1. 部署GitLab
(1)基础准备
解压软件包并导入镜像:
shell
[root@master ~]# curl -O http://mirrors.douxuedu.com/competition/Gitlab-CI.tar.gz
[root@master ~]# tar -zxvf Gitlab-CI.tar.gz
[root@master ~]# ctr -n k8s.io image import gitlab-ci/images/images.tar
[root@master ~]# docker load < gitlab-ci/images/images.tar(2)部署GitLab服务
新建命名空间gitlab-ci:
shell
[root@master ~]# kubectl create ns gitlab-ci
namespace/gitlab-ci created在gitlab-ci命名空间下部署GitLab,将80端口以NodePort方式对外暴露为30880,YAML资源文件如下:
shell
[root@master ~]# cd gitlab-ci
[root@master gitlab-ci]# vi gitlab-deploy.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: gitlab
namespace: gitlab-ci
labels:
name: gitlab
spec:
selector:
matchLabels:
name: gitlab
template:
metadata:
name: gitlab
labels:
name: gitlab
spec:
containers:
- name: gitlab
image: gitlab/gitlab-ce:latest
imagePullPolicy: IfNotPresent
env:
- name: GITLAB_ROOT_PASSWORD
value: Abc@1234
- name: GITLAB_ROOT_EMAIL
value: 123456@qq.com
ports:
- name: http
containerPort: 80
volumeMounts:
- name: gitlab-config
mountPath: /etc/gitlab
- name: gitlab-logs
mountPath: /var/log/gitlab
- name: gitlab-data
mountPath: /var/opt/gitlab
volumes:
- name: gitlab-config
hostPath:
path: /home/gitlab/conf
- name: gitlab-logs
hostPath:
path: /home/gitlab/logs
- name: gitlab-data
hostPath:
path: /home/gitlab/data创建service服务释放端口
shell
[root@master gitlab-ci]# vi gitlab-svc.yaml
apiVersion: v1
kind: Service
metadata:
name: gitlab
namespace: gitlab-ci
labels:
name: gitlab
spec:
type: NodePort
ports:
- name: http
port: 80
targetPort: http
nodePort: 30880
selector:
name: gitlab创建资源:
shell
[root@master gitlab-ci]# kubectl apply -f gitlab-deploy.yaml
deployment.apps/gitlab created
[root@master gitlab-ci]# kubectl apply -f gitlab-svc.yaml
service/gitlab created查看Pod:
shell
[root@master gitlab-ci]# kubectl -n gitlab-ci get pods
NAME READY STATUS RESTARTS AGE
gitlab-7b54df755-6ljtp 1/1 Running 0 45s(3)自定义hosts
查看GitLab Pod的IP地址:
shell
[root@master gitlab-ci]# kubectl -n gitlab-ci get pods -owide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
gitlab-7b54df755-6ljtp 1/1 Running 0 50s 10.244.1.43 k8s-worker-node1 <none> <none>在集群中自定义hosts添加gitlab Pod的解析:
shell
[root@master gitlab-ci]# kubectl edit configmap coredns -n kube-system
........
apiVersion: v1
data:
Corefile: |
.:53 {
errors
health {
lameduck 5s
}
ready
kubernetes cluster.local in-addr.arpa ip6.arpa {
pods insecure
fallthrough in-addr.arpa ip6.arpa
ttl 30
}
## 添加以下字段
hosts {
10.244.1.43 gitlab-7b54df755-6ljtp
fallthrough
}
prometheus :9153
##删除以下三行字段
forward . /etc/resolv.conf {
max_concurrent 1000
}
cache 30
loop
reload
loadbalance
}
........
[root@master gitlab-ci]# kubectl -n kube-system rollout restart deploy coredns
deployment.apps/coredns restarted进入gitlab pod中
shell
[root@master gitlab-ci]# kubectl exec -ti -n gitlab-ci gitlab-7b54df755-6ljtp bash
root@gitlab-7b54df755-6ljtp:/# vi /etc/gitlab/gitlab.rb 在首行添加(ip为pod IP地址)
shell
external_url 'http://10.244.1.43:80'
root@gitlab-7b54df755-6ljtp:/# reboot
root@gitlab-7b54df755-6ljtp:/# exit(4)访问GitLab
查看Service:
shell
[root@master gitlab-ci]# kubectl -n gitlab-ci get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
gitlab NodePort 10.96.108.3 <none> 80:30880/TCP 3m33s通过http://10.24.2.14:30880访问GitLab,用户名123456@qq.com,密码Abc@1234,如图1所示:
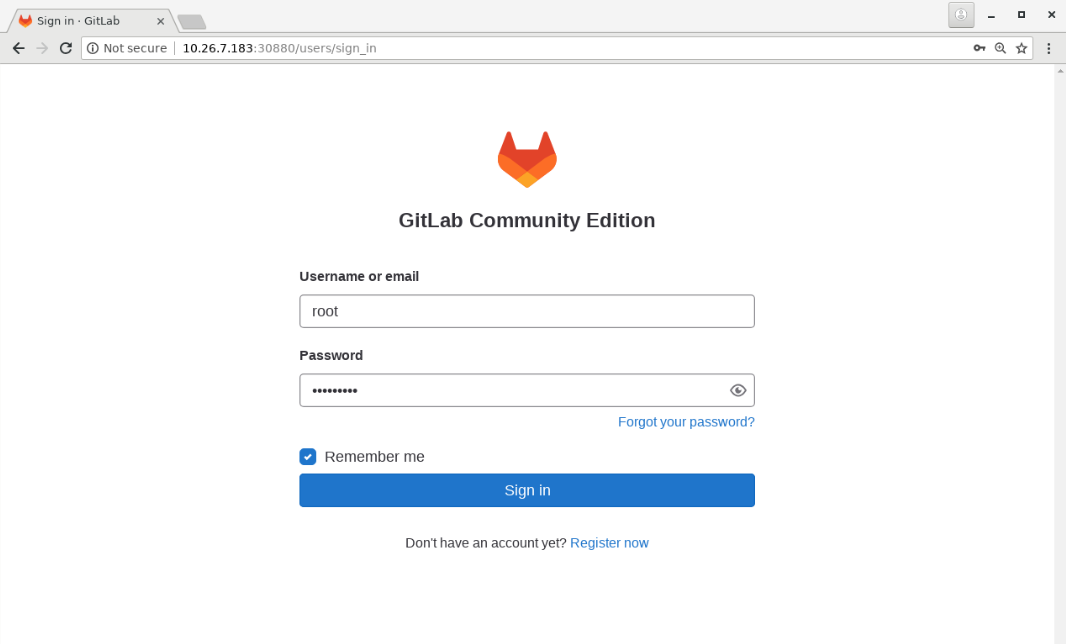
图1
(5)上传项目包
点击"Create a project"按钮,如图2所示:
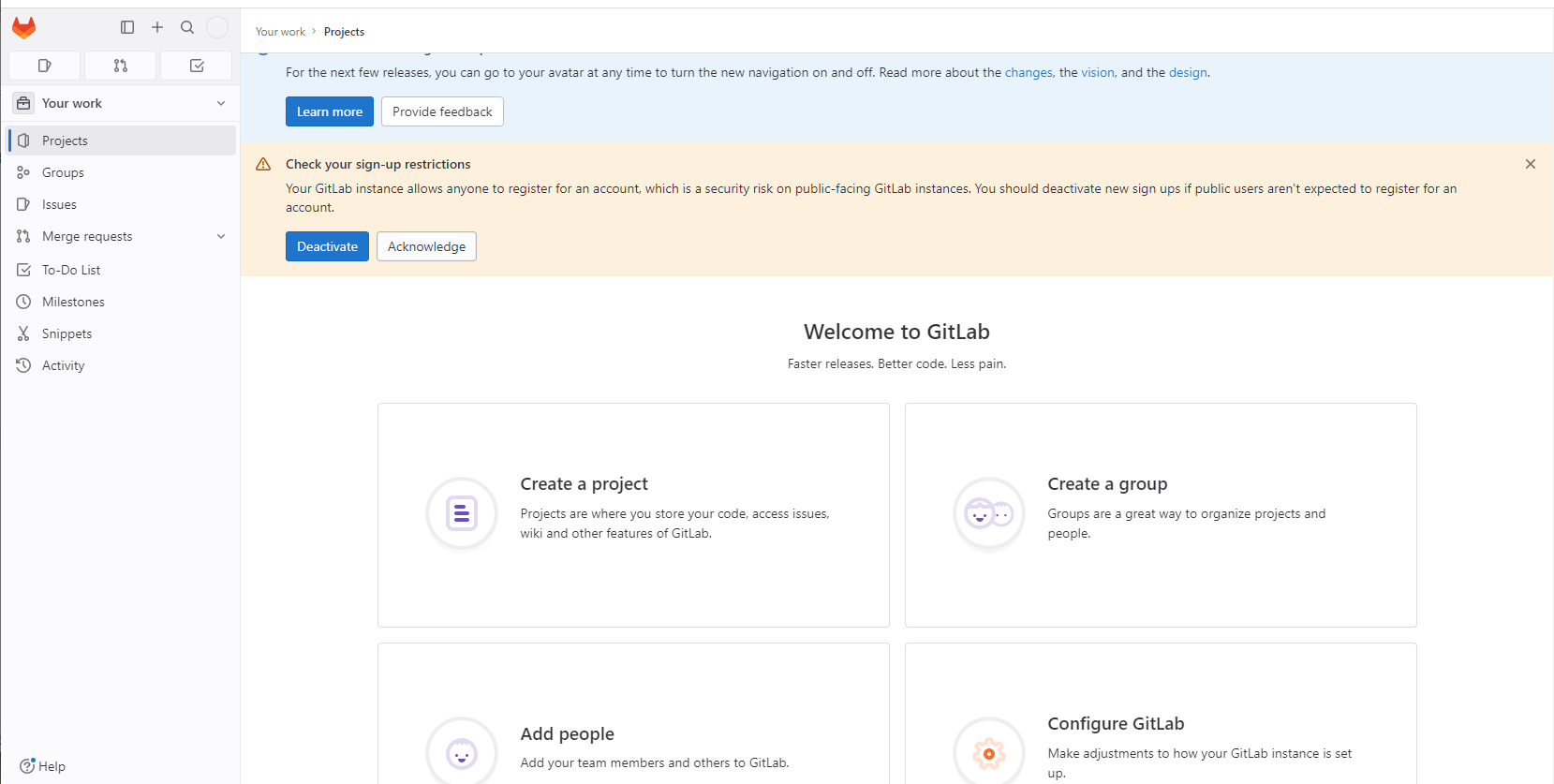
图2
点击"Create blank project"创建项目demo-2048,可见等级选择"Public",如图3所示:
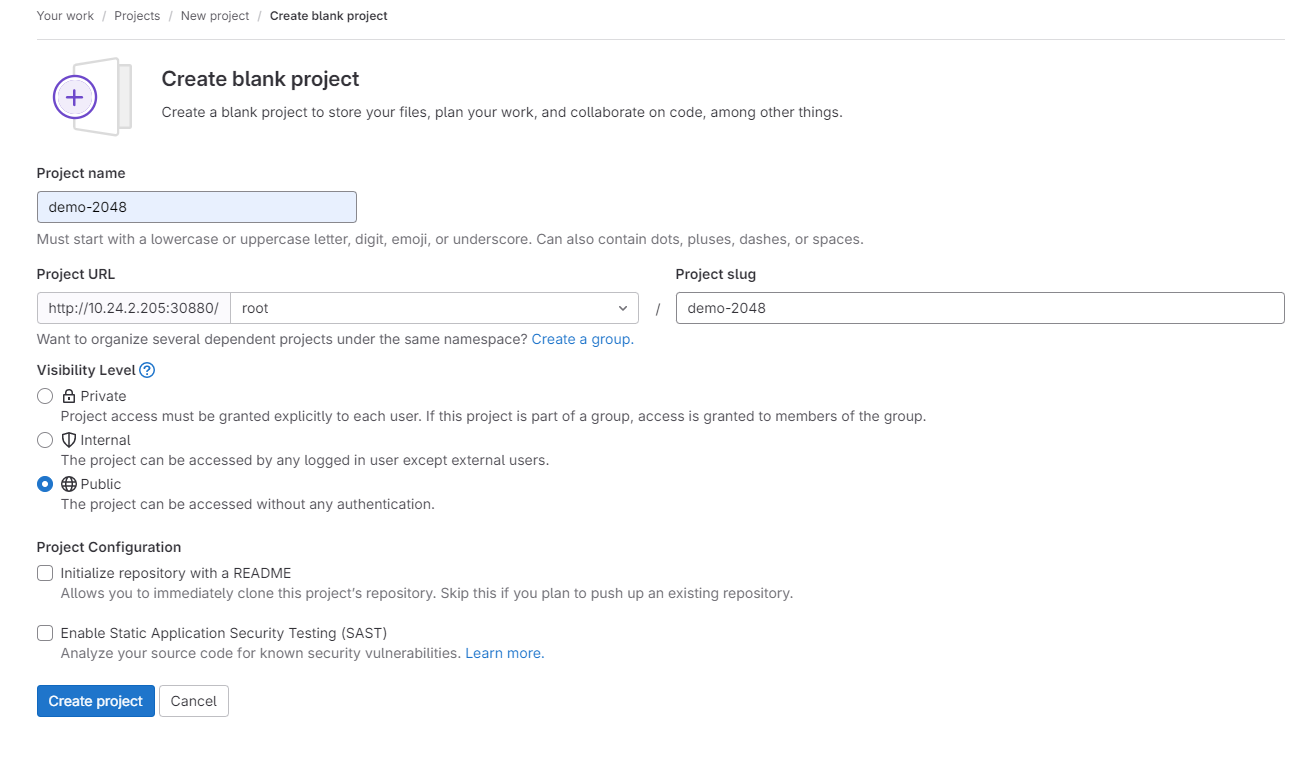
图3
点击"Create project",进入项目,如图4所示:
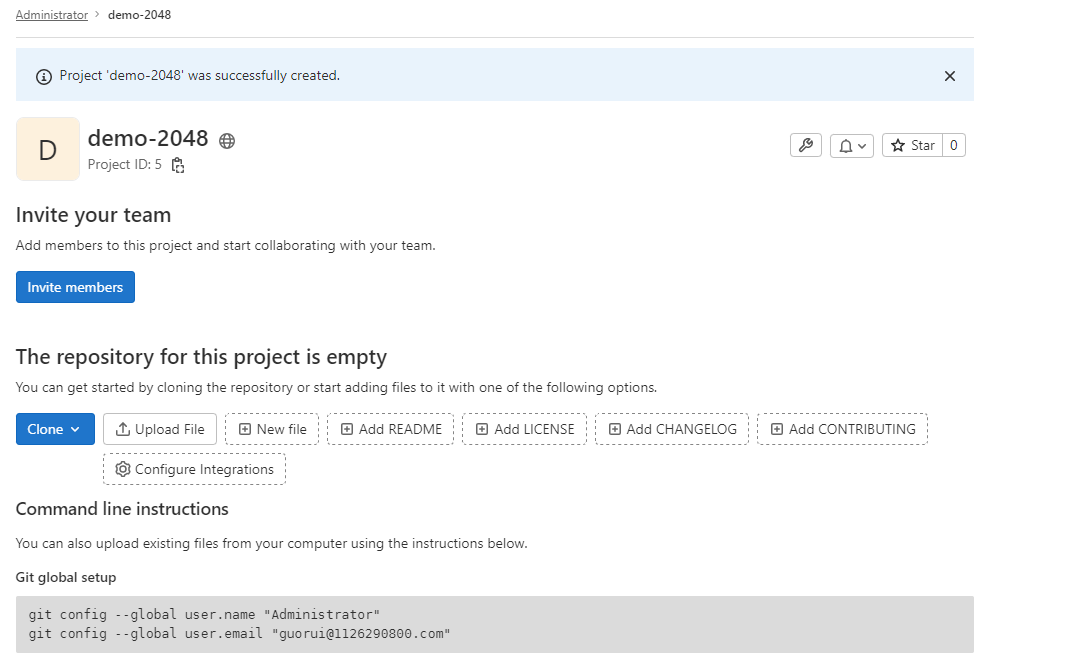
图4
将源代码推送到项目中:
shell
[root@master gitlab-ci]# cd /root/gitlab-ci/demo-2048
[root@master demo-2048]# git config --global user.name "administrator"
[root@master demo-2048]# git config --global user.email "admin@example.com"
[root@master demo-2048]# git remote remove origin
[root@master demo-2048]# git remote add origin http://10.24.2.14:30880/root/demo-2048.git
[root@master demo-2048]# git add .
[root@master demo-2048]# git commit -m "initial commit"
[master (root-commit) 105c032] initial commit
[root@master demo-2048]# git push -u origin drone
Username for 'http://10.24.2.14:30880': root
Password for 'http://root@10.24.2.14:30880': #输入密码Abc@1234
Counting objects: 189, done.
Delta compression using up to 8 threads.
Compressing objects: 100% (137/137), done.
Writing objects: 100% (189/189), 43.35 KiB | 0 bytes/s, done.
Total 189 (delta 40), reused 0 (delta 0)
remote: Resolving deltas: 100% (40/40), done.
To http://10.24.2.14:30880/root/cloud-manager.git
* [new branch] master -> master
Branch master set up to track remote branch master from origin.刷新页面如图5、图6所示:
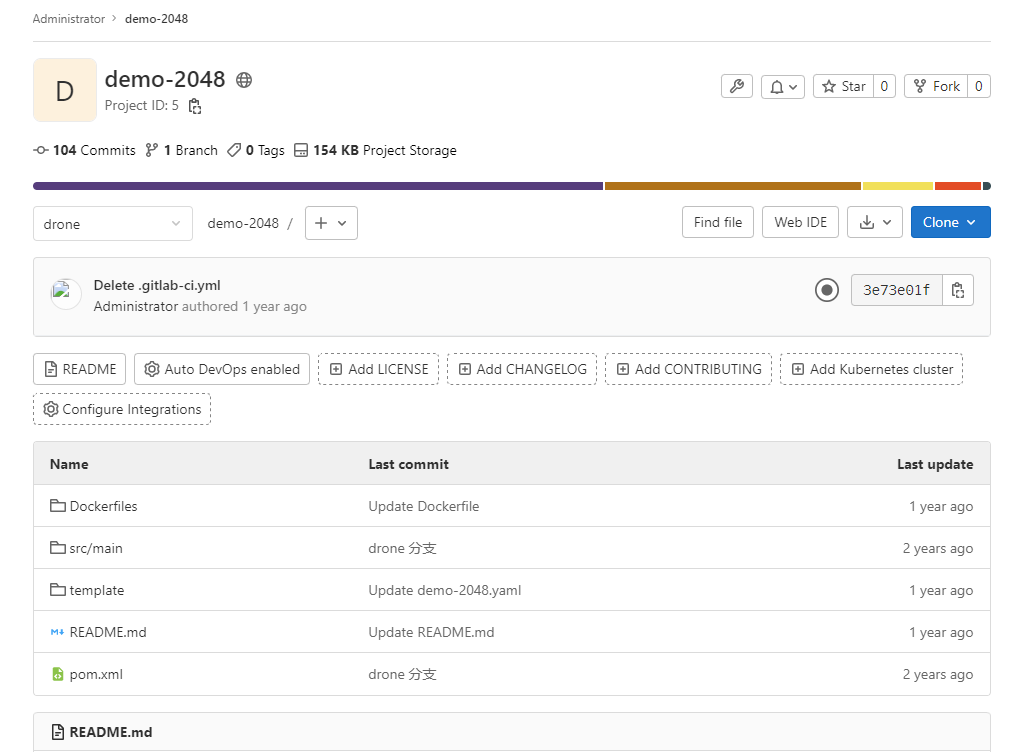
图5
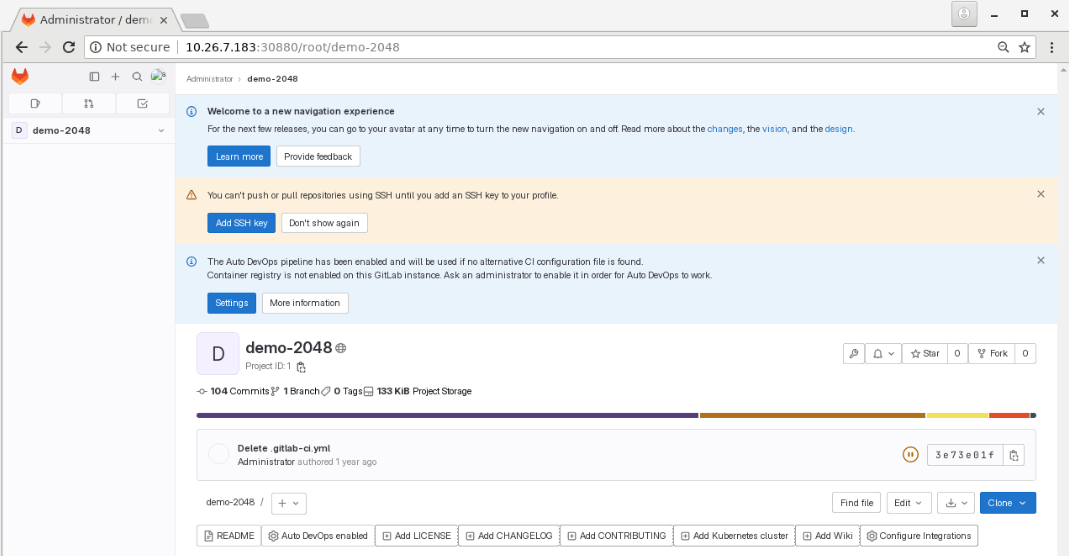
图6
2. 部署GitLab CI Runner
(1)获取 GitLab CI Register Token
登录GitLab管理界面(http://10.24.2.14:30880/admin),然后点击左侧菜单栏中的CI/CD下的Runners,如图7所示:
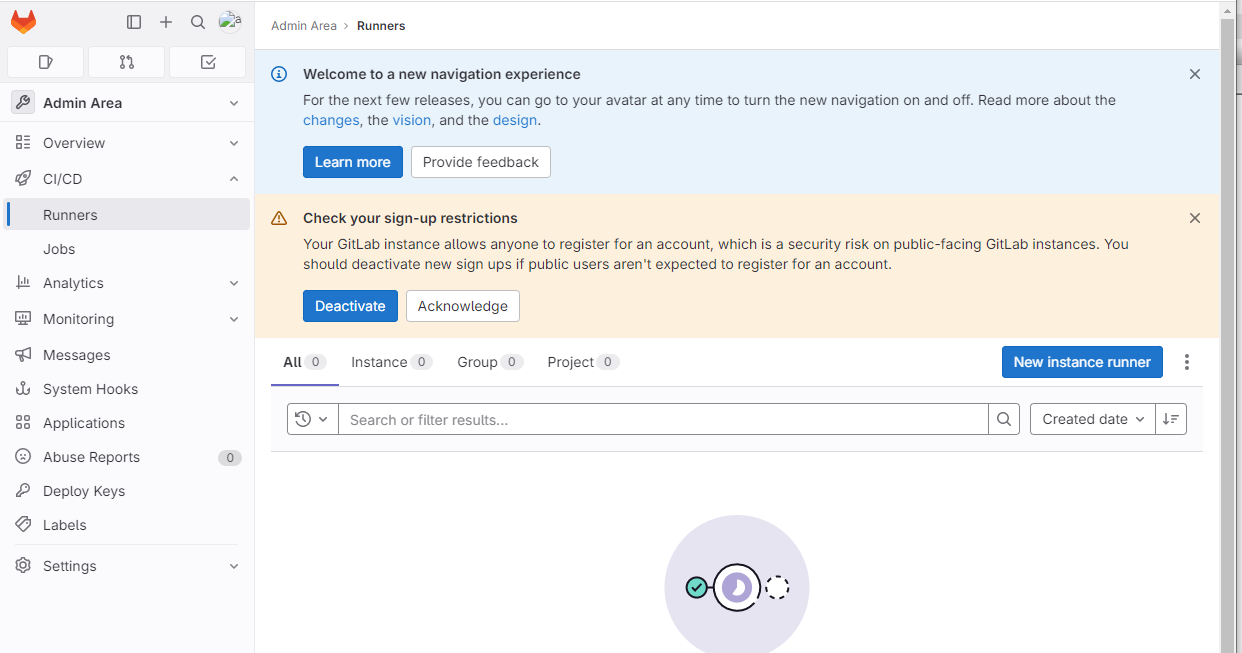
图7
点击右侧按钮,如图8所示:
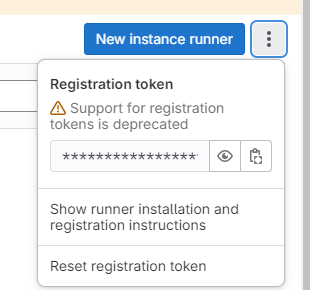
图8
记录下参数Registration token的值,后续注册Runners时会用到该参数。
(2)修改GitLab Runner配置清单
首先创建一个名为gitlab-ci的serviceAccount:
shell
[root@master ~]# cd /root/gitlab-ci/
[root@master gitlab-ci]# cat runner-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: gitlab-ci
namespace: gitlab-ci
[root@master gitlab-ci]# cat runner-role.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: gitlab-ci
namespace: gitlab-ci
rules:
- apiGroups: [""]
resources: ["*"]
verbs: ["*"]
[root@master gitlab-ci]# cat runner-rb.yaml
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: gitlab-ci
namespace: gitlab-ci
subjects:
- kind: ServiceAccount
name: gitlab-ci
namespace: gitlab-ci
roleRef:
kind: Role
name: gitlab-ci
apiGroup: rbac.authorization.k8s.io
[root@master gitlab-ci]# kubectl apply -f runner-sa.yaml
serviceaccount/gitlab-ci created
[root@master gitlab-ci]# kubectl apply -f runner-role.yaml
role.rbac.authorization.k8s.io/gitlab-ci created
[root@master gitlab-ci]# kubectl apply -f runner-rb.yaml
rolebinding.rbac.authorization.k8s.io/gitlab-ci created
[root@master gitlab-ci]# kubectl -n gitlab-ci get sa
NAME SECRETS AGE
default 1 10m
gitlab-ci 1 21s给default用户赋权:
shell
[root@master gitlab-ci]# vi default.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: default
labels:
k8s-app: gitlab-default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: default
namespace: gitlab-ci
[root@master gitlab-ci]# kubectl apply -f default.yaml
clusterrolebinding.rbac.authorization.k8s.io/default created修改values.yaml文件
shell
[root@master gitlab-ci]# tar -zxvf gitlab-runner-0.43.0.tgz
[root@master gitlab-ci]# vi gitlab-runner/values.yaml
...
## Use the following Kubernetes Service Account name if RBAC is disabled in this Helm chart (see rbac.create)
##
# serviceAccountName: default
serviceAccountName: gitlab-ci #添加,注意缩进格式
...
## The GitLab Server URL (with protocol) that want to register the runner against
## ref: https://docs.gitlab.com/runner/commands/index.html#gitlab-runner-register
##
# gitlabUrl: http://gitlab.your-domain.com/
gitlabUrl: http://10.24.2.14:30880/ #添加,缩进顶格
...
## The Registration Token for adding new Runners to the GitLab Server. This must
## be retrieved from your GitLab Instance.
## ref: https://docs.gitlab.com/ce/ci/runners/index.html
##
# runnerRegistrationToken: ""
runnerRegistrationToken: "riU8c4D2SNkKAv8GS9q_" #添加,缩进顶格
...
config: |
[[runners]]
[runners.kubernetes]
namespace = "{{.Release.Namespace}}"
image = "ubuntu:16.04"
privileged = true #添加,注意缩进格式
...
## For RBAC support:
rbac:
create: true #修改为true在进行maven/npm等构建工具打包时所依赖的包默认会从私服获取,为了加快构建速度可以在本地缓存一份,在此,需要创建PVC来持久化构建缓存,加速构建速度。为了节省存储空间决定不在每个项目中存储构建缓存,而是配置全局缓存。
创建一个PVC用于挂载到Pod中使用:
shell
[root@master gitlab-ci]# cat gitlab-runner/templates/pv.yaml
apiVersion: v1
kind: PersistentVolume
metadata:
name: ci-build-cache-pv
namespace: gitlab-ci
labels:
type: local
spec:
storageClassName: manual
capacity:
storage: 10Gi
accessModes:
- ReadWriteOnce
hostPath:
path: "/opt/ci-build-cache"
[root@master gitlab-ci]# cat gitlab-runner/templates/pvc.yaml
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: ci-build-cache-pvc
namespace: gitlab-ci
spec:
storageClassName: manual
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 5Gi编辑values.yaml文件,添加构建缓存信息配置:
shell
[root@master gitlab-ci]# vi gitlab-runner/values.yaml
## configure build cache
cibuild:
cache:
pvcName: ci-build-cache-pvc
mountPath: /home/gitlab-runner/ci-build-cache使用官方提供的runner镜像注册runner,默认的runner配置文件在/home/gitlab-runner/.gitlab-runner/config.toml。编辑templates/configmap.yml文件,entrypoint部分添加runner配置。在start之前添加,这样runner在创建构建Pod的时候会根据配置挂载PVC:
shell
[root@master gitlab-ci]# vi gitlab-runner/templates/configmap.yaml
cat >>/home/gitlab-runner/.gitlab-runner/config.toml <<EOF
[[runners.kubernetes.volumes.pvc]]
name = "{{.Values.cibuild.cache.pvcName}}"
mount_path = "{{.Values.cibuild.cache.mountPath}}"
EOF
# Start the runner
exec /entrypoint run --user=gitlab-runner \
--working-directory=/home/gitlab-runner
shell
### 注意缩进
cat >>/home/gitlab-runner/.gitlab-runner/config.toml <<EOF
[[runners.kubernetes.volumes.pvc]]
name = "{{.Values.cibuild.cache.pvcName}}"
mount_path = "{{.Values.cibuild.cache.mountPath}}"
EOF
# Start the runner
exec /entrypoint run --user=gitlab-runner \
--working-directory=/home/gitlab-runner(3)部署GitLab Runner
部署GitLab Runner:
shell
[root@master gitlab-ci]# helm -n gitlab-ci install gitlab-runner gitlab-runner
NAME: gitlab-runner
LAST DEPLOYED: Wed Jul 27 11:17:11 2022
NAMESPACE: gitlab-ci
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
Your GitLab Runner should now be registered against the GitLab instance reachable at: "http://10.24.2.14:30880/"
Runner namespace "gitlab-ci" was found in runners.config template.查看Realse和Pod:
shell
[root@master gitlab-ci]# helm -n gitlab-ci list
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
gitlab-runner gitlab-ci 1 2022-07-27 11:17:11.456495093 +0800 CST deployed gitlab-runner-0.43.0 15.2.0
[root@master gitlab-ci]# kubectl -n gitlab-ci get pods
NAME READY STATUS RESTARTS AGE
gitlab-7b54df755-6ljtp 1/1 Running 0 30m
gitlab-runner-5bc5578655-2ct85 1/1 Running 0 58s返回Runners页面并刷新,如图9所示:
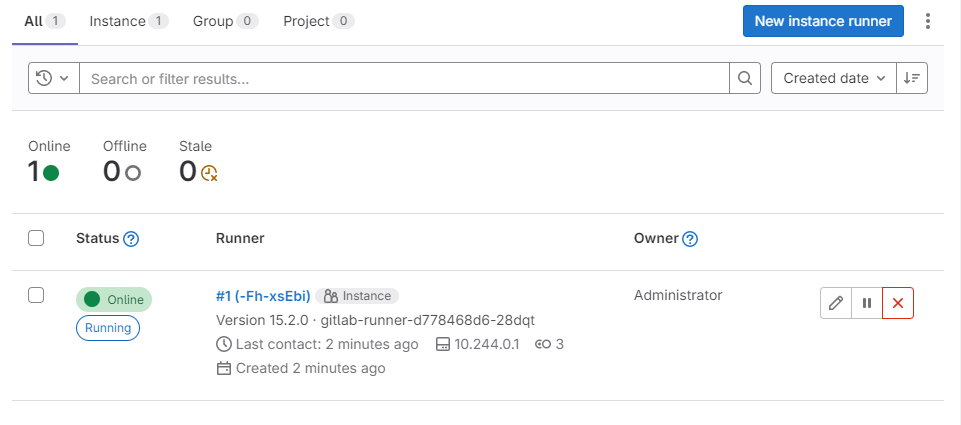
图9
可以看到Runner状态为online,表明已经注册成功。
3. 配置GitLab
(1)添加Kubernetes集群
在GitLab Admin界面下,依次点击"Settings"→"Network",展开"Outbound requests",勾选"Allow requests to the local network from webhooks and integrations",并保存。如图10所示:
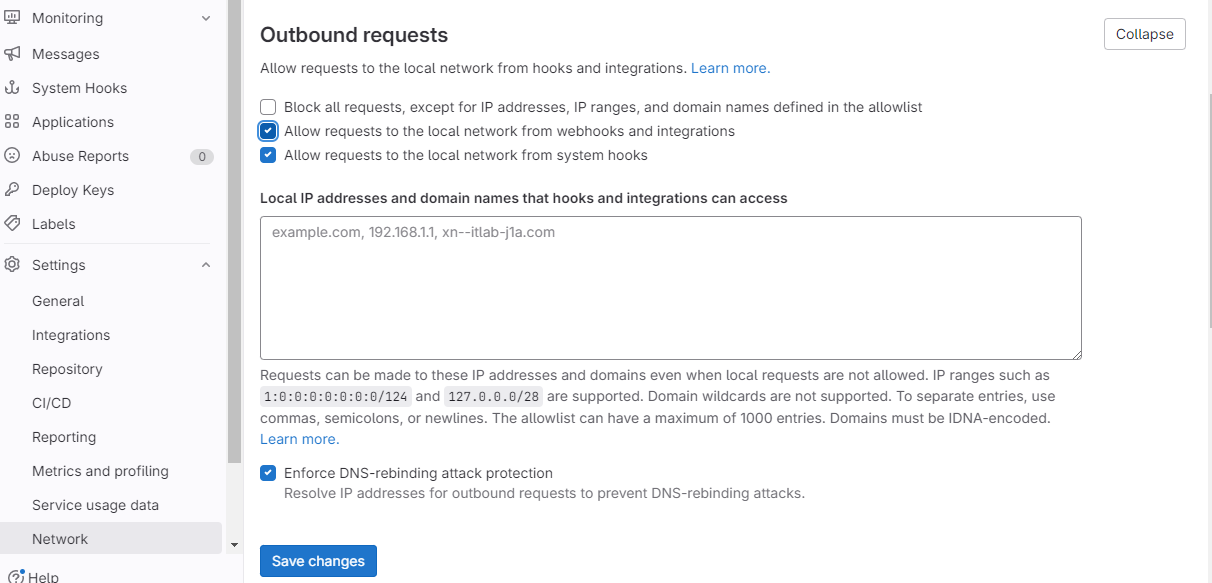
图10
进入demo-2048项目,新建配置文件(.gitlab/agents//config.yaml),此处为.gitlab/agents/kubernetes-agent/config.yaml,如图11所示:
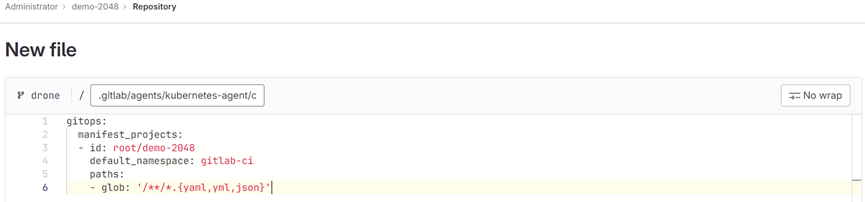
图11
config.yaml文件格式如下:
shell
gitops:
manifest_projects:
- id: gitlab-org/cluster-integration/gitlab-agent
default_namespace: my-ns
paths:
# Read all YAML files from this directory.
- glob: '/team1/app1/*.yaml'
# Read all .yaml files from team2/apps and all subdirectories.
- glob: '/team2/apps/**/*.yaml'
# If 'paths' is not specified or is an empty list, the configuration below is used.
- glob: '/**/*.{yaml,yml,json}'
reconcile_timeout: 3600s
dry_run_strategy: none
prune: true
prune_timeout: 3600s
prune_propagation_policy: foreground
inventory_policy: must_match依次点击左侧菜单栏"Operate"→"Kubernetes clusters",如图12所示:
图12
点击"Connect a cluster",并选择配置文件kubernetes-agent,如图13所示:
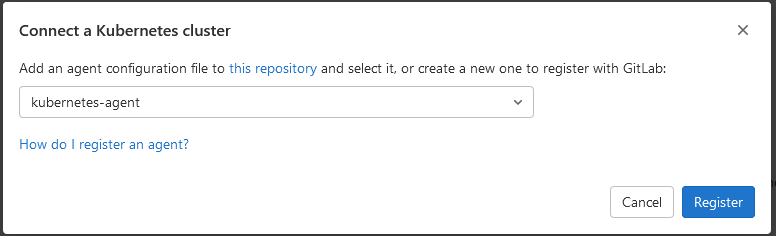
图13
点击"Register",如图14所示:
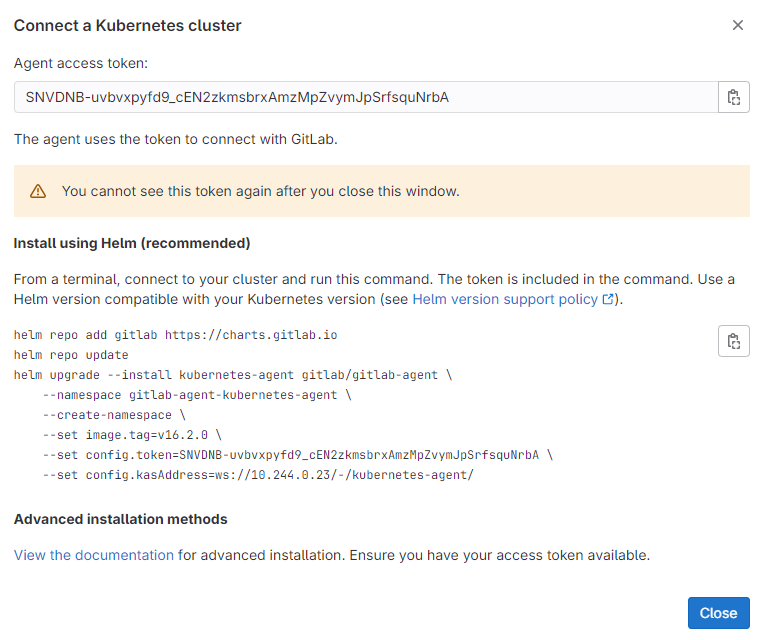
图14
通过如下命令安装agent,将config.token和config.kasAddress的值修改为上一步页面显示的值:
shell
[root@master gitlab-ci]# helm upgrade --install kubernetes-agent gitlab-agent-1.1.0.tgz --namespace gitlab-ci --create-namespace --set image.tag=v16.2.0 --set config.token=vTPAASMpwTW-tEQ3NHYc3y5YKCHCFep466q52dgaRCstXyXDzg --set config.kasAddress=ws://10.244.0.23/-/kubernetes-agent/
NAME: kubernetes-agent
LAST DEPLOYED: Wed Jul 13 17:27:21 2022
NAMESPACE: gitlab-ci
STATUS: deployed
REVISION: 1
TEST SUITE: None
shell
[root@master gitlab-ci]# helm upgrade --install kubernetes-agent gitlab-agent-1.1.0.tgz
--namespace gitlab-ci
--create-namespace
--set image.tag=v16.2.0
--set config.token=vTPAASMpwTW-tEQ3NHYc3y5YKCHCFep466q52dgaRCstXyXDzg
--set config.kasAddress=ws://10.244.0.23/-/kubernetes-agent/
NAME: kubernetes-agent
LAST DEPLOYED: Wed Jul 13 17:27:21 2022
NAMESPACE: gitlab-ci
STATUS: deployed
REVISION: 1
TEST SUITE: None
helm repo add gitlab https://charts.gitlab.io
helm repo update
helm upgrade --install kubernetes-agent gitlab-agent-1.1.0.tgz \
--namespace gitlab-ci \
--create-namespace \
--set image.tag=v16.2.0 \
--set config.token=NgYd7JkZN4T1dcWpx9PCsTC3FgVx3MQAycyXQArAGukxn_ymwA \
--set config.kasAddress=ws://192.168.100.3:30880/-/kubernetes-agent/
helm install kubernetes-agent gitlab-agent-1.1.0.tgz \
--namespace gitlab-ci \
--create-namespace \
--set image.tag=v16.2.0 \
--set config.token=NgYd7JkZN4T1dcWpx9PCsTC3FgVx3MQAycyXQArAGukxn_ymwA \
--set config.kasAddress=ws://192.168.100.3:30880/-/kubernetes-agent/查看Release和Pod:
shell
[root@ k8s-master-node1 gitlab-ci]# helm -n gitlab-ci list
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
gitlab-runner gitlab-ci 1 2022-07-27 11:17:11.456495093 +0800 CST deployed gitlab-runner-0.43.0 15.2.0
kubernetes-agent gitlab-ci 1 2022-07-27 11:22:27.285028745 +0800 CST deployed gitlab-agent-1.1.0 v15.0.0
[root@master gitlab-ci]# kubectl get pod -n gitlab-ci
NAME READY STATUS RESTARTS AGE
gitlab-7665cf47c5-8ghbw 1/1 Running 1 (89m ago) 96m
gitlab-runner-665f4647b9-zhrlh 1/1 Running 0 18m
kubernetes-agent-gitlab-agent-6df7787756-b4rzx 1/1 Running 0 14s点击"Close"并刷新界面,如图15所示:
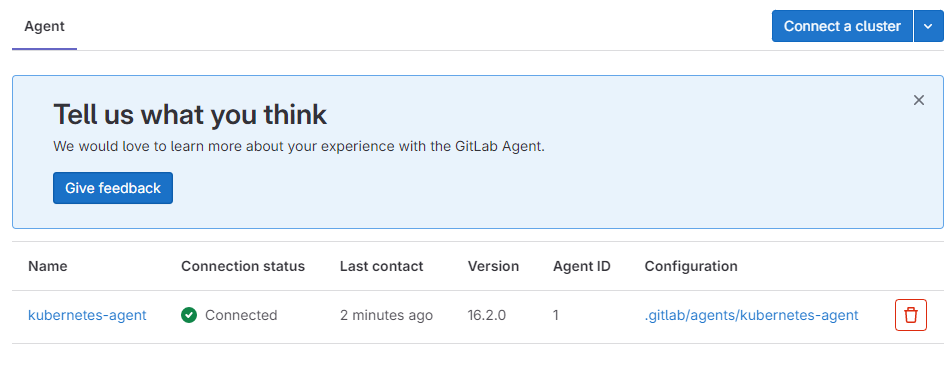
图15
可以看到,Kubernetes集群已连接成功。
(2)开启Container Registry
在GitLab中开启Container Registry,进入demo-2048项目,依次点击"Settings"→"CI/CD",如图16所示:
图16
展开"Variables",配置镜像仓库相关的参数。
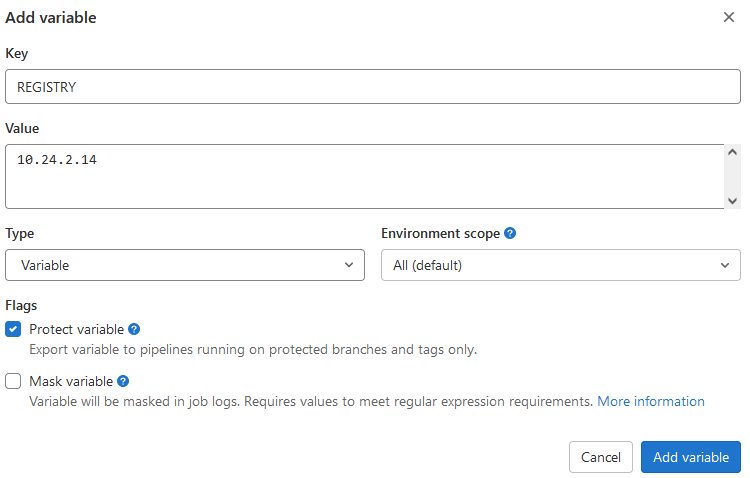
添加REGISTRY变量,其值为Harbor仓库地址,如图17所示:
17图
添加完成后如图18所示:
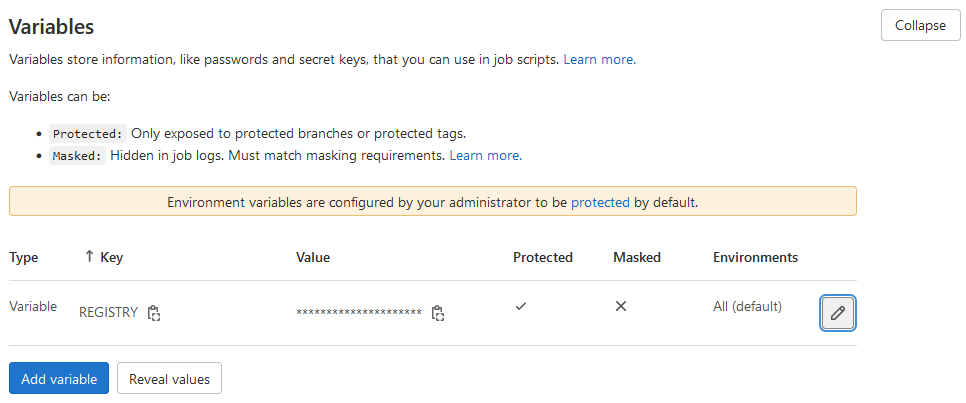
图18
然后继续添加变量REGISTRY_IMAGE(demo)、REGISTRY_USER(admin)、REGISTRY_PASSWORD(Harbor12345)、REGISTRY_PROJECT(demo)和HOST(10.24.2.14),添加完成后保存变量,如图19所示:
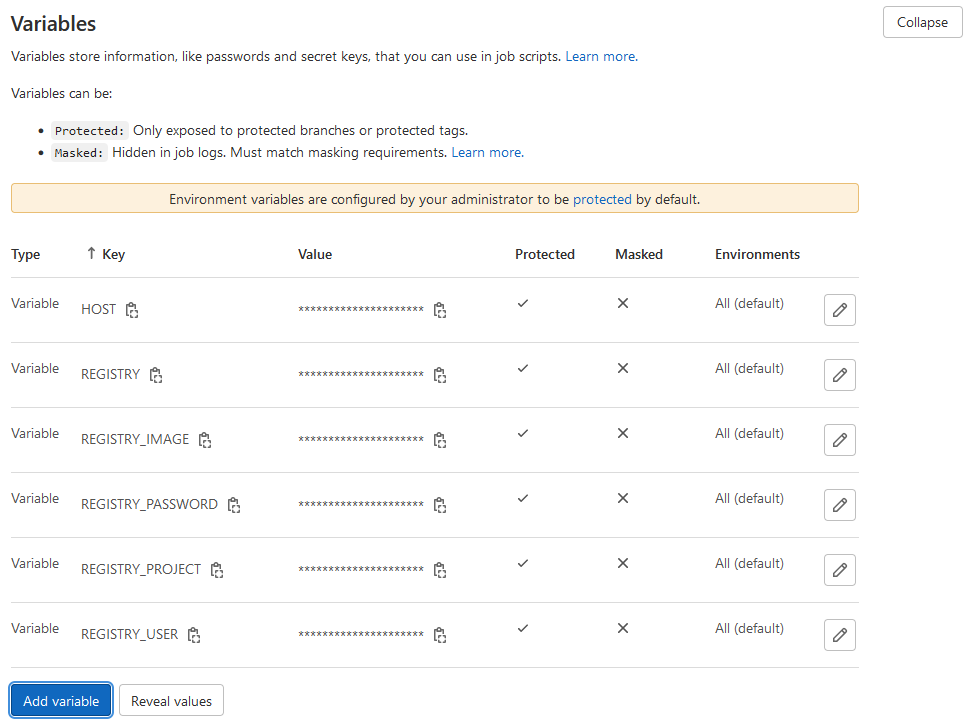
图19
4. Harbor仓库配置
(1)更新Harbor仓库
修改harbor仓库的helm配置:
shell
[root@master ~]# vi /opt/harbor/values.yaml
...
#将127.0.0.1改为master节点实际IP地址
externalURL: http://10.26.7.197:80
...修改完成后,更新harbor仓库:
shell
[root@master ~]# helm -n harbor upgrade harbor /opt/harbor(2)添加demo仓库
登录Harbor仓库新建一个公开项目demo,如图20所示:
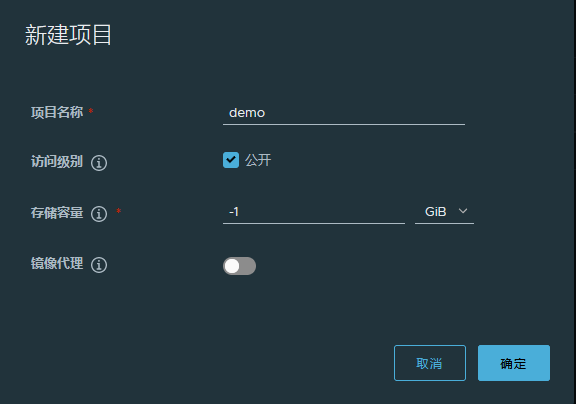
图20
将镜像tomcat:8.5.64-jdk8推送到该项目中:
shell
[root@master gitlab-ci]# ctr -n k8s.io images tag docker.io/library/tomcat:8.5.64-jdk8 10.24.2.14/library/tomcat:8.5.64-jdk8
[root@master gitlab-ci]# ctr -n k8s.io images push 10.24.2.14/library/tomcat:8.5.64-jdk8 --plain-http=true --user admin:Harbor12345 修改containerd配置文件
shell
[root@master ~]# vi /etc/containerd/config.toml
•••
[plugins."io.containerd.grpc.v1.cri".registry.mirrors]
[plugins."io.containerd.grpc.v1.cri".registry.mirrors."harbor.com"]
endpoint = ["http://harbor.com"]
[plugins."io.containerd.grpc.v1.cri".registry.mirrors."10.24.2.14"]
endpoint = ["http://10.24.2.14"]
[root@master ~]# systemctl daemon-reload
[root@master ~]# systemctl restart containerd5. .gitlab-ci.yaml文件
(1).gitlab-ci.yaml文件简介
GitLab CI通过YAML文件管理配置job,定义了job应该如何工作。该文件存放于仓库的根目录,默认名为.gitlab-ci.yaml。
- gitlab-ci.yml文件中指定了CI的触发条件、工作内容、工作流程,编写和理解此文件是CI实战中最重要的一步,该文件指定的任务内容总体构成了1个pipeline、1个pipeline包含不同的stage执行阶段、每个stage包含不同的具体job脚本任务。
当有新内容push到仓库,或者有代码合并后,GitLab会查找是否有.gitlab-ci.yml文件,如果文件存在,Runners将会根据该文件的内容开始build本次commit。
(2)Pipeline
一个.gitlab-ci.yml文件触发后会形成一个pipeline任务流,由gitlab-runner来运行处理。一次Pipeline其实相当于一次构建任务,里面可以包含很多个阶段(Stages),如安装依赖、运行测试、编译、部署测试服务器、部署生产服务器等流程。任何提交或者Merge Request的合并都可以触发Pipeline构建。
(3)Stages
Stages表示一个构建阶段,也就是上面提到的一个流程。我们可以在一次Pipeline中定义多个Stages,这些Stages会有以下特点:
- 所有Stages会按照顺序运行,即当一个Stage完成后,下一个Stage才会开始
- 只有当所有Stages完成后,该构建任务(Pipeline)才会成功
- 如果任何一个Stage失败,那么后面的Stages不会执行,该构建任务(Pipeline)失败
(4)Jobs
Jobs表示构建工作,表示某个Stage里面执行的工作。我们可以在Stages里面定义多个Jobs,这些Jobs会有以下特点:
- 相同Stage中的Jobs会并行执行
- 相同Stage中的Jobs都执行成功时,该Stage才会成功
- 如果任何一个Job失败,那么该Stage失败,即该构建任务(Pipeline)失败
一个Job被定义为一列参数,这些参数指定了Job的行为。下表列出了主要的Job参数,见表2:
表2
| 参数 | 是否必须 | 描述 |
|---|---|---|
| script | 是 | 由Runner执行的shell脚本或命令 |
| image | 否 | 用于docker镜像 |
| services | 否 | 用于docker服务 |
| stages | 否 | 定义构建阶段 |
| types | 否 | stages 的别名(已废除) |
| before_script | 否 | 定义在每个job之前运行的命令 |
| after_script | 否 | 定义在每个job之后运行的命令 |
| variable | 否 | 定义构建变量 |
| cache | 否 | 定义一组文件列表,可在后续运行中使用 |
(5)编写流水线脚本
编写.gitlab-ci.yml:
shell
stages:
- build
- release
- review
variables:
MAVEN_OPTS: "-Dmaven.repo.local=/opt/cache/.m2/repository"
maven_build:
image: maven:3.6-jdk-8
stage: build
only:
- drone
script:
- cp -r /opt/repository /opt/cache/.m2/
- mvn clean install -DskipTests=true
- cd target && jar -xf 2048.war
- cp -rfv 2048 /home/gitlab-runner/ci-build-cache
image_build:
image: docker:18.09.7
stage: release
variables:
DOCKER_DRIVER: overlay
DOCKER_HOST: tcp://localhost:2375
#CI_DEBUG_TRACE: "true"
services:
- name: docker:18.09.7-dind
command: ["--insecure-registry=0.0.0.0/0"]
script:
- cp -rfv /home/gitlab-runner/ci-build-cache/2048 .
- sed -i "s/10.24.2.3/$REGISTRY/g" ./Dockerfiles/Dockerfile
- docker build -t "${REGISTRY_IMAGE}:latest" -f ./Dockerfiles/Dockerfile .
- docker tag "${REGISTRY_IMAGE}:latest" "${REGISTRY}/${REGISTRY_PROJECT}/${REGISTRY_IMAGE}:latest"
- docker login -u "${REGISTRY_USER}" -p "${REGISTRY_PASSWORD}" "${REGISTRY}"
- docker push "${REGISTRY}/${REGISTRY_PROJECT}/${REGISTRY_IMAGE}:latest"
deploy_review:
image: kubectl:1.22
stage: review
only:
- drone
script:
- sed -i "s/REGISTRY/$REGISTRY/g" template/demo-2048.yaml
- kubectl apply -f template/6. 构建CICD
(1)触发构建
流水线脚本编写完成后会自动触发构建,进入demo-2048项目,依次点击"build"→"Pipelines",可以看到GitLab CI开始执行构建任务了,如图21所示:
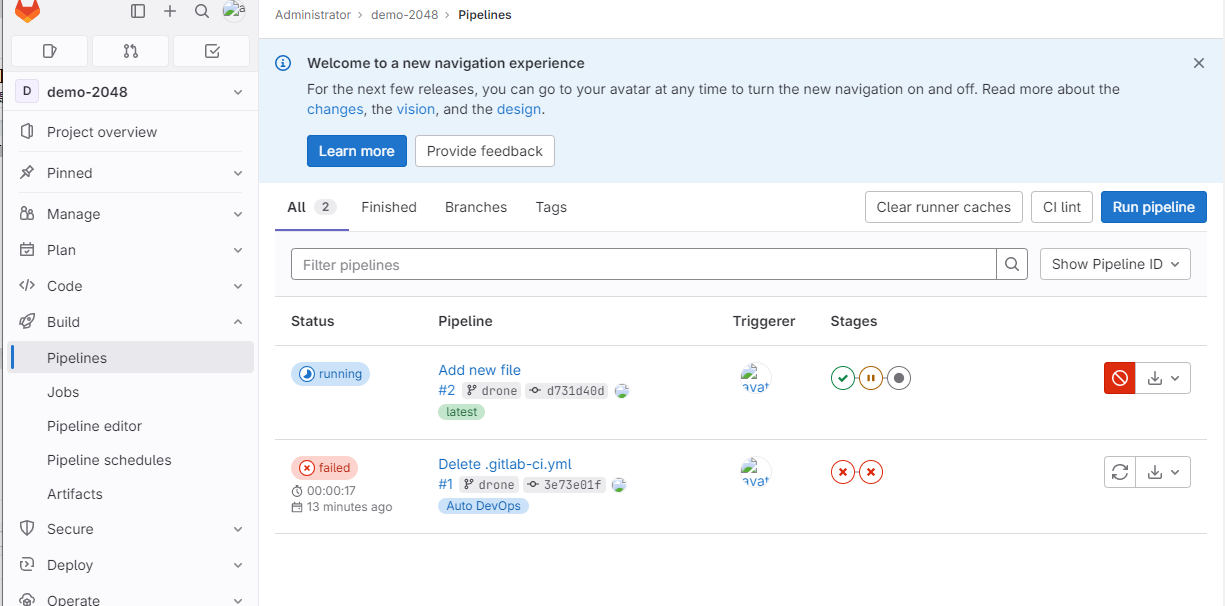
图21
点击"running"可查看构建详情,如图22所示:
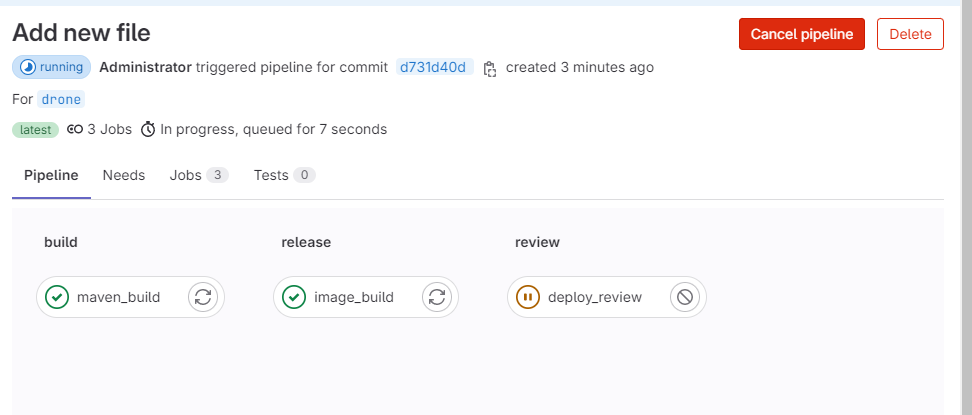
图22
点击流水线的任一阶段可查看构建详情,如图23所示:
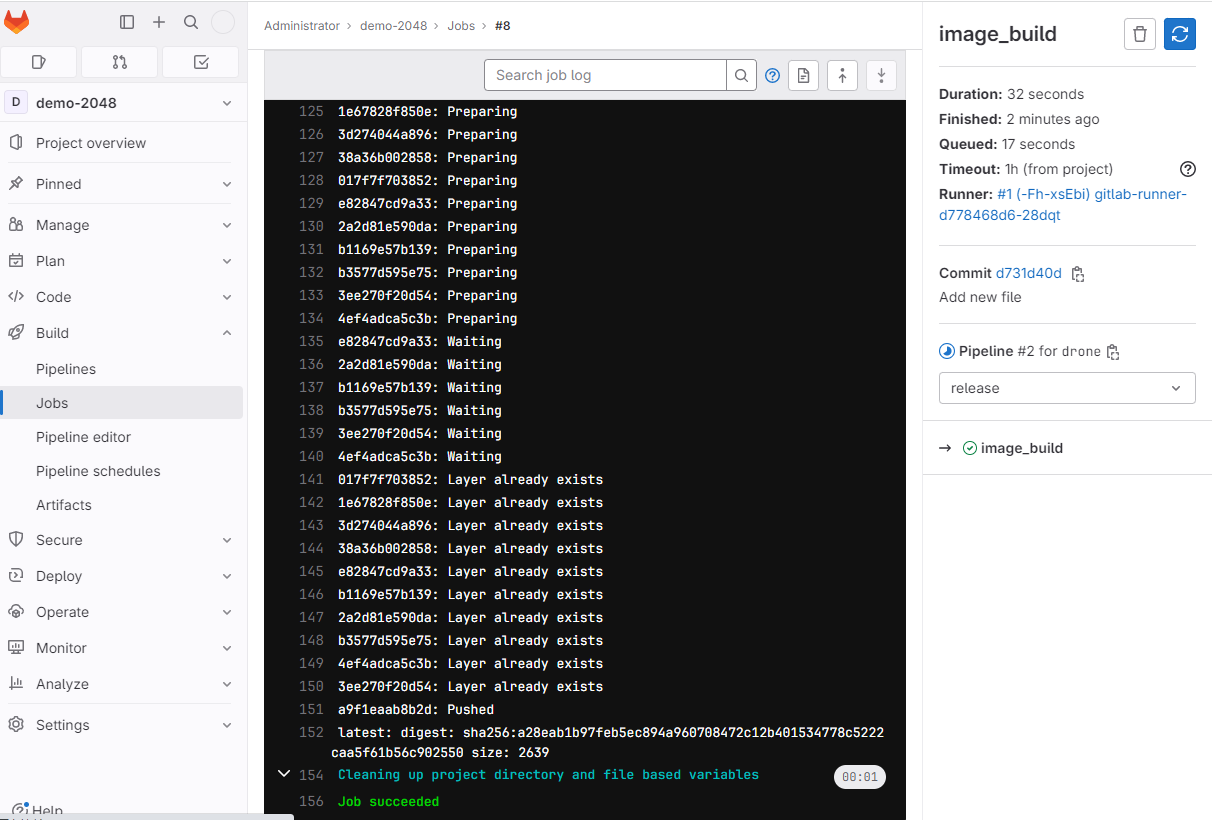
图23
此时Runner Pod所在的namespace下面也会出现1个新的Pod:
shell
[root@master gpmall]# kubectl -n gitlab-ci get pods
NAME READY STATUS RESTARTS AGE
gitlab-7b54df755-6ljtp 1/1 Running 0 3h6m
gitlab-runner-5dc59b5b77-x2vw8 1/1 Running 0 129m
kubernetes-agent-gitlab-agent-64bf6d87f4-vgxbx 1/1 Running 0 151m
runner-x16szo9v-project-2-concurrent-0jzq5h 2/2 Running 0 8s这个新Pod就是用来执行具体的Job任务的。
构建完成后如图24所示:
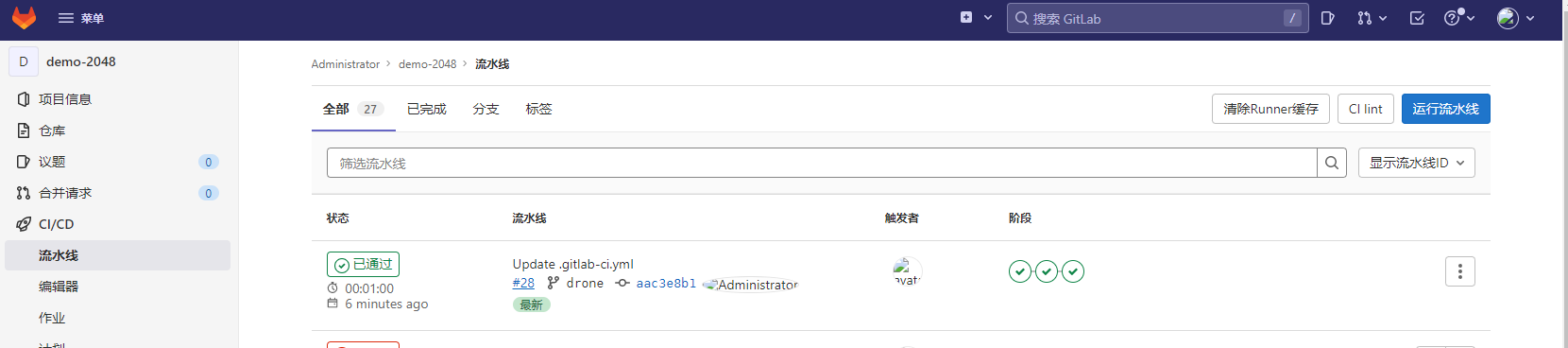
图24
查看新发布的Pod:
shell
[root@master manifests]# kubectl -n gitlab-ci get pods
NAME READY STATUS RESTARTS AGE
demo-2048-6bf767d4d4-kks65 1/1 Running 0 2m22s
gitlab-7b54df755-6ljtp 1/1 Running 0 3h8m
gitlab-runner-5dc59b5b77-x2vw8 1/1 Running 0 132m
kubernetes-agent-gitlab-agent-64bf6d87f4-vgxbx 1/1 Running 0 153m(2)查看Harbor
登录Harbor仓库,进入demo项目,如图25所示:
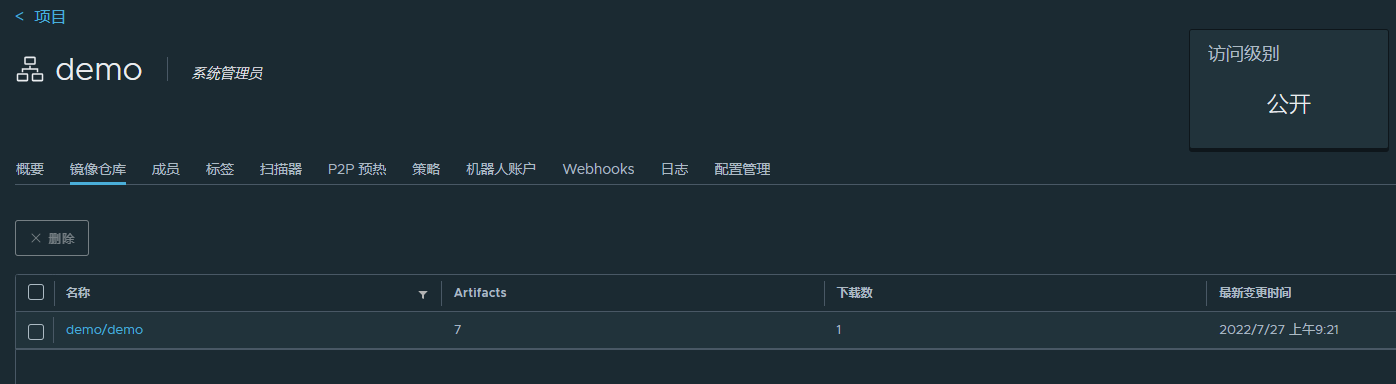
图25
可以看到镜像已构建并上传成功。
(3)验证服务
查看Service:
shell
[root@master gitlab-ci]# kubectl -n gitlab-ci get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
demo-2048 NodePort 10.96.222.104 <none> 8080:8889/TCP 3m14s访问Service,如图26所示:
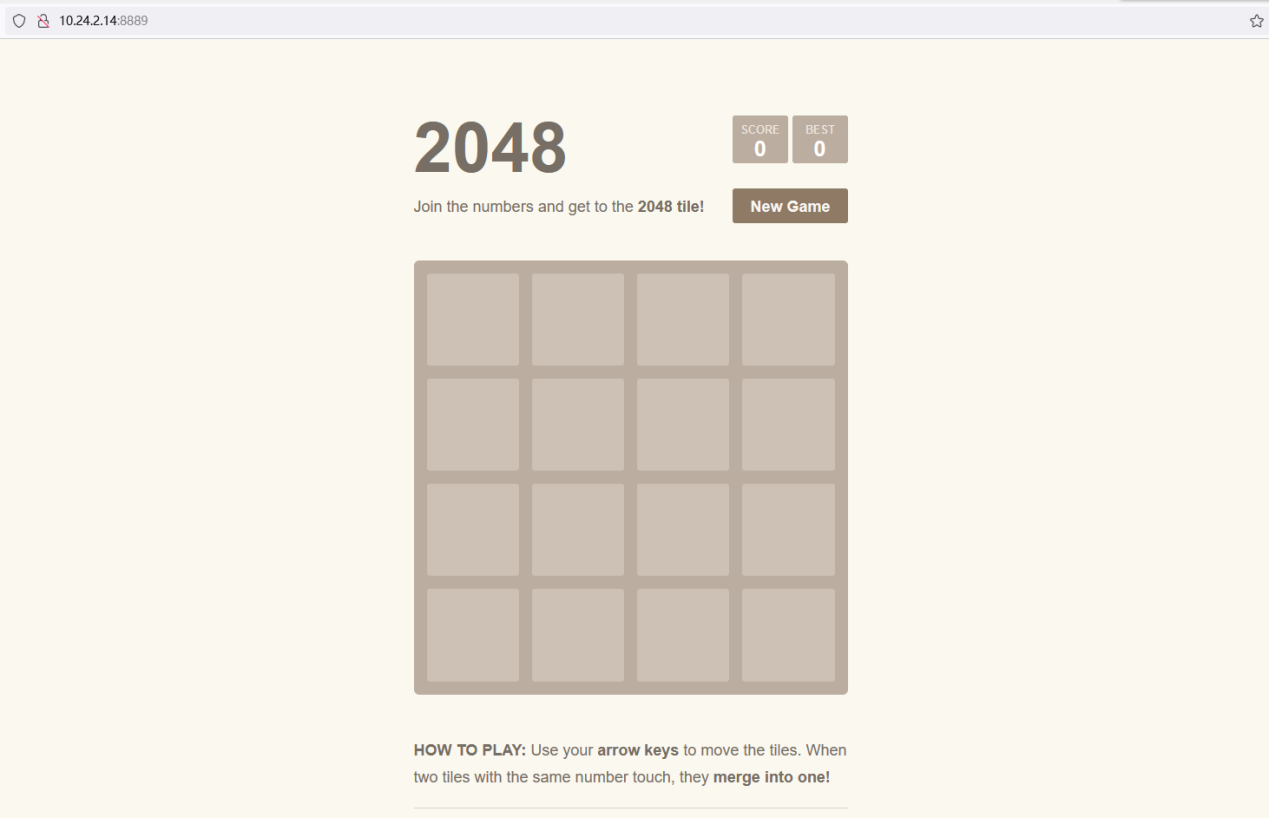
图26