此环境需要K8S最好是安装好了StorageClass,Helm,Ingress组件...
一、Helm部署Harbor
1.1 创建资源隔离的名称空间
bash
[root@k8s-master ~]# kubectl create ns harbor
[root@k8s-master ~]# kubectl get ns harbor
NAME STATUS AGE
harbor Active 38m1.2 添加Helm repo仓库
bash
[root@k8s-master ~]# helm repo add harbor https://helm.goharbor.io
[root@k8s-master ~]# helm repo ls
NAME URL
bitnami https://helm-charts.itboon.top/bitnami
ingress https://kubernetes.github.io/ingress-nginx
harbor https://helm.goharbor.io 1.3 拉取Harbor仓库的Chart包
bash
[root@k8s-master ~]# helm pull harbor/harbor
[root@k8s-master ~]# tar zxvf harbor-1.18.1.tgz
[root@k8s-master ~]# cd harbor/
[root@k8s-master ~/harbor]# ls
Chart.yaml LICENSE README.md templates values.yaml1.4 修改harborChart包的values配置
因为我这里使用了测试环境去部署这个Harbor所有一切按照测试环境来配置,例如存储大小以及URL地址。
关于这个URL地址,如果有真实的URL域名可以在values中将默认的core.harbor.domain的配置都替换为自己的真实域名即可。
bash
# 修改存储类,做持久化存储,我这里的是有一个部署好的动态存储NFS的类。
[root@k8s-master ~/harbor]# kubectl get sc
NAME PROVISIONER RECLAIMPOLICY VOLUMEBINDINGMODE ALLOWVOLUMEEXPANSION AGE
nfs-csi nfs.csi.k8s.io Delete Immediate true 2d
# 所以这里的持久化存储和后端的存储大小必须要按照自己的环境去修改。
[root@k8s-master ~/harbor]# grep -i 'storageclass' values.yaml
# The persistence is enabled by default and a default StorageClass
# Specify another StorageClass in the "storageClass" or set "existingClaim"
# Specify the "storageClass" used to provision the volume. Or the default
# StorageClass will be used (the default).
storageClass: "nfs-csi"
storageClass: "nfs-csi"
storageClass: "nfs-csi"
storageClass: "nfs-csi"
storageClass: "nfs-csi"
# 因为网络的原因,将镜像漏扫的Trivy漏洞库下载缓慢,所以这里就不开启更新了,后面我们可以手动配置这个漏洞库
[root@k8s-master ~/harbor]# grep -i 'skipUpdate' values.yaml
# skipUpdate the flag to disable Trivy DB downloads from GitHub
skipUpdate: true
# This option doesn't affect DB download. You need to specify skipUpdate as well as offlineScan in an air-gapped environment.
# 当然如果网络环境好的情况下,这个跳过配置可以关闭。1.5 安装Harbor
bash
[root@k8s-master ~/harbor]# helm install harbor . -f values.yaml -n harbor
[root@k8s-master ~/harbor]# kubectl -n harbor get po,svc,ingress,pv
NAME READY STATUS RESTARTS AGE
pod/harbor-core-7f44b67745-rzxsx 1/1 Running 0 14m
pod/harbor-database-0 1/1 Running 0 14m
pod/harbor-jobservice-57f8bd94bf-h6hgh 1/1 Running 2 (14m ago) 14m
pod/harbor-portal-5c8bf9b699-k8tzn 1/1 Running 0 14m
pod/harbor-redis-0 1/1 Running 0 14m
pod/harbor-registry-7c85656ff5-k9b8k 2/2 Running 0 14m
pod/harbor-trivy-0 1/1 Running 0 14m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/harbor-core ClusterIP 10.104.82.202 <none> 80/TCP 14m
service/harbor-database ClusterIP 10.106.164.167 <none> 5432/TCP 14m
service/harbor-jobservice ClusterIP 10.110.104.188 <none> 80/TCP 14m
service/harbor-portal ClusterIP 10.98.240.32 <none> 80/TCP 14m
service/harbor-redis ClusterIP 10.104.117.255 <none> 6379/TCP 14m
service/harbor-registry ClusterIP 10.109.120.134 <none> 5000/TCP,8080/TCP 14m
service/harbor-trivy ClusterIP 10.105.75.0 <none> 8080/TCP 14m
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress.networking.k8s.io/harbor-ingress nginx core.harbor.domain 10.0.0.150 80, 443 14m
NAME CAPACITY ACCESS MODES RECLAIM POLICY STATUS CLAIM STORAGECLASS VOLUMEATTRIBUTESCLASS REASON AGE
persistentvolume/pvc-0a1839d9-cc5d-4115-a257-5d1997d06214 1Gi RWO Delete Bound harbor/harbor-jobservice nfs-csi <unset> 44m
persistentvolume/pvc-5b9ee196-aec6-463b-b022-61db26f7123f 1Gi RWO Delete Bound harbor/data-harbor-redis-0 nfs-csi <unset> 44m
persistentvolume/pvc-9386cd02-ee67-44a9-82a5-e87d8c6d8321 5Gi RWO Delete Bound harbor/harbor-registry nfs-csi <unset> 44m
persistentvolume/pvc-cb73721f-465b-45f8-b608-7717a4ae828e 1Gi RWO Delete Bound harbor/database-data-harbor-database-0 nfs-csi <unset> 44m
persistentvolume/pvc-ec6ce660-3866-494d-b7b7-f26f1ab0c66f 5Gi RWO Delete Bound harbor/data-harbor-trivy-0 nfs-csi <unset> 44m1.6 浏览器访问Harbor
这里的访问可以将地址修改为公司或者自己的域名,如果没有域名只是测试,可以修改Windows的hosts解析文件,将解析记录添加完成之后浏览器访问对于的域名即可。
用户名:admin
密 码:Harbor12345
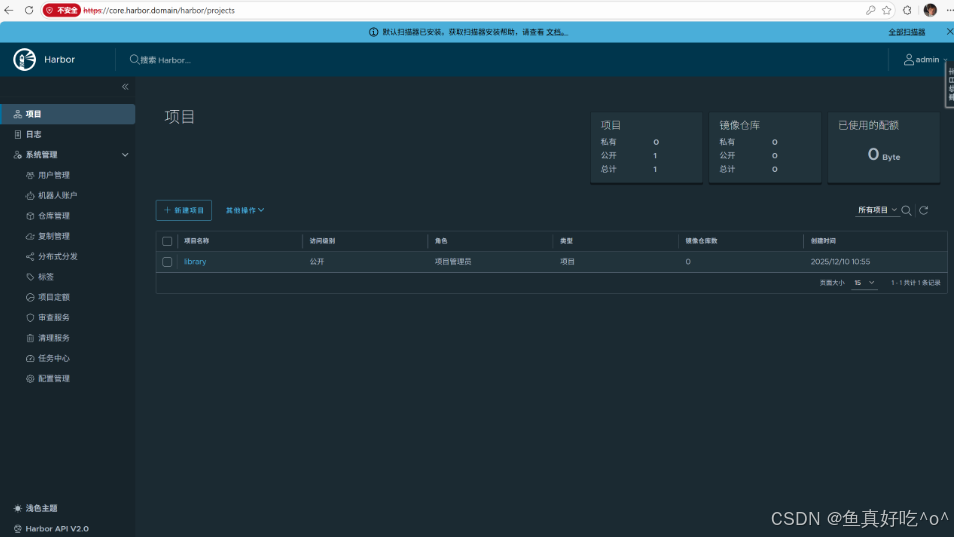
二、容器运行时接入Harbor仓库
2.1 查看自己的容器运行时,配置认证证书
bash
[root@k8s-master ~/harbor]# kubectl get nodes -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
k8s-master Ready control-plane 37d v1.32.9 10.0.0.6 <none> Ubuntu 25.10 6.17.0-6-generic containerd://2.1.3
k8s-node1 Ready <none> 37d v1.32.9 10.0.0.7 <none> Ubuntu 25.10 6.17.0-7-generic containerd://2.1.3
k8s-node2 Ready <none> 37d v1.32.9 10.0.0.8 <none> Ubuntu 25.10 6.17.0-6-generic containerd://2.1.3
# 可以看到我这里时containerd的运行时2.2 查看harbor的根证书
bash
[root@k8s-master ~/harbor]# kubectl get secret harbor-ingress -n harbor -o yaml
apiVersion: v1
data:
ca.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURFekNDQWZ1Z0F3SUJBZ0lRTXlmTVRIc2Y3TEloYndDb0JIODZhREFOQmdrcWhraUc5dzBCQVFzRkFEQVUKTVJJd0VBWURWUVFERXdsb1lYSmliM0l0WTJFd0hoY05NalV4TWpFd01ETXdNalU0V2hjTk1qWXhNakV3TURNdwpNalU0V2pBVU1SSXdFQVlEVlFRREV3bG9ZWEppYjNJdFkyRXdnZ0VpTUEwR0NTcUdTSWIzRFFFQkFRVUFBNElCCkR3QXdnZ0VLQW9JQkFRQ3h5ZXE2c0ZkaS9ZOUlvblluU1FLMXRNZUNUbmMrMXFhWDlmRnh0SFZnQ2J2SGFBMW4Kc2VzYUpFaDdxOGVYUHRLRzZxZ1A4bUNLSVNZbWNzTnhiVk95WHNJdTQrcW5odEpPYTlZaE5WM2N6eEdLVnoxUQpMY1pBSURtUUYyakhDbm42ckpPeU5PZXQwMzdJUUlHeVFMNXg3eWljUnNFTkM3YXFFVUpFS1Q1NUVLTEpTcFI4ClcxN0ZsdVdkdHB0NmgvTm51dVlGanZOLzBwbmsrTEcvazlWYzdud0p3Z2h4LzIwalN4R3JrYitBdGd1Vi9UUnYKVFh5ZVlnVTRIWU5sUjNZOWZCVzFhb3FWcHFuQTJ6Q21Benk4Z1Z3RHlVNi92VWluTXAySnBERXMvVGNXMm4yagptaGpRWVF6OGhWa3k5d2laM2JKNThrWldqUmNUUXBIZnorSXRBZ01CQUFHallUQmZNQTRHQTFVZER3RUIvd1FFCkF3SUNwREFkQmdOVkhTVUVGakFVQmdnckJnRUZCUWNEQVFZSUt3WUJCUVVIQXdJd0R3WURWUjBUQVFIL0JBVXcKQXdFQi96QWRCZ05WSFE0RUZnUVVFZG9rb0o0dkpVUTZaK01WS2NrcWk5eWRtVUl3RFFZSktvWklodmNOQVFFTApCUUFEZ2dFQkFGekRlVVhkVzk4cG5uWUR4UDdOMFRWY3BKZXQzcWYveXZtUlZRdnJMM3RYVk80WU1pdUxCVkQwCnorKzIwMVZRMmZSREMvaTI1S3lBQ1VxWWdUdUY3dmlQUForV0lZTitpZzJWakxWVnVZZjI2M0hZSlRNUjlhVkEKMlp0UXJoZ0d0cUV1L1JYOE00R1VDbEplb3JDVUpDQUlYc1FMbW1kd3JnVzJEZ05KL0EzcUhXY2FIOEttdE1JSApmUXpyVi9ULzdjMWtsL1ZrZjkxOUVCcU5KSU9JOUQvRmFCZ3pzbnpUd0pLb1VPRkZjWkRlNlM0QVAvNnVFR2xwCnBINU8zZklWeWpwMEY2YkpGdklWaWVQVHorOFNKZGZCbDdOSVNEV08ybGF5U2FyTEVtei85OVVYVFQyVThIcEwKWFhUU3NkaWpqRDBZTk03M2hBQnpXUWxVM3hYU0Z5ST0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURPakNDQWlLZ0F3SUJBZ0lRYnByaVVJZDNPajZQUjAvc1YrVEZ6REFOQmdrcWhraUc5dzBCQVFzRkFEQVUKTVJJd0VBWURWUVFERXdsb1lYSmliM0l0WTJFd0hoY05NalV4TWpFd01ETXdNalU0V2hjTk1qWXhNakV3TURNdwpNalU0V2pBZE1Sc3dHUVlEVlFRREV4SmpiM0psTG1oaGNtSnZjaTVrYjIxaGFXNHdnZ0VpTUEwR0NTcUdTSWIzCkRRRUJBUVVBQTRJQkR3QXdnZ0VLQW9JQkFRRGdYbW0vVTN0RG9rOVhrQ3NkNVBNVFYzQVJrM05QYVJEWHlBZzUKd2FwUWY1TlR4MHQrR290U0Fxb3JvNDJOcXY1TThoaGxEOXo1RUp0ZmtzYkZ0YzUrN25NV21vQS9EWWV3TFkvQQpHMFBKRXZDcU1QYmpDT2dqZFRaZjlNN0NJVWtVczZwL3p4L0d1N1JGSkhaWmxINjQ4aEtseHNkWUV5VGFRNHZvCnBjaWVBTjNLQzNZZFhRQkJodXVSLytXMkhpbG13cHIreXRHOU9NZnozZlFZZWxpT01KL2xXUjZzdVdrMUNMYmsKSmVrNnlOdHlScXd0djVHR0J5dE42NnM0NXZSV3ZyS1VibkJpZW9YaHhYUG83enRUUzd4ZThFMjh4OXg1UEZvVgpSMWRLNFZ1L05pOWhSd1NWbTQ3TjQxbEhSRWNkTm1ndUI2TGJCeTM1S2I0M0NSMFJBZ01CQUFHamZ6QjlNQTRHCkExVWREd0VCL3dRRUF3SUZvREFkQmdOVkhTVUVGakFVQmdnckJnRUZCUWNEQVFZSUt3WUJCUVVIQXdJd0RBWUQKVlIwVEFRSC9CQUl3QURBZkJnTlZIU01FR0RBV2dCUVIyaVNnbmk4bFJEcG40eFVweVNxTDNKMlpRakFkQmdOVgpIUkVFRmpBVWdoSmpiM0psTG1oaGNtSnZjaTVrYjIxaGFXNHdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBR3UwCk1DWGNWVVVrdktBZm1Pci9SVWRCakk4SXcxWFV5c3RhaUd0Y1UyQllCK0JsRjRIeUYvbU15MHFacnArMTE1Q1MKVVhTR1V4NGJteHduZWRQNDBpajRUQit0UEVnb1ZnaVh3SUVEZWV5ajBMQU1ZZ2diOFFPdDV5QTRuU05SSWZKZwo5N0diNS9aMno2cmVwaXJHOVJFUUI4a0Y3cGREUFJ5UnRXbEl4d0ZCcENNVzdZTzNORVVITEpZc2U2dlg3RlVqCllqQjVzTzVWK21NQXk5Q2JicytzOHBnMG9CNm96WG1VQXcyRHVrS04vZDcwN2tWRDZrZHNTME1lTmh1U2ZDckgKaldBS2txam9KT09sT3RZQm13N24rVUpwekp5dHhjRWVQNlBPMFVMTDlocGlVay9Xc1hlNXZRNGxaN00xenIwRAptMVZ2d25OdXZVMzkvV2VOYTYwPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
tls.key: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBNEY1cHYxTjdRNkpQVjVBckhlVHpFMWR3RVpOelQya1ExOGdJT2NHcVVIK1RVOGRMCmZocUxVZ0txSzZPTmphcitUUElZWlEvYytSQ2JYNUxHeGJYT2Z1NXpGcHFBUHcySHNDMlB3QnREeVJMd3FqRDIKNHdqb0kzVTJYL1RPd2lGSkZMT3FmODhmeHJ1MFJTUjJXWlIrdVBJU3BjYkhXQk1rMmtPTDZLWEluZ0RkeWd0MgpIVjBBUVlicmtmL2x0aDRwWnNLYS9zclJ2VGpIODkzMEdIcFlqakNmNVZrZXJMbHBOUWkyNUNYcE9zamJja2FzCkxiK1JoZ2NyVGV1ck9PYjBWcjZ5bEc1d1lucUY0Y1Z6Nk84N1UwdThYdkJOdk1mY2VUeGFGVWRYU3VGYnZ6WXYKWVVjRWxadU96ZU5aUjBSSEhUWm9MZ2VpMndjdCtTbStOd2tkRVFJREFRQUJBb0lCQUNTbUoxM1NOQk5ESXZTcApudkZlSVhwcVVPcitDOXJQemFtQmloNXREUFhqTU55QmRFcGY2WnYyeFhjbFd3emwvbTN4S1p6d2IyYmJtSldPCjh4citiSUY5VDUxRWxXZzNQSS9Ca1hhT3ZZN05valFhbFdsV1hoelVtNUltK2RMcC92Yjd0Z0QwZ3p0Q0U5c3IKYm8ySlhQMjJ4T2NCUmpTVHcvUkhEa1p0Tmd6Z3h1Zk5XS0c1WDVXZThUSkRQeGo1L3hGWWFhdjFDOVRLV0RsMAp1dDhhQlhUN1IzVnpHSWI4T1o0T0pwZDUxVlVKdUs2aFRvN3BMVExTN1JrK0JFOHE5aDQxUkxxb1NtUHF2TzlqCmlaYk16ZTVWVTdEK1F1Z0Q3dUpUUDJPVktudUVvZ0VpVE1iU3RndUVEN1BBNGVGRFhwSGcrZks1bm9STHVEbFYKNGpGaWMvVUNnWUVBNFZOZ2QwcjRic21aMEtZdmIzSndXeWFONGNCLytPamtQVGVzUmpNVzNqMUlPTnVnbmRkSAo4OGMzYksvN2pOcng3aktOa3Vrbmh1SVZST0M3OVJ3bUQwRkhSVlNrbXBhVG4wSEp2ZXhDMHFIejh2UlA1RFZICnI3cXdSRDYvcytxWktzT29VNXNxanRSMzhqaGlIb0NKRnZUTXNISEZTdHNuNW9ZU2EyaXdHU01DZ1lFQS91bXcKUlNDanQ4ZG5aL0dFNktuMUJVcjBybXppT21EMjhTUFFsSk00OGZ0Zm9LRW51bVNaUXQ0eCs1dHdyRG43ZVdCOApUZjVFM2FoMk1jeXlSTm5WNG5NQ1VqUkM2UytTbTN2aXVLSW1PODJCN0RwTUpEaEEyazV2V1BIbDdnVDVzV0grCm82c2wreDRqYWtYejRlSmVzVW13TWxOMFJVQyswTGNIUTdXNWhqc0NnWUFjanFhaE45MDRuVkJqUTB5cndVTkEKS2lpOVBkcDZQM245MERxRFF5SlkxRWQ4L1VqaitFN2tOSkZ2c3ZZY3Fmc1RoMUN1RitLc2s2YkNiZ0VrVlliMQpVLzZtYU0zYjBjMnYxM1NzSDI5d3BwbjJac1JoVmVkWi9EMHV5UTBlemxMUE9yRHd0Nit6SG5aOU9td2xGWUZLCmFZZ3ZySnVtbXhQNWdYQ0FNR3B4SlFLQmdRQzlvVGhZNUdRR1JoZDlzcVNOdEVrcXk4empxT3BPUlczT2l6Y1MKSDhjZjlFRDZMSWh5VjMzUHlaMWpNQW9NaFFHM0ZIakVTR0FRaU02TVUxdFdicnAydjltOUwxV0xSTEdLYXdtSgpFazdnOUFzdm9WcWRJeC9UaHIrOGFnOERGcjV0SDVvZlJTVjIvcitYd2p3Z0VKY2l5YytDVUtUUkU4NGZVOWphCm5PaExtd0tCZ0Z4Vkk4SUZUTmlqQXo0bUN0bXZ3ZEpTLzlSdFhkbEZDNjhRNVlJZ0VxSW9uVmVjL0VpRzhUdWEKSVBCdGM0Wmw1bnZXeUVCeUU3M1g5WXY5YTk1aG1SQzNYK0J6U0N5Rys5a3JkYWtvNnpzekk3NmZ5MHhiUERVeAprSlJOUkJ4YWlrUHZNYWFnTHpqQmVzbDFESHVoUkJzd2lzRVA3SjFKVXE4Rmxia0V4dDN2Ci0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
kind: Secret
metadata:
annotations:
meta.helm.sh/release-name: harbor
meta.helm.sh/release-namespace: harbor
creationTimestamp: "2025-12-10T03:02:59Z"
labels:
app: harbor
app.kubernetes.io/instance: harbor
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/name: harbor
app.kubernetes.io/part-of: harbor
app.kubernetes.io/version: 2.14.1
chart: harbor
heritage: Helm
release: harbor
name: harbor-ingress
namespace: harbor
resourceVersion: "145677"
uid: 5b16d7d7-d039-4382-851e-f332f65e36f2
type: kubernetes.io/tls因为证书基本都要经过特殊的base64编码,所以这里还需要解码
bash
[root@k8s-master ~/harbor]# echo 'LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURFekNDQWZ1Z0F3SUJBZ0lRTXlmTVRIc2Y3TEloYndDb0JIODZhREFOQmdrcWhraUc5dzBCQVFzRkFEQVUKTVJJd0VBWURWUVFERXdsb1lYSmliM0l0WTJFd0hoY05NalV4TWpFd01ETXdNalU0V2hjTk1qWXhNakV3TURNdwpNalU0V2pBVU1SSXdFQVlEVlFRREV3bG9ZWEppYjNJdFkyRXdnZ0VpTUEwR0NTcUdTSWIzRFFFQkFRVUFBNElCCkR3QXdnZ0VLQW9JQkFRQ3h5ZXE2c0ZkaS9ZOUlvblluU1FLMXRNZUNUbmMrMXFhWDlmRnh0SFZnQ2J2SGFBMW4Kc2VzYUpFaDdxOGVYUHRLRzZxZ1A4bUNLSVNZbWNzTnhiVk95WHNJdTQrcW5odEpPYTlZaE5WM2N6eEdLVnoxUQpMY1pBSURtUUYyakhDbm42ckpPeU5PZXQwMzdJUUlHeVFMNXg3eWljUnNFTkM3YXFFVUpFS1Q1NUVLTEpTcFI4ClcxN0ZsdVdkdHB0NmgvTm51dVlGanZOLzBwbmsrTEcvazlWYzdud0p3Z2h4LzIwalN4R3JrYitBdGd1Vi9UUnYKVFh5ZVlnVTRIWU5sUjNZOWZCVzFhb3FWcHFuQTJ6Q21Benk4Z1Z3RHlVNi92VWluTXAySnBERXMvVGNXMm4yagptaGpRWVF6OGhWa3k5d2laM2JKNThrWldqUmNUUXBIZnorSXRBZ01CQUFHallUQmZNQTRHQTFVZER3RUIvd1FFCkF3SUNwREFkQmdOVkhTVUVGakFVQmdnckJnRUZCUWNEQVFZSUt3WUJCUVVIQXdJd0R3WURWUjBUQVFIL0JBVXcKQXdFQi96QWRCZ05WSFE0RUZnUVVFZG9rb0o0dkpVUTZaK01WS2NrcWk5eWRtVUl3RFFZSktvWklodmNOQVFFTApCUUFEZ2dFQkFGekRlVVhkVzk4cG5uWUR4UDdOMFRWY3BKZXQzcWYveXZtUlZRdnJMM3RYVk80WU1pdUxCVkQwCnorKzIwMVZRMmZSREMvaTI1S3lBQ1VxWWdUdUY3dmlQUForV0lZTitpZzJWakxWVnVZZjI2M0hZSlRNUjlhVkEKMlp0UXJoZ0d0cUV1L1JYOE00R1VDbEplb3JDVUpDQUlYc1FMbW1kd3JnVzJEZ05KL0EzcUhXY2FIOEttdE1JSApmUXpyVi9ULzdjMWtsL1ZrZjkxOUVCcU5KSU9JOUQvRmFCZ3pzbnpUd0pLb1VPRkZjWkRlNlM0QVAvNnVFR2xwCnBINU8zZklWeWpwMEY2YkpGdklWaWVQVHorOFNKZGZCbDdOSVNEV08ybGF5U2FyTEVtei85OVVYVFQyVThIcEwKWFhUU3NkaWpqRDBZTk03M2hBQnpXUWxVM3hYU0Z5ST0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=' |base64 -d
-----BEGIN CERTIFICATE-----
MIIDEzCCAfugAwIBAgIQMyfMTHsf7LIhbwCoBH86aDANBgkqhkiG9w0BAQsFADAU
MRIwEAYDVQQDEwloYXJib3ItY2EwHhcNMjUxMjEwMDMwMjU4WhcNMjYxMjEwMDMw
MjU4WjAUMRIwEAYDVQQDEwloYXJib3ItY2EwggEiMA0GCSqGSIb3DQEBAQUAA4IB
DwAwggEKAoIBAQCxyeq6sFdi/Y9IonYnSQK1tMeCTnc+1qaX9fFxtHVgCbvHaA1n
sesaJEh7q8eXPtKG6qgP8mCKISYmcsNxbVOyXsIu4+qnhtJOa9YhNV3czxGKVz1Q
LcZAIDmQF2jHCnn6rJOyNOet037IQIGyQL5x7yicRsENC7aqEUJEKT55EKLJSpR8
W17FluWdtpt6h/NnuuYFjvN/0pnk+LG/k9Vc7nwJwghx/20jSxGrkb+AtguV/TRv
TXyeYgU4HYNlR3Y9fBW1aoqVpqnA2zCmAzy8gVwDyU6/vUinMp2JpDEs/TcW2n2j
mhjQYQz8hVky9wiZ3bJ58kZWjRcTQpHfz+ItAgMBAAGjYTBfMA4GA1UdDwEB/wQE
AwICpDAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwDwYDVR0TAQH/BAUw
AwEB/zAdBgNVHQ4EFgQUEdokoJ4vJUQ6Z+MVKckqi9ydmUIwDQYJKoZIhvcNAQEL
BQADggEBAFzDeUXdW98pnnYDxP7N0TVcpJet3qf/yvmRVQvrL3tXVO4YMiuLBVD0
z++201VQ2fRDC/i25KyACUqYgTuF7viPPZ+WIYN+ig2VjLVVuYf263HYJTMR9aVA
2ZtQrhgGtqEu/RX8M4GUClJeorCUJCAIXsQLmmdwrgW2DgNJ/A3qHWcaH8KmtMIH
fQzrV/T/7c1kl/Vkf919EBqNJIOI9D/FaBgzsnzTwJKoUOFFcZDe6S4AP/6uEGlp
pH5O3fIVyjp0F6bJFvIViePTz+8SJdfBl7NISDWO2laySarLEmz/99UXTT2U8HpL
XXTSsdijjD0YNM73hABzWQlU3xXSFyI=
-----END CERTIFICATE-----将解码的证书内容重定向到我们的ca.crt文件中
bash
[root@k8s-master ~/harbor]# echo 'LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURFekNDQWZ1Z0F3SUJBZ0lRTXlmTVRIc2Y3TEloYndDb0JIODZhREFOQmdrcWhraUc5dzBCQVFzRkFEQVUKTVJJd0VBWURWUVFERXdsb1lYSmliM0l0WTJFd0hoY05NalV4TWpFd01ETXdNalU0V2hjTk1qWXhNakV3TURNdwpNalU0V2pBVU1SSXdFQVlEVlFRREV3bG9ZWEppYjNJdFkyRXdnZ0VpTUEwR0NTcUdTSWIzRFFFQkFRVUFBNElCCkR3QXdnZ0VLQW9JQkFRQ3h5ZXE2c0ZkaS9ZOUlvblluU1FLMXRNZUNUbmMrMXFhWDlmRnh0SFZnQ2J2SGFBMW4Kc2VzYUpFaDdxOGVYUHRLRzZxZ1A4bUNLSVNZbWNzTnhiVk95WHNJdTQrcW5odEpPYTlZaE5WM2N6eEdLVnoxUQpMY1pBSURtUUYyakhDbm42ckpPeU5PZXQwMzdJUUlHeVFMNXg3eWljUnNFTkM3YXFFVUpFS1Q1NUVLTEpTcFI4ClcxN0ZsdVdkdHB0NmgvTm51dVlGanZOLzBwbmsrTEcvazlWYzdud0p3Z2h4LzIwalN4R3JrYitBdGd1Vi9UUnYKVFh5ZVlnVTRIWU5sUjNZOWZCVzFhb3FWcHFuQTJ6Q21Benk4Z1Z3RHlVNi92VWluTXAySnBERXMvVGNXMm4yagptaGpRWVF6OGhWa3k5d2laM2JKNThrWldqUmNUUXBIZnorSXRBZ01CQUFHallUQmZNQTRHQTFVZER3RUIvd1FFCkF3SUNwREFkQmdOVkhTVUVGakFVQmdnckJnRUZCUWNEQVFZSUt3WUJCUVVIQXdJd0R3WURWUjBUQVFIL0JBVXcKQXdFQi96QWRCZ05WSFE0RUZnUVVFZG9rb0o0dkpVUTZaK01WS2NrcWk5eWRtVUl3RFFZSktvWklodmNOQVFFTApCUUFEZ2dFQkFGekRlVVhkVzk4cG5uWUR4UDdOMFRWY3BKZXQzcWYveXZtUlZRdnJMM3RYVk80WU1pdUxCVkQwCnorKzIwMVZRMmZSREMvaTI1S3lBQ1VxWWdUdUY3dmlQUForV0lZTitpZzJWakxWVnVZZjI2M0hZSlRNUjlhVkEKMlp0UXJoZ0d0cUV1L1JYOE00R1VDbEplb3JDVUpDQUlYc1FMbW1kd3JnVzJEZ05KL0EzcUhXY2FIOEttdE1JSApmUXpyVi9ULzdjMWtsL1ZrZjkxOUVCcU5KSU9JOUQvRmFCZ3pzbnpUd0pLb1VPRkZjWkRlNlM0QVAvNnVFR2xwCnBINU8zZklWeWpwMEY2YkpGdklWaWVQVHorOFNKZGZCbDdOSVNEV08ybGF5U2FyTEVtei85OVVYVFQyVThIcEwKWFhUU3NkaWpqRDBZTk03M2hBQnpXUWxVM3hYU0Z5ST0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=' |base64 -d >ca.crt2.3 创建容器运行时的证书目录
bash
[root@k8s-master ~/harbor]# mkdir -p /etc/containerd/certs.d/core.harbor.domain
[root@k8s-master ~/harbor]# ll /etc/containerd/certs.d/core.harbor.domain
total 0
[root@k8s-master ~/harbor]# cp -a ca.crt /etc/containerd/certs.d/core.harbor.domain/
[root@k8s-master ~/harbor]# ll /etc/containerd/certs.d/core.harbor.domain/
total 4
-rw-r--r-- 1 root root 1127 Dec 10 11:27 ca.crt
[root@k8s-master ~/harbor]# cp ca.crt /usr/local/share/ca-certificates/
[root@k8s-master ~/harbor]# /usr/sbin/update-ca-certificates
Updating certificates in /etc/ssl/certs...
rehash: warning: skipping ca-certificates.crt, it does not contain exactly one certificate or CRL
1 added, 0 removed; done.
Running hooks in /etc/ca-certificates/update.d...
done.
# 额外注意
检查containerd的config.toml文件,最好添加证书目录
[plugins]
[plugins."io.containerd.grpc.v1.cri".registry]
config_path = "/etc/containerd/certs.d"2.4 测试
bash
# 推送命令
[root@k8s-master ~/harbor]# ctr -n k8s.io images tag docker.io/library/busybox:latest core.harbor.domain/library/busybox:v1
# 登录仓库
(如果你是测试的自建域名需要加入Linux服务器的hosts解析记录,如果是真实域名可跳过)
[root@k8s-master ~/harbor]# tail -1 /etc/hosts
10.0.0.150 core.harbor.domain
[root@k8s-master ~/harbor]# nerdctl -n k8s.io login core.harbor.domain
Enter Username: admin
Enter Password:
WARNING! Your credentials are stored unencrypted in '/root/.docker/config.json'.
Configure a credential helper to remove this warning. See
https://docs.docker.com/go/credential-store/
Login Succeeded
[root@k8s-master ~/harbor]# nerdctl -n k8s.io image push core.harbor.domain/library/busybox:v1
INFO[0000] pushing as a reduced-platform image (application/vnd.docker.distribution.manifest.v2+json, sha256:0124622a5e535aa839c9f2d58ae95be4202bbeb2bb32917f4feaef28ab9cff44)
manifest-sha256:0124622a5e535aa839c9f2d58ae95be4202bbeb2bb32917f4feaef28ab9cff44: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:a10d77880eaf7e9f53f332b86ff61f9c2b9dfe41900762958e19614687a7cb05: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:87ff76f62d367950186bde563642e39208c0e2b4afc833b4b3b01b8fef60ae9e: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 0.7 s total: 2.1 Mi (3.0 MiB/s) 
三、漏扫方案
因为我们跳过了trivy漏扫库的更新,所以如果直接去进行漏扫肯定会失败的,报错的日志类似于
2025-12-10T05:56:07Z [INFO] [/pkg/scan/job.go:172]: Report mime types: [application/vnd.security.vulnerability.report; version=1.1]
2025-12-10T05:56:07Z [INFO] [/pkg/scan/job.go:229]: Get report for mime type: application/vnd.security.vulnerability.report; version=1.1
2025-12-10T05:56:09Z [ERROR] [/pkg/scan/job.go:294]: scan job: fetch scan report, mimetype application/vnd.security.vulnerability.report; version=1.1: running trivy wrapper: running trivy: exit status 1: 2025-12-10T05:56:08Z WARN '--vuln-type' is deprecated. Use '--pkg-types' instead.
2025-12-10T05:56:08Z INFO Adding schema version to the DB repository for backward compatibility repository="mirror.gcr.io/aquasec/trivy-db:2"
2025-12-10T05:56:08Z INFO Adding schema version to the DB repository for backward compatibility repository="ghcr.io/aquasecurity/trivy-db:2"
2025-12-10T05:56:08Z INFO Adding schema version to the DB repository for backward compatibility repository="mirror.gcr.io/aquasec/trivy-java-db:1"
2025-12-10T05:56:08Z INFO Adding schema version to the DB repository for backward compatibility repository="ghcr.io/aquasecurity/trivy-java-db:1"
2025-12-10T05:56:08Z ERROR [vulndb] The first run cannot skip downloading DB
2025-12-10T05:56:08Z FATAL Fatal error run error: init error: DB error: database error: --skip-db-update cannot be specified on the first run
: general response handler: unexpected status code: 500, expected: 200
3.1 离线传入漏洞库文件
bash
先将漏洞库文件传入到我们的物理机上面
[root@k8s-master ~]# ll trivy.tar.gz
-rw-r--r-- 1 root root 46635463 Nov 5 16:34 trivy.tar.gz
然后拷贝到pod内部
[root@k8s-master ~]# kubectl -n harbor cp trivy.tar.gz harbor-trivy-0:/tmp/
进入pod
[root@k8s-master ~/harbor]# kubectl -n harbor exec -it harbor-trivy-0 -- /bin/bash
进入到漏扫库目录
scanner [ ~ ]$ cd /home/scanner/.cache/
默认的是空的
scanner [ ~/.cache ]$ ls -l trivy/
total 0
我们将默认的目录给删除,重新解压我们离线包
scanner [ ~/.cache ]$ mv /tmp/trivy.tar.gz .
scanner [ ~/.cache ]$ rm -rf trivy
scanner [ ~/.cache ]$ tar xf trivy.tar.gz
scanner [ ~/.cache ]$ ls -l trivy
total 8
drwxr-xr-x 2 scanner scanner 4096 2024-03-26 01:26 db
drwx------ 2 scanner scanner 4096 2024-03-26 01:20 fanal
scanner [ ~/.cache ]$ ls -l trivy/db/
total 437448
-rw-r--r-- 1 scanner scanner 153 2024-03-26 01:26 metadata.json
-rw------- 1 scanner scanner 447942656 2024-03-26 00:16 trivy.db3.2 进行漏扫
3.2.1 进入项目名称
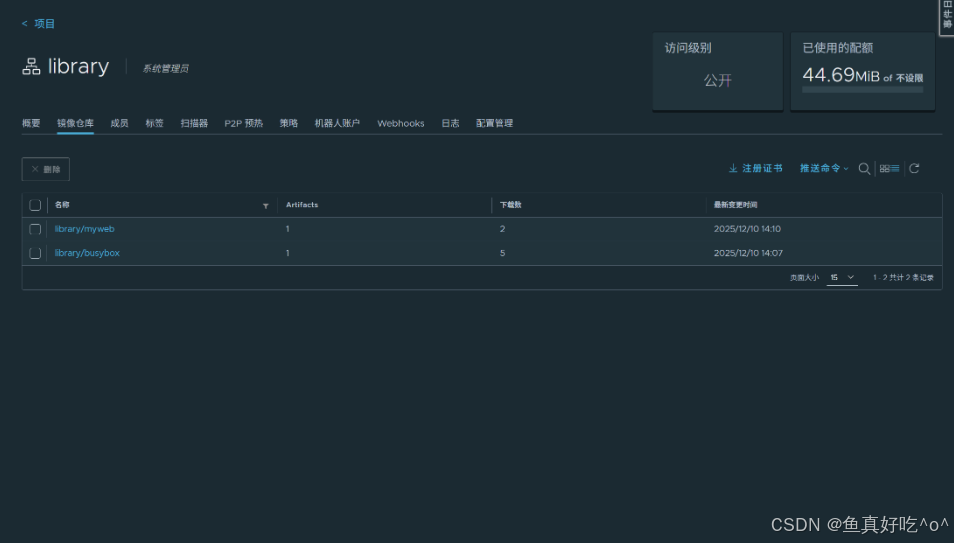
3.2.2 选择镜像点击漏扫
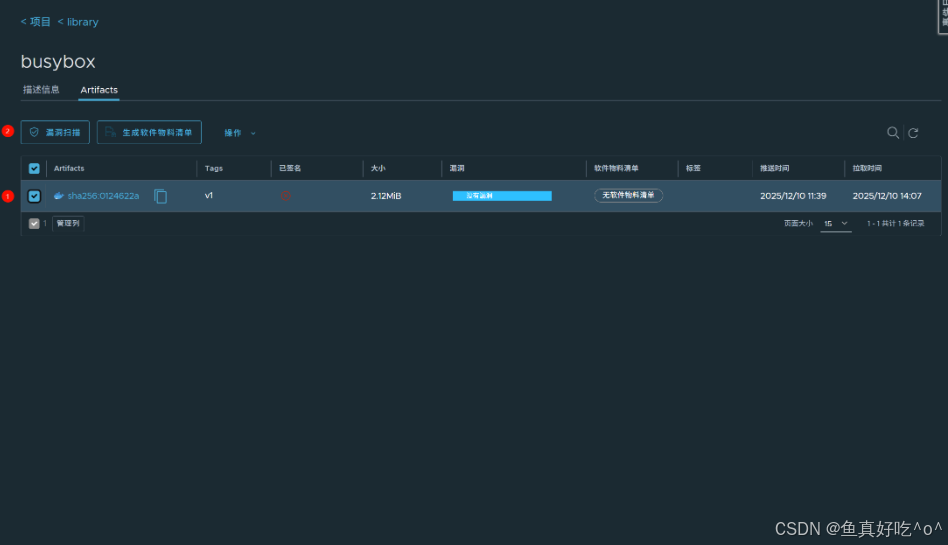
这是官方的busybox镜像竟然没有漏洞!
那我试一下我自己封装的nginx镜像
bash
[root@k8s-master ~/harbor]# nerdctl -n k8s.io push core.harbor.domain/library/myweb:v1
INFO[0000] pushing as a reduced-platform image (application/vnd.docker.distribution.manifest.v2+json, sha256:14410504676fae6af753a134e6e2e6f94cedd037c041f22e0eed7ee9a83b2690)
manifest-sha256:14410504676fae6af753a134e6e2e6f94cedd037c041f22e0eed7ee9a83b2690: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:cb304388cde09953497b7cbe0122cab88ca896c07b68db9b5a7e1c9e01398b38: done |++++++++++++++++++++++++++++++++++++++|
config-sha256:747b42d457cf84d79bba790e188520262b5122ce677b2c1bf34f79af18947ba0: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:aec1e8cf14f5c0071d1d8f6b3f6e273bfac3916b5b960e5746bfb6b33b91be23: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:63ca1fbb43ae5034640e5e6cb3e083e05c290072c5366fcaa9d62435a4cced85: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:2ff96b2e5450a90407eb56d0683091192aff9b7e5fa37254b94a7f8dcc4c79bf: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:11134cc97d7f076e5df4c36365e99ef68baf1d2c5f9d0964c680773ee06d0ef6: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:f7a5847cdca904c51b6573daca690f67c343c38218dfb838aeac772c52ed5afa: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:027907faf592c9d4a0b1cb1a421347fa1d83a7bd9c819e68417b5ea1d4b643a9: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:b0f60355fd52e5a6375c2a09aaf215035e7eb84e78c9d3aaaa928a1e3017a336: done |++++++++++++++++++++++++++++++++++++++|
layer-sha256:717b3a077b07fb6f8bdf782e1750f20ae11d8bb5917e167a29c0b0022e0a9a53: done |++++++++++++++++++++++++++++++++++++++|
elapsed: 1.4 s total: 42.6 M (30.4 MiB/s) 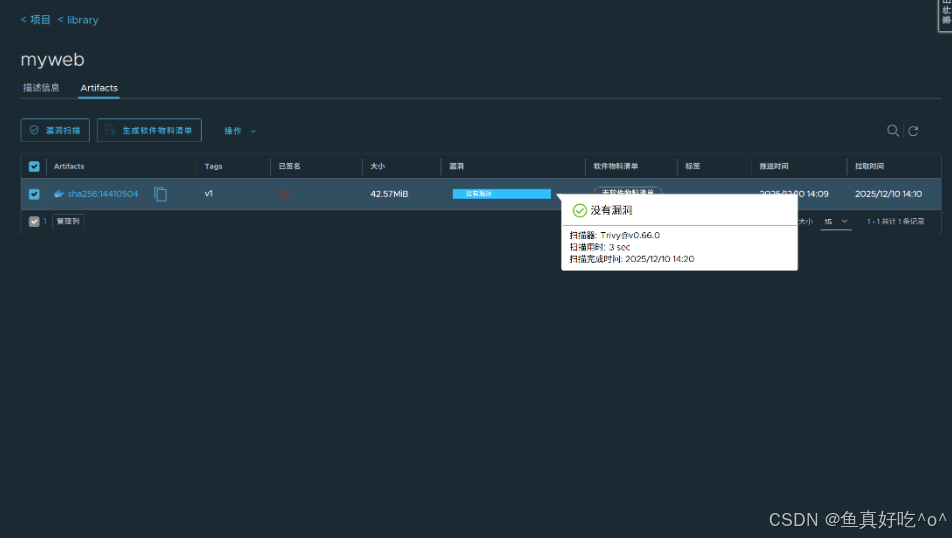
也没有漏洞,安全的
彩蛋
1. Docker运行时接入云原生Harbor
直接按照2.2的操作就行
创建容器运行时的证书目录
bash
mkdir -p /etc/docker/certs.d/core.harbor.domain
cp ca.crt /etc/docker/certs.d/core.harbor.domain/然后测试即可,步骤比containerd简缩一点
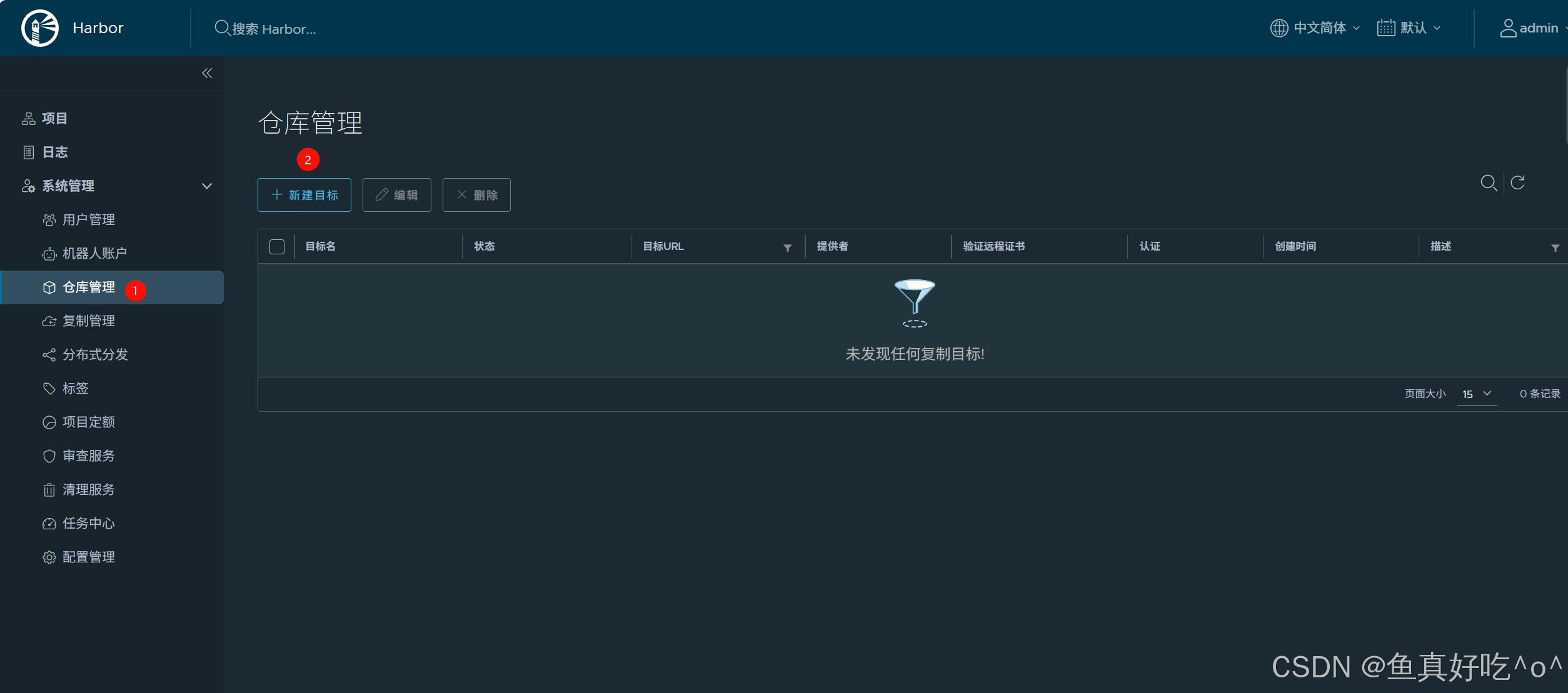
2. Harbor同步DockerHub仓库
首先你要有自己的DockerHub账号且能够正常登录。
其次你需要一台大容量且网络比较好的服务器。
最后Harbor要配置仓库和复制规则。
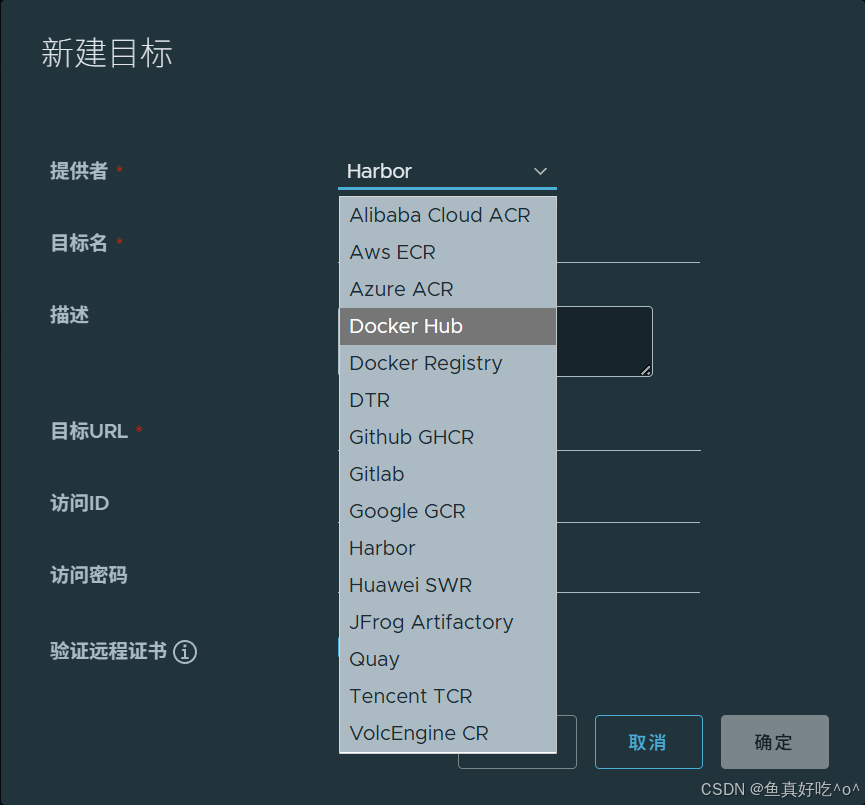
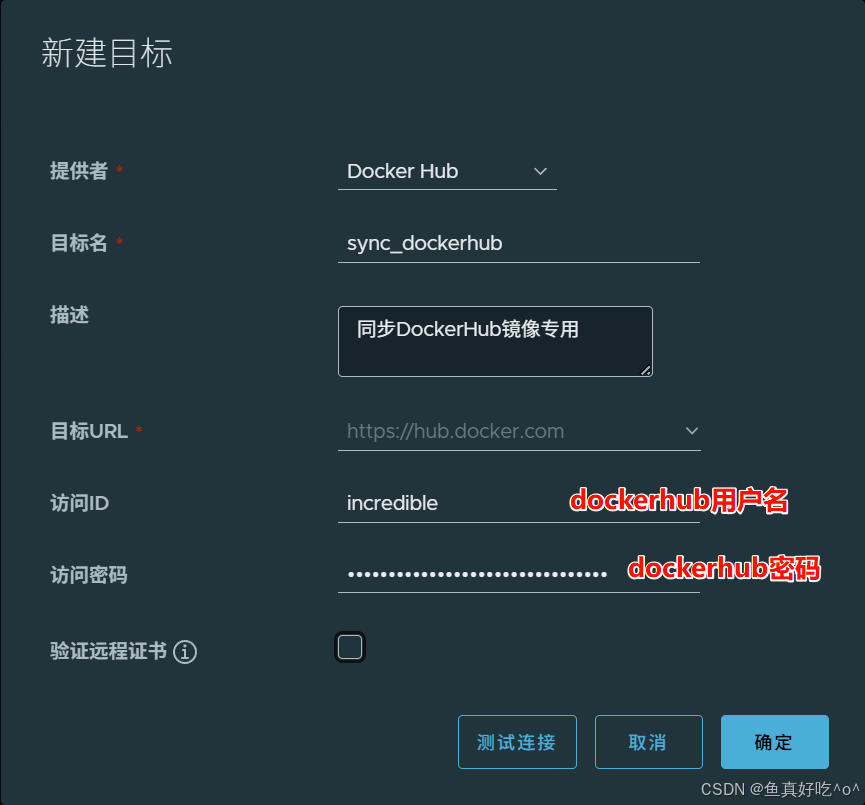
取消证书验证并且测试连接,这里因为网络的问题就不连接了。。。
回到复制规则这里新建复制规则
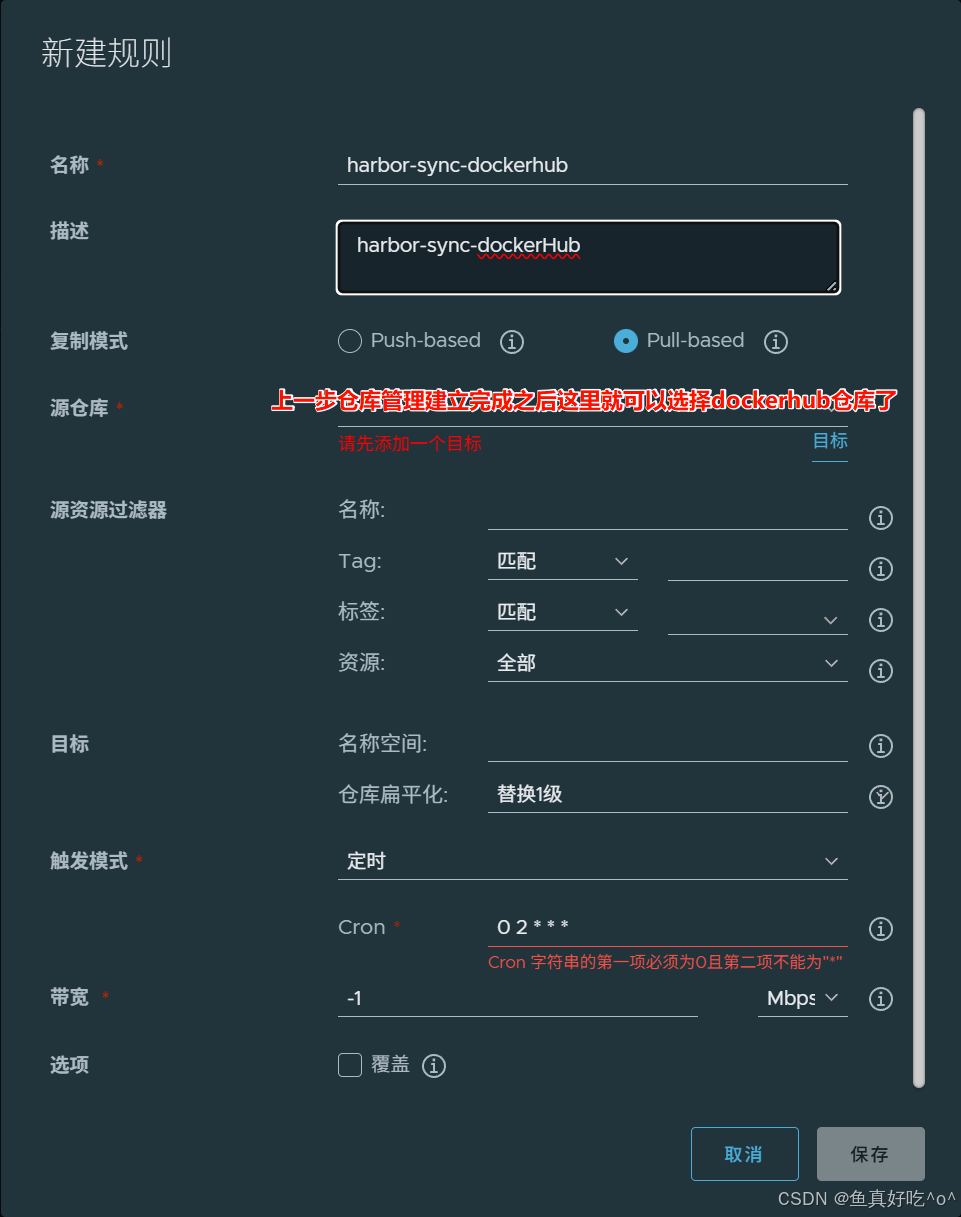
我们选择定时同步在深夜。
保存之后看到状态时启用的并且为succeed即可。