前情提要:通过本篇博客,你可以学会keepalived+LVS实现高可用+高性能的web&mariadb双主双业务集群架构的详细架构原理,keepalived的基本初始化配置,还有该双主双业务架构的各个主机的详细环境配置以及keepalived的详细配置,最终可以实现IPVS的高可用+高性能的web&mariadb集群
一、实验环境配置
1.1 架构图
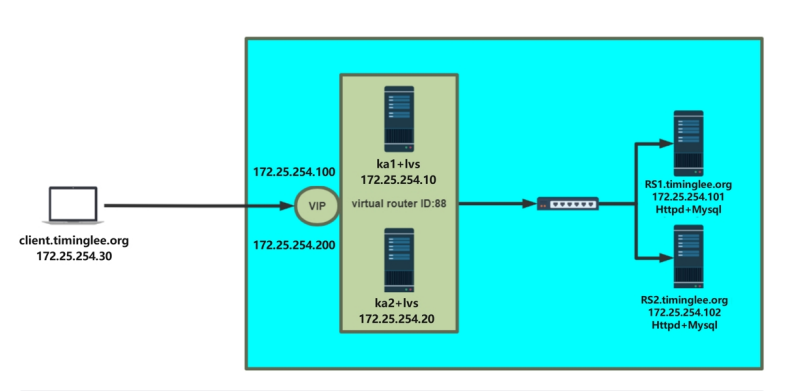
注意:IP地址请以主机环境清单为准。
1.2 主机环境清单
- KA1
- IP:172.25.254.50/24,NAT网卡,VIP:172.25.254.100/24,172.25.254.200/24
- KA2
- IP:172.25.254.60/24,NAT网卡,VIP:172.25.254.100/24,172.25.254.200/24
- RS1
- IP:172.25.254.10/24,NAT网卡
- RS2
- IP:172.25.254.20/24,NAT网卡
1.3 主机环境配置
1、配置RS1和RS2主机的IP地址
RS1如下
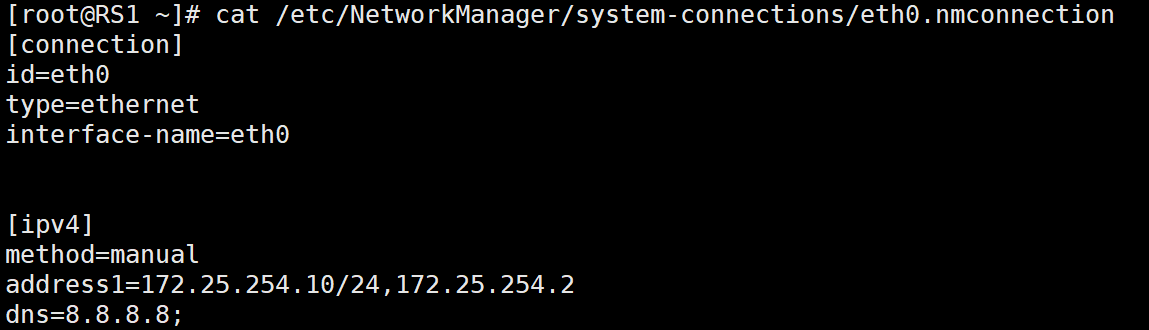
RS2如下
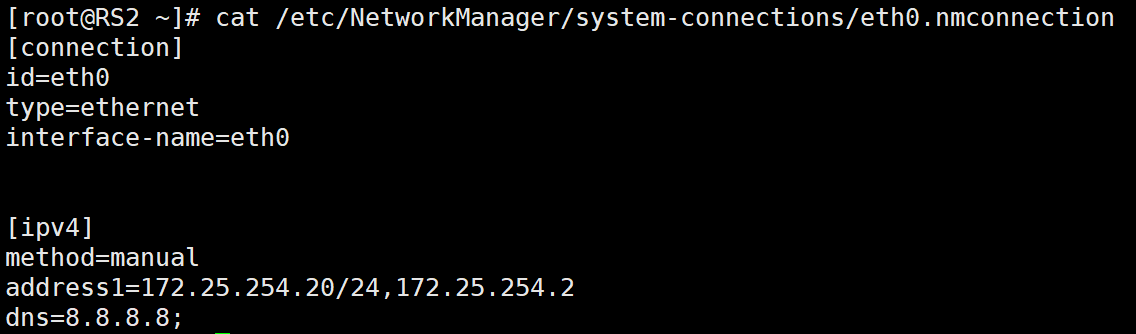
2、配置KA1和KA2主机的IP地址
KA1如下
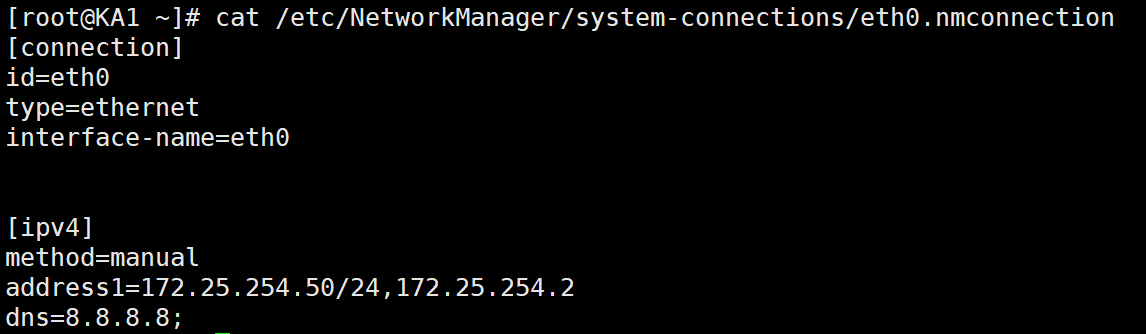
KA2如下
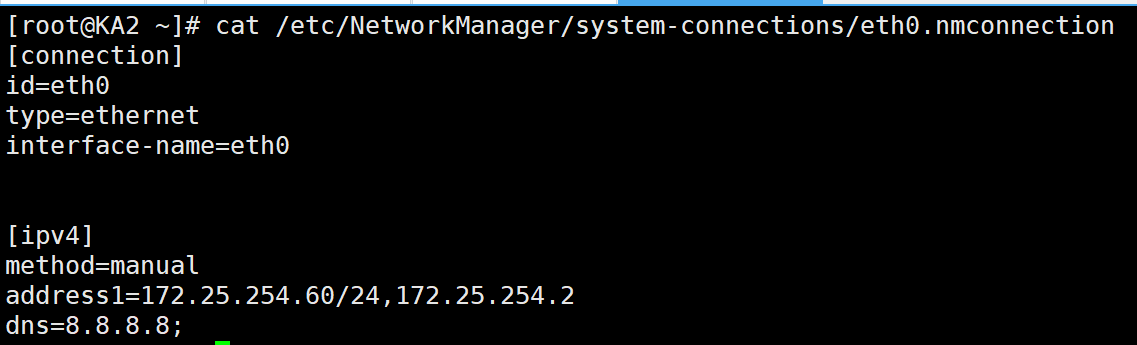
以上IP地址请自行配置
3、配置KA1和KA2主机的本地解析
操作如下
bash
[root@KA1 ~]# vim /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
172.25.254.50 KA1
172.25.254.60 KA2
172.25.254.10 RS1
172.25.254.20 RS2
[root@KA1 ~]# scp /etc/hosts 172.25.254.60:/etc/hosts
hosts 100% 244 488.6KB/s 00:00 以上完成了KA1和KA2主机的本地解析配置
4、配置KA1和KA2的时间同步
KA1如下
KA1修改**/etc/chrony.conf** 配置文件第26行白名单并取消第29行注释,核心作用是:在网络中所有外部时间源都失效时,防止 Chrony 服务完全停止,并允许本地服务器继续为网络内的其他客户端提供时间同步服务
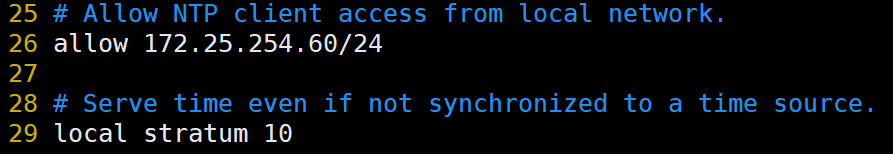
修改完成后重启chronyd并且设定开机自启动
bash
[root@KA1 ~]# systemctl restart chronyd
[root@KA1 ~]# systemctl enable --now chronydKA2如下
修改**/etc/chrony.conf**修改时间服务器为KA1主机
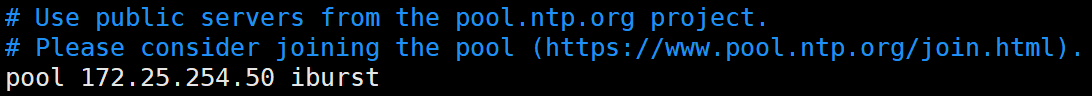
然后重启并设定开机自启即可
bash
[root@KA2 ~]# systemctl restart chronyd
[root@KA2 ~]# systemctl enable --now chronyd最后检测KA2是否可以和KA1进行时间同步
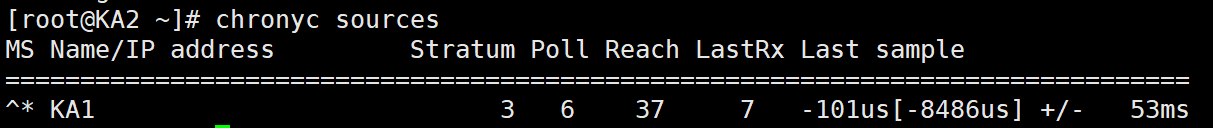
可见时间同步成功,配置正确
至此实验主机环境配置结束
二、Keepalived初始化配置
首先分别在KA1和KA2上安装Keepalived并且设定开机自启动
bash
# KA1
[root@KA1 ~]# dnf install keepalived.x86_64 -y
[root@KA1 ~]# systemctl enable --now keepalived
# KA2
[root@KA2 ~]# dnf install keepalived.x86_64 -y
[root@KA2 ~]# systemctl enable --now keepalived2.1 日志分离
默认情况下。keepalived的日志会被保存在/var/log/messages文件中,这个文件中除了含有keepalived的日志外,还有其他服务的日志信息,这样不利于对于keepalived的日志进行查看
在KA1和KA2主机上均做如下配置,此处以KA1为例
bash
[root@KA1 ~]# vim /etc/sysconfig/keepalived
KEEPALIVED_OPTIONS="-D -S 6"
[root@KA1 ~]# systemctl restart keepalived.service
[root@KA1 ~]# vim /etc/rsyslog.conf
local6.* /var/log/keepalived.log
[root@KA1 ~]# systemctl restart rsyslog.service
#测试
[root@KA1 log]# systemctl restart keepalived
[root@KA1 log]# ls /var/log/keepalived.log
keepalived.log至此成功实现keepalived的日志分离
2.2 子配置文件
在主配置文件中如果写入过多的配置不利于对于主配置文件的阅读
以KA1为例
在keepalived的主配置/etc/keepalived/keepalived.conf文件加入以下内容,然后创建子配置文件目录
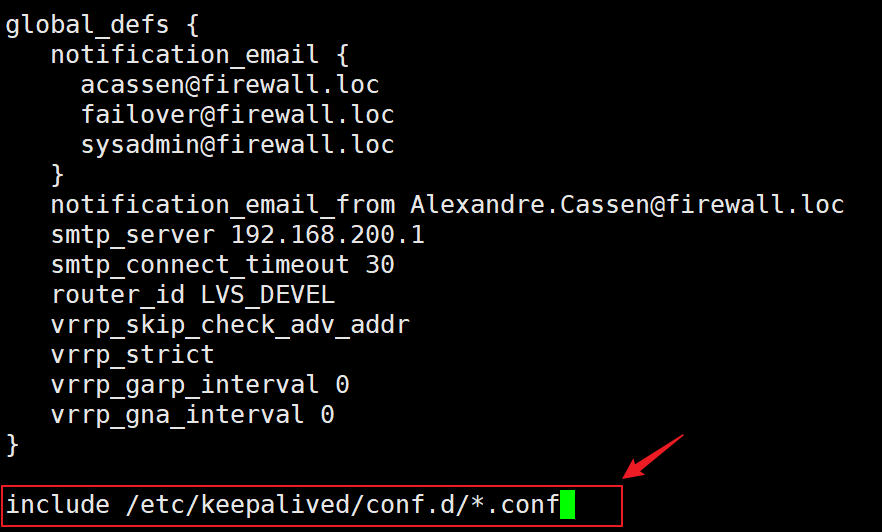
bash
[root@KA1 ~]# mkdir /etc/keepalived/conf.d以上完成了子配置文件目录的创建,后续配置keepalived时将配置文件放在该目录下即可
三、LVS相关环境配置
1、配置RS1和RS2回环网卡,以RS1为例
bash
[root@RS1 system-connections]# cp eth0.nmconnection lo.nmconnection -p
[root@RS1 system-connections]# vim lo.nmconnection
[connection]
id=lo
type=loopback
interface-name=lo
[ipv4]
method=manual
address1=127.0.0.1/8
address2=172.25.254.100/32
address3=172.25.254.200/32
[root@RS1 system-connections]# nmcli connection reload
[root@RS1 system-connections]# nmcli connection up lo
连接已成功激活(D-Bus 活动路径:/org/freedesktop/NetworkManager/ActiveConnection/5)
[root@RS1 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet 172.25.254.100/32 scope global lo
valid_lft forever preferred_lft forever
inet 172.25.254.200/32 scope global lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:0c:29:41:fa:79 brd ff:ff:ff:ff:ff:ff
altname enp3s0
altname ens160
inet 172.25.254.10/24 brd 172.25.254.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::2360:d7ac:9af2:bb39/64 scope link noprefixroute
valid_lft forever preferred_lft forever2、禁止arp响应,以RS1为例
bash
[root@RS1 ~]# vim /etc/sysctl.conf
net.ipv4.conf.all.arp_ignore=1
net.ipv4.conf.all.arp_announce=2
net.ipv4.conf.lo.arp_announce=2
net.ipv4.conf.lo.arp_ignore=1
[root@RS1 ~]# sysctl -p
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
net.ipv4.conf.lo.arp_announce = 2
net.ipv4.conf.lo.arp_ignore = 13、KA1和KA2安装LVS
bash
[root@KA1 ~]# dnf install ipvsadm -y四、业务配置
本次实验中我们使用该架构同时提供web服务和数据库服务,首先我们需要在RS1和RS2中部署服务
3.1 部署web服务和数据库服务
3.1.1 RS1和RS2http服务配置
RS1和RS2均安装apache
bash
[root@RS1 ~]# dnf install httpd -yRS1配置测试网页
bash
[root@RS1 ~]# echo 172.25.254.10-RS1 > /var/www/html/index.html
[root@RS1 ~]# curl 172.25.254.10
172.25.254.10-RS1RS2配置测试网页
bash
[root@RS2 ~]# echo 172.25.254.20-RS2 > /var/www/html/index.html
[root@RS2 ~]# curl 172.25.254.20
172.25.254.20-RS2注意:实际生产环境中需要两台服务主机提供相同服务,此处仅为了后续测试而使用不同的html页面内容
3.1.2 RS1和RS2mariadb服务配置
RS1与RS2均安装mariadb-server并启动
bash
[root@RS1 ~]# dnf install mariadb-server -y
[root@RS1 ~]# systemctl enable --now mariadbRS1与RS2均创建角色
bash
MariaDB [(none)]> create user 'dragon'@'%' identified by '123';
Query OK, 0 rows affected (0.002 sec)
MariaDB [(none)]> grant all on *.* to 'dragon'@'%';
Query OK, 0 rows affected (0.002 sec)注意:该数据库配置实际上是分开的两个服务,RS1和RS2并没有实现数据库数据共享,若需要配置成同一个数据库服务,请看博主置顶博文https://blog.csdn.net/2301_79481320/article/details/155075834?fromshare=blogdetail&sharetype=blogdetail&sharerId=155075834&sharerefer=PC&sharesource=2301_79481320&sharefrom=from_link
3.2 配置keepalived虚拟路由
修改KA1主配置文件如下
bash
[root@KA1 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
doubledragon@163.com
}
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id KA1
vrrp_skip_check_adv_addr
#vrrp_strict
vrrp_garp_interval 1
vrrp_gna_interval 1
vrrp_mcast_group4 224.0.0.44
}
include /etc/keepalived/conf.d/*.conf
vrrp_instance WEB_VIP {
state MASTER
interface eth0
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:0
}
}修改KA2主配置文件如下
bash
[root@KA2 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
doubledragon@163.com
}
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id KA2
vrrp_skip_check_adv_addr
#vrrp_strict
vrrp_garp_interval 1
vrrp_gna_interval 1
vrrp_mcast_group4 224.0.0.44
}
include /etc/keepalived/conf.d/*.conf
vrrp_instance WEB_VIP {
state BACKUP
interface eth0
virtual_router_id 51
priority 80
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.254.100/24 dev eth0 label eth0:0
}
}3.3 修改keepalived子配置文件
KA1如下
bash
[root@KA1 ~]# vim /etc/keepalived/conf.d/web.conf
virtual_server 172.25.254.100 80 {
delay_loop 6
lb_algo rr
lb_kind DR
protocol TCP
real_server 172.25.254.10 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 1
retry 3
delay_before_retry 1
}
}
real_server 172.25.254.20 80 {
weight 1
TCP_CHECK {
connect_timeout 5
retry 3
delay_before_retry 3
connect_port 80
}
}
}
[root@KA1 ~]# vim /etc/keepalived/conf.d/datebase.conf
virtual_server 172.25.254.200 3306 {
delay_loop 6
lb_algo rr
lb_kind DR
protocol TCP
real_server 172.25.254.10 3306 {
weight 1
TCP_CHECK {
connect_timeout 5
retry 3
delay_before_retry 3
connect_port 3306
}
}
real_server 172.25.254.20 3306 {
weight 1
TCP_CHECK {
connect_timeout 5
retry 3
delay_before_retry 3
connect_port 3306
}
}
}KA2如下
bash
[root@KA2 ~]# vim /etc/keepalived/conf.d/web.conf
real_server 172.25.254.10 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 1
retry 3
delay_before_retry 1
}
}
real_server 172.25.254.20 80 {
weight 1
TCP_CHECK {
connect_timeout 5
retry 3
delay_before_retry 3
connect_port 80
}
}
}
[root@KA2 ~]# vim /etc/keepalived/conf.d/datebase.conf
virtual_server 172.25.254.200 3306 {
delay_loop 6
lb_algo rr
lb_kind DR
protocol TCP
real_server 172.25.254.10 3306 {
weight 1
TCP_CHECK {
connect_timeout 5
retry 3
delay_before_retry 3
connect_port 3306
}
}
real_server 172.25.254.20 3306 {
weight 1
TCP_CHECK {
connect_timeout 5
retry 3
delay_before_retry 3
connect_port 3306
}
}
}3.4 重启服务并测试
重启KA1和KA2服务
bash
[root@KA1 ~]# systemctl restart keepalived.service查看KA1和KA2的VIP
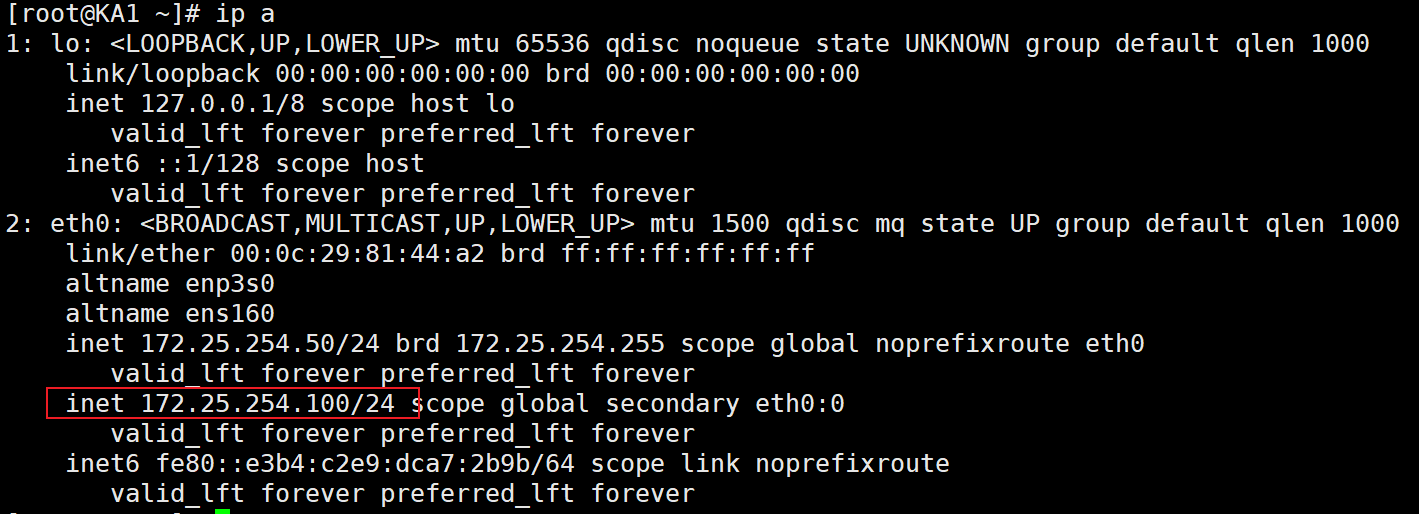
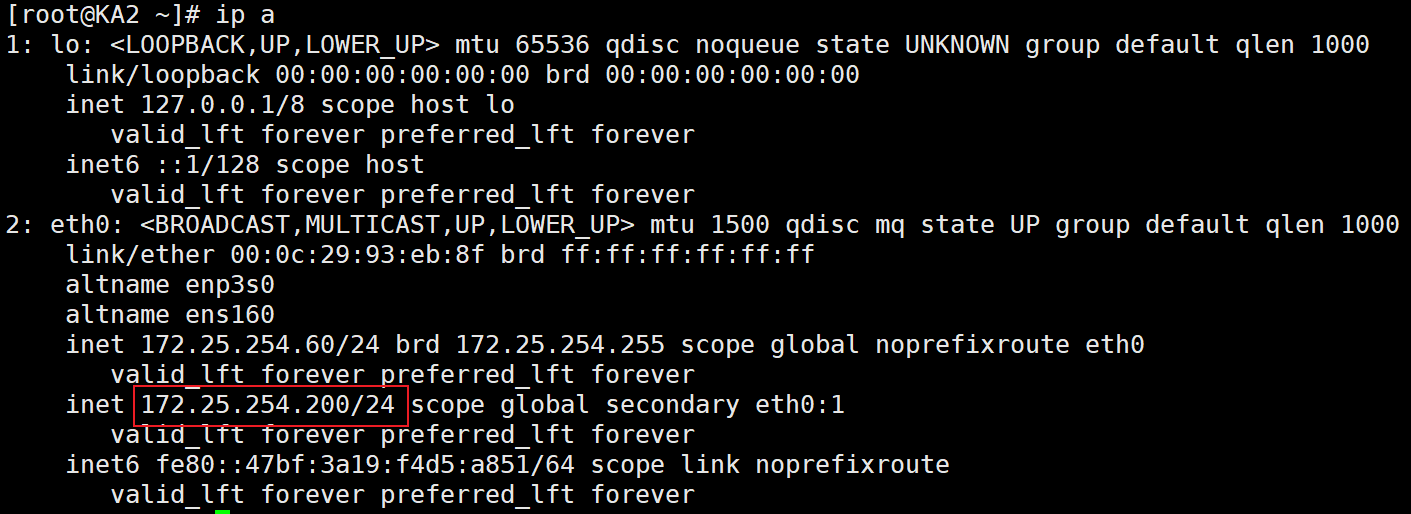
可见VIP没有问题
进行web访问测试
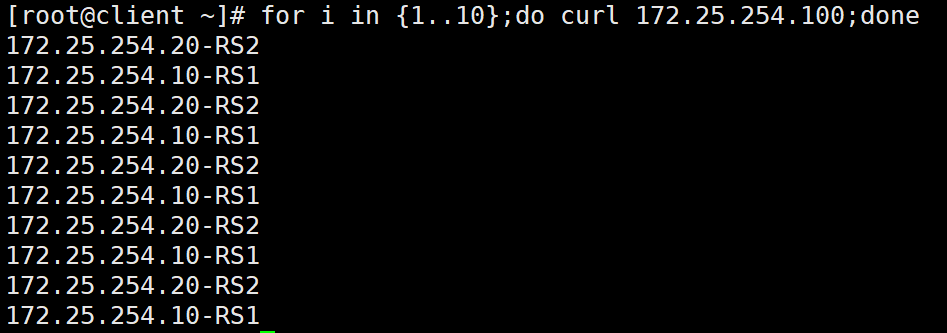
可见web访问测试没有问题
进行数据库访问测试
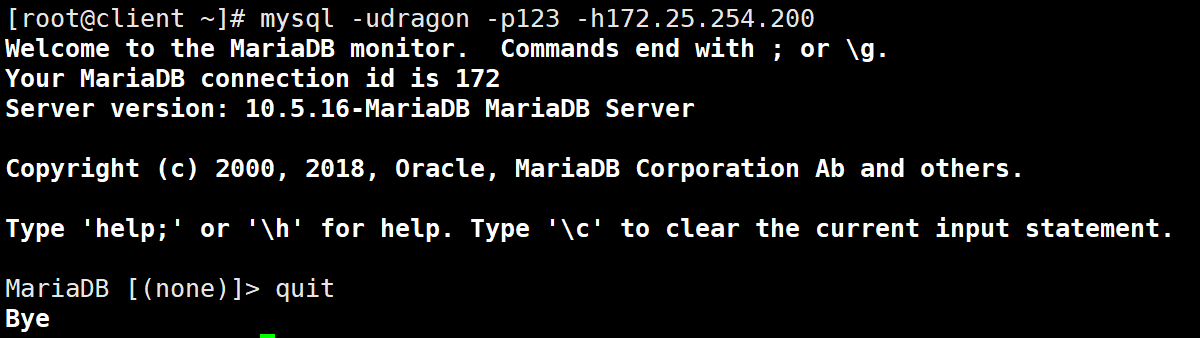
可见没有问题
VIP漂移测试
停止KA1的keepalived
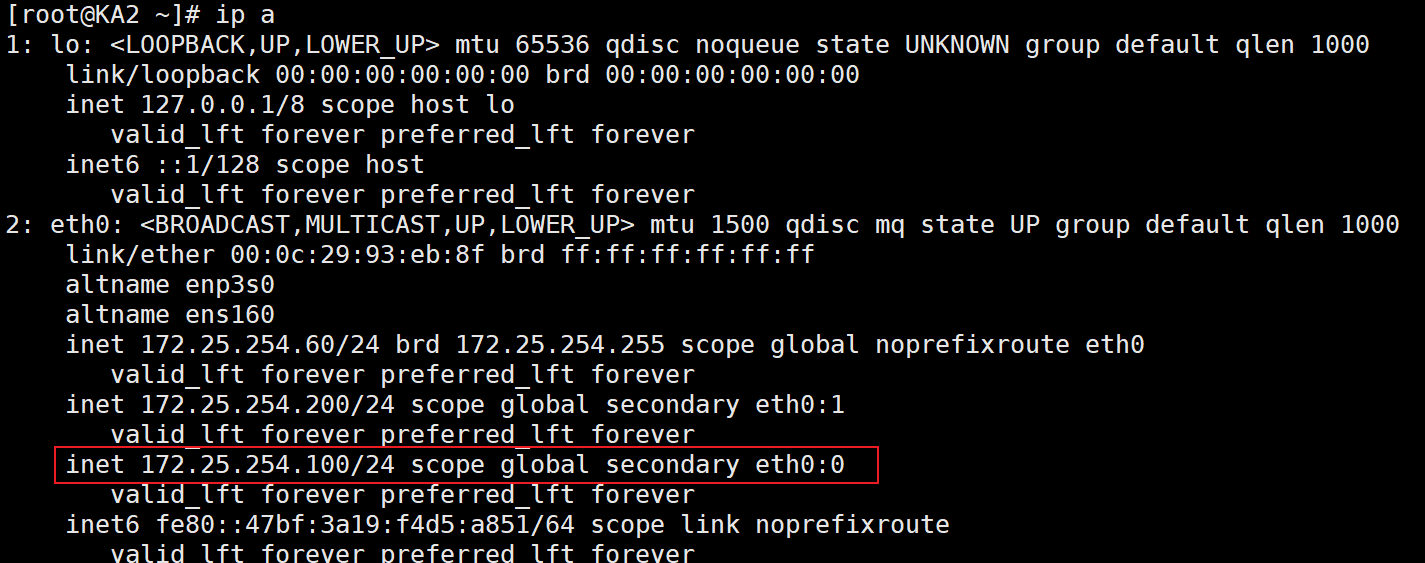
可见VIP成功漂移到KA2,没有问题
至此该实验完成