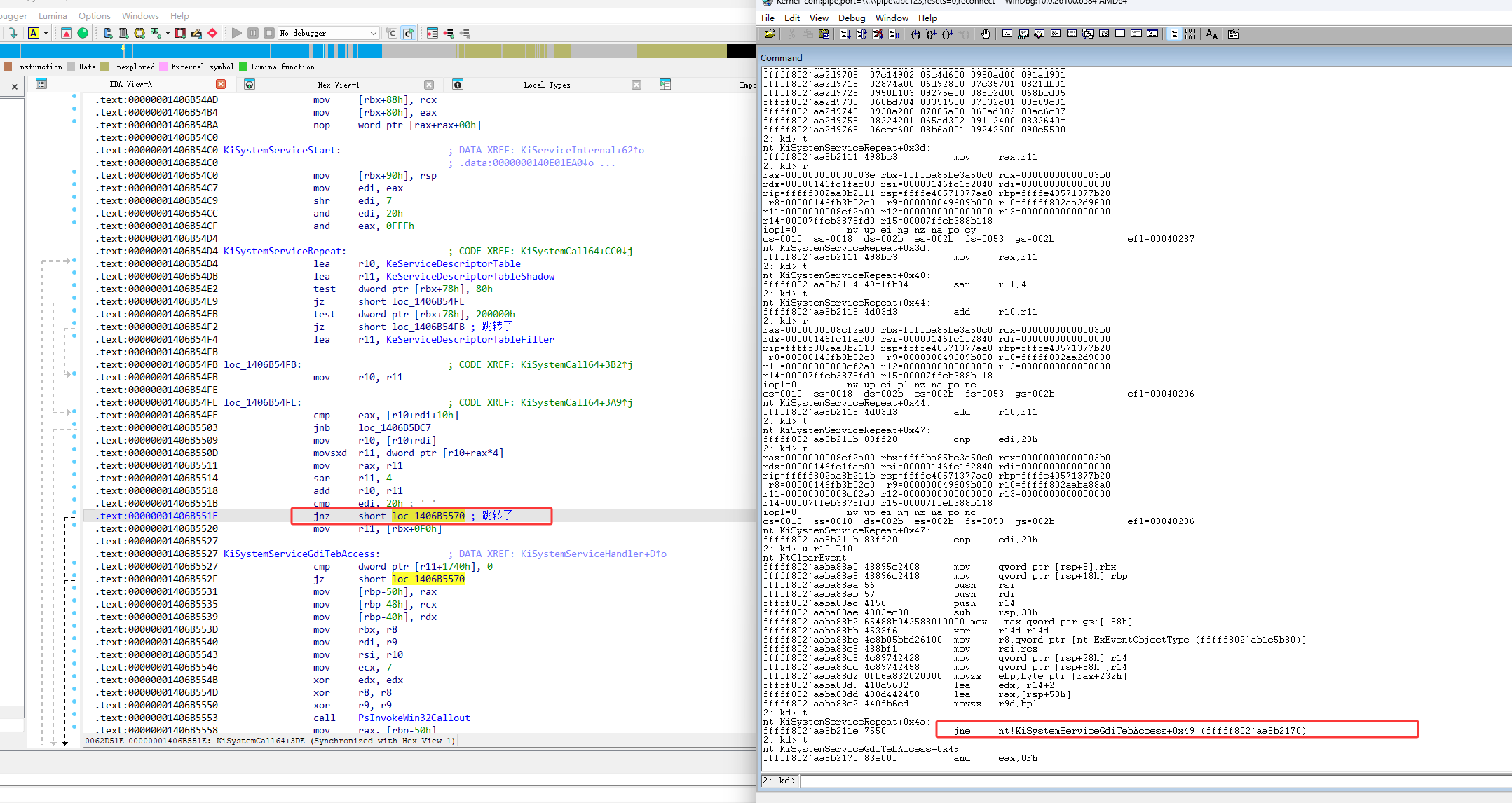
跳转后的代码
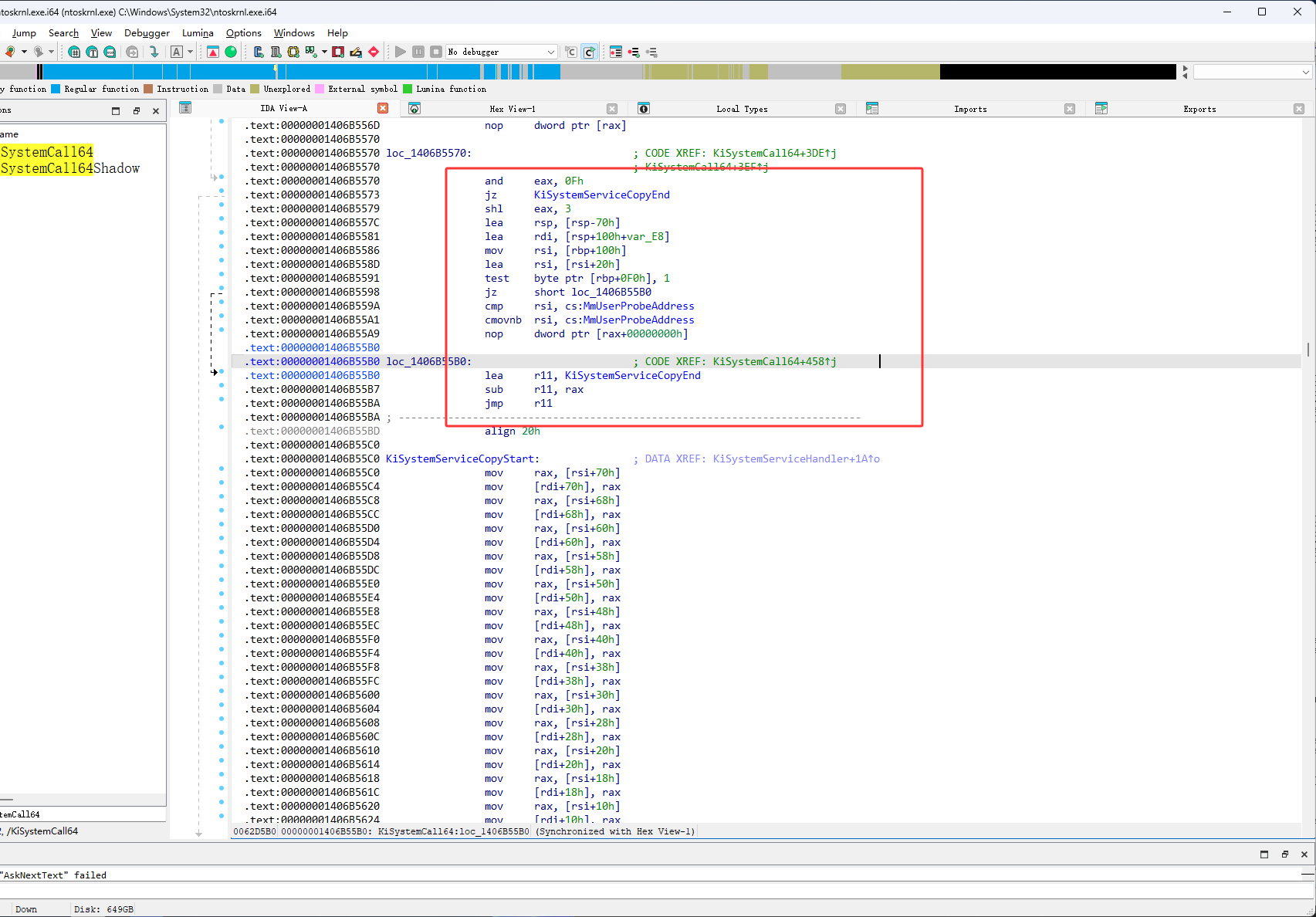
然后继续按F11,找call r10,它在下图红框位置进行跳转了
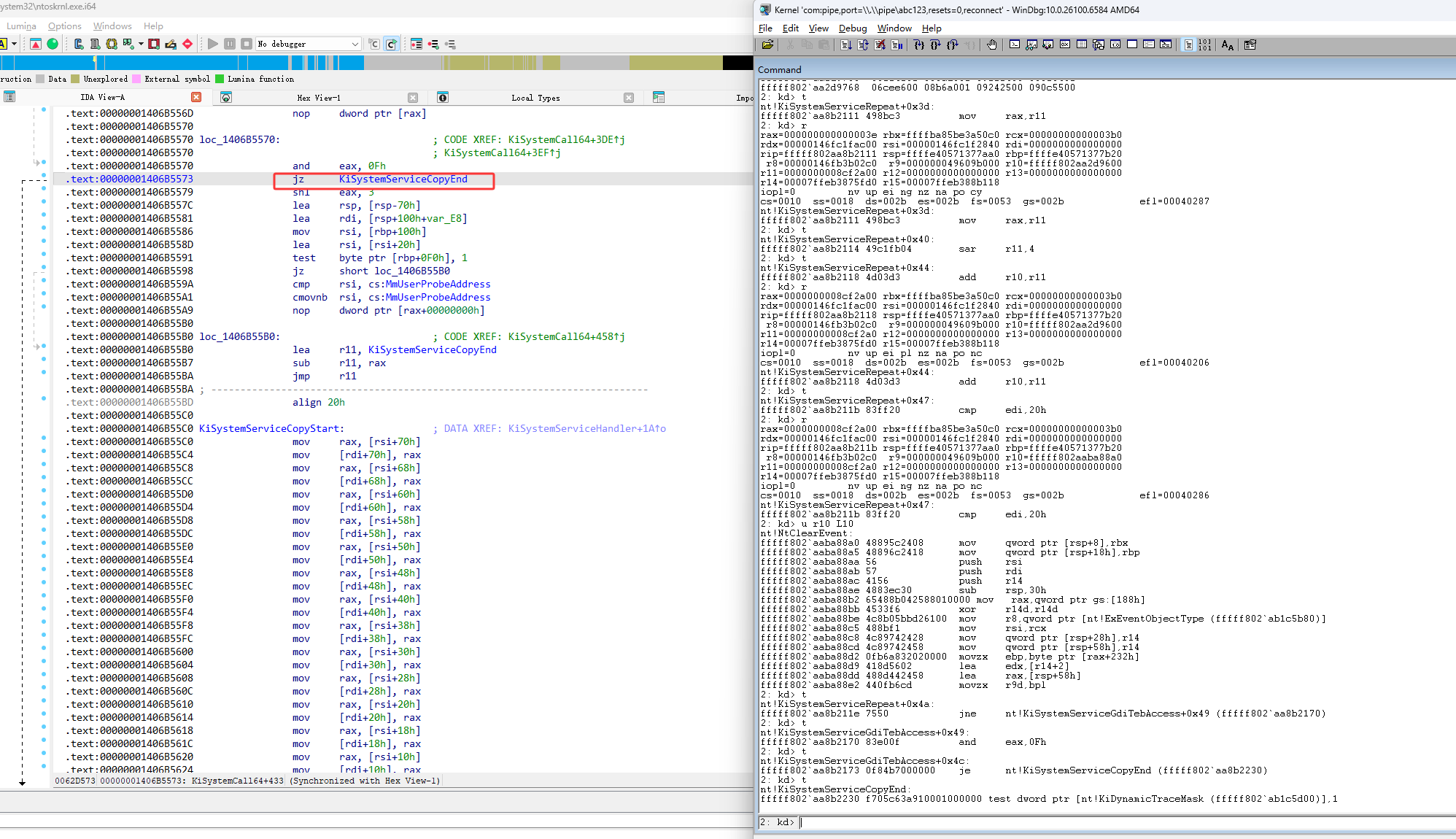
找了call r10执行内核函数
接下来找我们的ReadProcessMemory(3F),OpenProcess(0x26)
首先是ReadProcessMemory
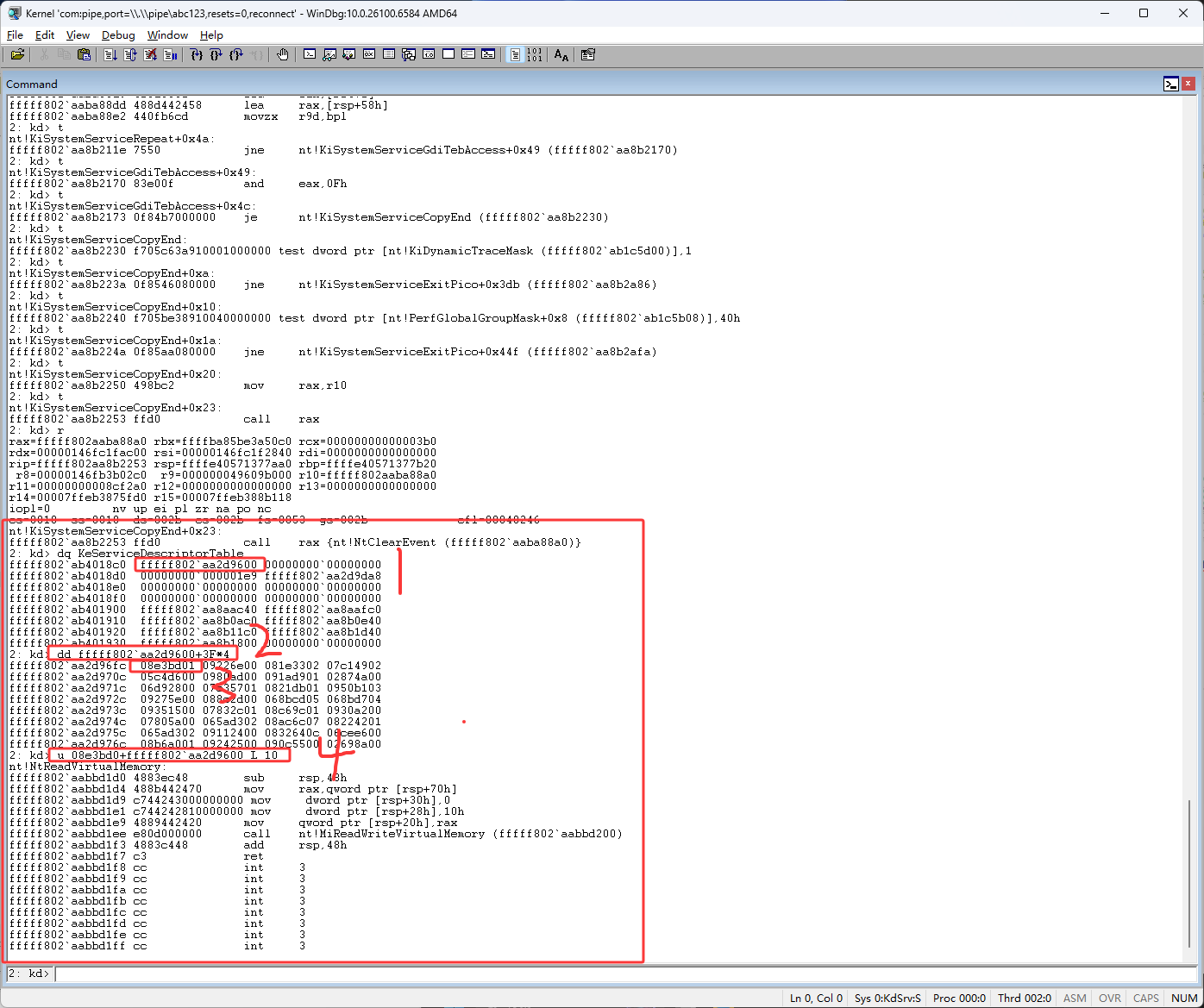
OpenProcess
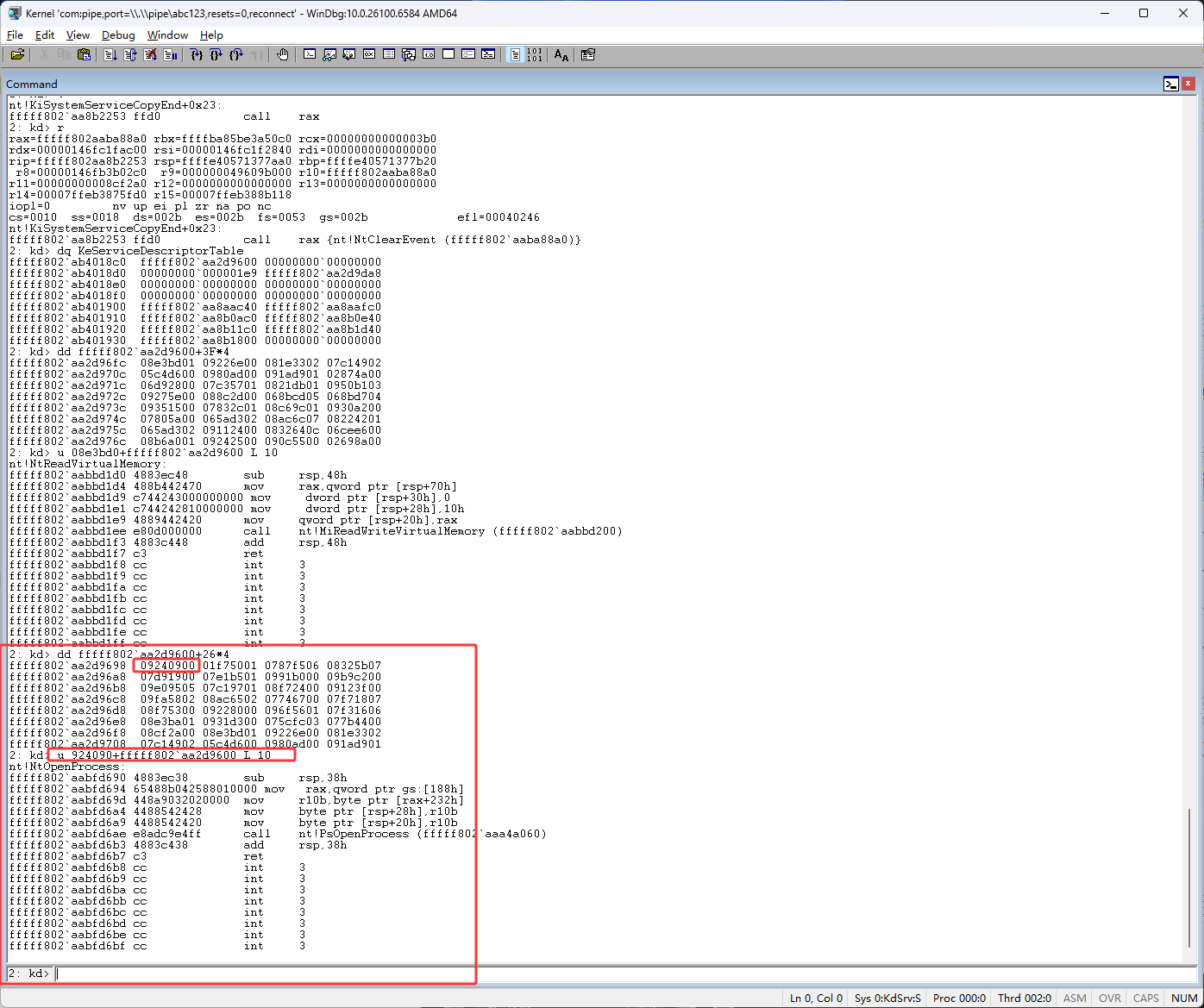
windbg过程
nt!DbgBreakPointWithStatus:
fffff802`aa6f7690 cc int 3
0: kd> u KiSystemServiceStart L20
nt!KiSystemServiceStart:
fffff802`aa8b20c0 4889a390000000 mov qword ptr [rbx+90h],rsp
fffff802`aa8b20c7 8bf8 mov edi,eax
fffff802`aa8b20c9 c1ef07 shr edi,7
fffff802`aa8b20cc 83e720 and edi,20h
fffff802`aa8b20cf 25ff0f0000 and eax,0FFFh
nt!KiSystemServiceRepeat:
fffff802`aa8b20d4 4c8d15e5f7b400 lea r10,[nt!KeServiceDescriptorTable (fffff802`ab4018c0)]
fffff802`aa8b20db 4c8d1d9e419100 lea r11,[nt!KeServiceDescriptorTableShadow (fffff802`ab1c6280)]
fffff802`aa8b20e2 f7437880000000 test dword ptr [rbx+78h],80h
fffff802`aa8b20e9 7413 je nt!KiSystemServiceRepeat+0x2a (fffff802`aa8b20fe)
fffff802`aa8b20eb f7437800002000 test dword ptr [rbx+78h],200000h
fffff802`aa8b20f2 7407 je nt!KiSystemServiceRepeat+0x27 (fffff802`aa8b20fb)
fffff802`aa8b20f4 4c8d1dc5429100 lea r11,[nt!KeServiceDescriptorTableFilter (fffff802`ab1c63c0)]
fffff802`aa8b20fb 4d8bd3 mov r10,r11
fffff802`aa8b20fe 413b443a10 cmp eax,dword ptr [r10+rdi+10h]
fffff802`aa8b2103 0f83be080000 jae nt!KiSystemServiceExitPico+0x31c (fffff802`aa8b29c7)
fffff802`aa8b2109 4d8b143a mov r10,qword ptr [r10+rdi]
fffff802`aa8b210d 4d631c82 movsxd r11,dword ptr [r10+rax*4]
fffff802`aa8b2111 498bc3 mov rax,r11
fffff802`aa8b2114 49c1fb04 sar r11,4
fffff802`aa8b2118 4d03d3 add r10,r11
fffff802`aa8b211b 83ff20 cmp edi,20h
fffff802`aa8b211e 7550 jne nt!KiSystemServiceGdiTebAccess+0x49 (fffff802`aa8b2170)
fffff802`aa8b2120 4c8b9bf0000000 mov r11,qword ptr [rbx+0F0h]
nt!KiSystemServiceGdiTebAccess:
fffff802`aa8b2127 4183bb4017000000 cmp dword ptr [r11+1740h],0
fffff802`aa8b212f 743f je nt!KiSystemServiceGdiTebAccess+0x49 (fffff802`aa8b2170)
fffff802`aa8b2131 488945b0 mov qword ptr [rbp-50h],rax
fffff802`aa8b2135 48894db8 mov qword ptr [rbp-48h],rcx
fffff802`aa8b2139 488955c0 mov qword ptr [rbp-40h],rdx
fffff802`aa8b213d 498bd8 mov rbx,r8
fffff802`aa8b2140 498bf9 mov rdi,r9
fffff802`aa8b2143 498bf2 mov rsi,r10
fffff802`aa8b2146 b907000000 mov ecx,7
0: kd> bu fffff802`aa8b20c0
0: kd> bl
0 e Disable Clear fffff802`aa8b20c0 0001 (0001) nt!KiSystemServiceStart
0: kd> g
Breakpoint 0 hit
nt!KiSystemServiceStart:
fffff802`aa8b20c0 4889a390000000 mov qword ptr [rbx+90h],rsp
2: kd> t
nt!KiSystemServiceStart+0x7:
fffff802`aa8b20c7 8bf8 mov edi,eax
2: kd> r
rax=000000000000003e rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000003
rip=fffff802aa8b20c7 rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=00000000000003b0
r11=0000000000000246 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040246
nt!KiSystemServiceStart+0x7:
fffff802`aa8b20c7 8bf8 mov edi,eax
2: kd> t
nt!KiSystemServiceStart+0x9:
fffff802`aa8b20c9 c1ef07 shr edi,7
2: kd> r
rax=000000000000003e rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=000000000000003e
rip=fffff802aa8b20c9 rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=00000000000003b0
r11=0000000000000246 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040246
nt!KiSystemServiceStart+0x9:
fffff802`aa8b20c9 c1ef07 shr edi,7
2: kd> t
nt!KiSystemServiceStart+0xc:
fffff802`aa8b20cc 83e720 and edi,20h
2: kd> r
rax=000000000000003e rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b20cc rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=00000000000003b0
r11=0000000000000246 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040246
nt!KiSystemServiceStart+0xc:
fffff802`aa8b20cc 83e720 and edi,20h
2: kd> t
nt!KiSystemServiceStart+0xf:
fffff802`aa8b20cf 25ff0f0000 and eax,0FFFh
2: kd> r
rax=000000000000003e rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b20cf rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=00000000000003b0
r11=0000000000000246 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040246
nt!KiSystemServiceStart+0xf:
fffff802`aa8b20cf 25ff0f0000 and eax,0FFFh
2: kd> t
nt!KiSystemServiceRepeat:
fffff802`aa8b20d4 4c8d15e5f7b400 lea r10,[nt!KeServiceDescriptorTable (fffff802`ab4018c0)]
2: kd> r
rax=000000000000003e rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b20d4 rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=00000000000003b0
r11=0000000000000246 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei pl nz na pe nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040202
nt!KiSystemServiceRepeat:
fffff802`aa8b20d4 4c8d15e5f7b400 lea r10,[nt!KeServiceDescriptorTable (fffff802`ab4018c0)]
2: kd> dq KeServiceDescriptorTable
fffff802`ab4018c0 fffff802`aa2d9600 00000000`00000000
fffff802`ab4018d0 00000000`000001e9 fffff802`aa2d9da8
fffff802`ab4018e0 00000000`00000000 00000000`00000000
fffff802`ab4018f0 00000000`00000000 00000000`00000000
fffff802`ab401900 fffff802`aa8aac40 fffff802`aa8aafc0
fffff802`ab401910 fffff802`aa8b0ac0 fffff802`aa8b0e40
fffff802`ab401920 fffff802`aa8b11c0 fffff802`aa8b1d40
fffff802`ab401930 fffff802`aa8b1800 00000000`00000000
2: kd> u fffff802`aa2d9da8
nt!KiArgumentTable:
fffff802`aa2d9da8 1000 adc byte ptr [rax],al
fffff802`aa2d9daa 0800 or byte ptr [rax],al
fffff802`aa2d9dac 0000 add byte ptr [rax],al
fffff802`aa2d9dae 1418 adc al,18h
fffff802`aa2d9db0 1404 adc al,4
fffff802`aa2d9db2 0000 add byte ptr [rax],al
fffff802`aa2d9db4 0000 add byte ptr [rax],al
fffff802`aa2d9db6 0000 add byte ptr [rax],al
2: kd> t
nt!KiSystemServiceRepeat+0x7:
fffff802`aa8b20db 4c8d1d9e419100 lea r11,[nt!KeServiceDescriptorTableShadow (fffff802`ab1c6280)]
2: kd> r
rax=000000000000003e rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b20db rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=fffff802ab4018c0
r11=0000000000000246 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei pl nz na pe nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040202
nt!KiSystemServiceRepeat+0x7:
fffff802`aa8b20db 4c8d1d9e419100 lea r11,[nt!KeServiceDescriptorTableShadow (fffff802`ab1c6280)]
2: kd> dq KeServiceDescriptorTableShadow
fffff802`ab1c6280 fffff802`aa2d9600 00000000`00000000
fffff802`ab1c6290 00000000`000001e9 fffff802`aa2d9da8
fffff802`ab1c62a0 fffff802`3c0be000 00000000`00000000
fffff802`ab1c62b0 00000000`000005cc fffff802`3c0bfd04
fffff802`ab1c62c0 fffff802`aa7d89f0 00000000`00000000
fffff802`ab1c62d0 ffffba85`b76a6c40 ffffffff`80000018
fffff802`ab1c62e0 00000000`00000000 ffffba85`b7692940
fffff802`ab1c62f0 00000000`00000000 ffffba85`b7702a00
2: kd> u fffff802`aa2d9da8
nt!KiArgumentTable:
fffff802`aa2d9da8 1000 adc byte ptr [rax],al
fffff802`aa2d9daa 0800 or byte ptr [rax],al
fffff802`aa2d9dac 0000 add byte ptr [rax],al
fffff802`aa2d9dae 1418 adc al,18h
fffff802`aa2d9db0 1404 adc al,4
fffff802`aa2d9db2 0000 add byte ptr [rax],al
fffff802`aa2d9db4 0000 add byte ptr [rax],al
fffff802`aa2d9db6 0000 add byte ptr [rax],al
2: kd> t
nt!KiSystemServiceRepeat+0xe:
fffff802`aa8b20e2 f7437880000000 test dword ptr [rbx+78h],80h
2: kd> t
nt!KiSystemServiceRepeat+0x15:
fffff802`aa8b20e9 7413 je nt!KiSystemServiceRepeat+0x2a (fffff802`aa8b20fe)
2: kd> t
nt!KiSystemServiceRepeat+0x2a:
fffff802`aa8b20fe 413b443a10 cmp eax,dword ptr [r10+rdi+10h]
2: kd> t
nt!KiSystemServiceRepeat+0x2f:
fffff802`aa8b2103 0f83be080000 jae nt!KiSystemServiceExitPico+0x31c (fffff802`aa8b29c7)
2: kd> t
nt!KiSystemServiceRepeat+0x35:
fffff802`aa8b2109 4d8b143a mov r10,qword ptr [r10+rdi]
2: kd> r
rax=000000000000003e rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b2109 rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=fffff802ab4018c0
r11=fffff802ab1c6280 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei ng nz na po cy
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040287
nt!KiSystemServiceRepeat+0x35:
fffff802`aa8b2109 4d8b143a mov r10,qword ptr [r10+rdi] ds:002b:fffff802`ab4018c0={nt!KiServiceTable (fffff802`aa2d9600)}
2: kd> dq KeServiceDescriptorTable
fffff802`ab4018c0 fffff802`aa2d9600 00000000`00000000
fffff802`ab4018d0 00000000`000001e9 fffff802`aa2d9da8
fffff802`ab4018e0 00000000`00000000 00000000`00000000
fffff802`ab4018f0 00000000`00000000 00000000`00000000
fffff802`ab401900 fffff802`aa8aac40 fffff802`aa8aafc0
fffff802`ab401910 fffff802`aa8b0ac0 fffff802`aa8b0e40
fffff802`ab401920 fffff802`aa8b11c0 fffff802`aa8b1d40
fffff802`ab401930 fffff802`aa8b1800 00000000`00000000
2: kd> t
nt!KiSystemServiceRepeat+0x39:
fffff802`aa8b210d 4d631c82 movsxd r11,dword ptr [r10+rax*4]
2: kd> r
rax=000000000000003e rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b210d rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=fffff802aa2d9600
r11=fffff802ab1c6280 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei ng nz na po cy
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040287
nt!KiSystemServiceRepeat+0x39:
fffff802`aa8b210d 4d631c82 movsxd r11,dword ptr [r10+rax*4] ds:002b:fffff802`aa2d96f8=08cf2a00
2: kd> dd r10
fffff802`aa2d9600 02b46204 038b2500 09193402 0711e100
fffff802`aa2d9610 07687300 05c63d00 0767d505 07f39606
fffff802`aa2d9620 07f31d05 08b53a01 08e54600 07e1b300
fffff802`aa2d9630 0913e500 08b20100 08b49000 07683d00
fffff802`aa2d9640 07efc101 08ae1001 09fac300 0759a702
fffff802`aa2d9650 086ab600 07982f00 07671301 09fae402
fffff802`aa2d9660 07891e02 08f12501 08e1f701 09cc2f05
fffff802`aa2d9670 07ea7600 09fa2c03 07824300 09c50e00
2: kd> dd r10+3e
fffff802`aa2d963e c1010768 100107ef c30008ae a70209fa
fffff802`aa2d964e b6000759 2f00086a 13010798 e4020767
fffff802`aa2d965e 1e0209fa 25010789 f70108f1 2f0508e1
fffff802`aa2d966e 760009cc 2c0307ea 430009fa 0e000782
fffff802`aa2d967e 390009c5 fe0108bb 5b0009ef 000208ec
fffff802`aa2d968e 950008ef 240107c1 090008e2 50010924
fffff802`aa2d969e f50601f7 5b070787 19000832 b50107d9
fffff802`aa2d96ae b00007e1 c2000991 950509b9 970109e0
2: kd> dd r10+3e*4
fffff802`aa2d96f8 08cf2a00 08e3bd01 09226e00 081e3302
fffff802`aa2d9708 07c14902 05c4d600 0980ad00 091ad901
fffff802`aa2d9718 02874a00 06d92800 07c35701 0821db01
fffff802`aa2d9728 0950b103 09275e00 088c2d00 068bcd05
fffff802`aa2d9738 068bd704 09351500 07832c01 08c69c01
fffff802`aa2d9748 0930a200 07805a00 065ad302 08ac6c07
fffff802`aa2d9758 08224201 065ad302 09112400 0832640c
fffff802`aa2d9768 06cee600 08b6a001 09242500 090c5500
2: kd> t
nt!KiSystemServiceRepeat+0x3d:
fffff802`aa8b2111 498bc3 mov rax,r11
2: kd> r
rax=000000000000003e rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b2111 rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=fffff802aa2d9600
r11=0000000008cf2a00 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei ng nz na po cy
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040287
nt!KiSystemServiceRepeat+0x3d:
fffff802`aa8b2111 498bc3 mov rax,r11
2: kd> t
nt!KiSystemServiceRepeat+0x40:
fffff802`aa8b2114 49c1fb04 sar r11,4
2: kd> t
nt!KiSystemServiceRepeat+0x44:
fffff802`aa8b2118 4d03d3 add r10,r11
2: kd> r
rax=0000000008cf2a00 rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b2118 rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=fffff802aa2d9600
r11=00000000008cf2a0 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei pl nz na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040206
nt!KiSystemServiceRepeat+0x44:
fffff802`aa8b2118 4d03d3 add r10,r11
2: kd> t
nt!KiSystemServiceRepeat+0x47:
fffff802`aa8b211b 83ff20 cmp edi,20h
2: kd> r
rax=0000000008cf2a00 rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b211b rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=fffff802aaba88a0
r11=00000000008cf2a0 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei ng nz na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040286
nt!KiSystemServiceRepeat+0x47:
fffff802`aa8b211b 83ff20 cmp edi,20h
2: kd> u r10 L10
nt!NtClearEvent:
fffff802`aaba88a0 48895c2408 mov qword ptr [rsp+8],rbx
fffff802`aaba88a5 48896c2418 mov qword ptr [rsp+18h],rbp
fffff802`aaba88aa 56 push rsi
fffff802`aaba88ab 57 push rdi
fffff802`aaba88ac 4156 push r14
fffff802`aaba88ae 4883ec30 sub rsp,30h
fffff802`aaba88b2 65488b042588010000 mov rax,qword ptr gs:[188h]
fffff802`aaba88bb 4533f6 xor r14d,r14d
fffff802`aaba88be 4c8b05bbd26100 mov r8,qword ptr [nt!ExEventObjectType (fffff802`ab1c5b80)]
fffff802`aaba88c5 488bf1 mov rsi,rcx
fffff802`aaba88c8 4c89742428 mov qword ptr [rsp+28h],r14
fffff802`aaba88cd 4c89742458 mov qword ptr [rsp+58h],r14
fffff802`aaba88d2 0fb6a832020000 movzx ebp,byte ptr [rax+232h]
fffff802`aaba88d9 418d5602 lea edx,[r14+2]
fffff802`aaba88dd 488d442458 lea rax,[rsp+58h]
fffff802`aaba88e2 440fb6cd movzx r9d,bpl
2: kd> t
nt!KiSystemServiceRepeat+0x4a:
fffff802`aa8b211e 7550 jne nt!KiSystemServiceGdiTebAccess+0x49 (fffff802`aa8b2170)
2: kd> t
nt!KiSystemServiceGdiTebAccess+0x49:
fffff802`aa8b2170 83e00f and eax,0Fh
2: kd> t
nt!KiSystemServiceGdiTebAccess+0x4c:
fffff802`aa8b2173 0f84b7000000 je nt!KiSystemServiceCopyEnd (fffff802`aa8b2230)
2: kd> t
nt!KiSystemServiceCopyEnd:
fffff802`aa8b2230 f705c63a910001000000 test dword ptr [nt!KiDynamicTraceMask (fffff802`ab1c5d00)],1
2: kd> t
nt!KiSystemServiceCopyEnd+0xa:
fffff802`aa8b223a 0f8546080000 jne nt!KiSystemServiceExitPico+0x3db (fffff802`aa8b2a86)
2: kd> t
nt!KiSystemServiceCopyEnd+0x10:
fffff802`aa8b2240 f705be38910040000000 test dword ptr [nt!PerfGlobalGroupMask+0x8 (fffff802`ab1c5b08)],40h
2: kd> t
nt!KiSystemServiceCopyEnd+0x1a:
fffff802`aa8b224a 0f85aa080000 jne nt!KiSystemServiceExitPico+0x44f (fffff802`aa8b2afa)
2: kd> t
nt!KiSystemServiceCopyEnd+0x20:
fffff802`aa8b2250 498bc2 mov rax,r10
2: kd> t
nt!KiSystemServiceCopyEnd+0x23:
fffff802`aa8b2253 ffd0 call rax
2: kd> r
rax=fffff802aaba88a0 rbx=ffffba85be3a50c0 rcx=00000000000003b0
rdx=00000146fc1fac00 rsi=00000146fc1f2840 rdi=0000000000000000
rip=fffff802aa8b2253 rsp=ffffe40571377aa0 rbp=ffffe40571377b20
r8=00000146fb3b02c0 r9=000000049609b000 r10=fffff802aaba88a0
r11=00000000008cf2a0 r12=0000000000000000 r13=0000000000000000
r14=00007ffeb3875fd0 r15=00007ffeb388b118
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00040246
nt!KiSystemServiceCopyEnd+0x23:
fffff802`aa8b2253 ffd0 call rax {nt!NtClearEvent (fffff802`aaba88a0)}
2: kd> dq KeServiceDescriptorTable
fffff802`ab4018c0 fffff802`aa2d9600 00000000`00000000
fffff802`ab4018d0 00000000`000001e9 fffff802`aa2d9da8
fffff802`ab4018e0 00000000`00000000 00000000`00000000
fffff802`ab4018f0 00000000`00000000 00000000`00000000
fffff802`ab401900 fffff802`aa8aac40 fffff802`aa8aafc0
fffff802`ab401910 fffff802`aa8b0ac0 fffff802`aa8b0e40
fffff802`ab401920 fffff802`aa8b11c0 fffff802`aa8b1d40
fffff802`ab401930 fffff802`aa8b1800 00000000`00000000
2: kd> dd fffff802`aa2d9600+3F*4
fffff802`aa2d96fc 08e3bd01 09226e00 081e3302 07c14902
fffff802`aa2d970c 05c4d600 0980ad00 091ad901 02874a00
fffff802`aa2d971c 06d92800 07c35701 0821db01 0950b103
fffff802`aa2d972c 09275e00 088c2d00 068bcd05 068bd704
fffff802`aa2d973c 09351500 07832c01 08c69c01 0930a200
fffff802`aa2d974c 07805a00 065ad302 08ac6c07 08224201
fffff802`aa2d975c 065ad302 09112400 0832640c 06cee600
fffff802`aa2d976c 08b6a001 09242500 090c5500 02698a00
2: kd> u 08e3bd0+fffff802`aa2d9600 L 10
nt!NtReadVirtualMemory:
fffff802`aabbd1d0 4883ec48 sub rsp,48h
fffff802`aabbd1d4 488b442470 mov rax,qword ptr [rsp+70h]
fffff802`aabbd1d9 c744243000000000 mov dword ptr [rsp+30h],0
fffff802`aabbd1e1 c744242810000000 mov dword ptr [rsp+28h],10h
fffff802`aabbd1e9 4889442420 mov qword ptr [rsp+20h],rax
fffff802`aabbd1ee e80d000000 call nt!MiReadWriteVirtualMemory (fffff802`aabbd200)
fffff802`aabbd1f3 4883c448 add rsp,48h
fffff802`aabbd1f7 c3 ret
fffff802`aabbd1f8 cc int 3
fffff802`aabbd1f9 cc int 3
fffff802`aabbd1fa cc int 3
fffff802`aabbd1fb cc int 3
fffff802`aabbd1fc cc int 3
fffff802`aabbd1fd cc int 3
fffff802`aabbd1fe cc int 3
fffff802`aabbd1ff cc int 3
2: kd> dd fffff802`aa2d9600+26*4
fffff802`aa2d9698 09240900 01f75001 0787f506 08325b07
fffff802`aa2d96a8 07d91900 07e1b501 0991b000 09b9c200
fffff802`aa2d96b8 09e09505 07c19701 08f72400 09123f00
fffff802`aa2d96c8 09fa5802 08ac6502 07746700 07f71807
fffff802`aa2d96d8 08f75300 09228000 096f5601 07f31606
fffff802`aa2d96e8 08e3ba01 0931d300 075cfc03 077b4400
fffff802`aa2d96f8 08cf2a00 08e3bd01 09226e00 081e3302
fffff802`aa2d9708 07c14902 05c4d600 0980ad00 091ad901
2: kd> u 924090+fffff802`aa2d9600 L 10
nt!NtOpenProcess:
fffff802`aabfd690 4883ec38 sub rsp,38h
fffff802`aabfd694 65488b042588010000 mov rax,qword ptr gs:[188h]
fffff802`aabfd69d 448a9032020000 mov r10b,byte ptr [rax+232h]
fffff802`aabfd6a4 4488542428 mov byte ptr [rsp+28h],r10b
fffff802`aabfd6a9 4488542420 mov byte ptr [rsp+20h],r10b
fffff802`aabfd6ae e8adc9e4ff call nt!PsOpenProcess (fffff802`aaa4a060)
fffff802`aabfd6b3 4883c438 add rsp,38h
fffff802`aabfd6b7 c3 ret
fffff802`aabfd6b8 cc int 3
fffff802`aabfd6b9 cc int 3
fffff802`aabfd6ba cc int 3
fffff802`aabfd6bb cc int 3
fffff802`aabfd6bc cc int 3
fffff802`aabfd6bd cc int 3
fffff802`aabfd6be cc int 3
fffff802`aabfd6bf cc int 3